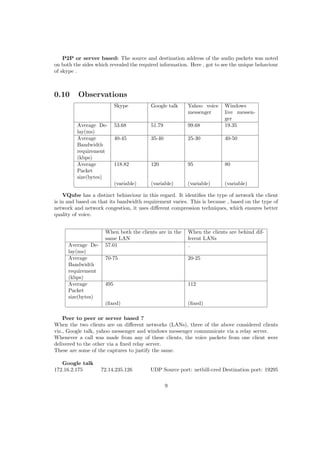
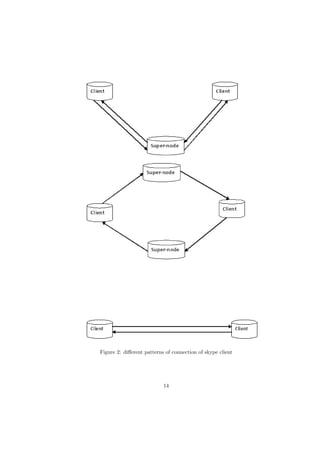
This document summarizes the study of parameters that determine the quality of service of various Voice over IP (VoIP) clients. The study measured parameters like bandwidth requirement, delay, packet size and observed how clients behaved under different network conditions. Key findings were that bandwidth, jitter, latency and packet loss most affected quality of service. The VoIP clients tested included Google Talk, Skype, VQube, Windows Live Messenger and Yahoo Voice Messenger. Network Address Translation (NAT) types and Simple Traversal of UDP through NAT (STUN) were also explained.