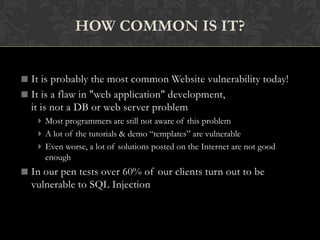
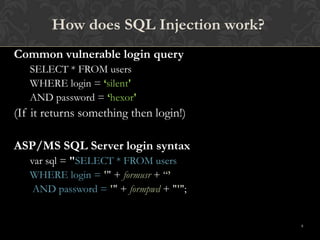
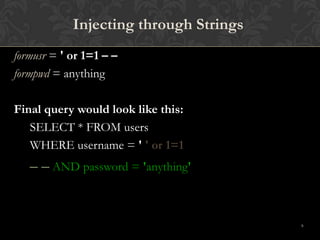
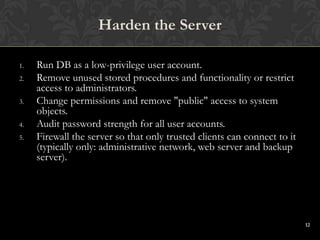
This document discusses SQL injections and how to prevent them. It begins by defining SQL injection as the ability to inject SQL commands into a database through an application. It then explains how SQL injections work by exploiting vulnerabilities in user input validation. The document outlines common techniques used in SQL injections and discusses how widespread this issue is. It provides recommendations for input validation, securing databases, and detecting and discouraging SQL injection attacks. The key takeaway is that proper input validation and server hardening are needed to prevent SQL injections.