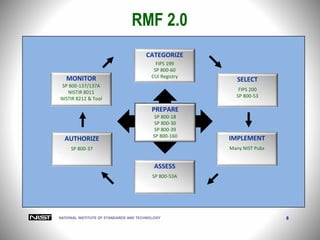
The document outlines the Risk Management Framework (RMF) for information systems as revised by NIST in October 2018, detailing an updated approach for managing security and privacy throughout the system life cycle. Key improvements include integrating privacy risk management, supply chain risk management, and enhanced authorization options, alongside a timeline for public comments and future publication dates. It emphasizes the importance of continuous risk assessment and the defined roles and responsibilities within the risk management process.









![NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY 11
RMF 2.0 Task Outcomes
Tasks Outcomes
Task I-1
CONTROL IMPLEMENTATION
Controls specified in the security and privacy plans
are implemented.
[Cybersecurity Framework: PR.IP-1]
Systems security and privacy engineering
methodologies are used to implement the controls
in the system security and privacy plans.
[Cybersecurity Framework: PR.IP-2]
Task I-2
BASELINE CONFIGURATION
The configuration baseline is established.
[Cybersecurity Framework: PR.IP-1]
The security and privacy plans are updated based on
information obtained during the implementation of
the controls.
[Cybersecurity Framework: Profile]](https://image.slidesharecdn.com/nistpresentation-rmf2-181106190827/85/NIST-presentation-on-RMF-2-0-SP-800-37-rev-2-11-320.jpg)


















![NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY 30
Security Control Structure – Revision 5
AU-4 AUDIT LOG STORAGE CAPACITY
Control: Allocate audit log storage capacity to accommodate [Assignment: organization-
defined audit log retention requirements].
Discussion: Organizations consider the types of audit logging to be performed and the audit
log processing requirements when allocating audit log storage capacity. Allocating
sufficient audit log storage capacity reduces the likelihood of such capacity being exceeded
and resulting in the potential loss or reduction of audit logging capability.
Related controls: AU-2, AU-5, AU-6, AU-7, AU-9, AU-11, AU-12, SI-4.
Control Enhancements:
(1) AUDIT LOG STORAGE CAPACITY | TRANSFER TO ALTERNATE STORAGE
Transfer audit logs [Assignment: organization-defined frequency] to a different system, system
component, or media other than the system or system component conducting the logging.
Supplemental Guidance: This type of transfer, also known as off-loading, is a common process in systems
with limited audit log storage capacity and thus supports availability of the audit logs. The initial audit log
storage is used only in a transitory fashion until the system can communicate with the secondary or alternate
system allocated to audit log storage, at which point the audit logs are transferred. This control
enhancement is similar to AU-9(2) in that the audit logs are transferred to a different entity; however, the
primary purpose of selecting AU-9(2) is to protect the confidentiality and integrity of audit records.
Organizations can select either enhancement to obtain the dual benefit of increased audit log storage
capacity and preserving the confidentiality, integrity, and availability of audit records and logs.
Related controls: None
References: None.](https://image.slidesharecdn.com/nistpresentation-rmf2-181106190827/85/NIST-presentation-on-RMF-2-0-SP-800-37-rev-2-30-320.jpg)