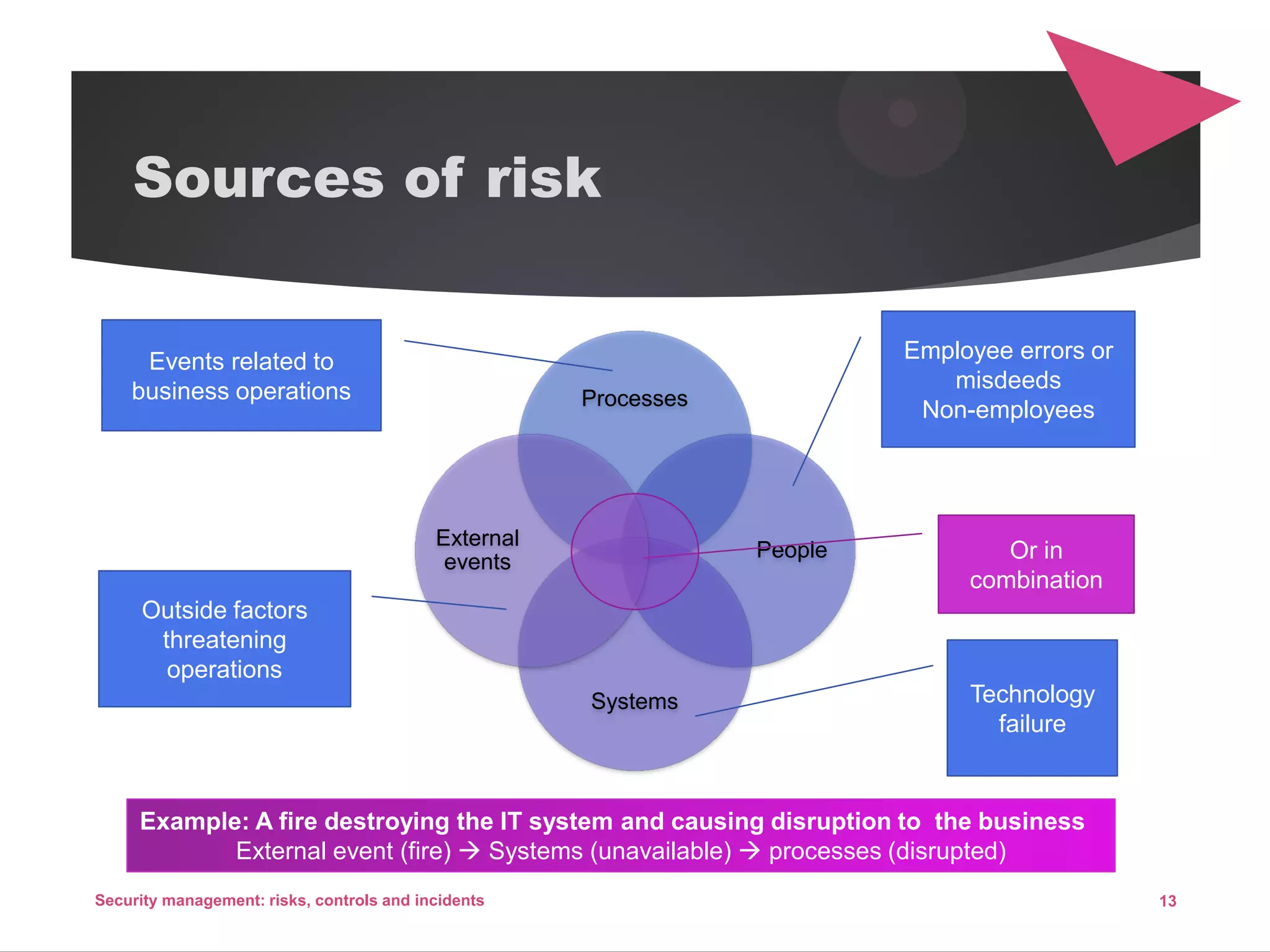
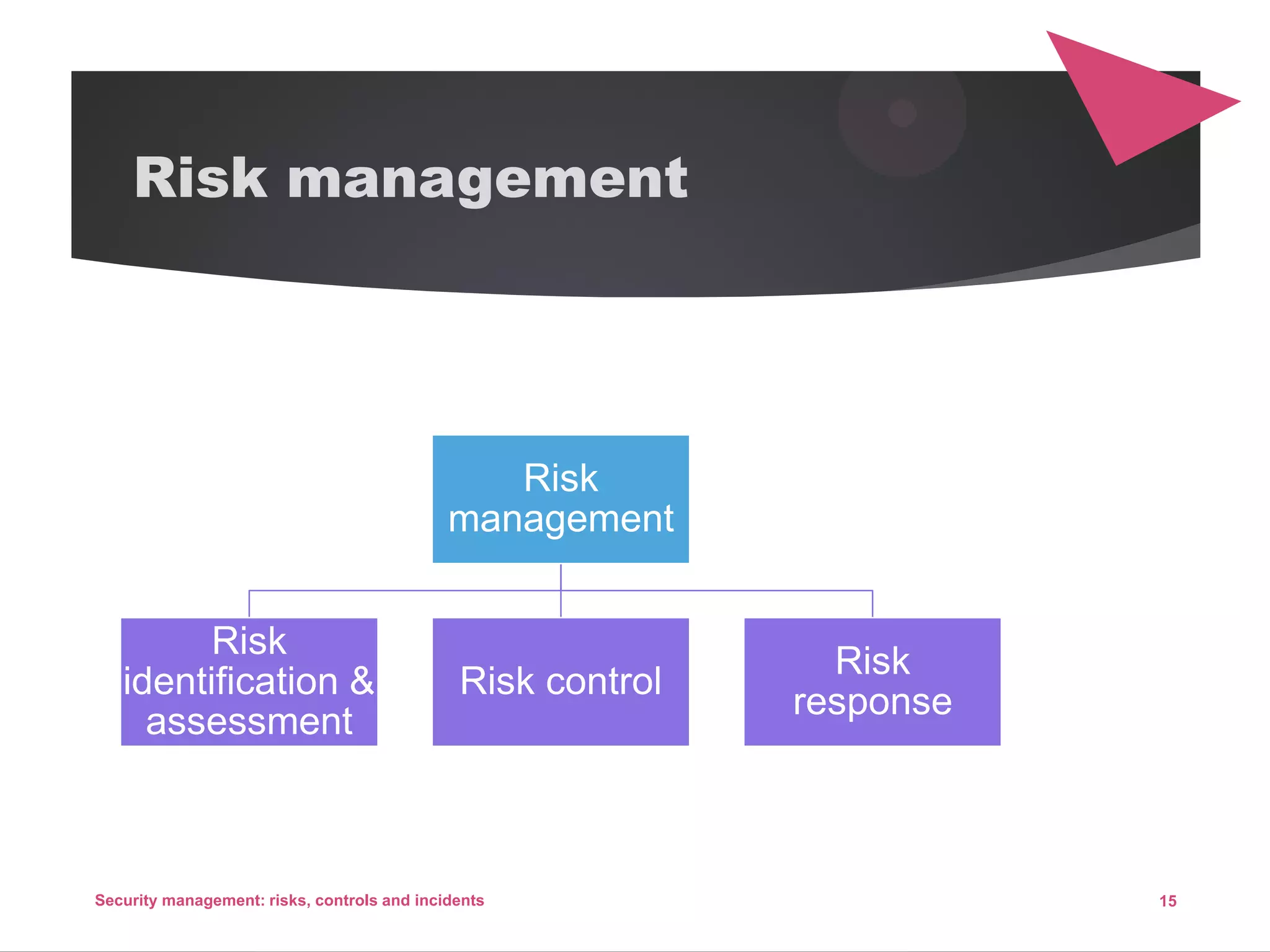
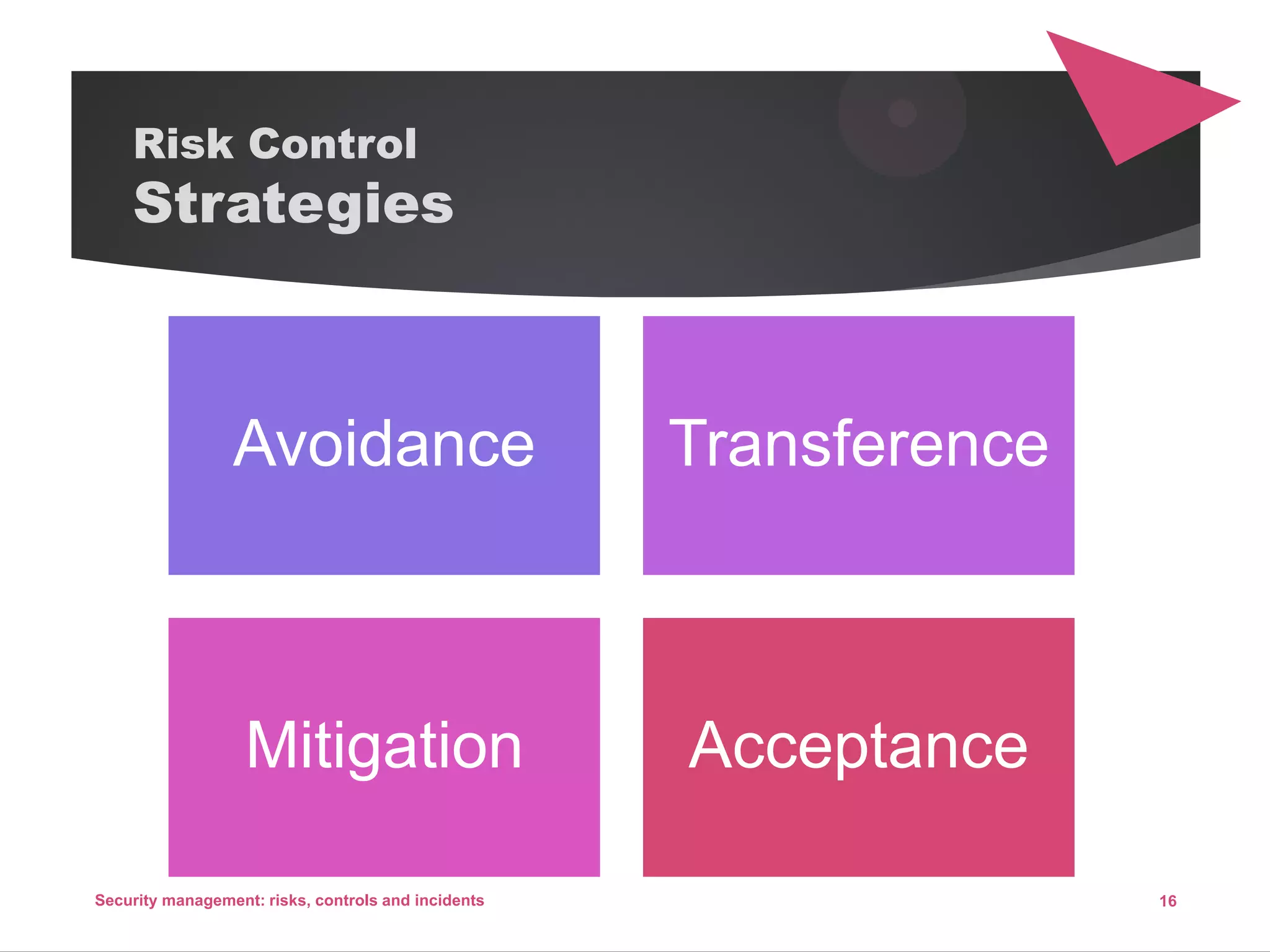
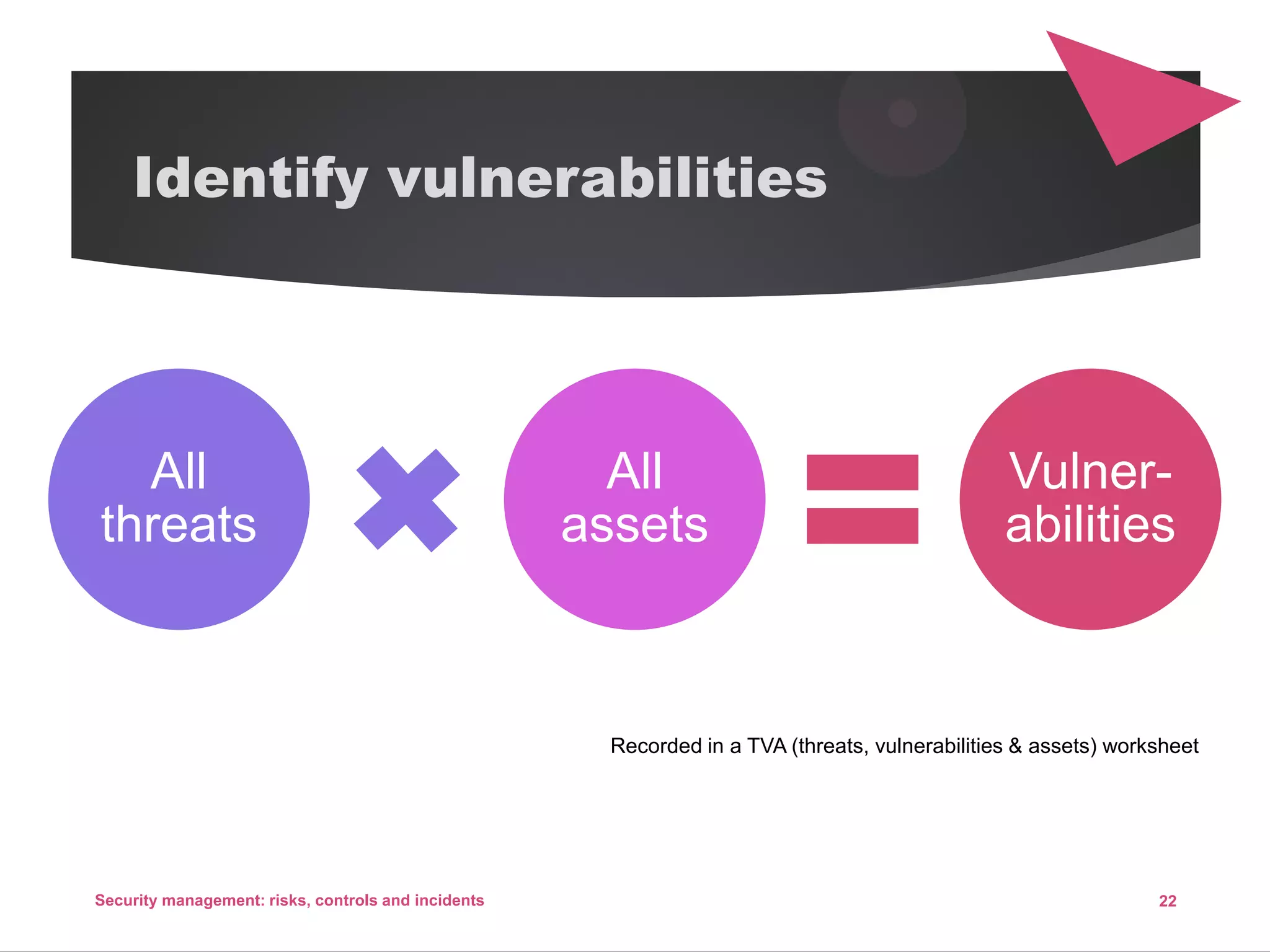
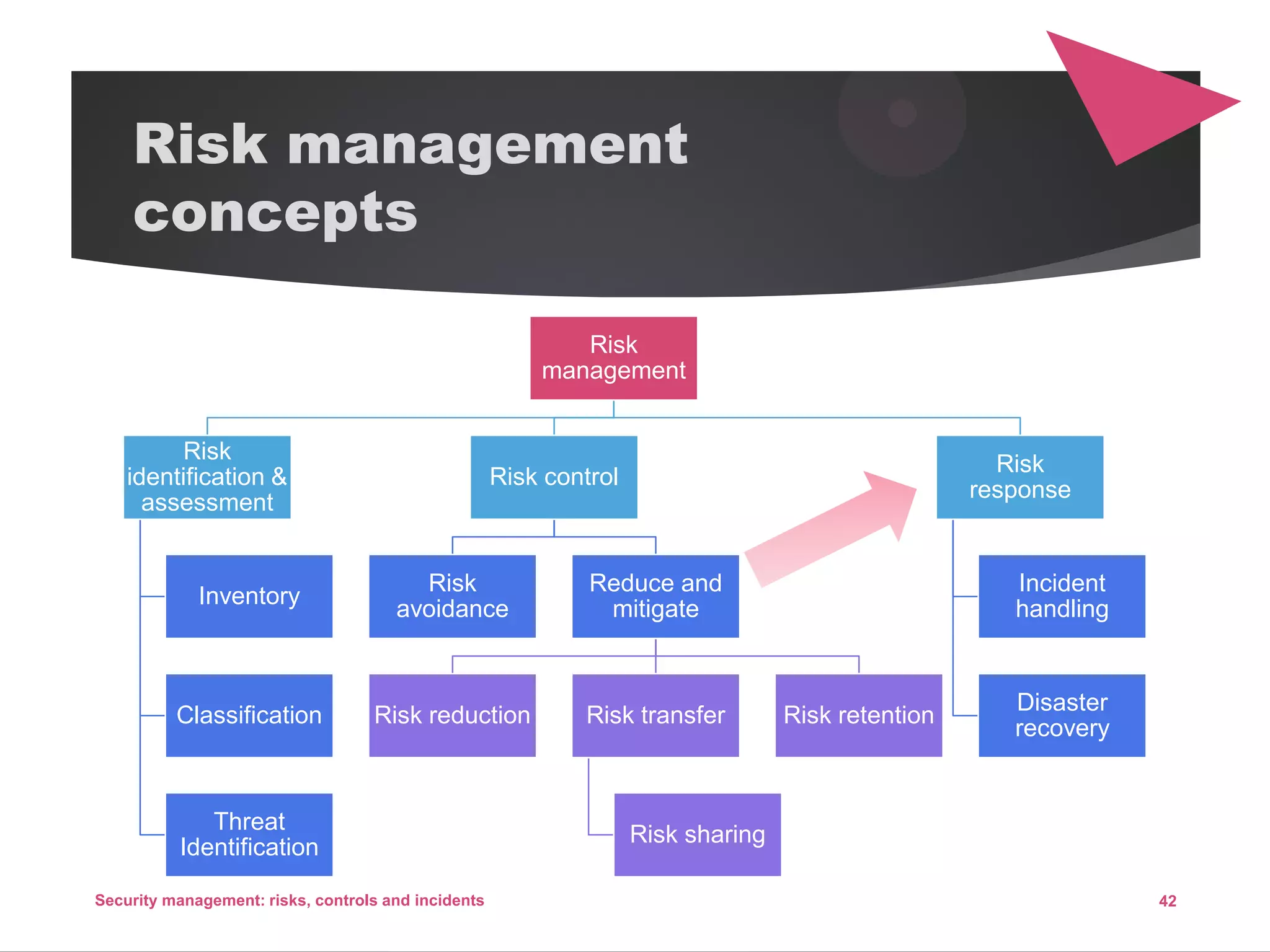
