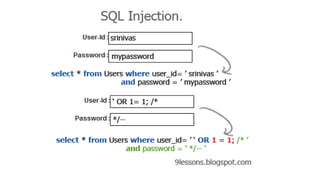
This document discusses SQL injection, including how it works, examples of attacks, impact, types of SQL injection attacks, and defenses against SQL injection. SQL injection allows malicious SQL code to be injected into an entry field of a web application to gain unauthorized access to the underlying database. It remains a common web application security vulnerability. The document recommends data sanitization, web application firewalls, limiting database privileges, and using prepared statements instead of constructing SQL queries with user input to help defend against SQL injection attacks.