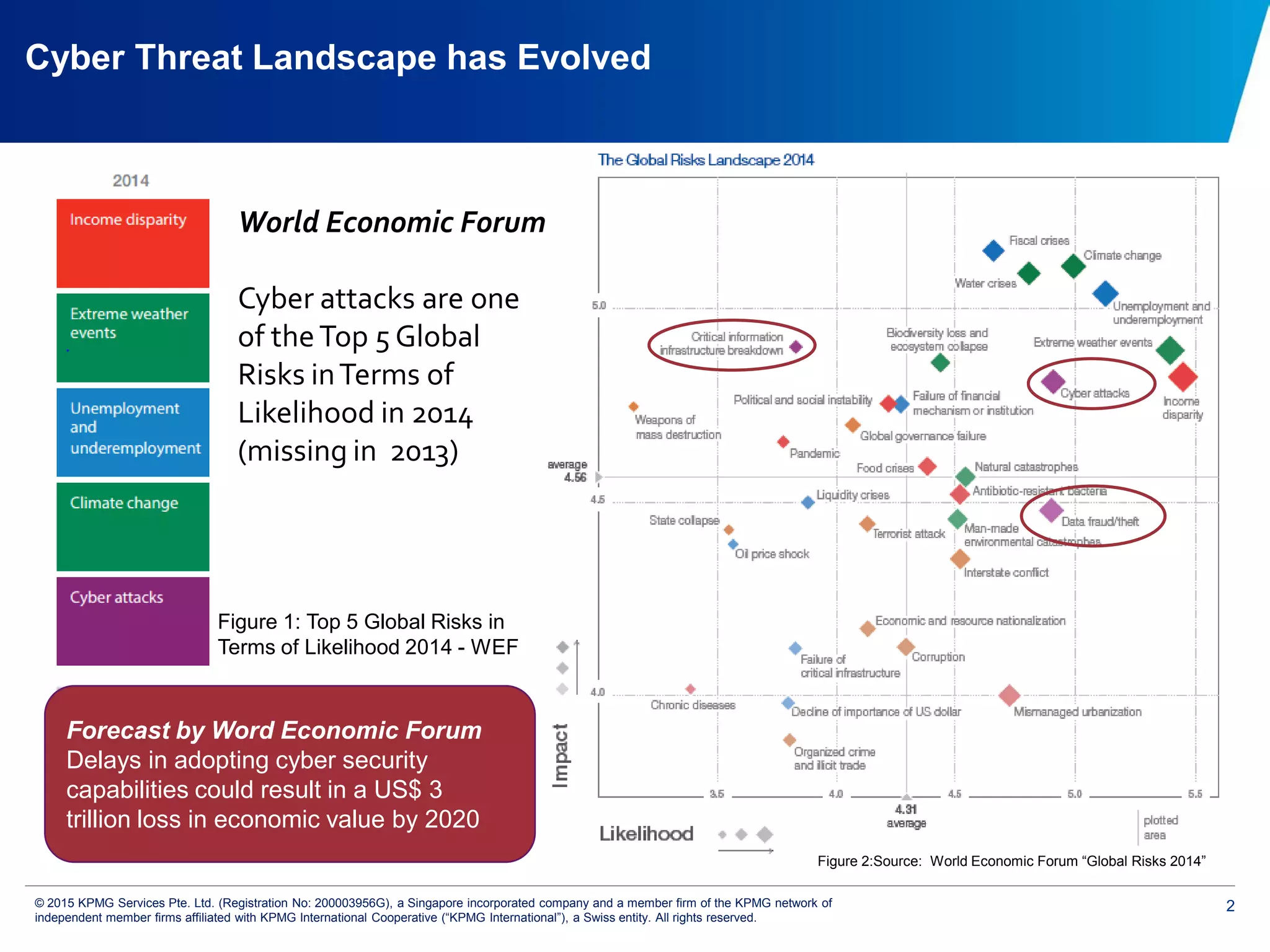