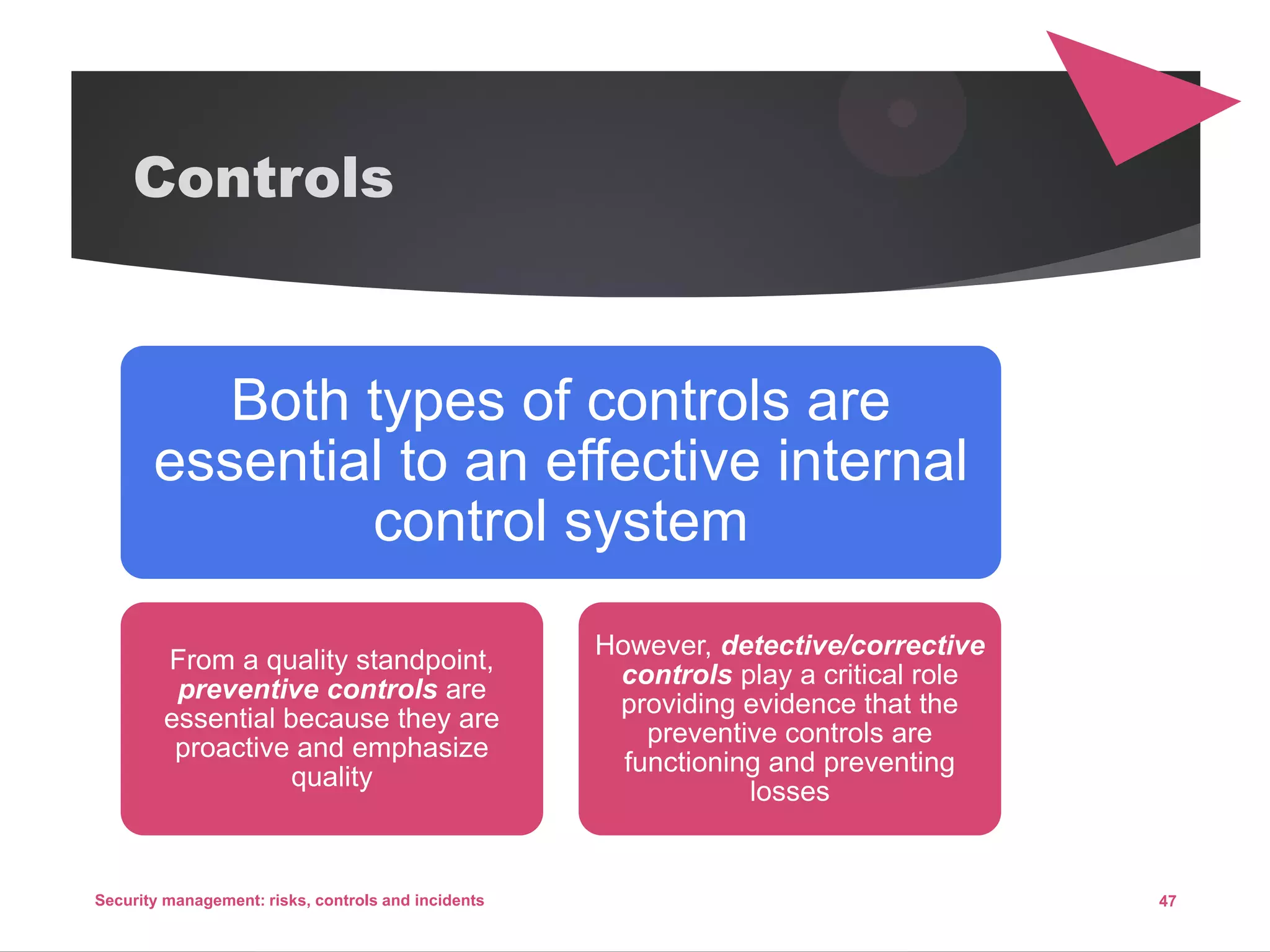
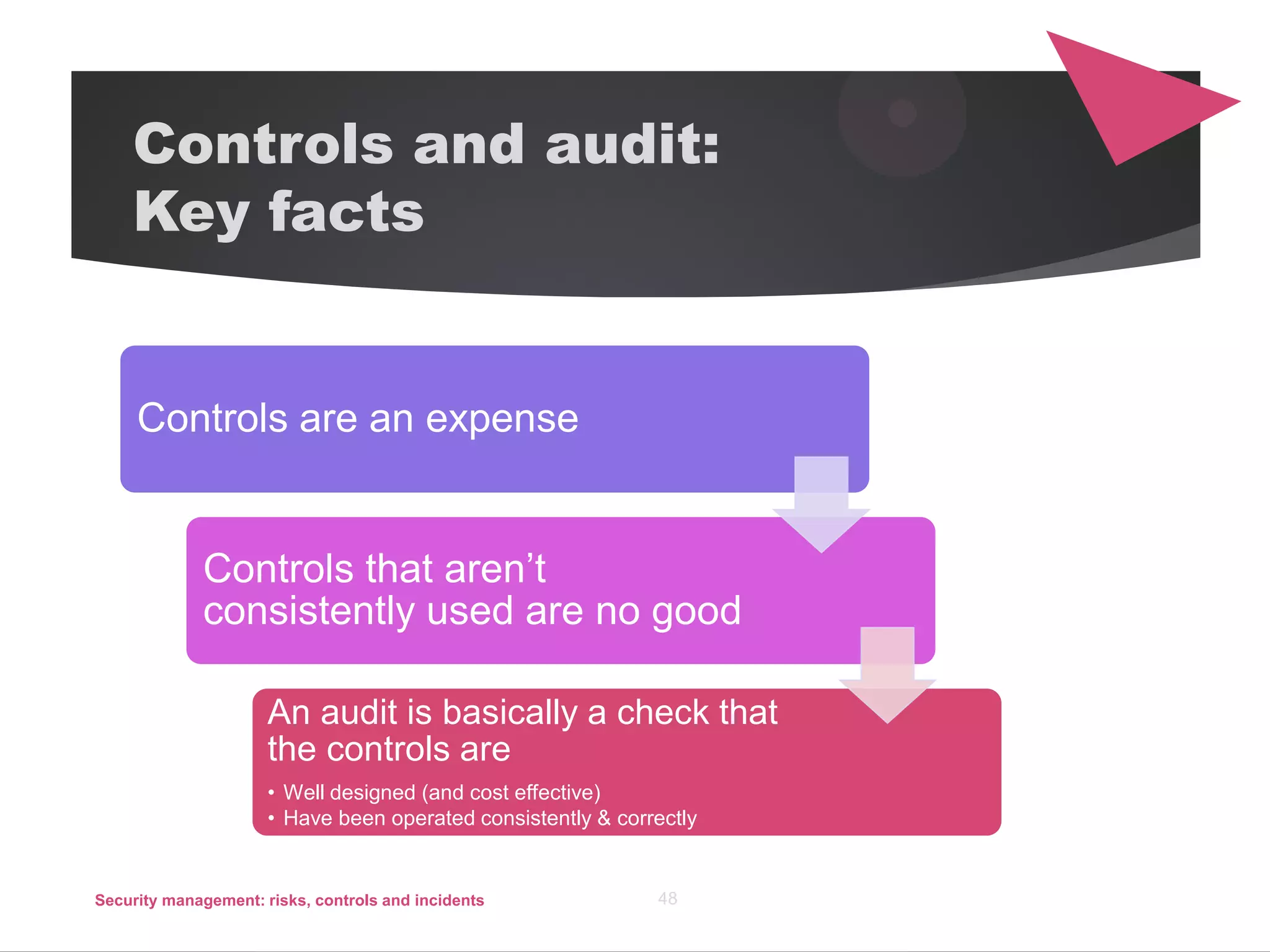
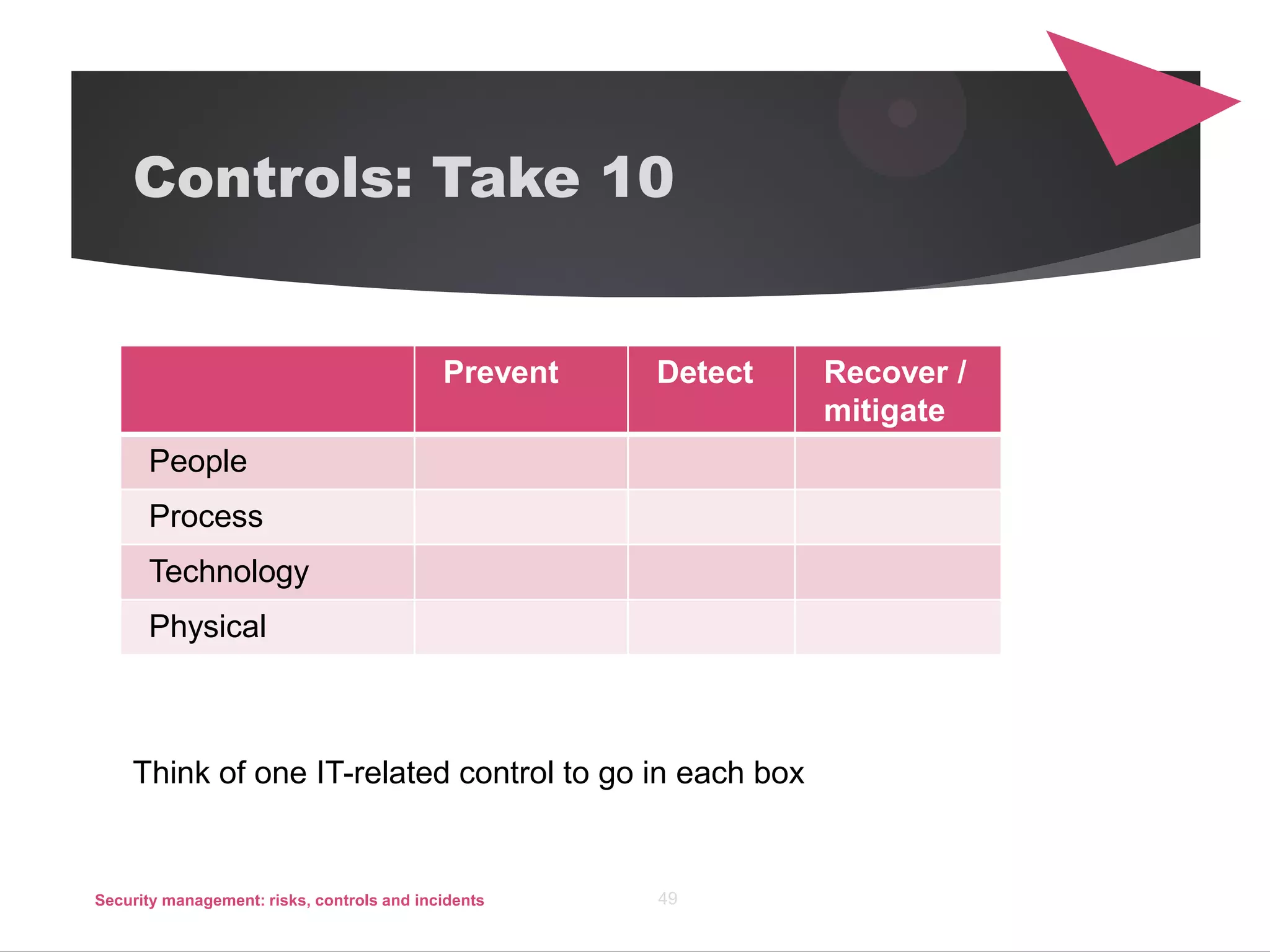
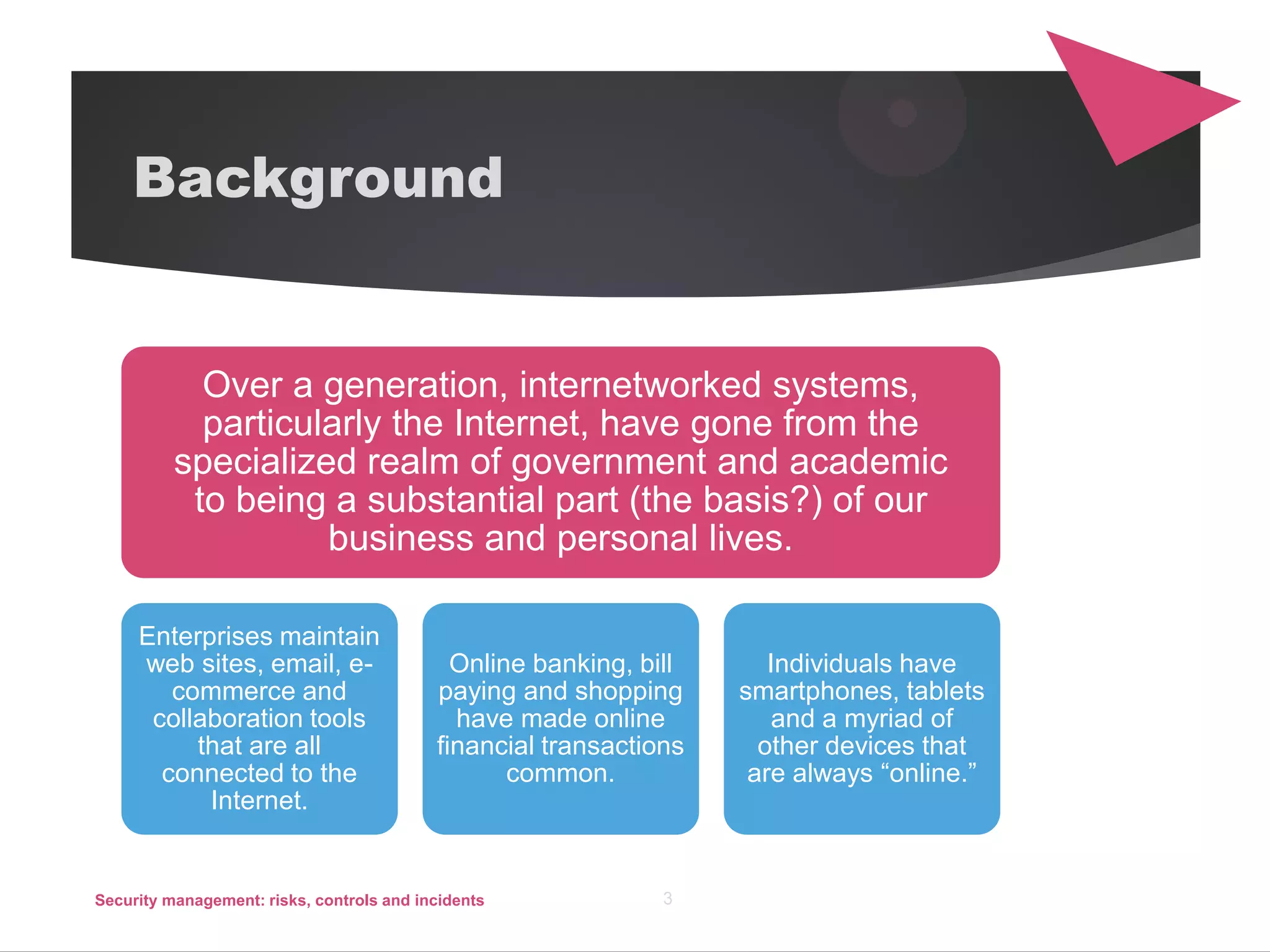
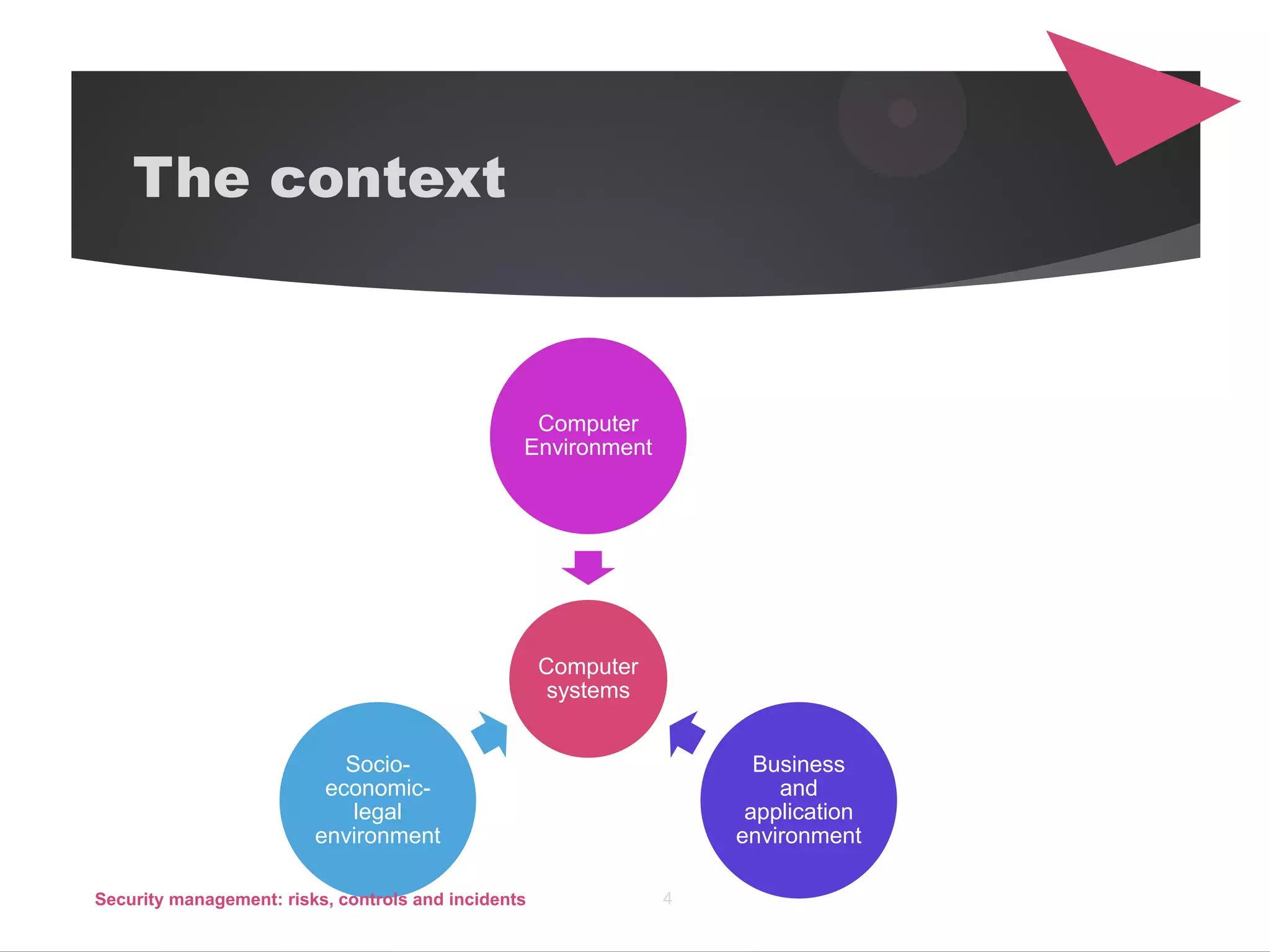
