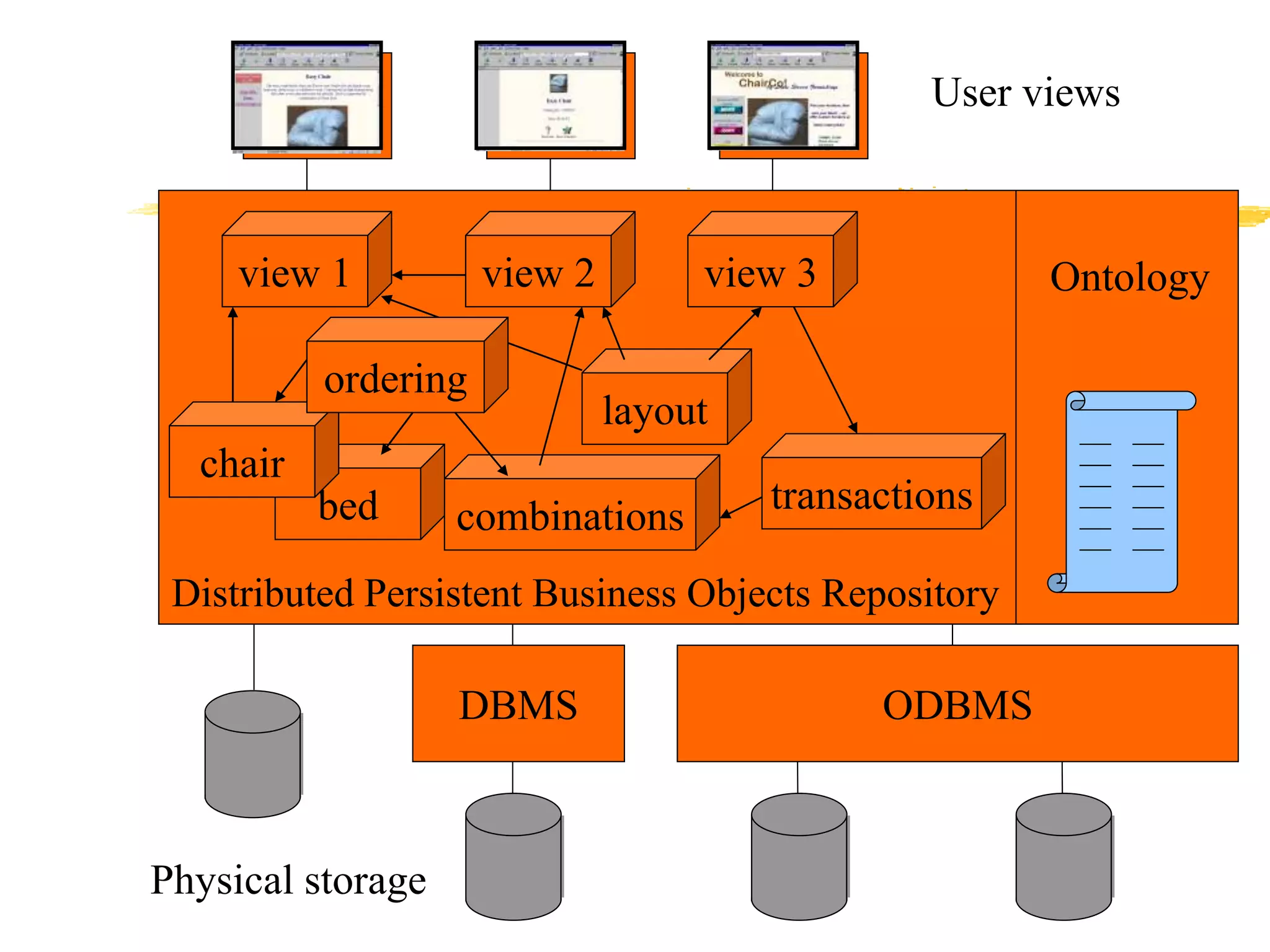
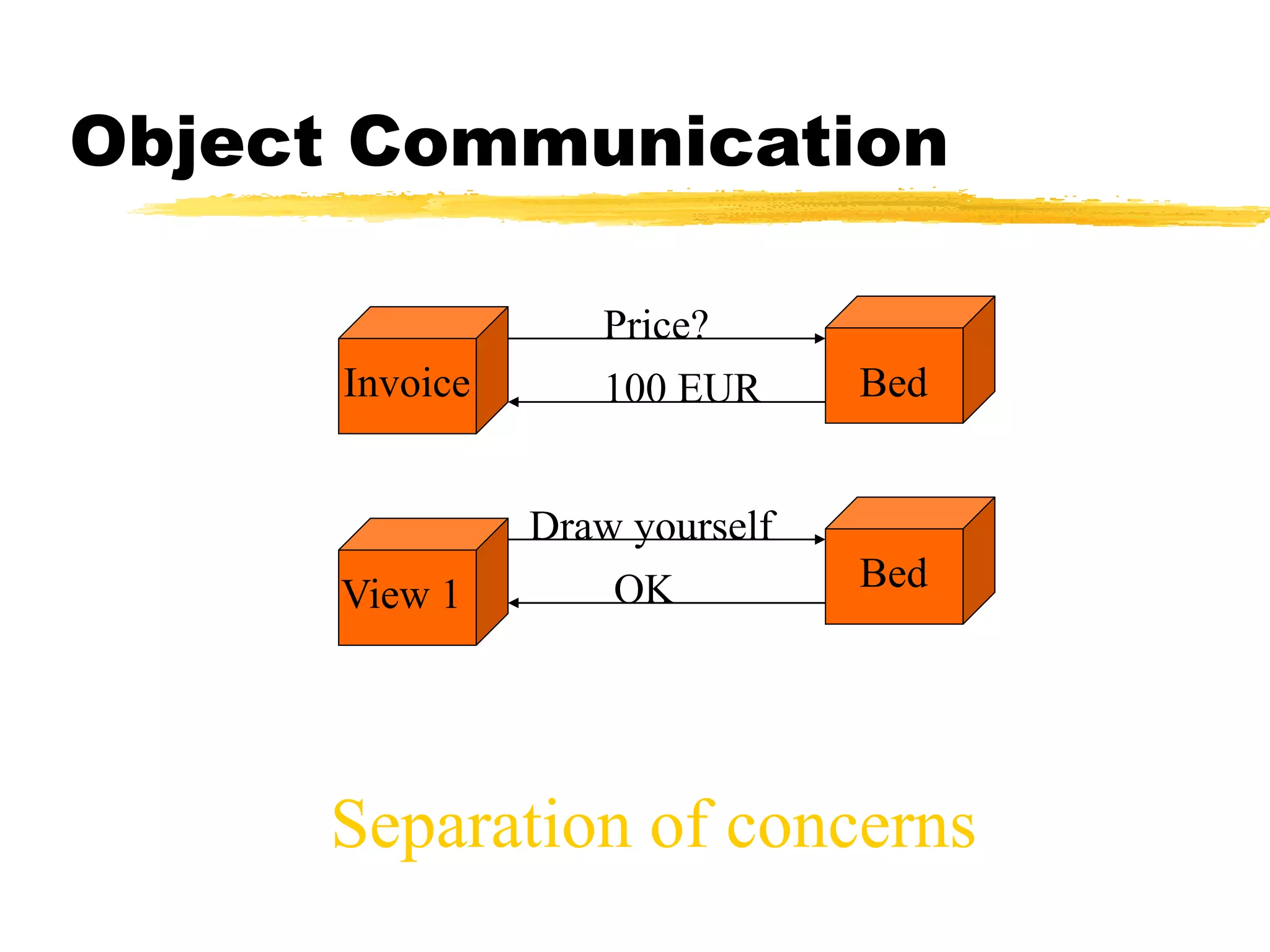
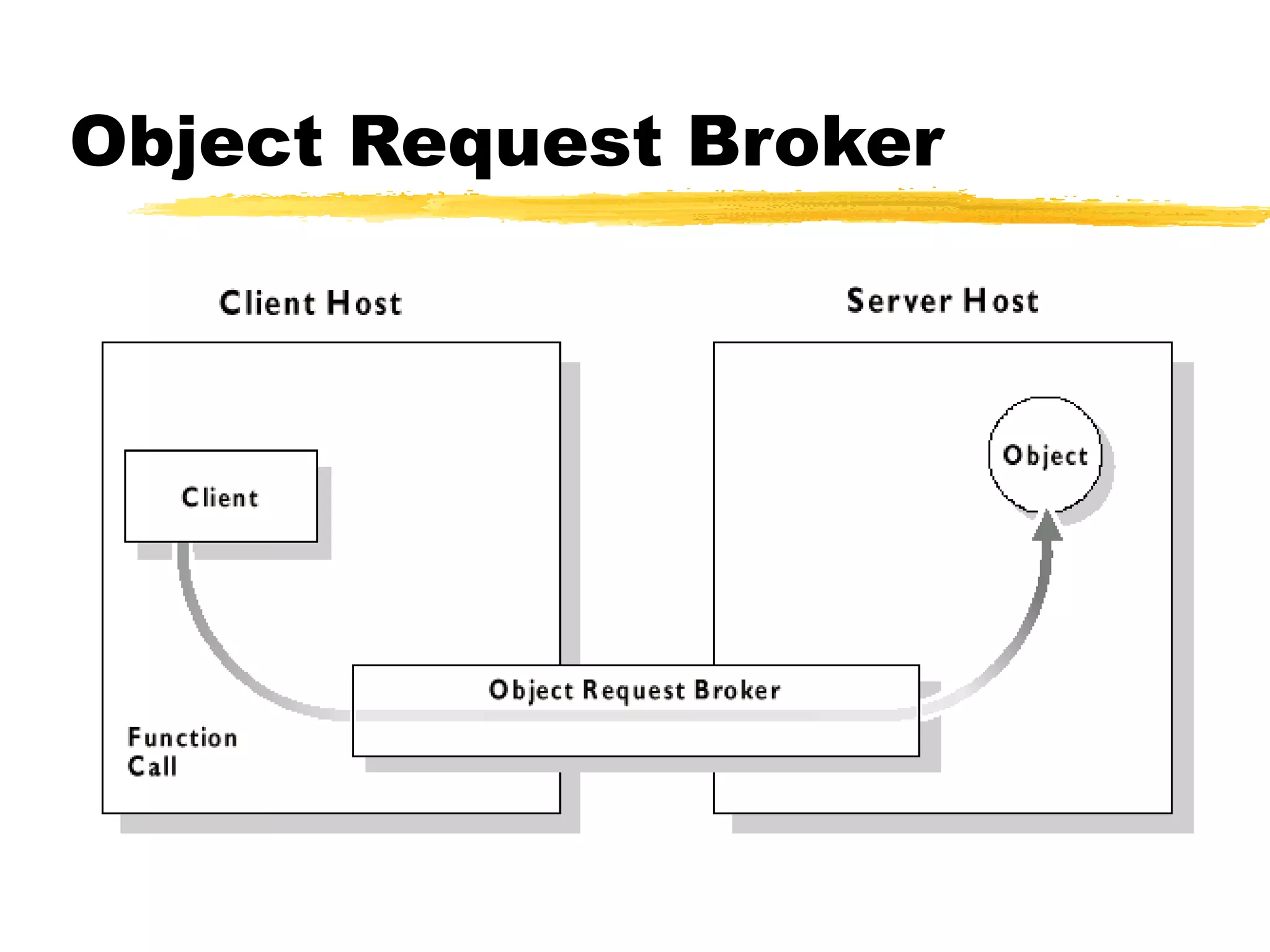
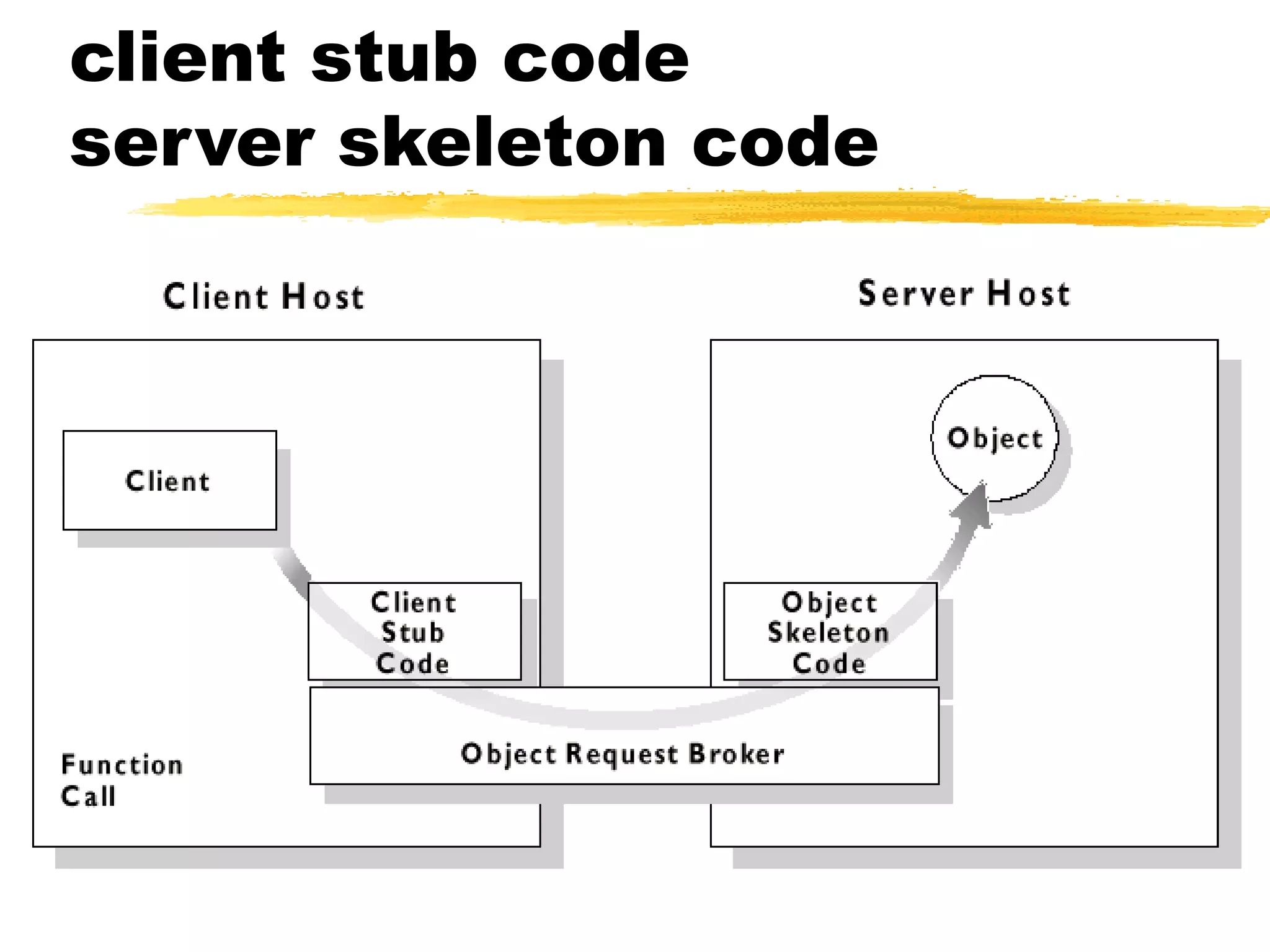