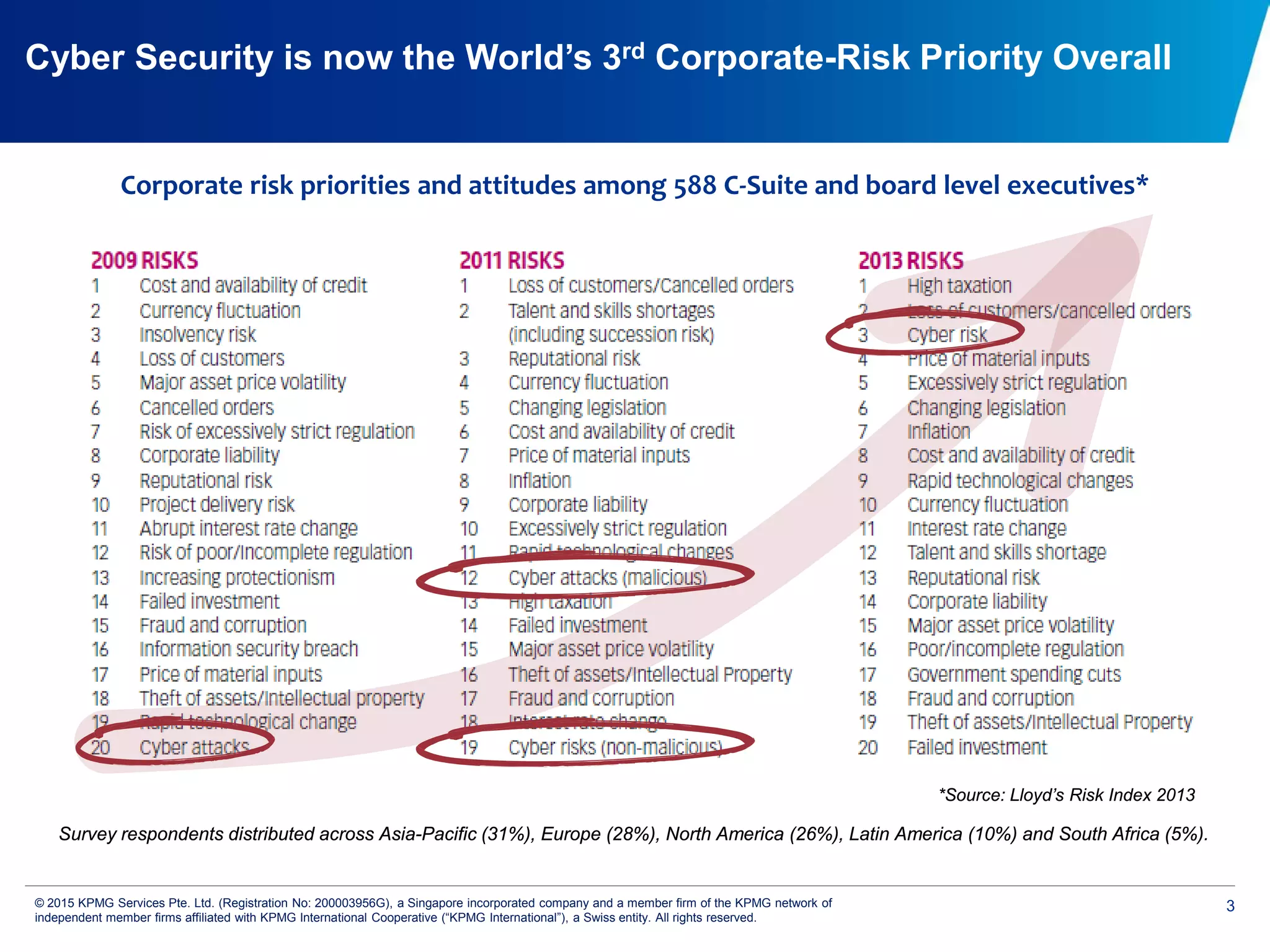
