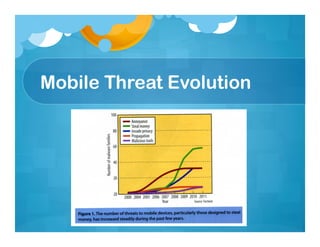
Mobile devices offer many useful applications and functions, but also come with privacy and security risks. Personal information and location data can potentially be accessed by hackers, corporations, or the government. Threats include malware, botnets, and vulnerabilities in apps, social networks, and wireless technologies. Users should secure their devices with antivirus software, encryption, passwords, and remote wiping capabilities. While perfect security is impossible, taking reasonable precautions can help protect against casual theft and privacy risks.