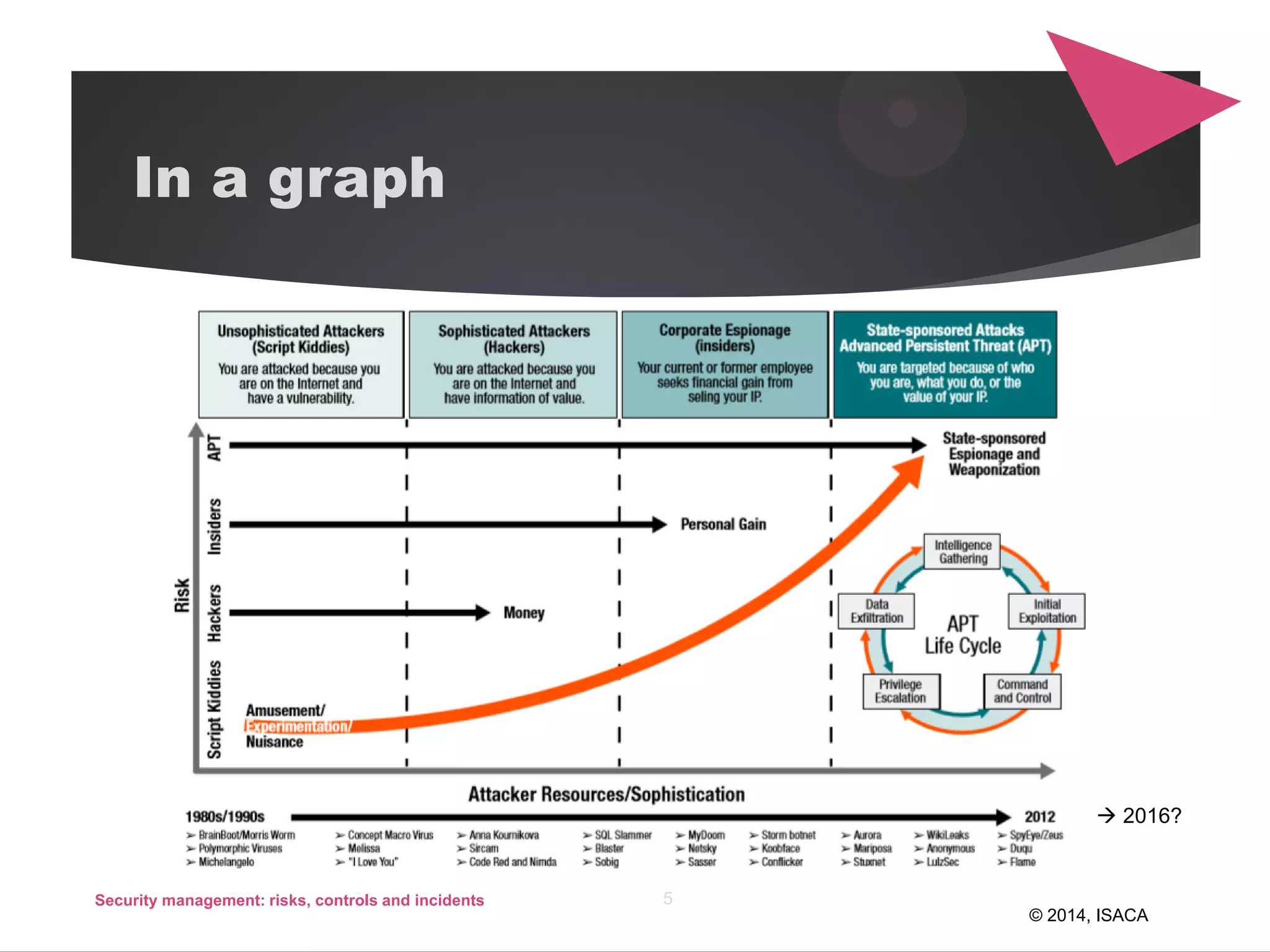
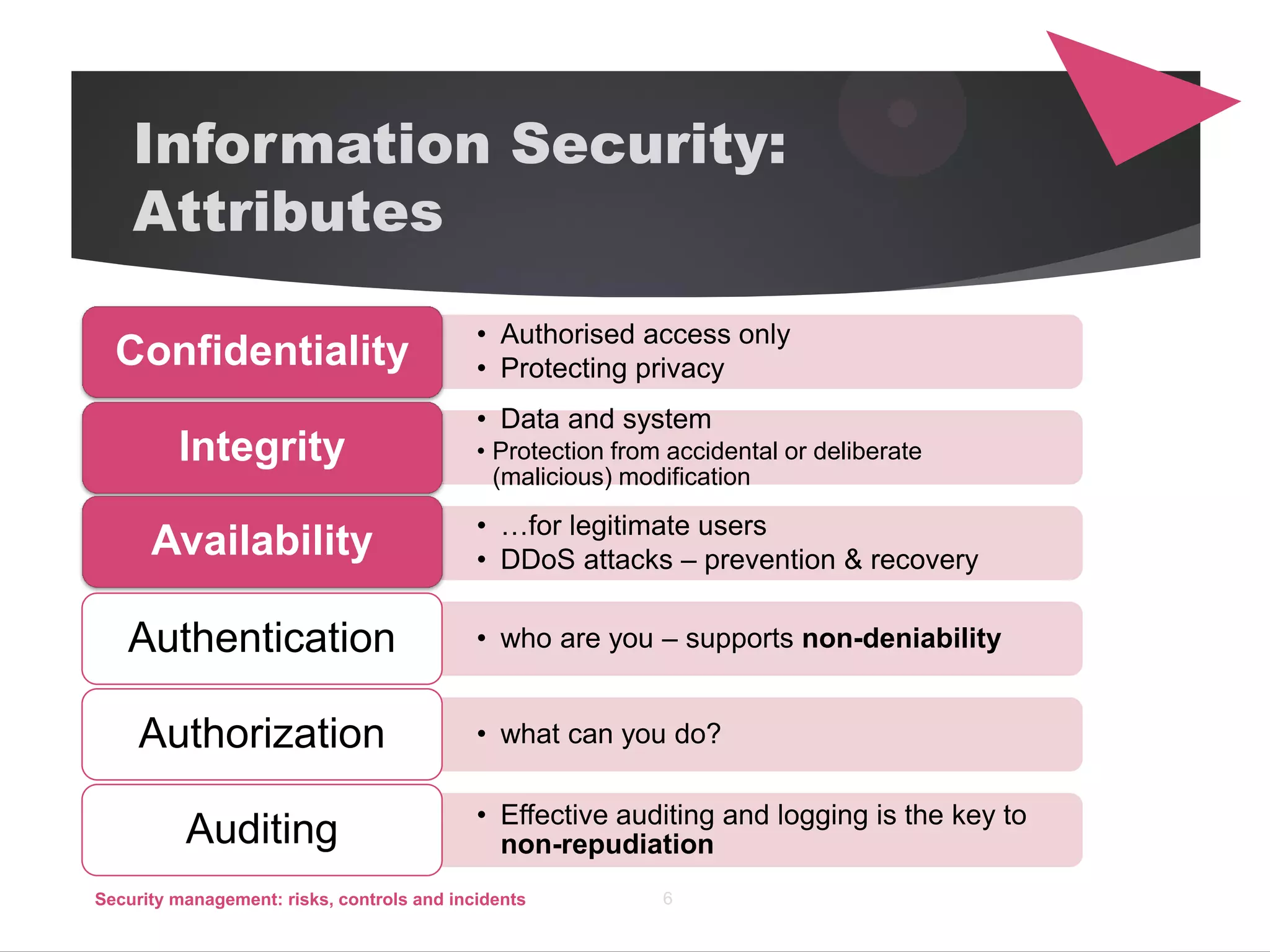
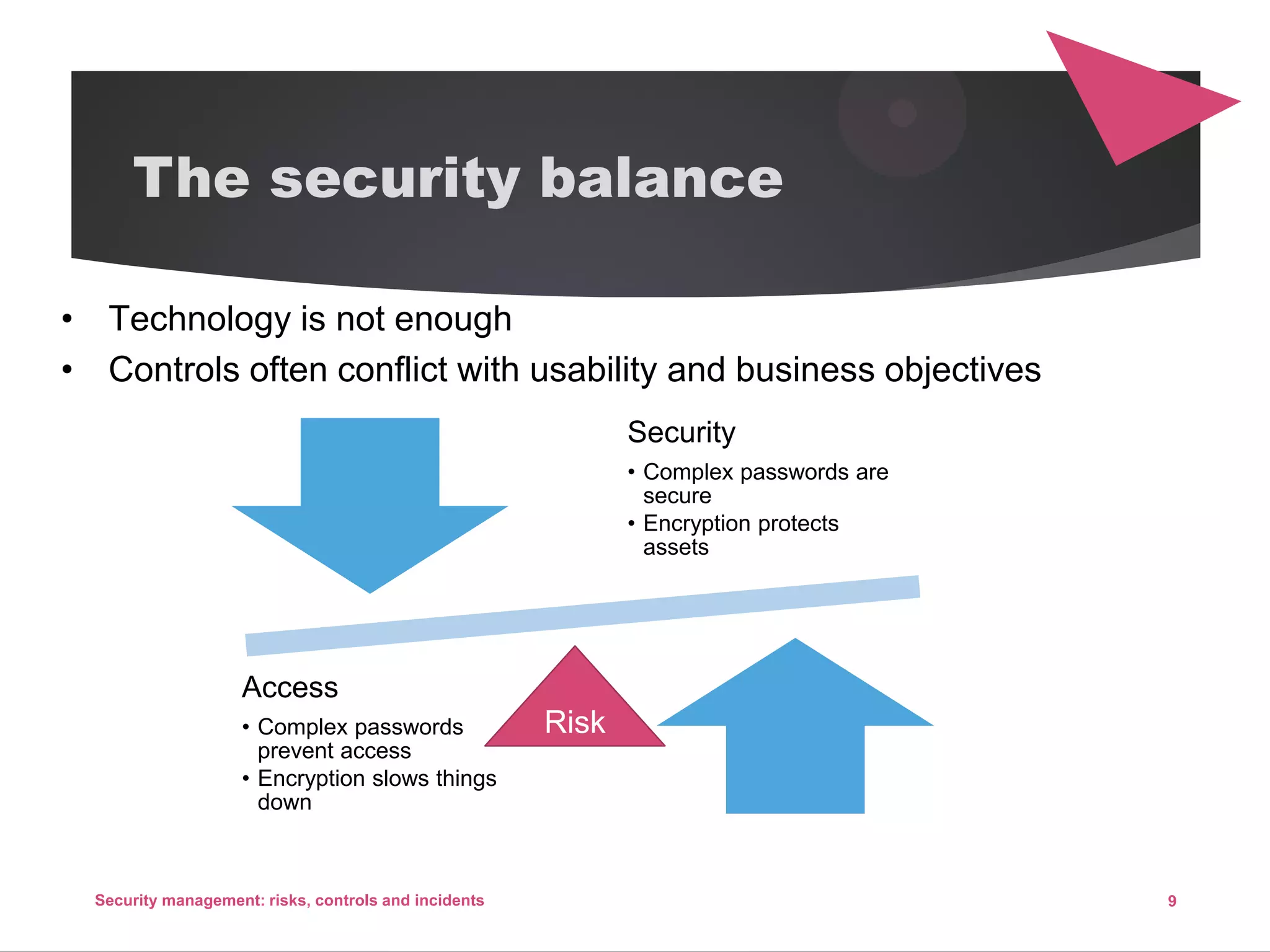
The document discusses security management, focusing on the identification, assessment, and control of risks in interconnected systems that are increasingly integral to business operations. It emphasizes the importance of balancing security measures with usability and outlines various strategies for risk management, including avoidance, transference, mitigation, and acceptance. The document also covers incident handling as a form of risk mitigation and the significance of having a structured response plan in case of security incidents.



![Risk is
...let’s start with Wikipedia:
The potential that a chosen (in)action will lead to a loss
[or a gain]
Implies that a choice having an influence on the outcome
exists (or existed)
Potential losses themselves may also be called “risks”
Almost any human endeavour carries some risk, but some
are much more risky than others.
11Security management: risks, controls and incidents](https://image.slidesharecdn.com/securitymanagment-riskscontrolsandincidents-160419195825/75/Security-managment-risks-controls-and-incidents-10-2048.jpg)