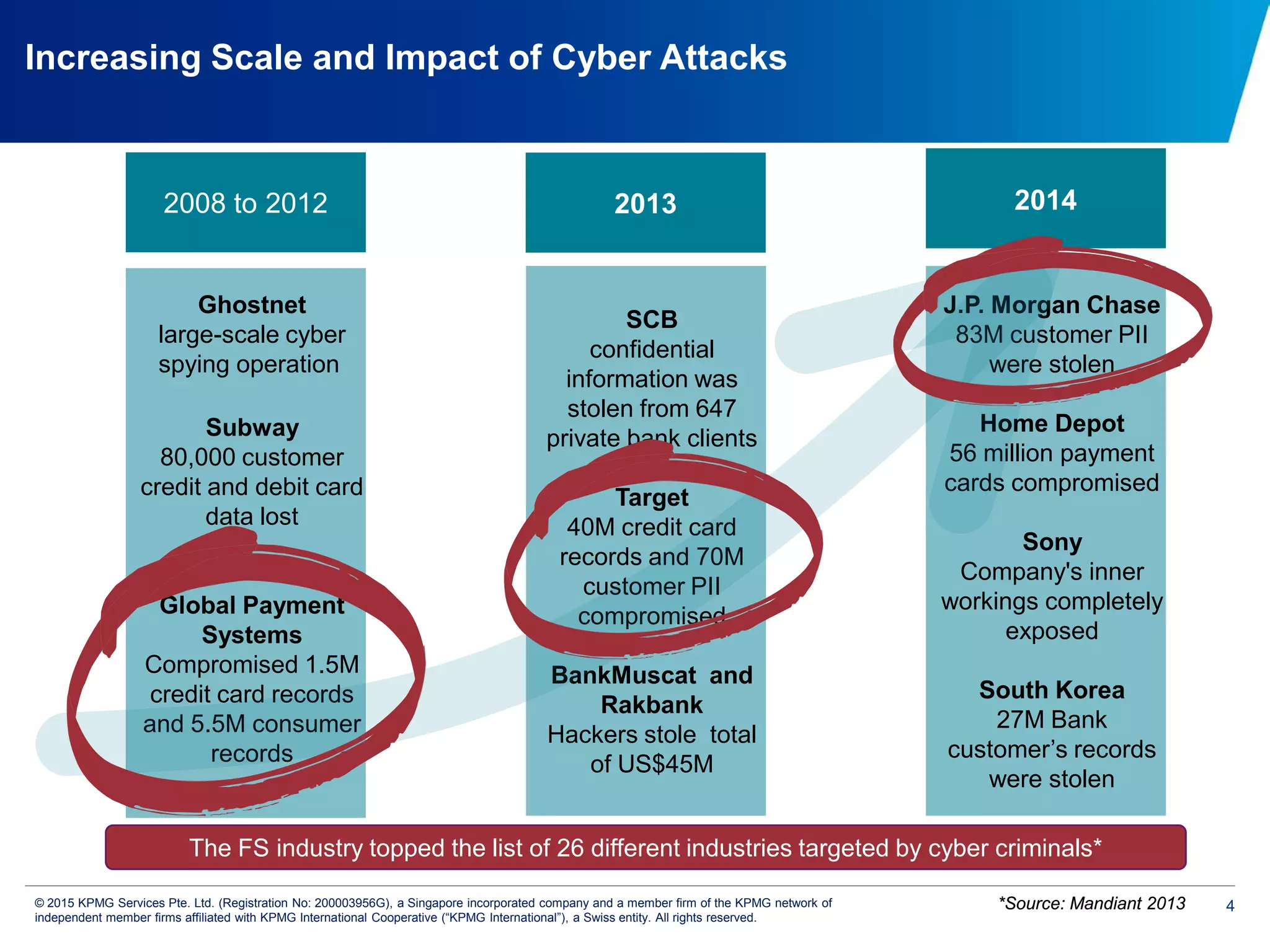
