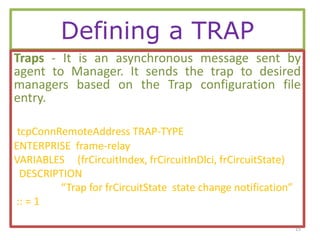
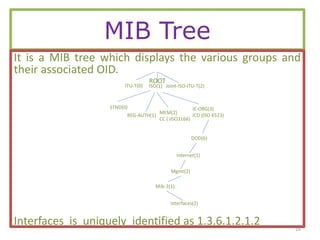
The document provides a comprehensive overview of SNMP (Simple Network Management Protocol), detailing its use for managing and monitoring devices on IP networks as defined by IETF RFC 1157. Key components discussed include managed objects, management information base (MIB), SNMP agents, and managers, along with the architecture for data transmission and the structure of MIBs. It also covers SNMP operations such as retrieving and modifying object values and provides examples of defining tables and handling asynchronous messages through traps.