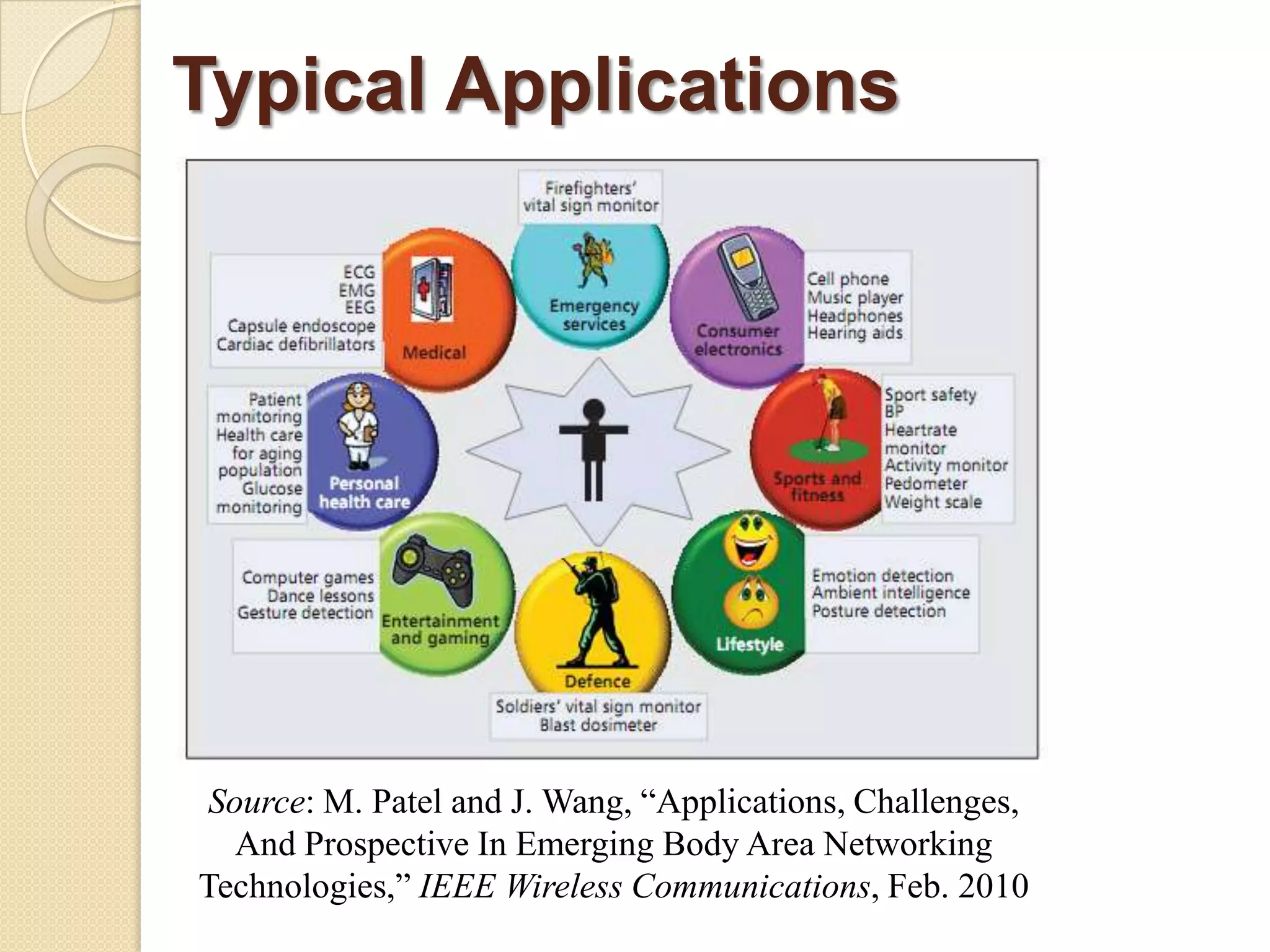
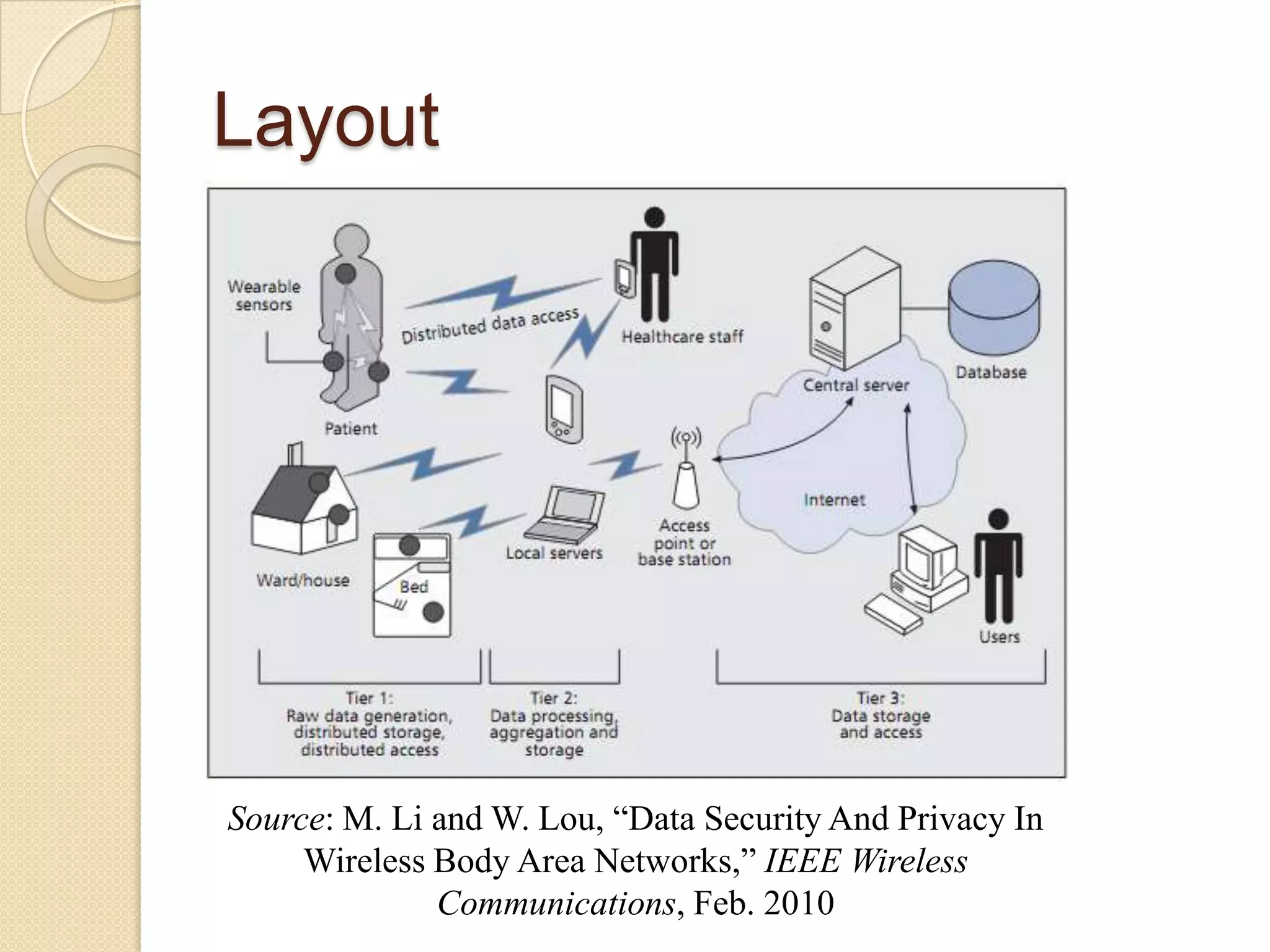
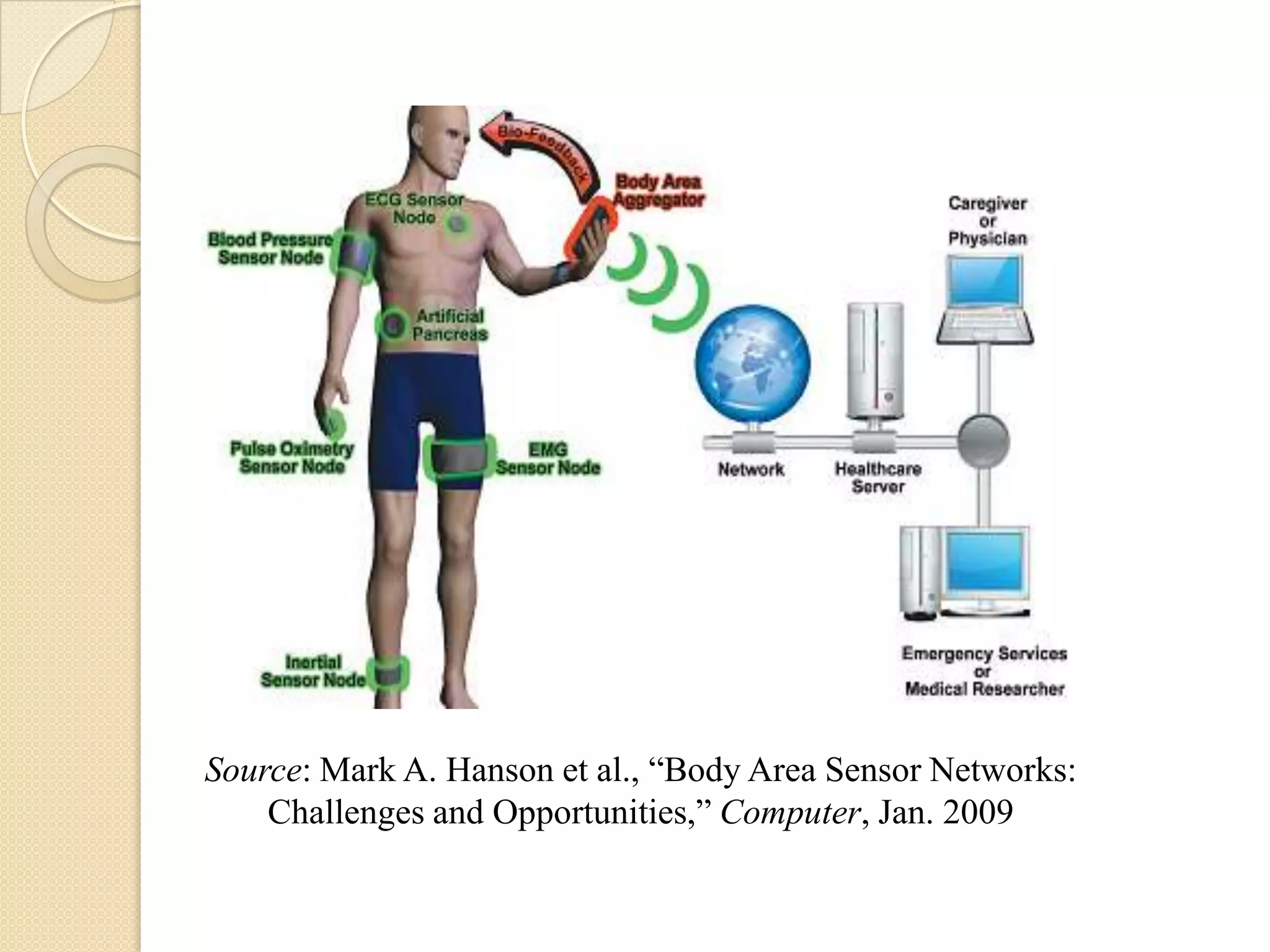
