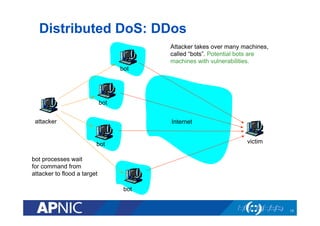
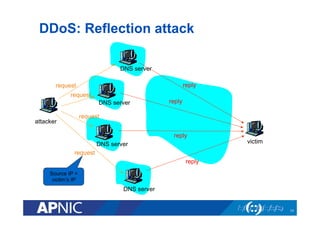
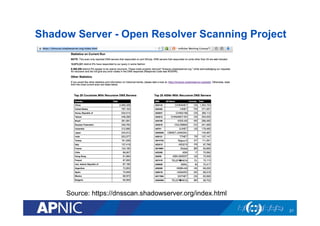
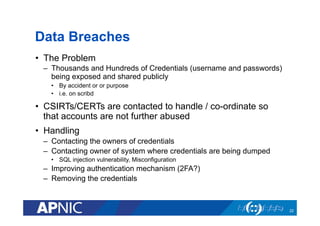
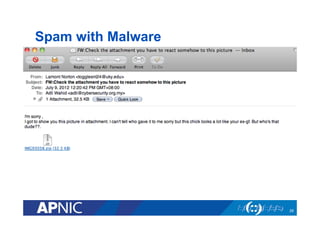
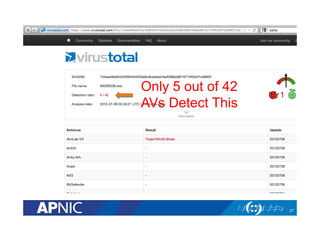
The document outlines the essential framework for setting up Computer Security Incident Response Teams (CSIRTs), emphasizing the importance of understanding the cyber threat landscape, incident handling processes, and collaboration within organizations. It details various types of cyber threats, including malware, phishing, and data breaches, while providing insights into incident response strategies and tools necessary for effective management. The document also stresses the need for continuous learning, cooperation with law enforcement, and proper resource allocation to enhance cybersecurity measures.





























![Incident Response vs. Incident Handling?
• Incident Response is all of the technical components
required in order to analyze and contain an incident.
– Skills: requires strong networking, log analysis, and forensics skills.
• Incident Handling is the logistics, communications,
coordination, and planning functions needed in order to
resolve an incident in a calm and efficient manner.
[isc.sans.org]
40](https://image.slidesharecdn.com/setting-up-csirt-publication-edition-140604223541-phpapp01/85/Setting-up-CSIRT-39-320.jpg)