Skype uses a peer-to-peer architecture where each computer has equal capabilities as both a client and server. It allows for voice and video calls over the internet using protocols like SIP and RTP. Skype employs a hybrid P2P model with supernodes to decentralize functions like user search and directory sharing. Calls between Skype users can happen directly or through relays if behind firewalls, while connections to regular phones use SkypeOut gateways.





![tries to establish a TCP connection with each of the seven Skype maintained
default SNs IP address on port 33033.
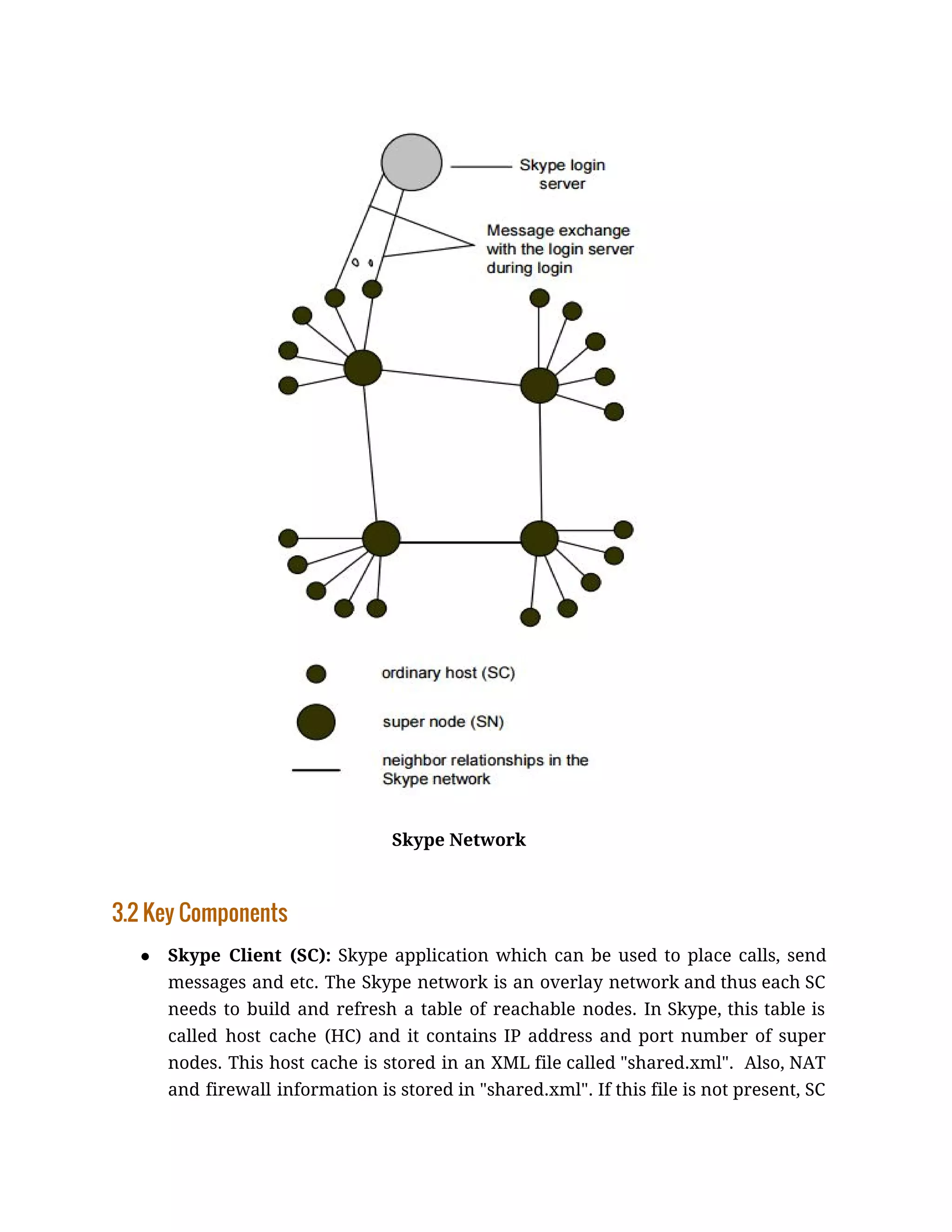
● Super Node (SN): Super nodes are the endpoints where Skype clients connect
to. Any node with a public IP address having sufficient CPU, memory, and
network bandwidth is a candidate to become a super node and a Skype client
cannot prevent itself from becoming a super node. Also, if a SC cannot establish
a TCP connection with a SN then it will report a login failure.
● Skype Authentication Server: This is the only centralized Skype server which
is used to authenticate Skype users. An authenticated user is then announced to
other peers and buddies. If the user saves his/her credentials, authentication
will not be necessary. This server (IP address: 212.72.49.141 [Buddy list] or
195.215.8.141) also stores the buddy list for each user. Note that the buddy list is
also stored locally in an unencrypted file called "config.xml". In addition, if two
SCs have the same buddy, their corresponding config.xml files have a different
four-byte number for the same buddy. Finally, it has been shown that Skype
routes login messages through SNs if the authentication server is blocked.
● Start of Message (SoM) Structure: Skype uses the same port to communicate
with the outside world. Therefore, it needs an unencrypted structure in the
beginning of each UDP packet to analyze the sequence and the flows at the
application layer. This structure is called SoM.
3.3 Skype Connections
● Skype to Skype (End to End) (E2E)
Call signalling and media transfer
1. If both caller and receiver are on public IPs and receiver is in the buddy
list of the caller, then they establish a call through a direct TCP
connection with each other and transfer media using UDP.
2. If the caller or receiver is behind a port-restricted NAT then they
establish a call through a few packets initially transferred between](https://image.slidesharecdn.com/skype-161119215913/75/Skype-7-2048.jpg)