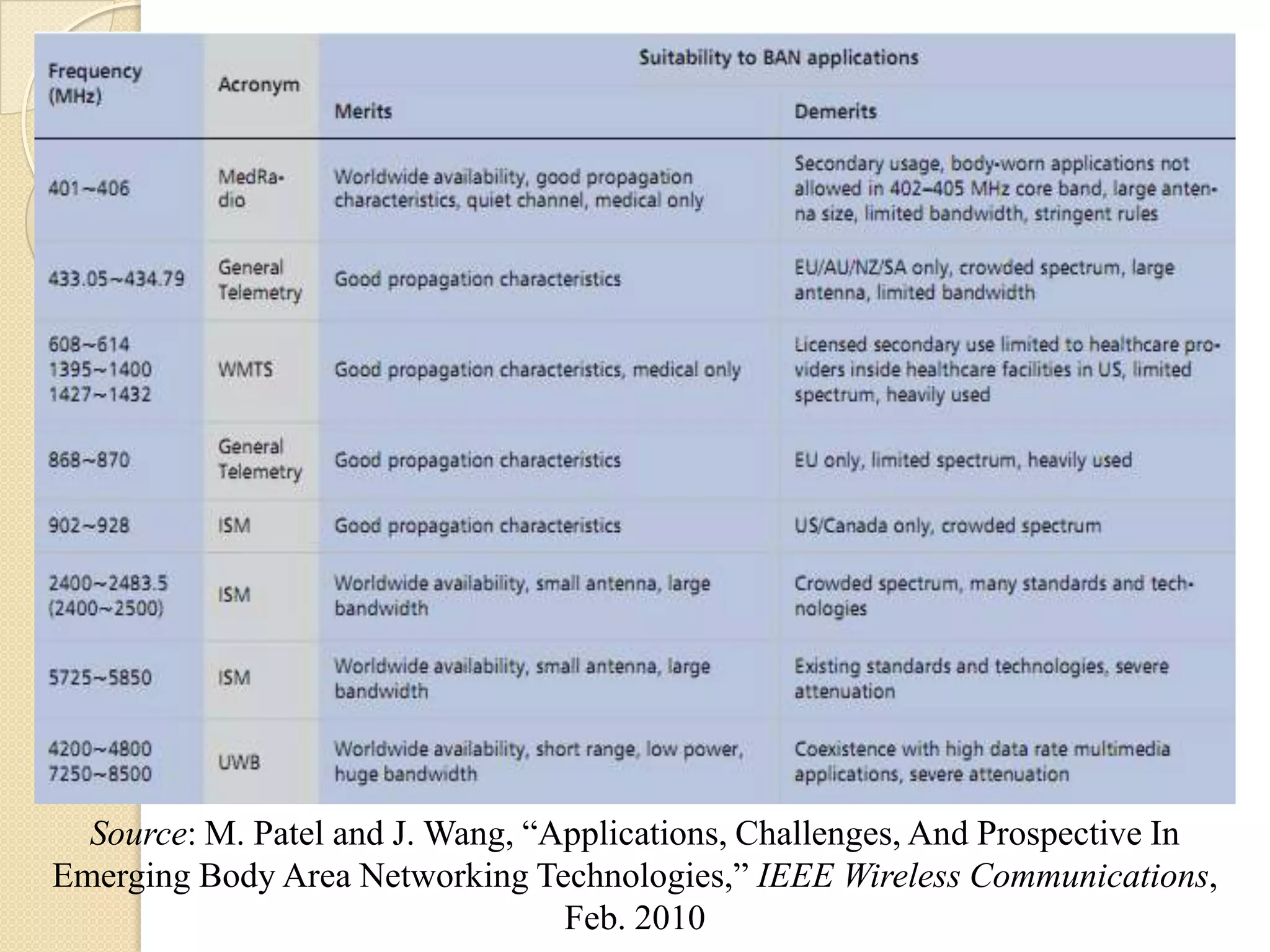
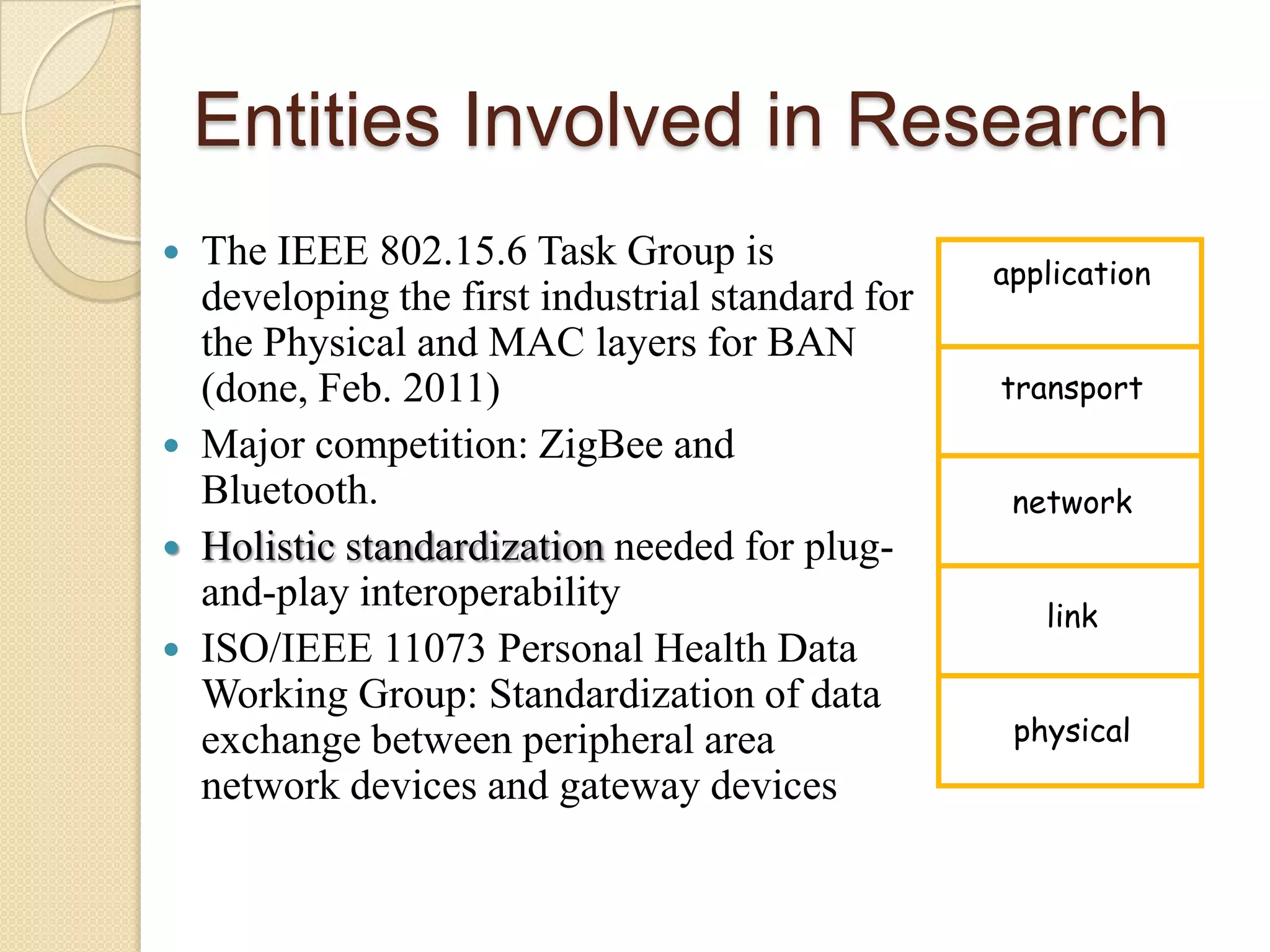