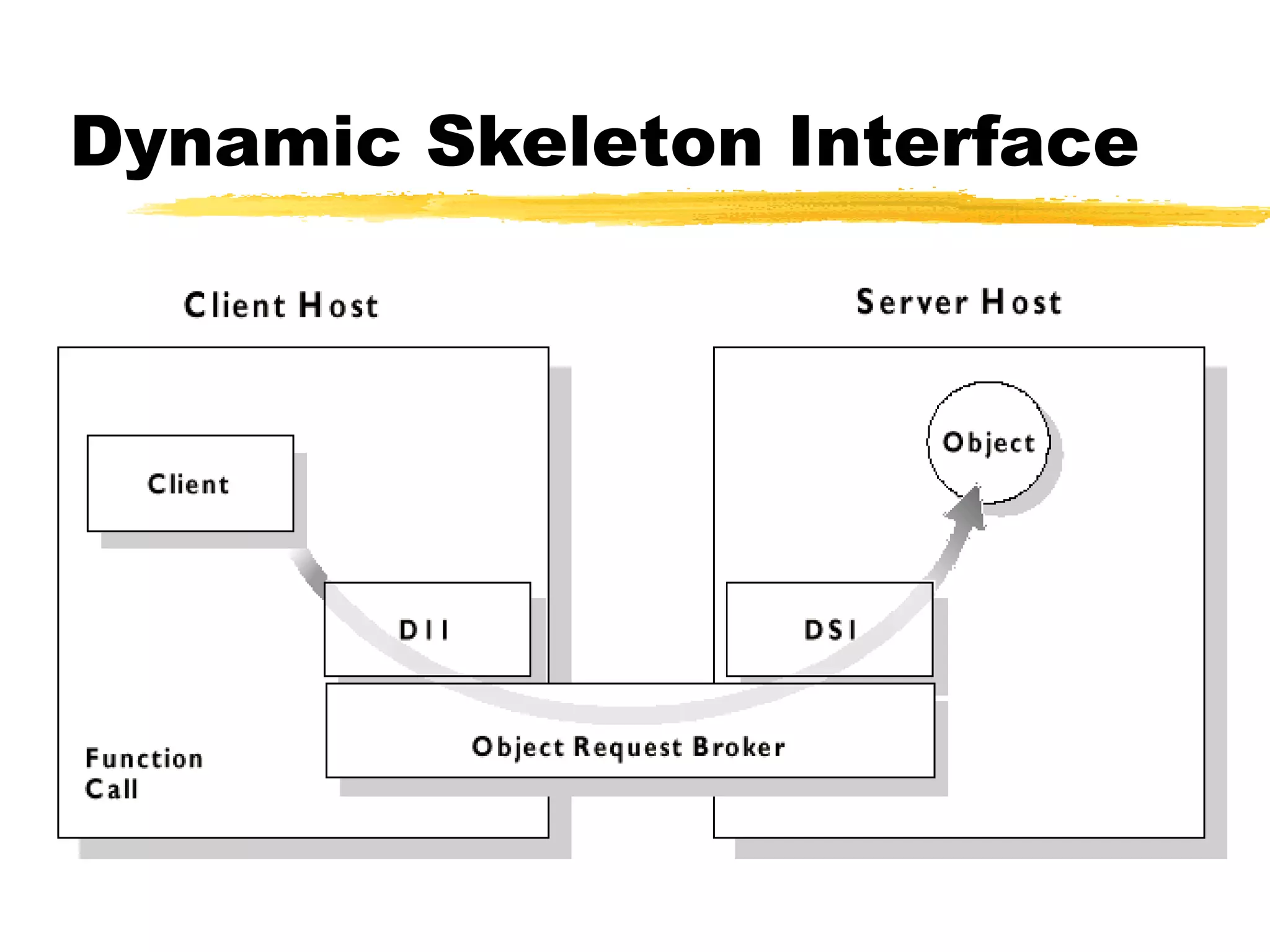
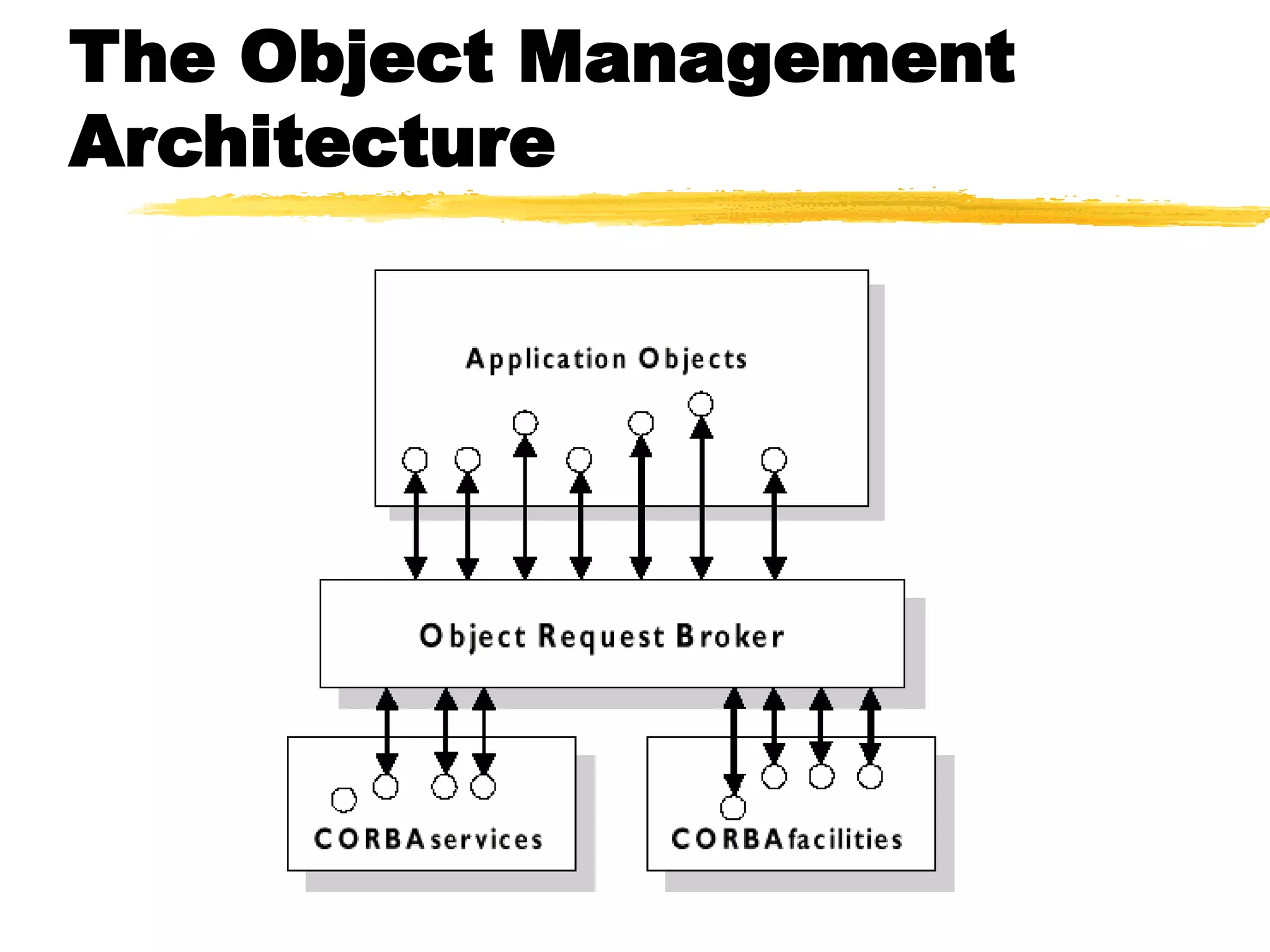
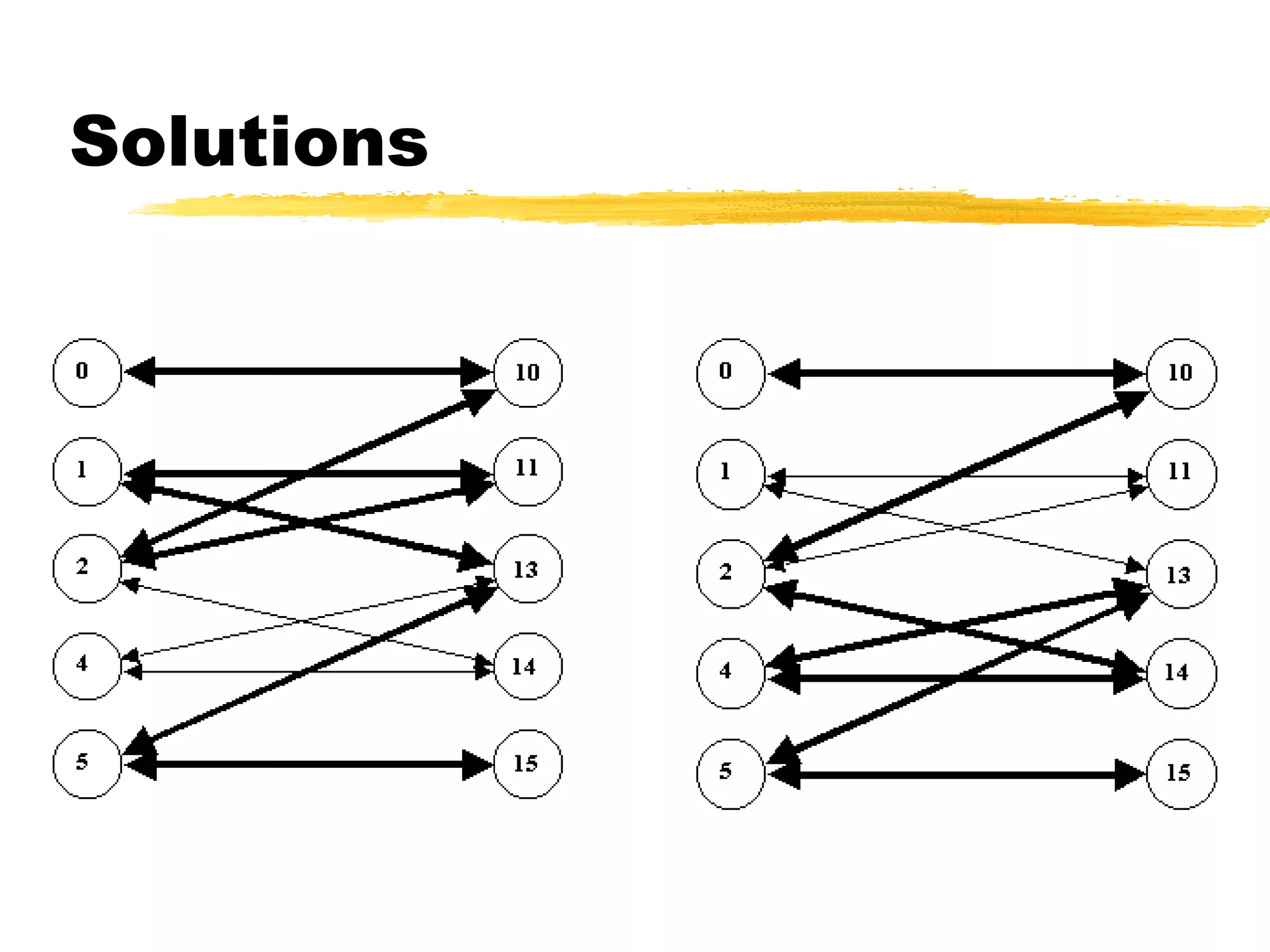
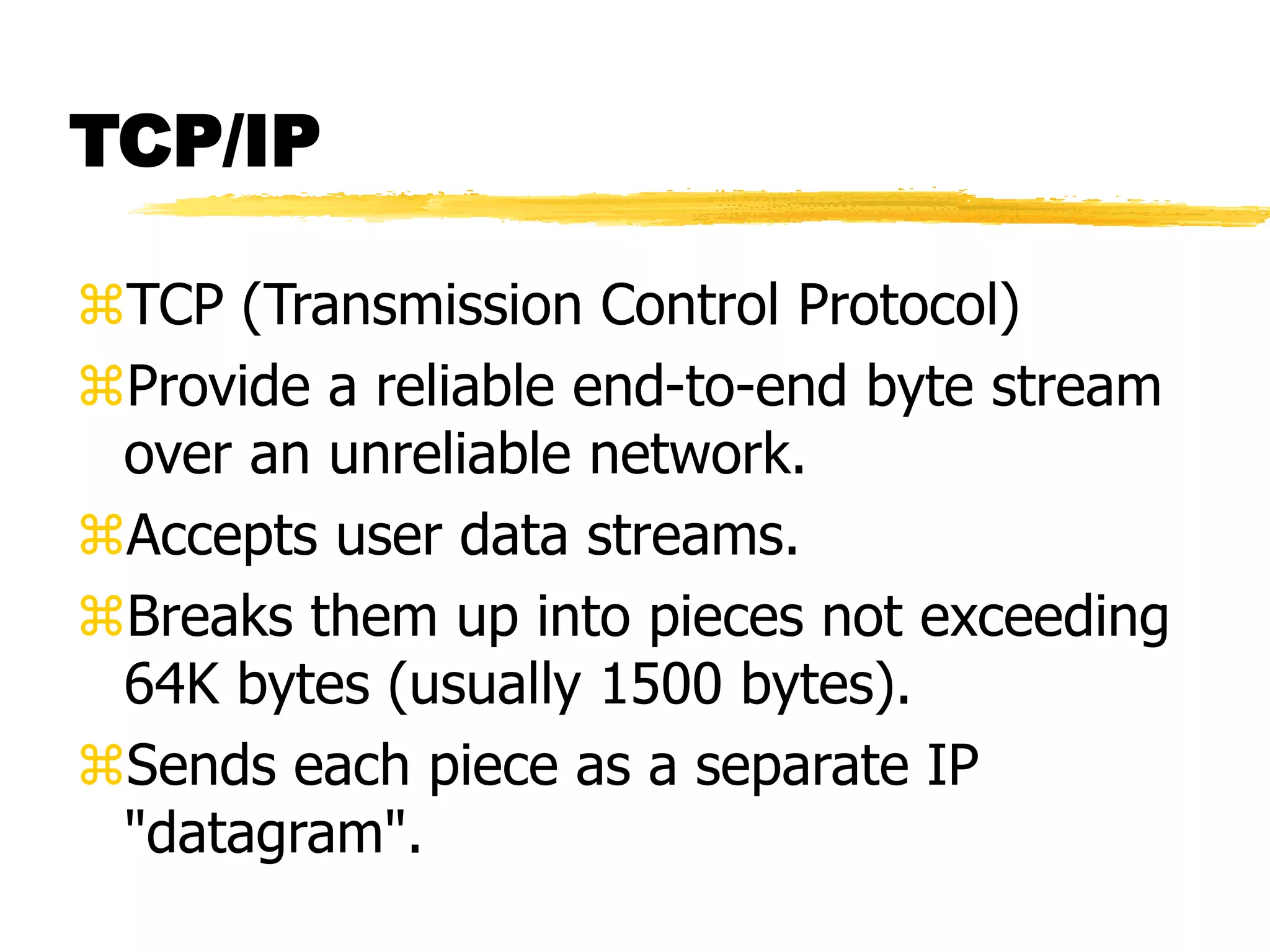