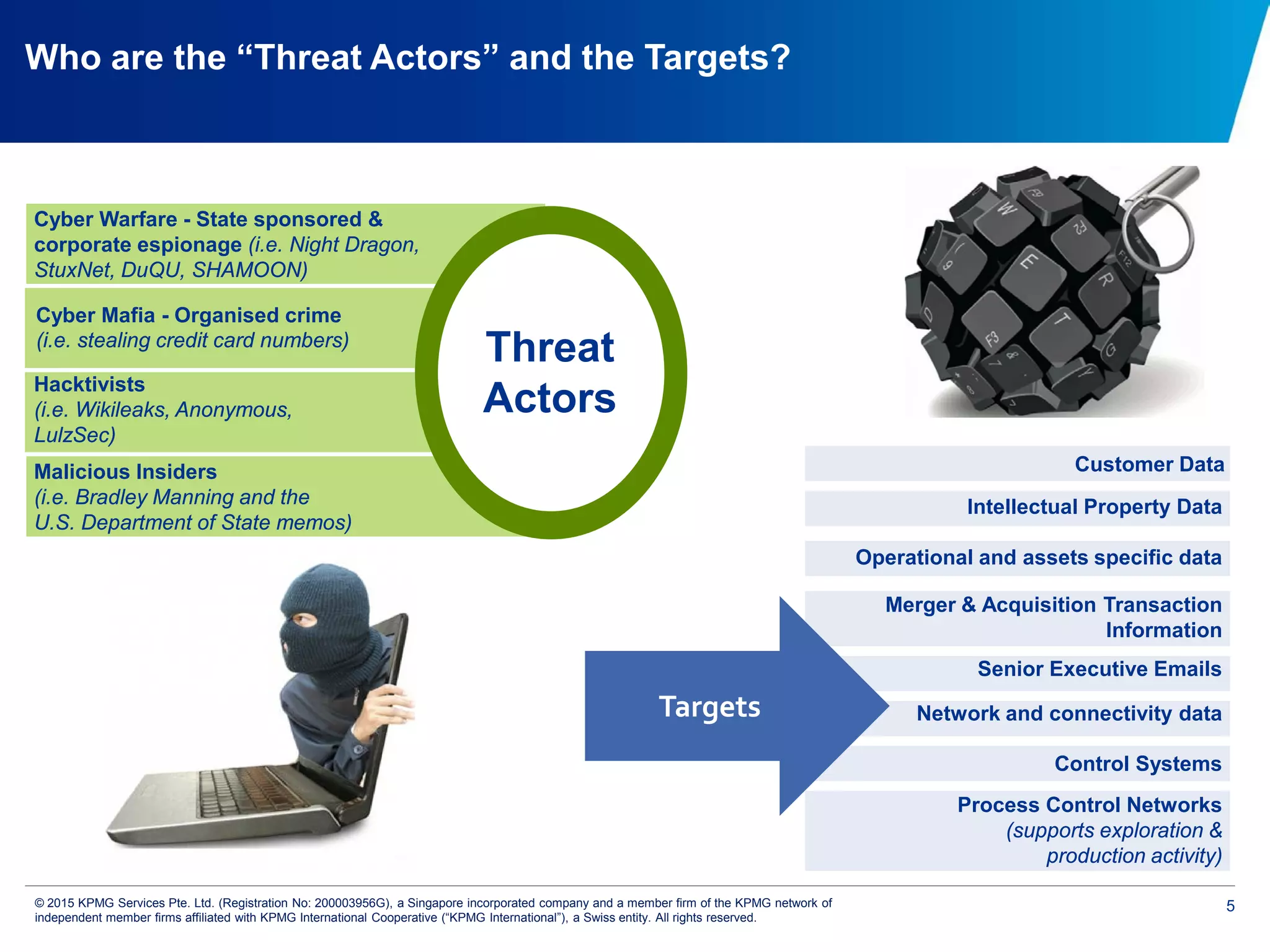
