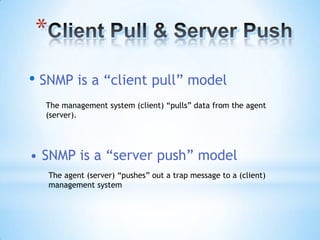
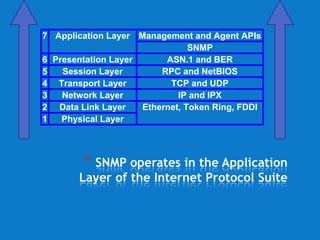
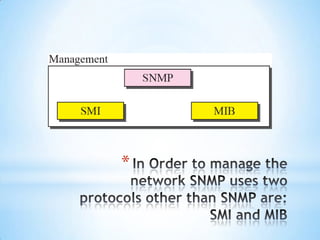
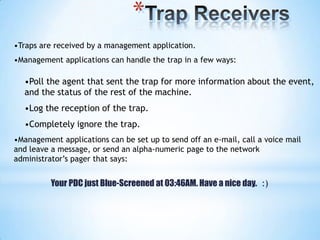
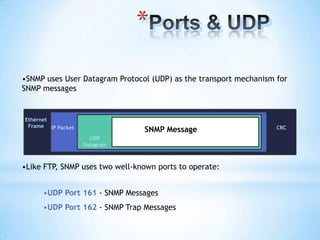
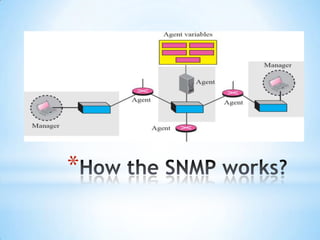
SNMP (Simple Network Management Protocol) enables remote management of network devices via agents and managers. It includes operations like 'get', 'set', and 'trap', and utilizes a structured format for managing information through MIB and SMI. SNMP employs UDP for message transport and operates through various node types, including managed and management nodes, with options for proxy agents to extend its capabilities.