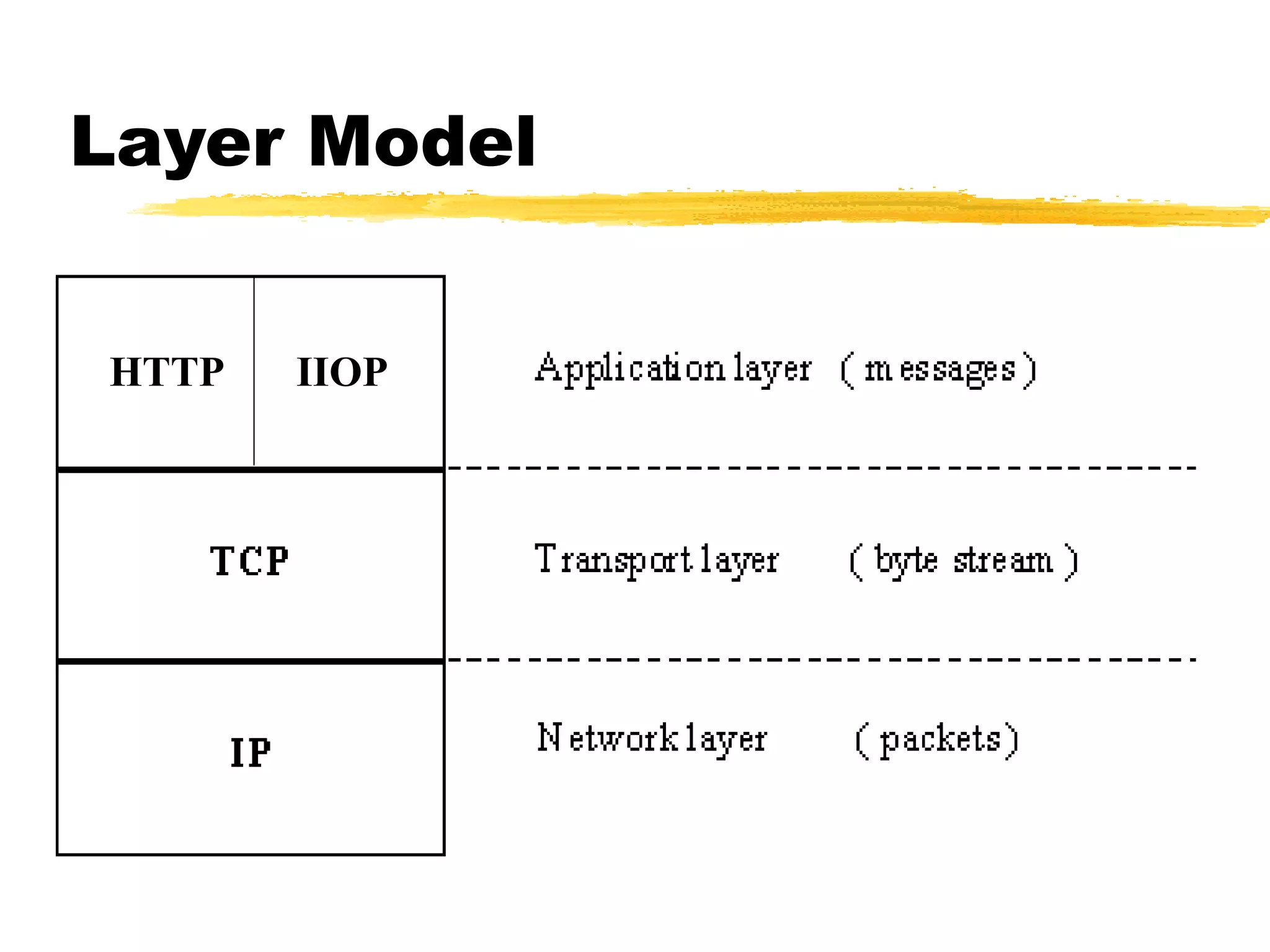
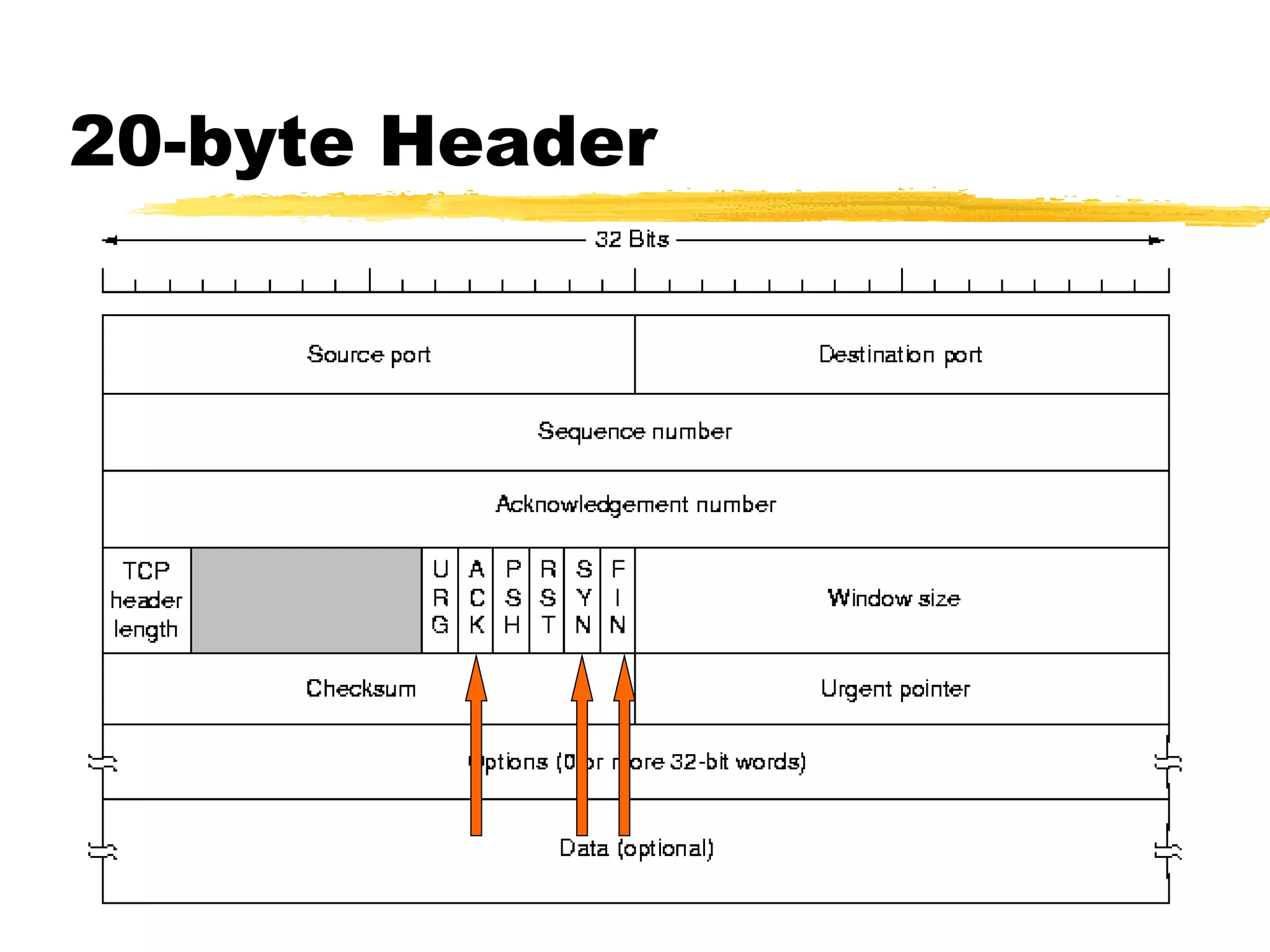
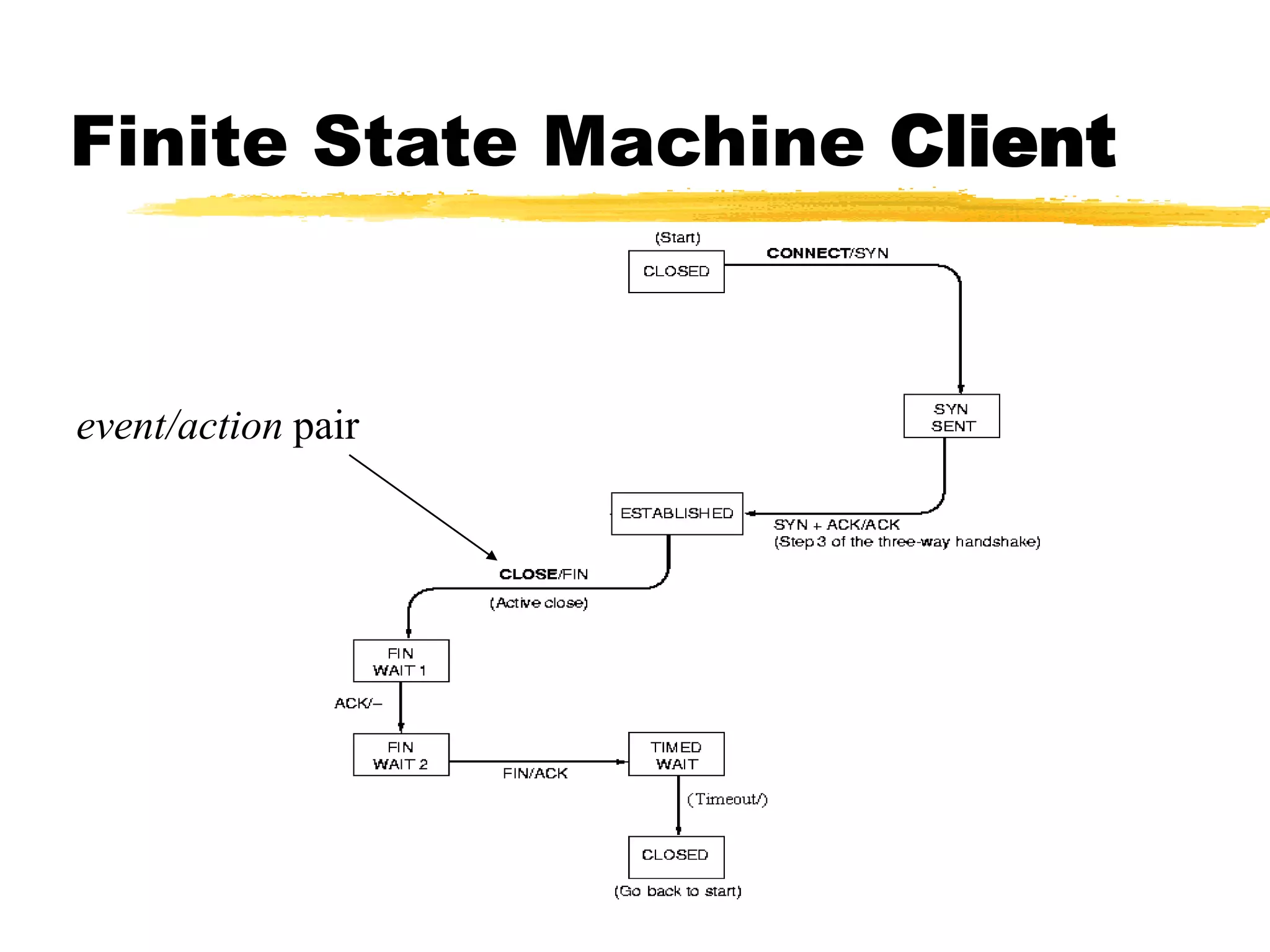
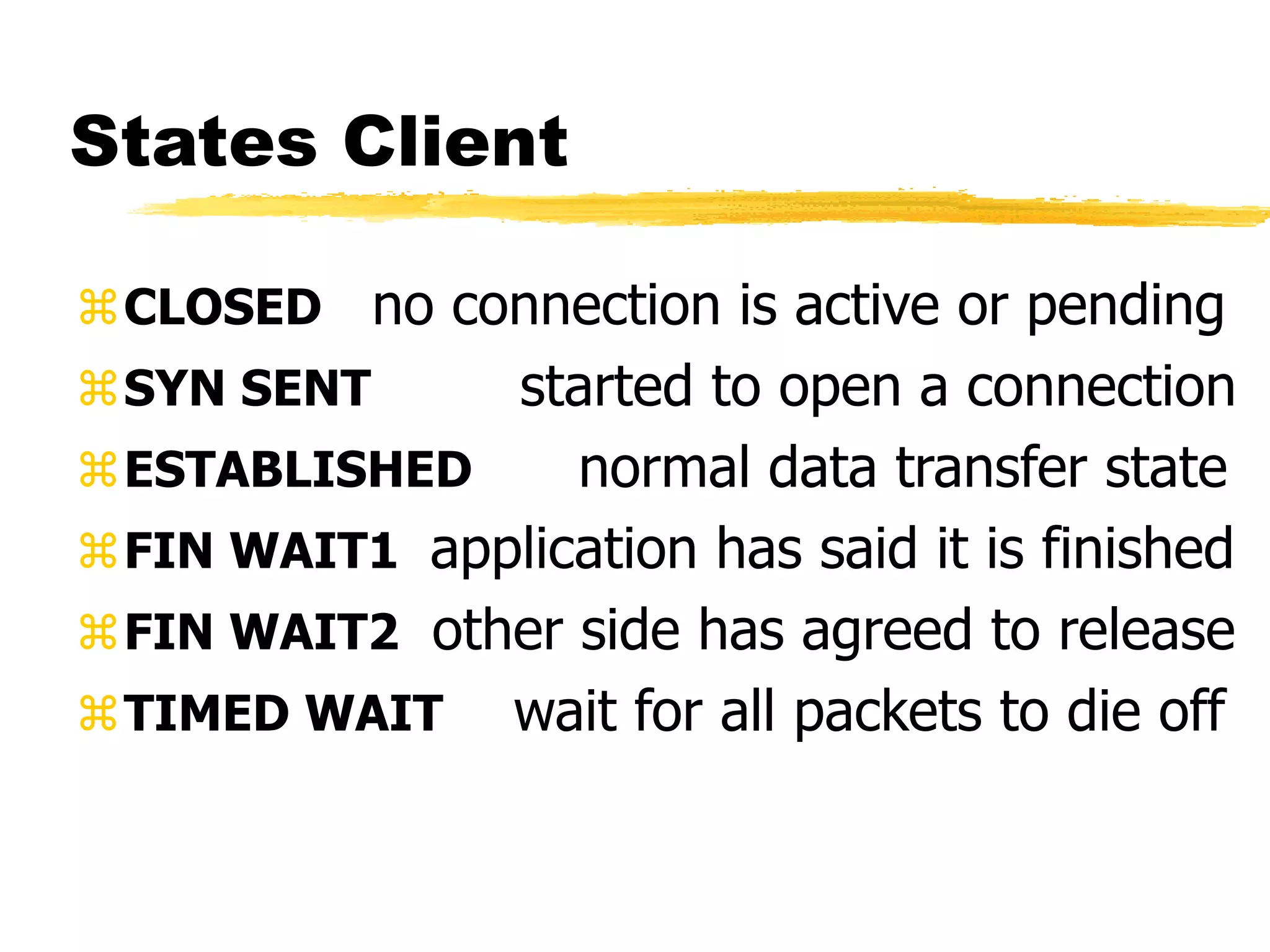
