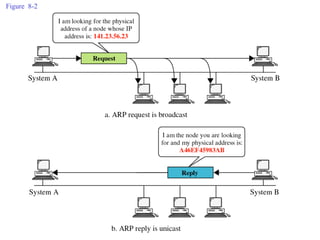
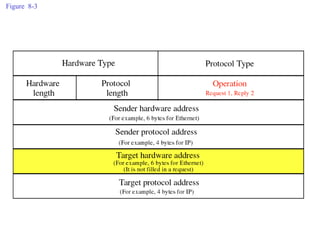
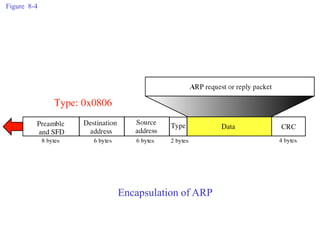
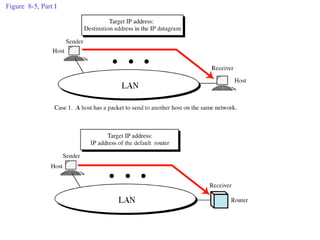
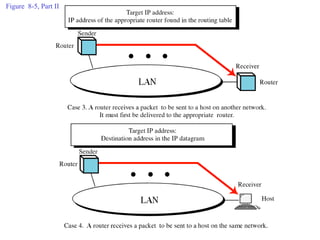
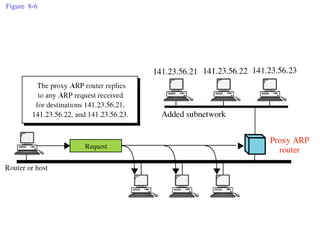
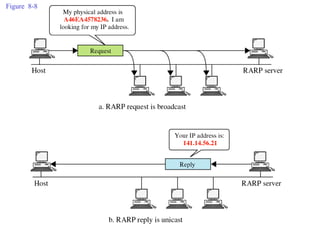
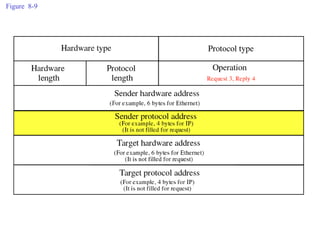
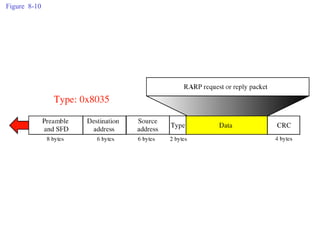
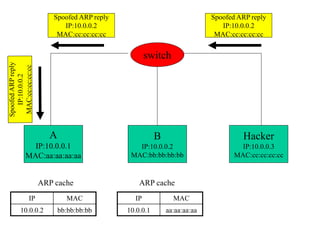
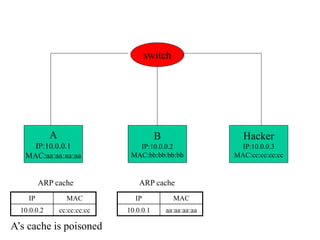
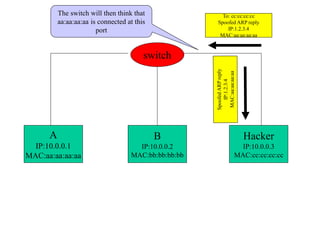
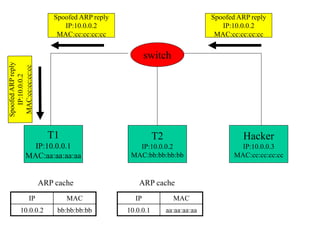
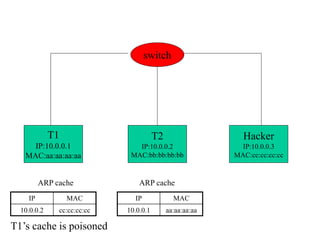
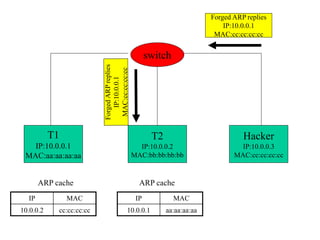
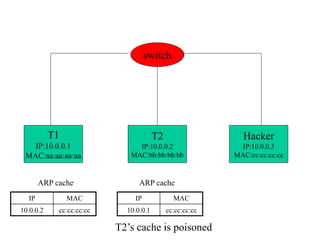
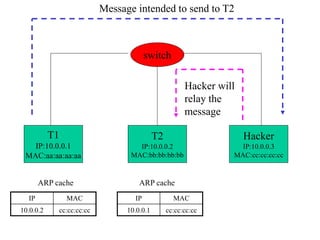
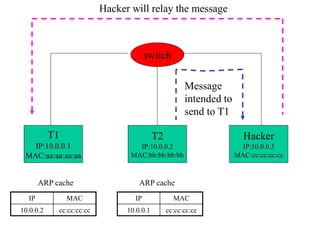
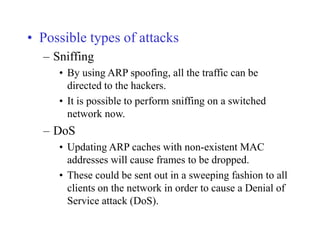
ARP spoofing allows an attacker to intercept or modify communications between two hosts on a local network by falsifying ARP responses and changing a target's ARP cache entries. The attacker sends spoofed ARP replies associating the target's IP addresses with the attacker's MAC address, intercepting traffic intended for another host. This enables man-in-the-middle attacks where the attacker can sniff or modify intercepted traffic before forwarding it. Defenses include static ARP entries and port security on switches, but weaknesses remain, especially on networks using dynamic addressing protocols like DHCP.