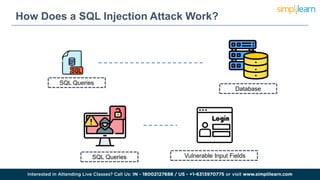
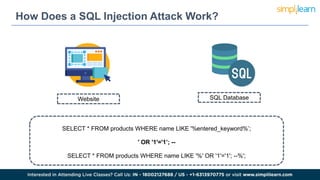
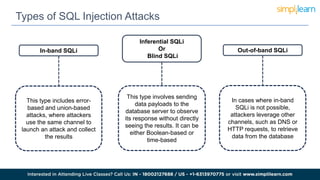
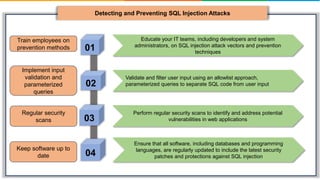
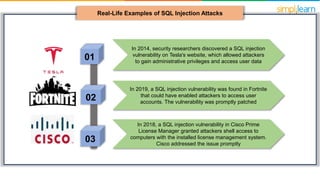
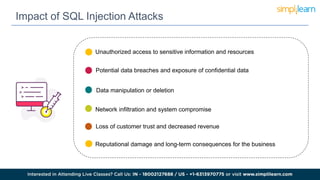
SQL injection is a technique used by attackers to manipulate web application database queries through malicious SQL code, potentially gaining unauthorized access to sensitive information. Types of attacks include in-band, inferential, and out-of-band SQL injection, each with various methods of execution. Preventive measures include educating IT teams, validating user input, performing regular security scans, and keeping software up to date.