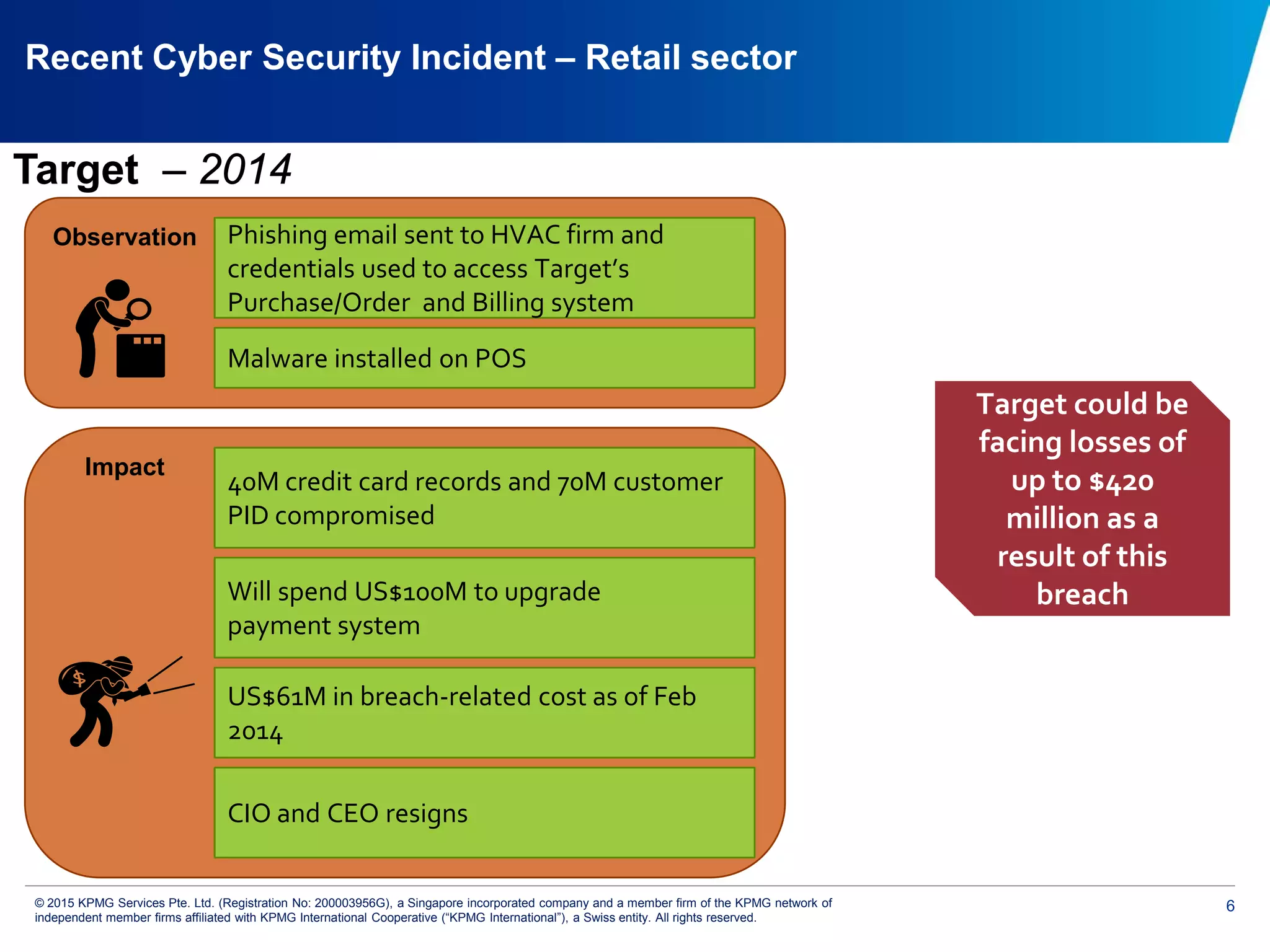
