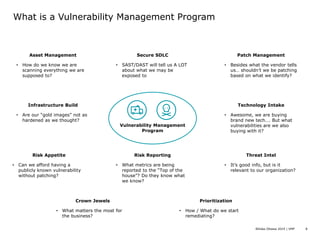
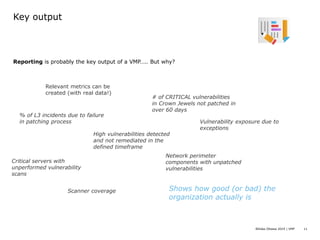
Dennis Chaupis presented on vulnerability management programs. He explained that a VMP involves more than just vulnerability assessments and penetration testing, including asset management, patch management, infrastructure builds, technology intake processes, secure software development, threat intelligence, endpoint security, and defining an organization's risk appetite. A VMP relies on other security processes and aims to formalize how they work together. Key roles in a VMP include the CISO overseeing the program while working with the CIO, CRO, and chief auditor. Important outputs of a VMP are security metrics and reporting that show an organization's vulnerability status.