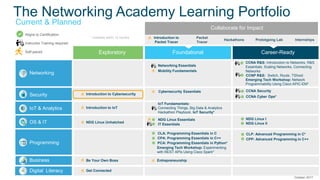
The document provides an overview of the Introduction to Cybersecurity 2.1 course. It summarizes that the course explores cyber trends, threats, and how to stay safe online. It consists of 5 modules that cover the need for cybersecurity, types of attacks, protecting personal and organizational data, and career opportunities in cybersecurity. The course is self-paced and takes approximately 15 hours to complete.