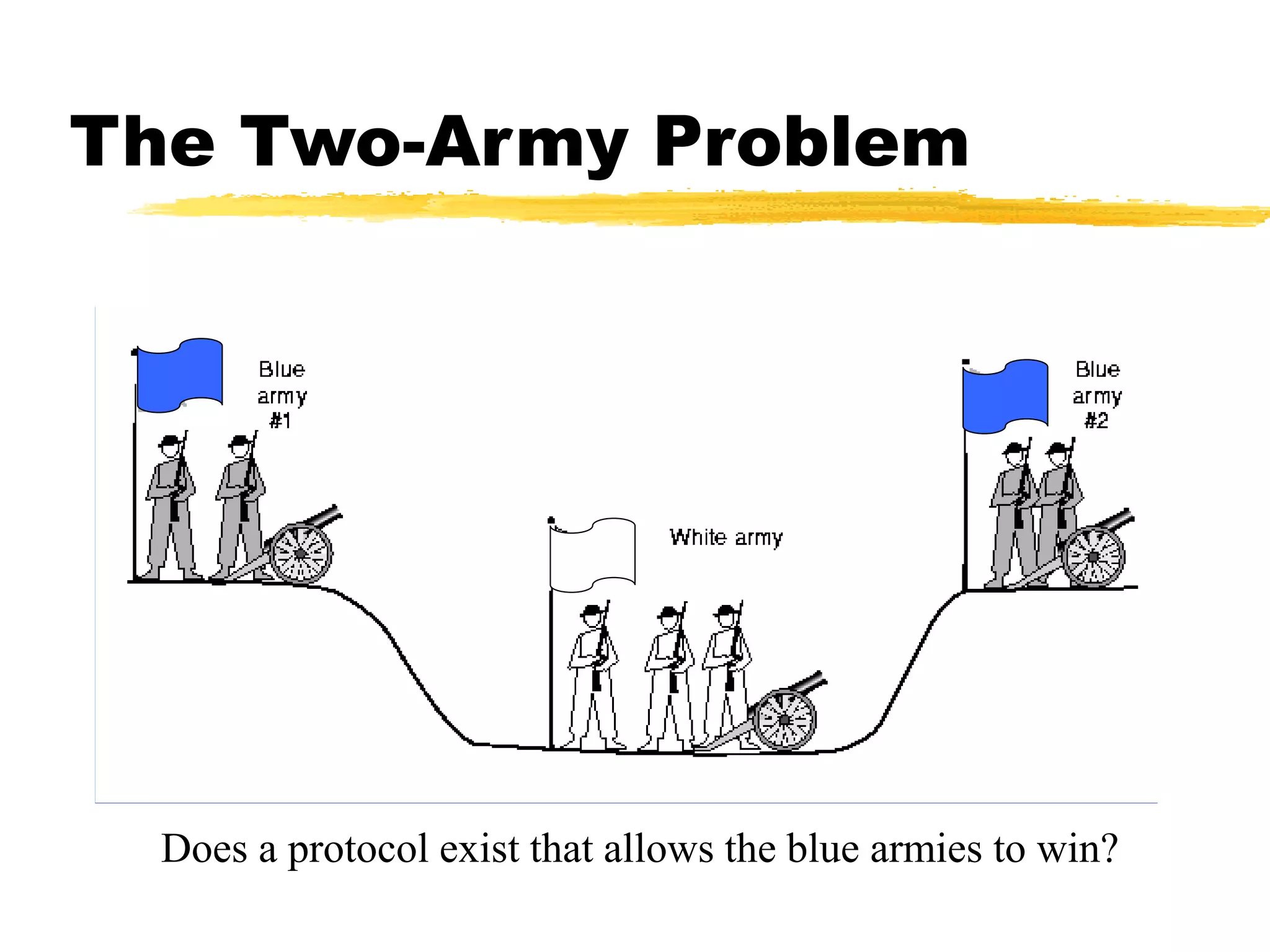
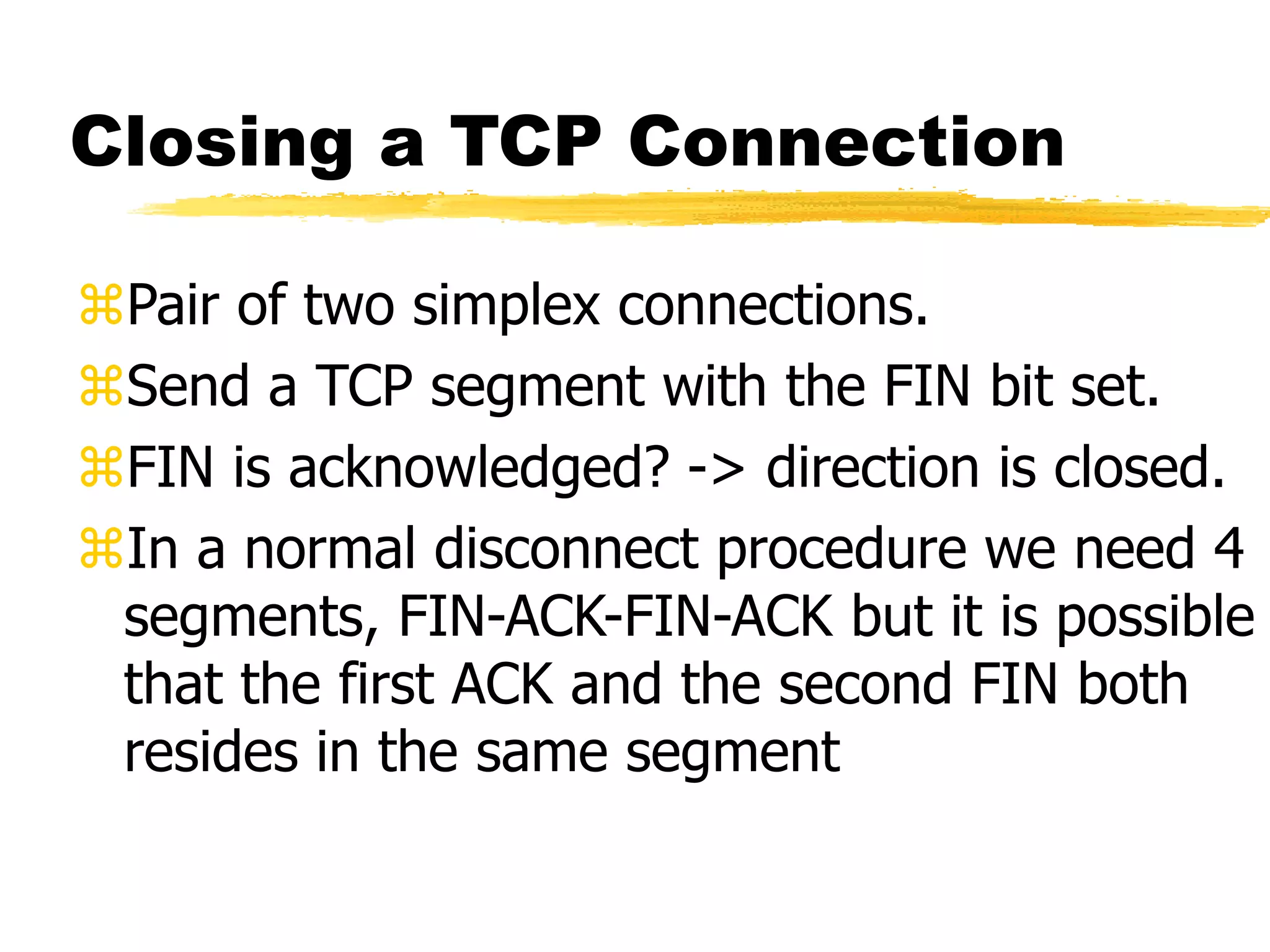
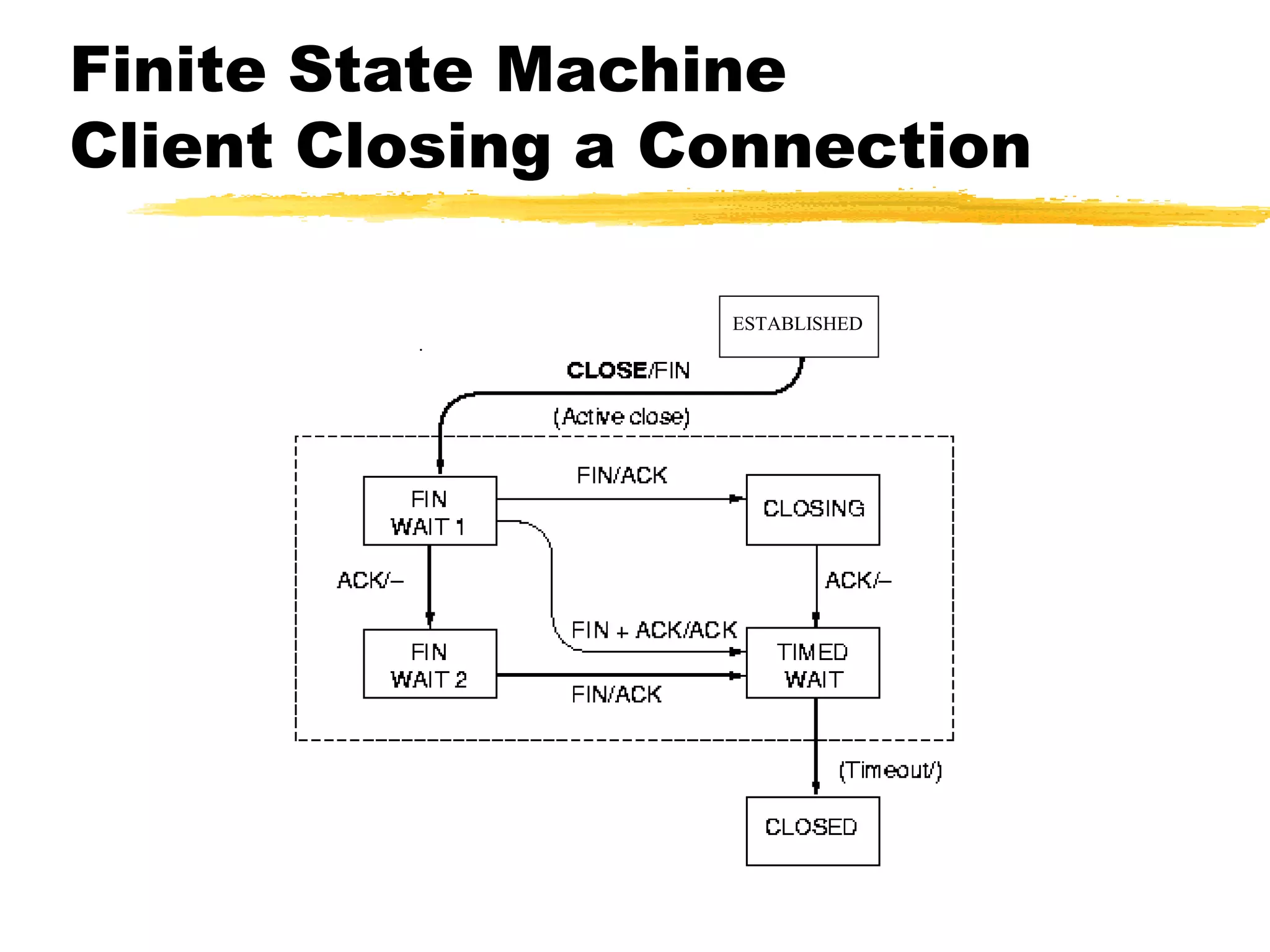
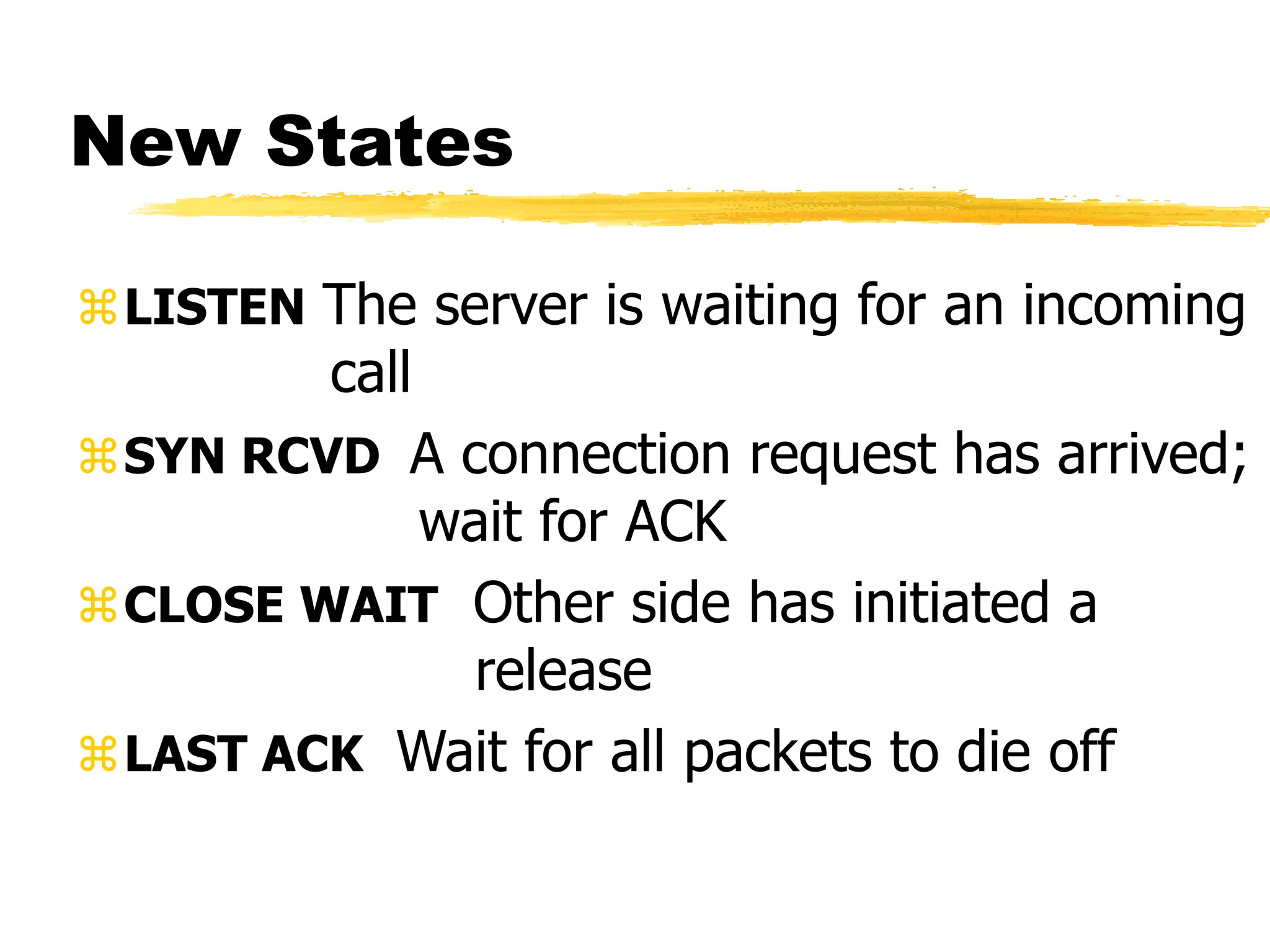