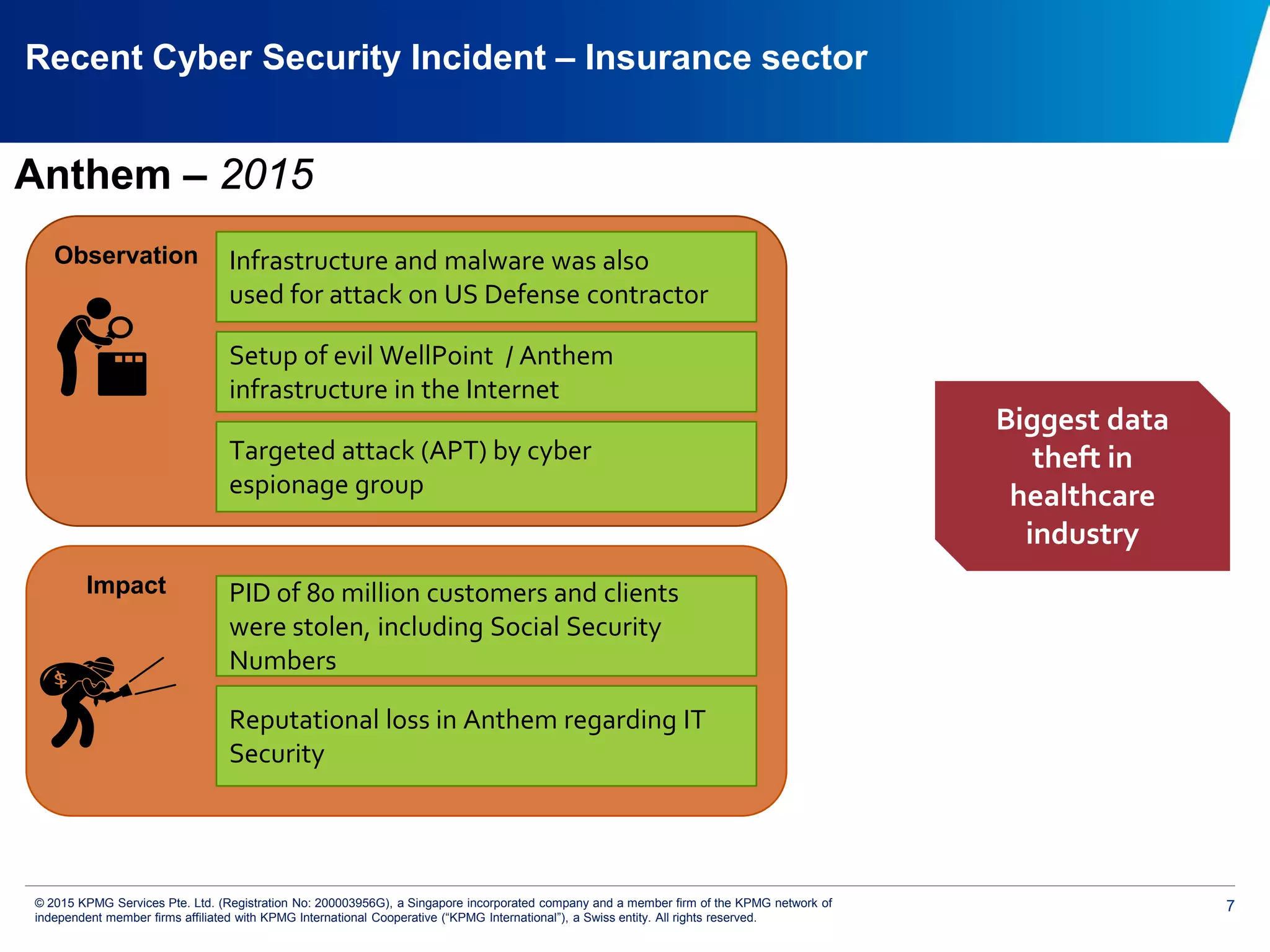
