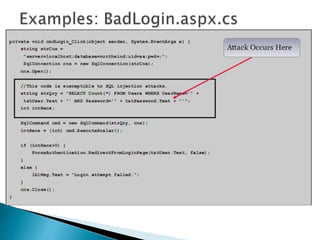
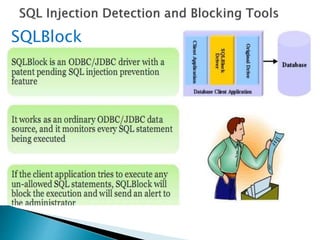
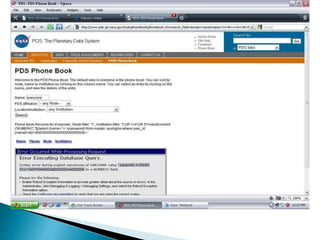
The document discusses SQL injection, a security exploit that allows attackers to manipulate and retrieve data from a web application's backend database through malformed SQL statements. It outlines various types of SQL injection techniques, including SQL manipulation, code injection, and buffer overflow, along with their operation methods. Additionally, it addresses countermeasures to prevent such attacks, emphasizing the importance of minimizing database privileges and implementing input validation and error handling.