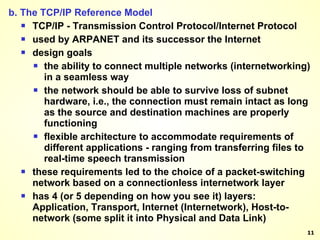
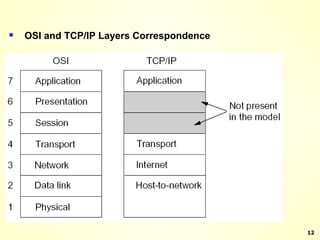
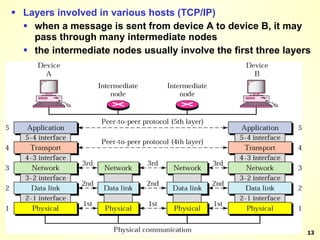
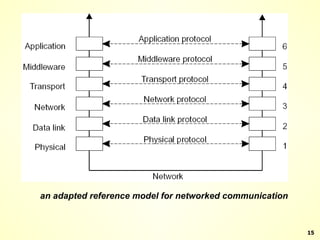
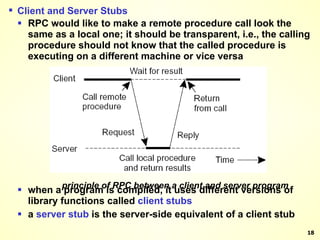
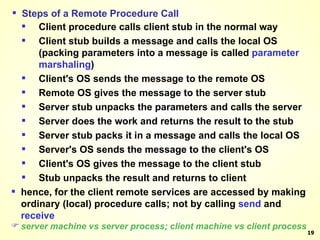
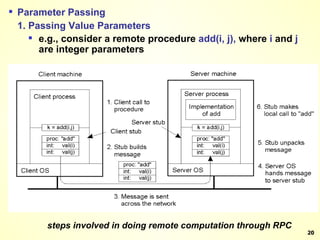
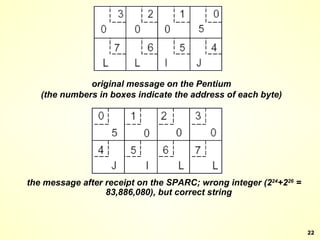
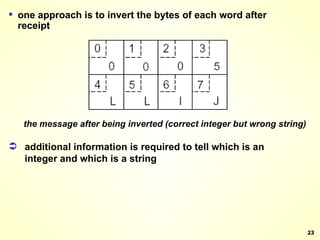
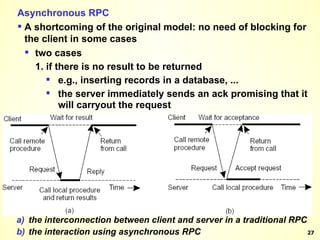
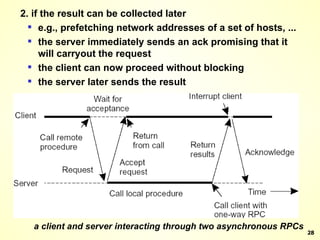
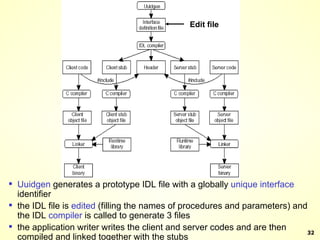
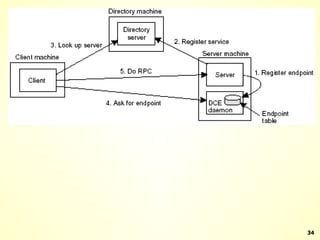
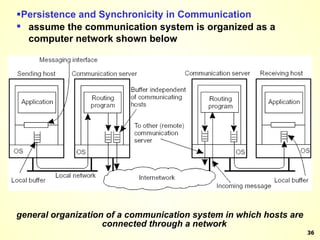
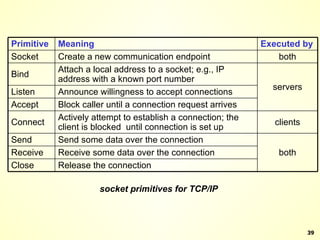
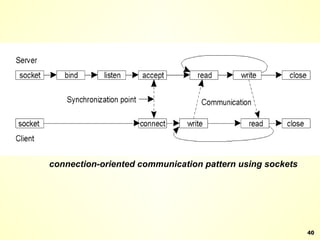
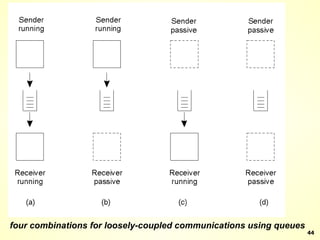
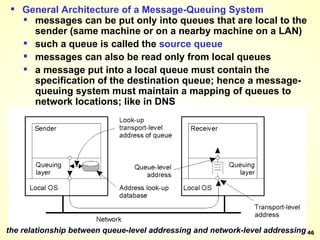
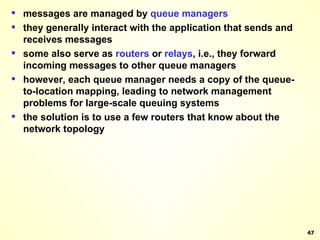
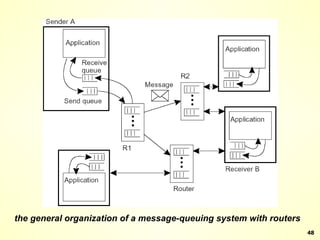
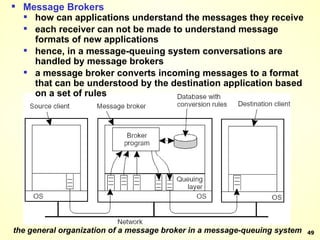
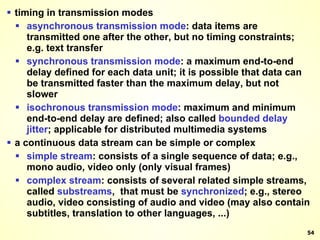
