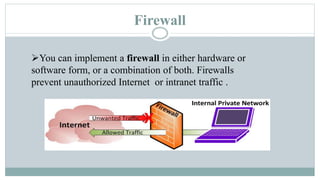
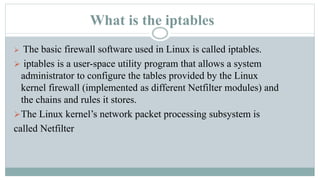
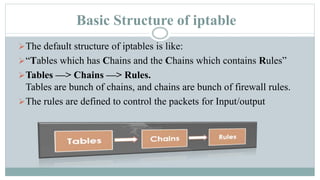
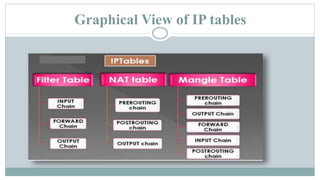
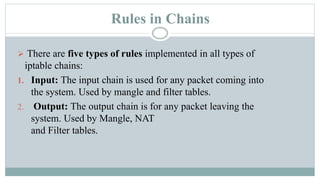
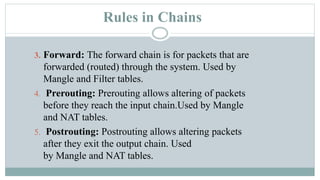
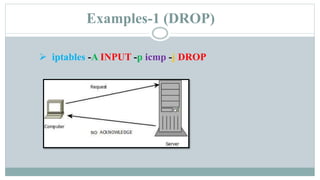
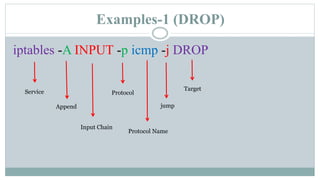
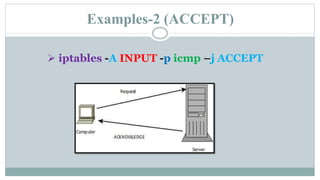
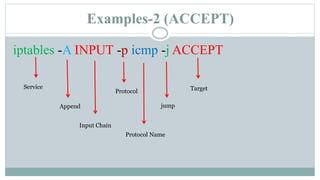
This document provides an overview of iptables in Linux. Iptables is the user-space utility that allows configuration of Linux's built-in netfilter firewall. It can be used to filter packets, perform network address translation, and mangling packets. Iptables uses tables, chains, and rules to examine packets and determine whether to accept, drop, reject, or log them. Examples are provided of rules that drop or accept ICMP packets on the INPUT chain.