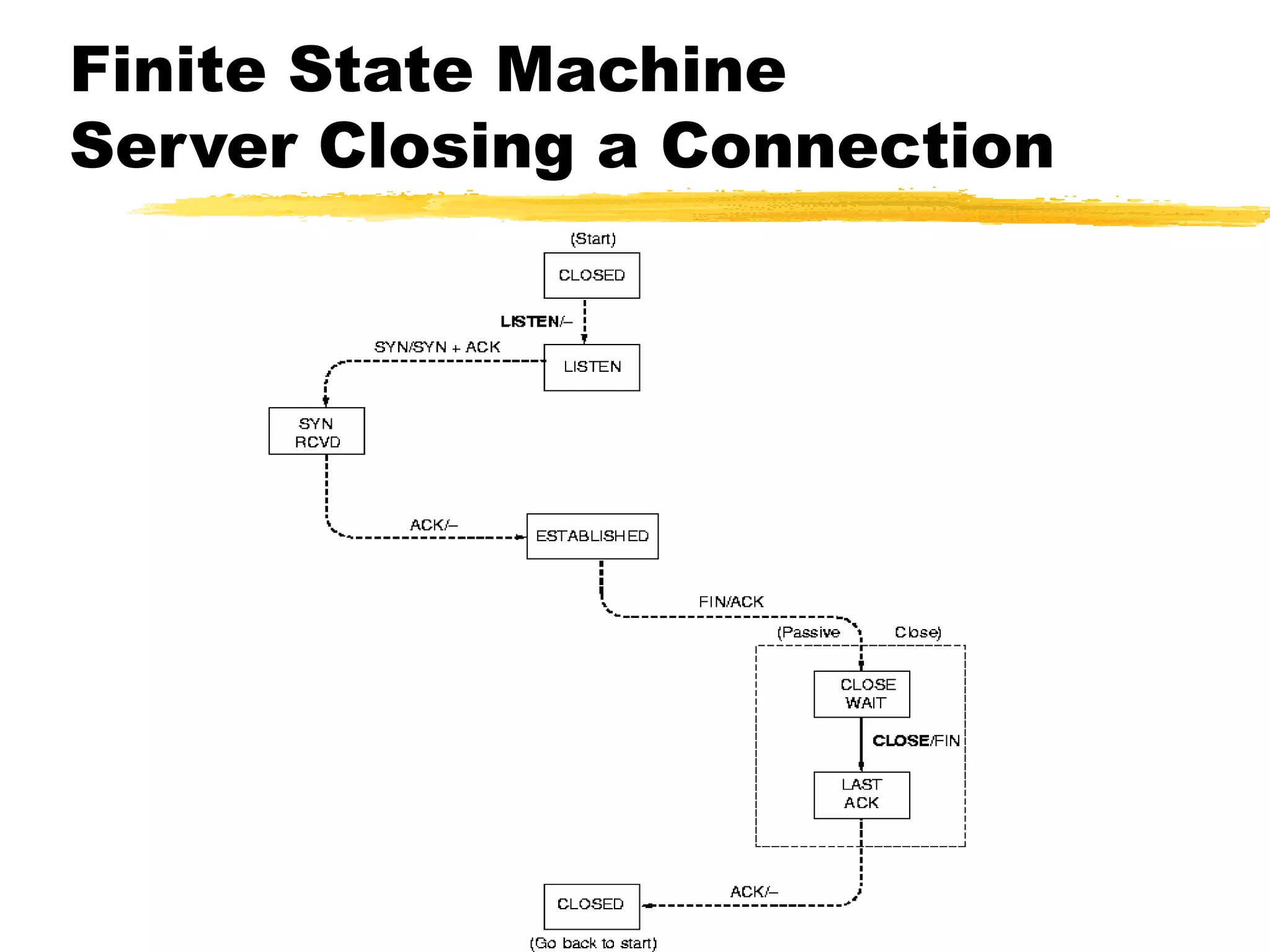
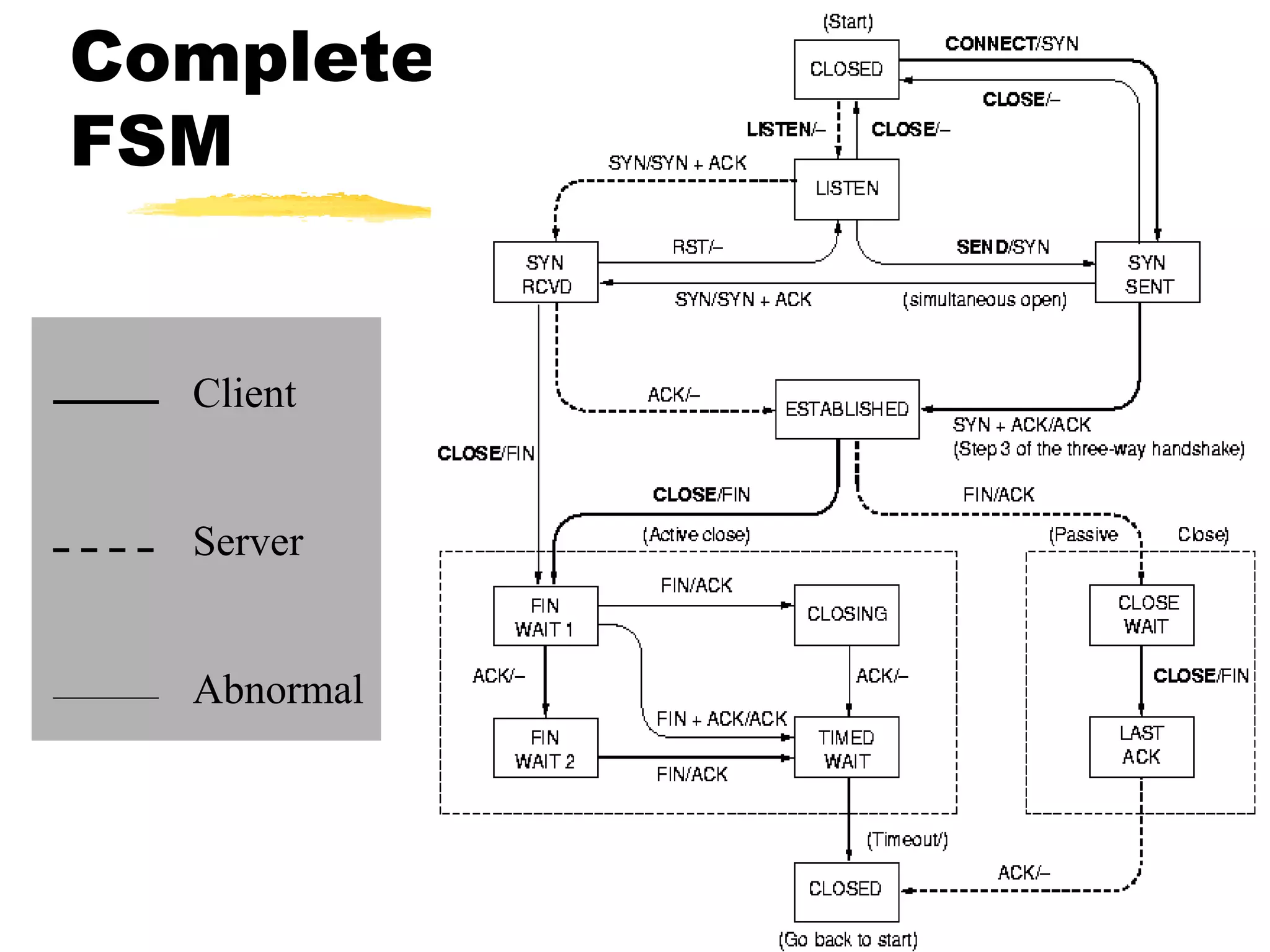
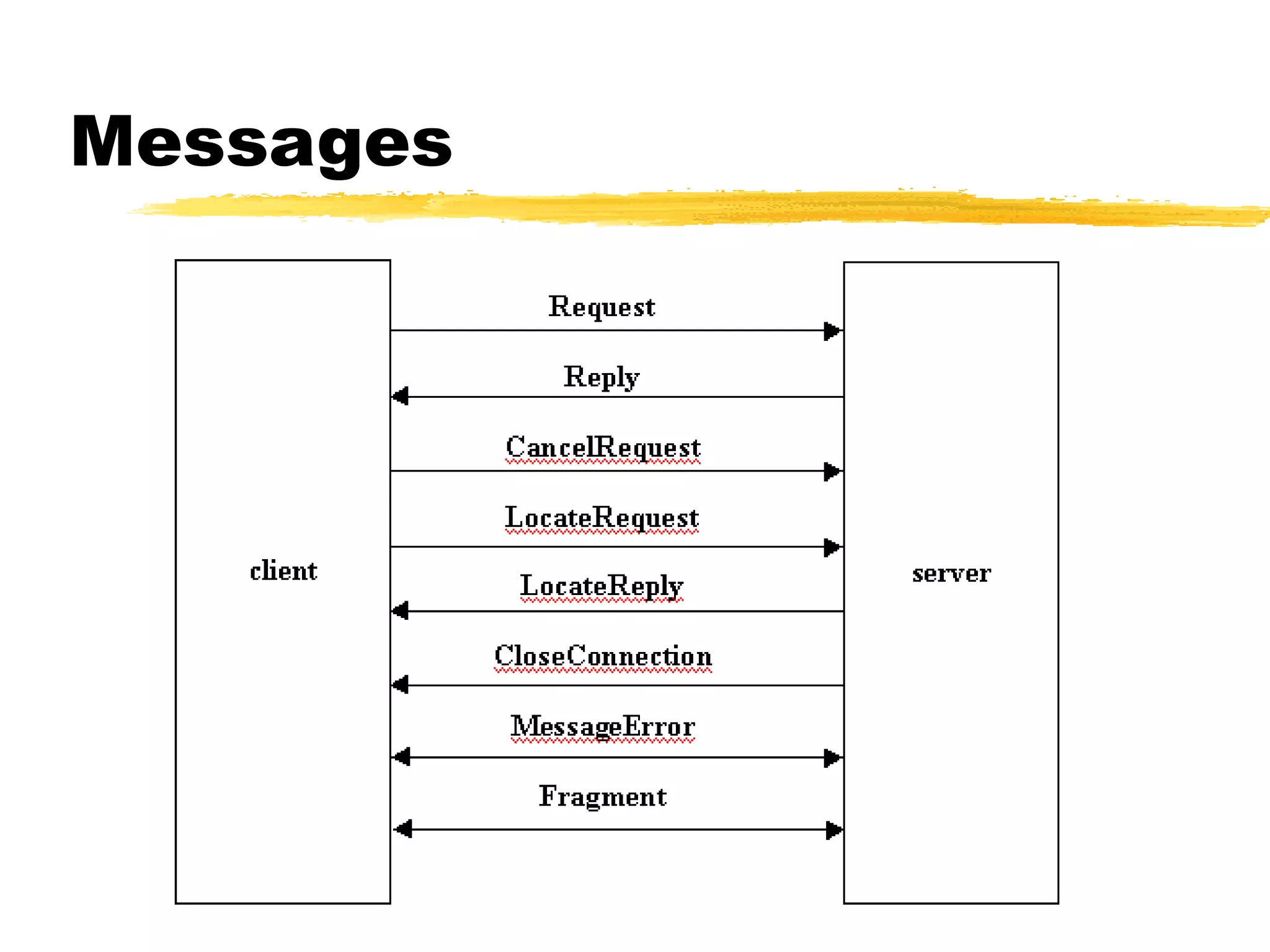
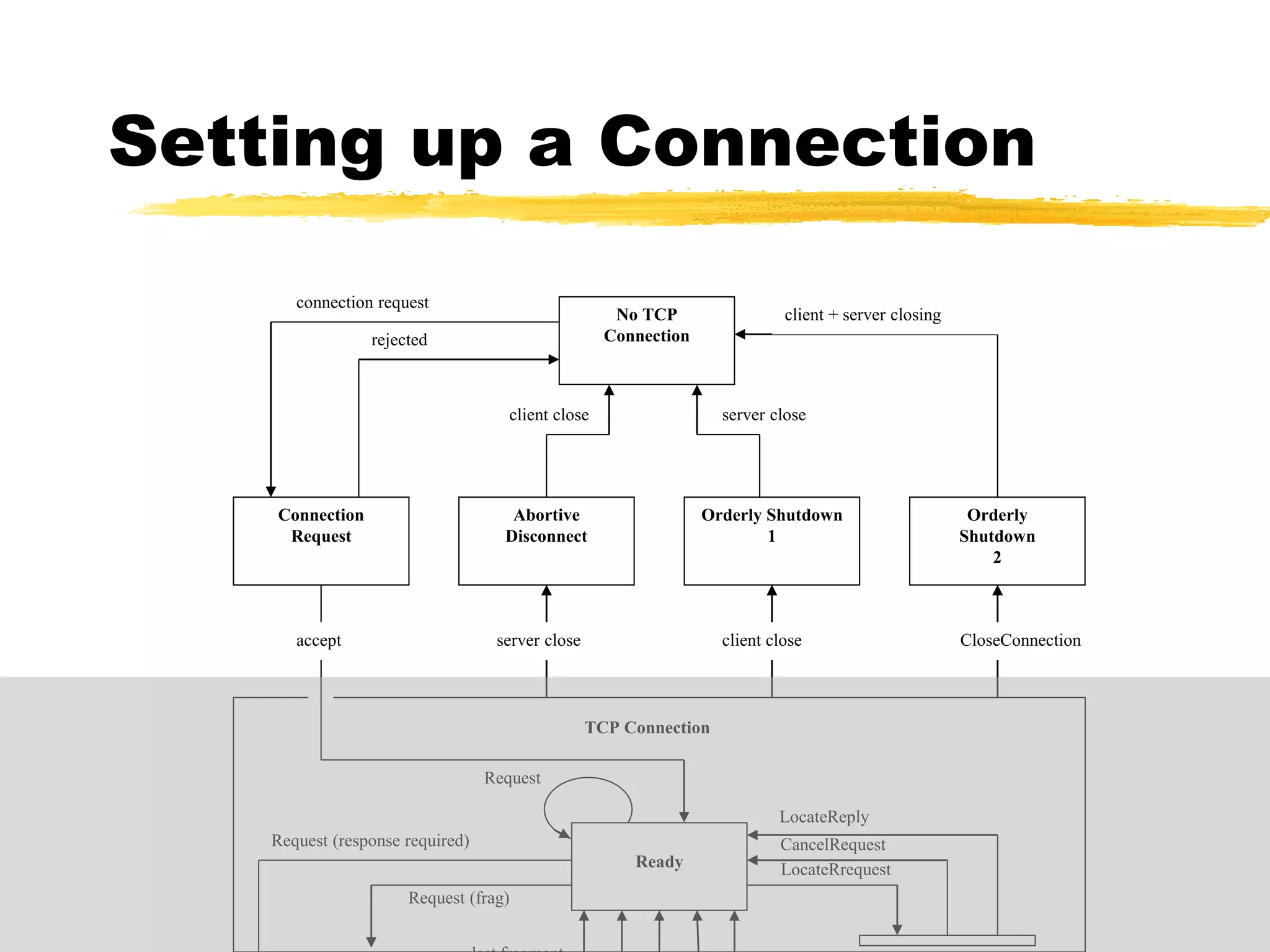