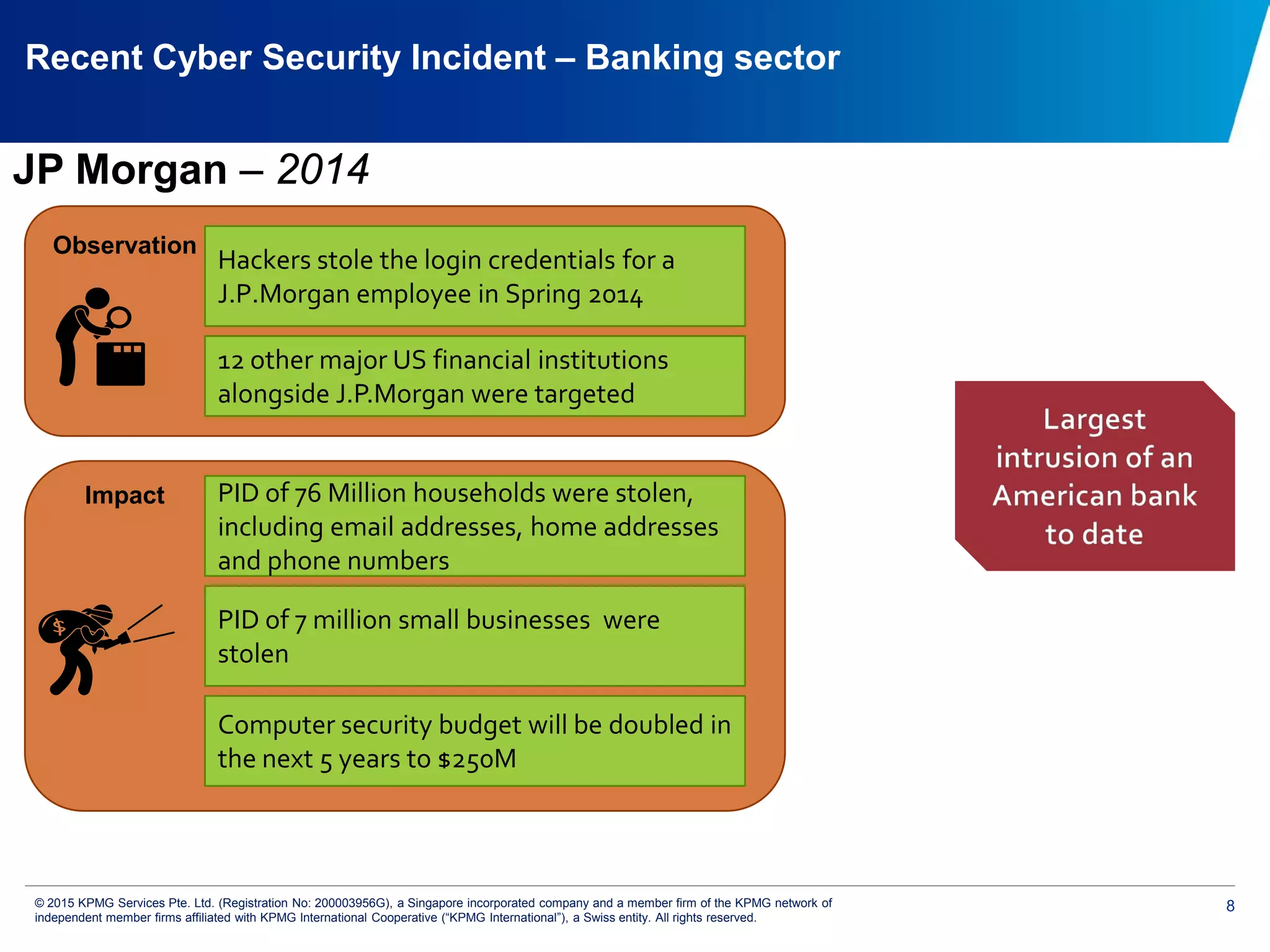