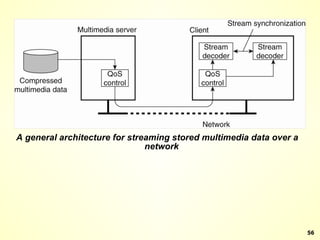
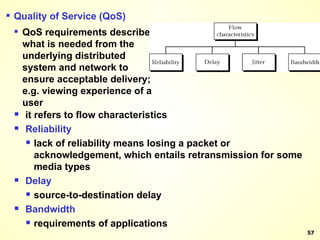
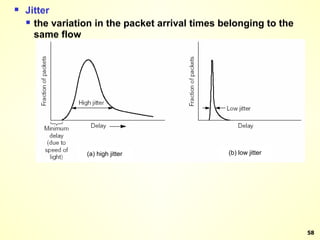
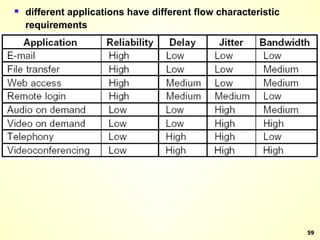
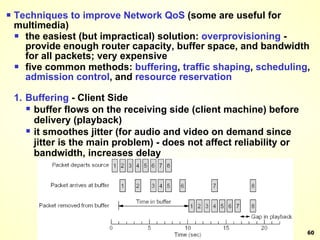
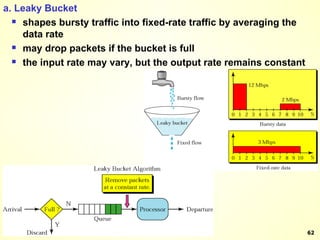
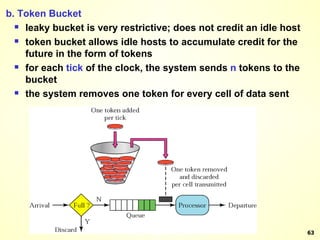
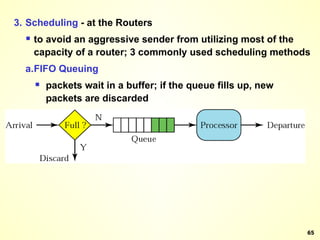
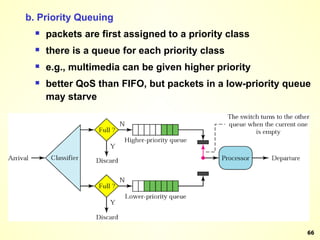
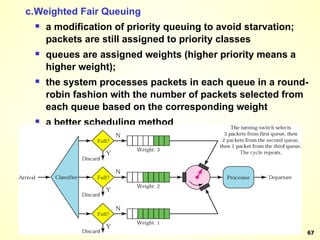
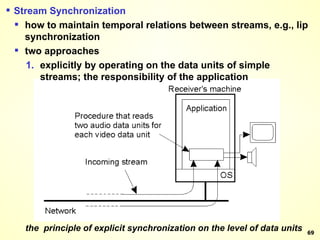
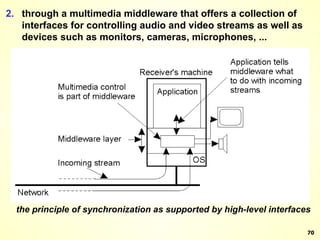
The document discusses interprocess communication in distributed systems. It introduces four widely used communication models: remote procedure call (RPC), message-oriented middleware (MOM), stream-oriented communication, and multicast communication. RPC allows processes to call procedures located on other machines transparently. MOM supports persistent asynchronous communication through message queues.