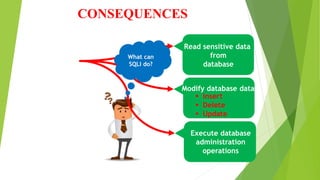
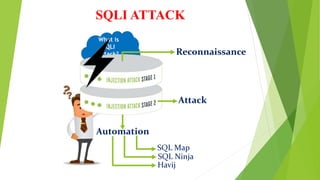
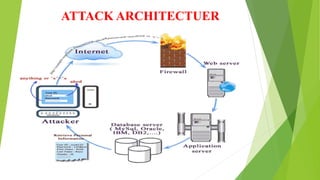
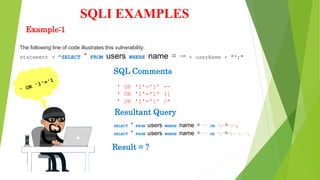
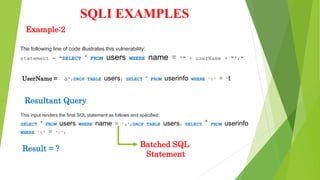
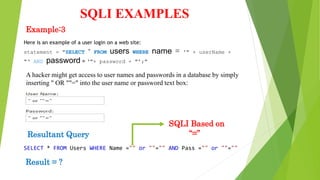
This document discusses SQL injection (SQLI), which is a code injection technique used to attack data-driven applications. SQLI works by inserting malicious SQL statements into entry fields for execution on the backend database. This allows attackers to read sensitive data, modify database contents, and perform administration tasks. The document outlines common SQLI attack methods like error-based and union-based techniques. It also categorizes SQLI attacks as in-band, inferential/blind, or out-of-band based on how results are returned. Examples are provided to illustrate how SQLI exploits vulnerabilities in dynamic SQL queries.