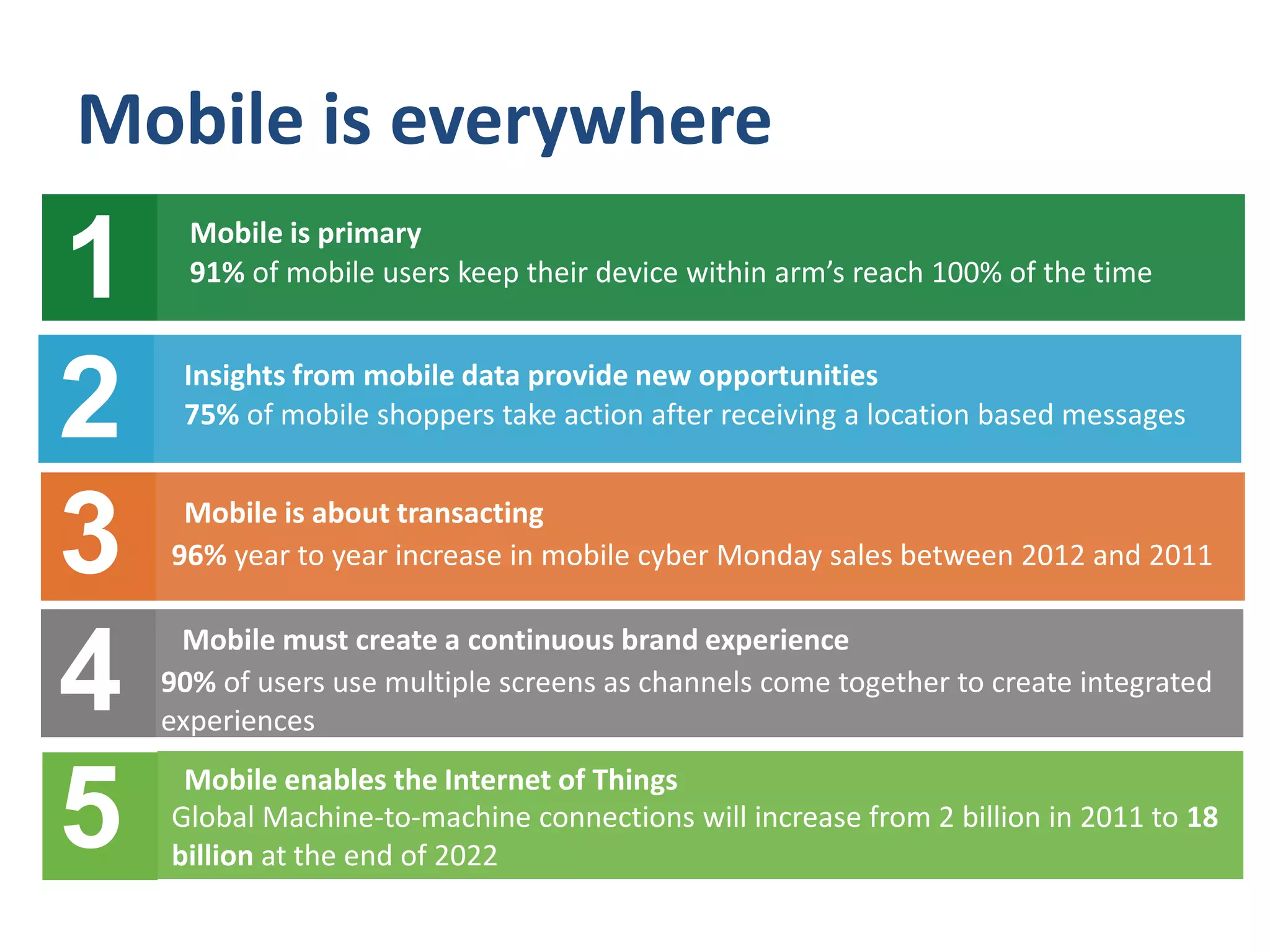
Mobile devices have become integral for communication and personal information storage, making them valuable yet vulnerable to security threats. Key risks include device theft, phishing scams, malware, and insecure Wi-Fi networks, which can lead to identity theft and unauthorized access to personal data. To mitigate these risks, users are advised to implement safety measures such as using PINs, installing trusted apps, and avoiding unsecured networks.