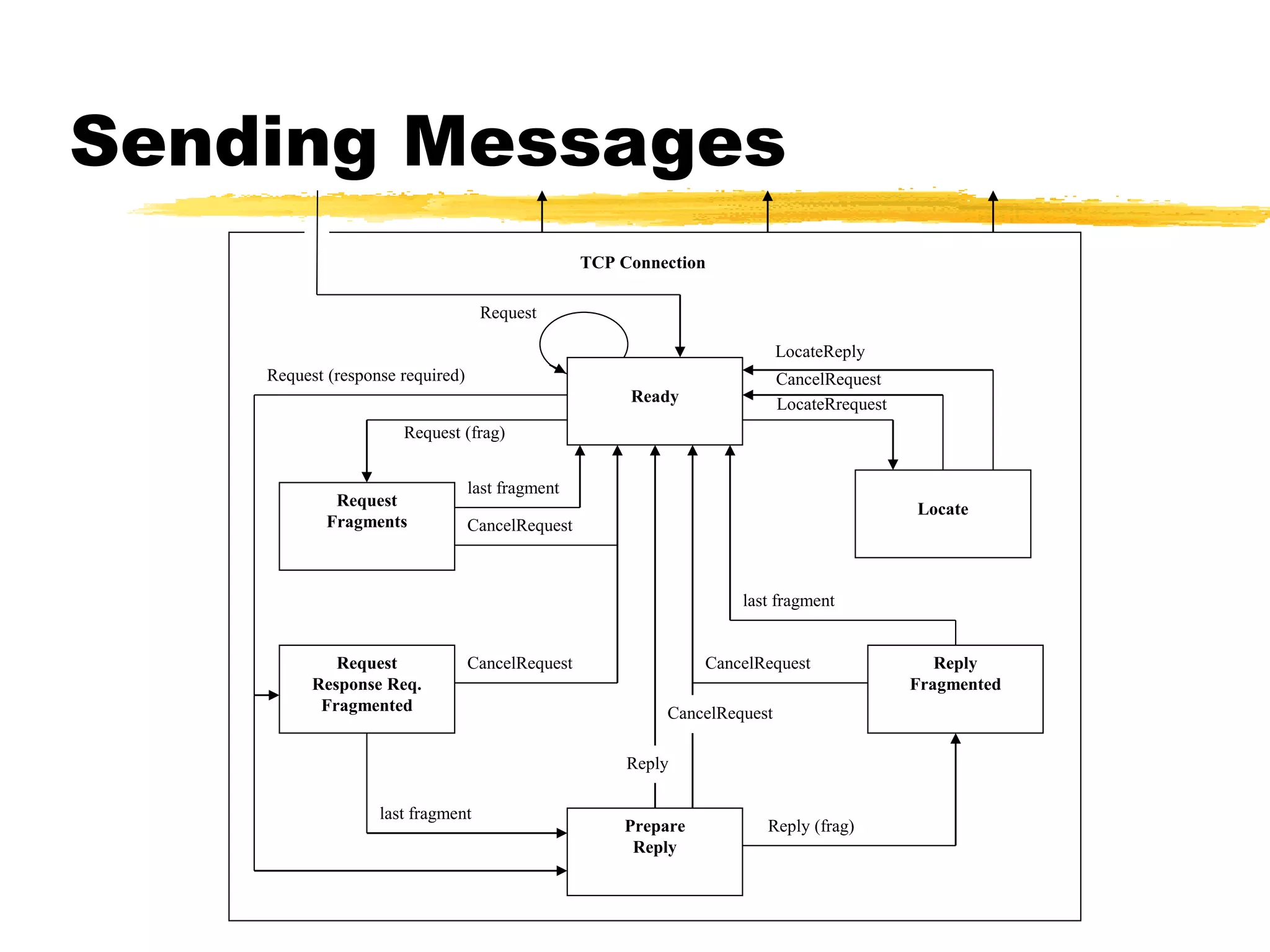
This document provides an overview of CORBA (Common Object Request Broker Architecture) and IIOP (Internet Inter-ORB Protocol). It discusses how CORBA allows distributed objects to communicate by defining standard protocols like IIOP that uses TCP/IP. It also explains key CORBA concepts like IDL (Interface Definition Language) for defining object interfaces, ORBs (Object Request Brokers) that allow communication between objects, and how IIOP maps CORBA messages to TCP.