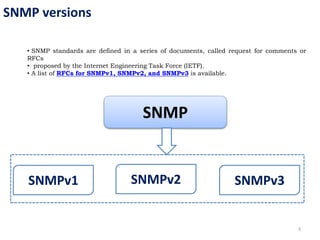
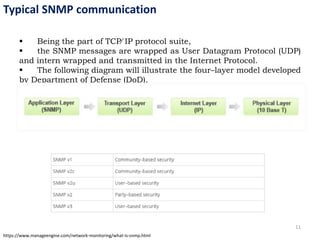
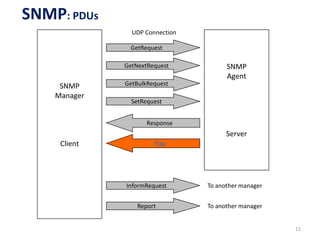
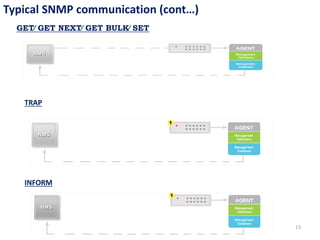
The document provides an overview of the Simple Network Management Protocol (SNMP), detailing its versions (v1, v2, v3) and related RFCs. It covers SNMP's architecture, including manager-agent communication, types of protocol data units (PDUs), and the basic functions of SNMP in network management. Additionally, the document explains how SNMP operates within the TCP/IP protocol suite and includes communication flow examples.