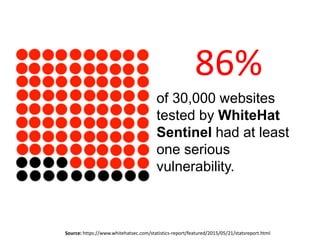
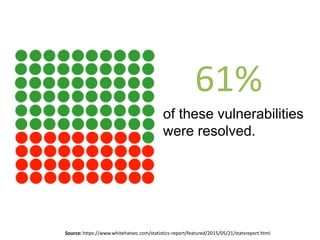
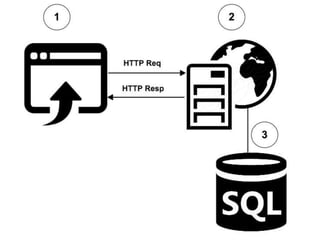
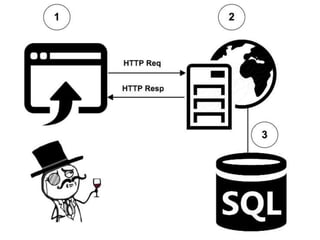
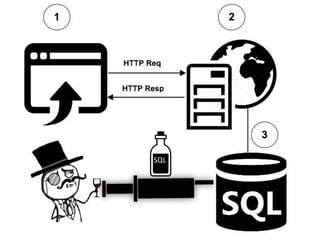
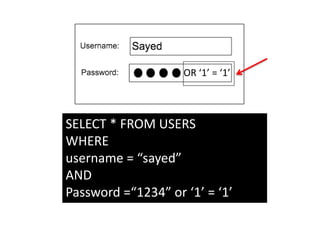
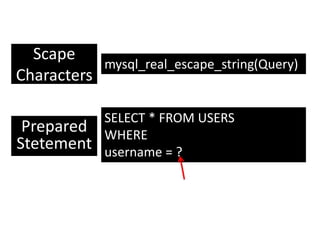
According to a 2015 study, 86% of over 30,000 websites tested had at least one serious vulnerability. Of the vulnerabilities found, 61% were resolved within 193 days. SQL injection is a type of attack where an attacker tries to alter SQL statements by inserting new SQL keywords or operators. Examples provided demonstrate how an attacker can use SQL injection to drop all databases or return all records. Prevention techniques like escaping characters and using prepared statements can help protect against SQL injection attacks.