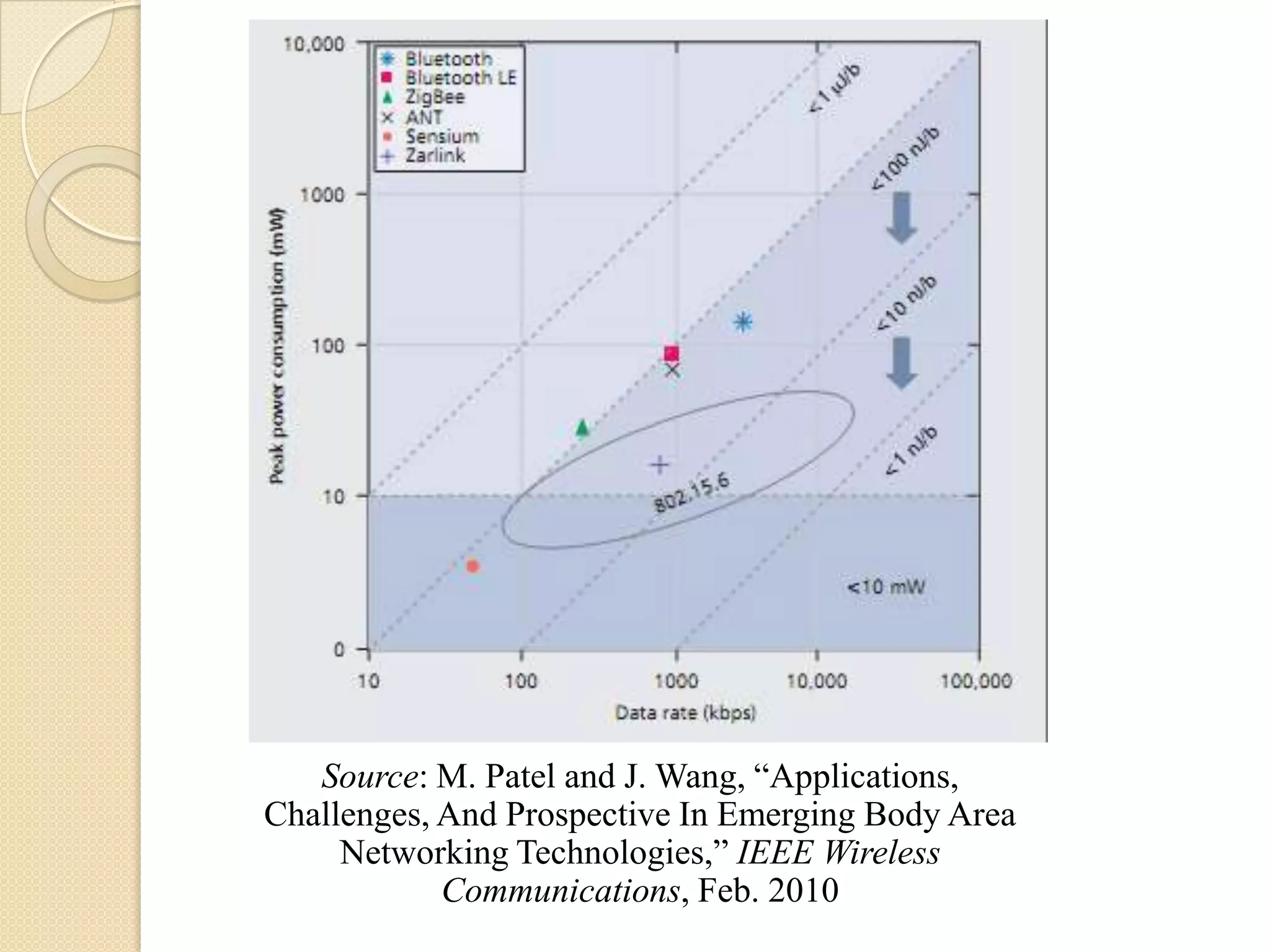
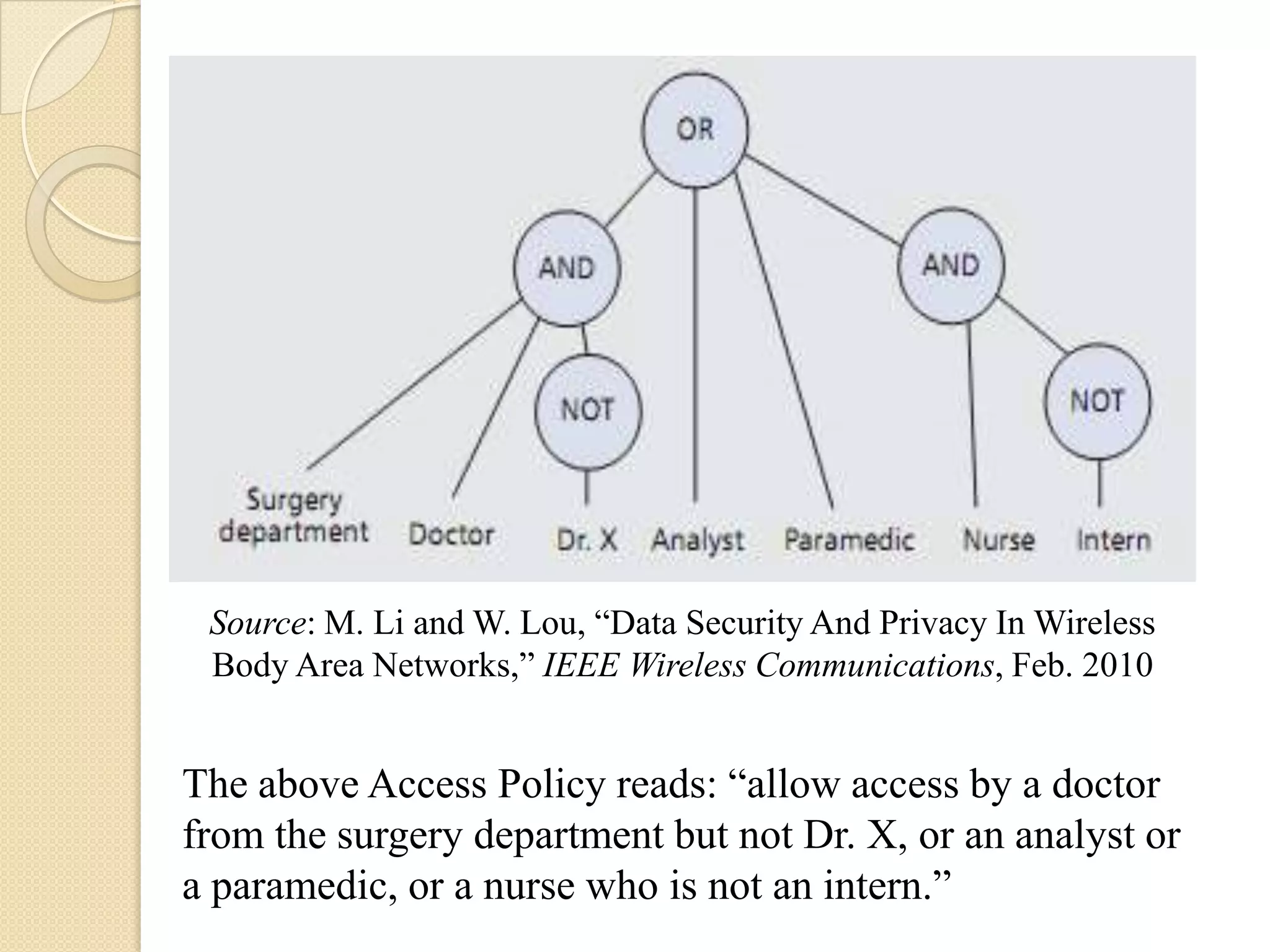
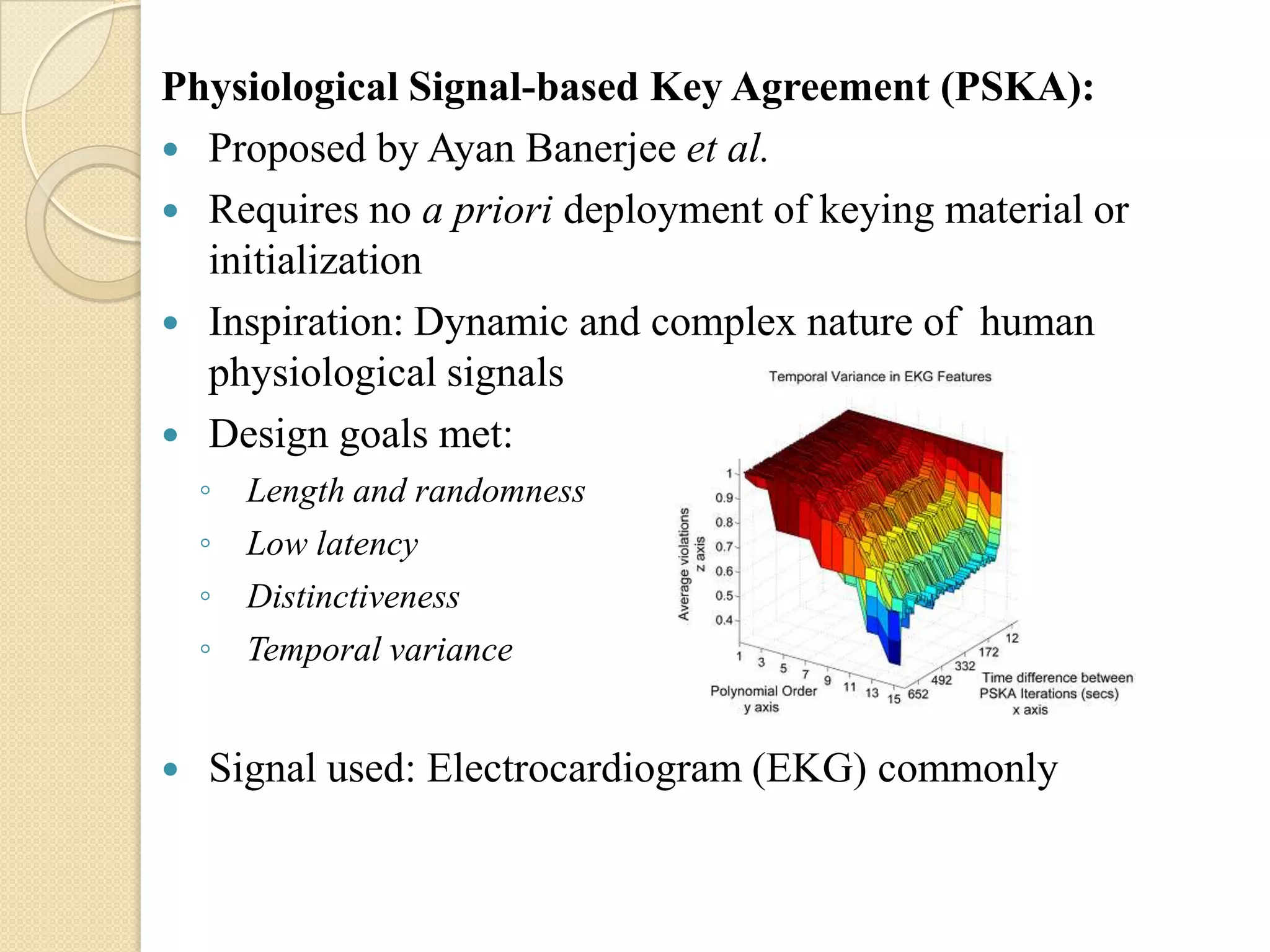
The seminar covered data security, privacy, and applications in emerging body area networks (BANs). Key topics included typical BAN applications in healthcare, research challenges around frequency bands and hardware, and models proposed for secure data storage and access control. Four models were described in detail: one based on redundant residue number systems, one using erasure coding, one using constant data motion, and one using attribute-based encryption to implement fine-grained access control of encrypted health data in BANs.