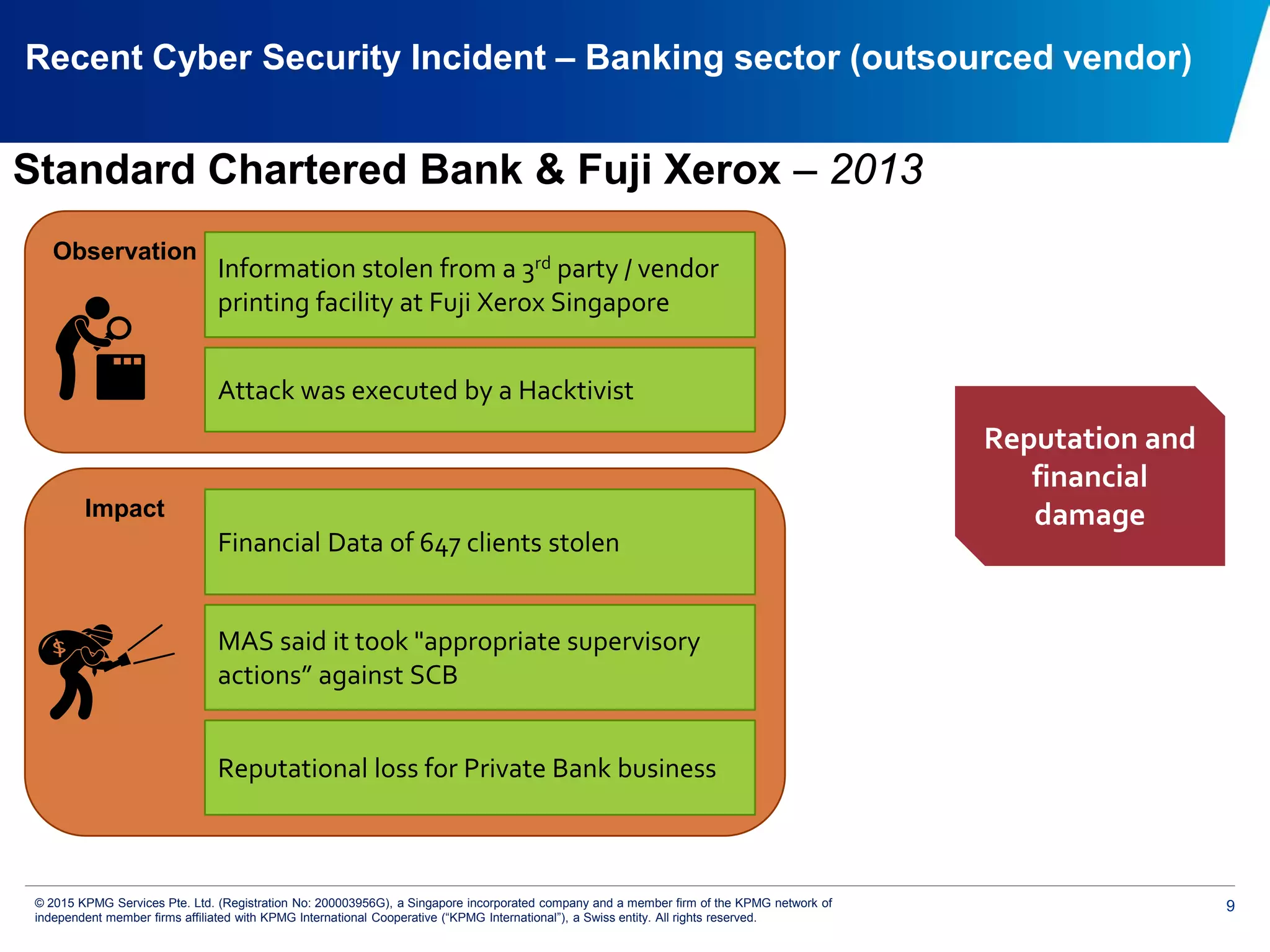
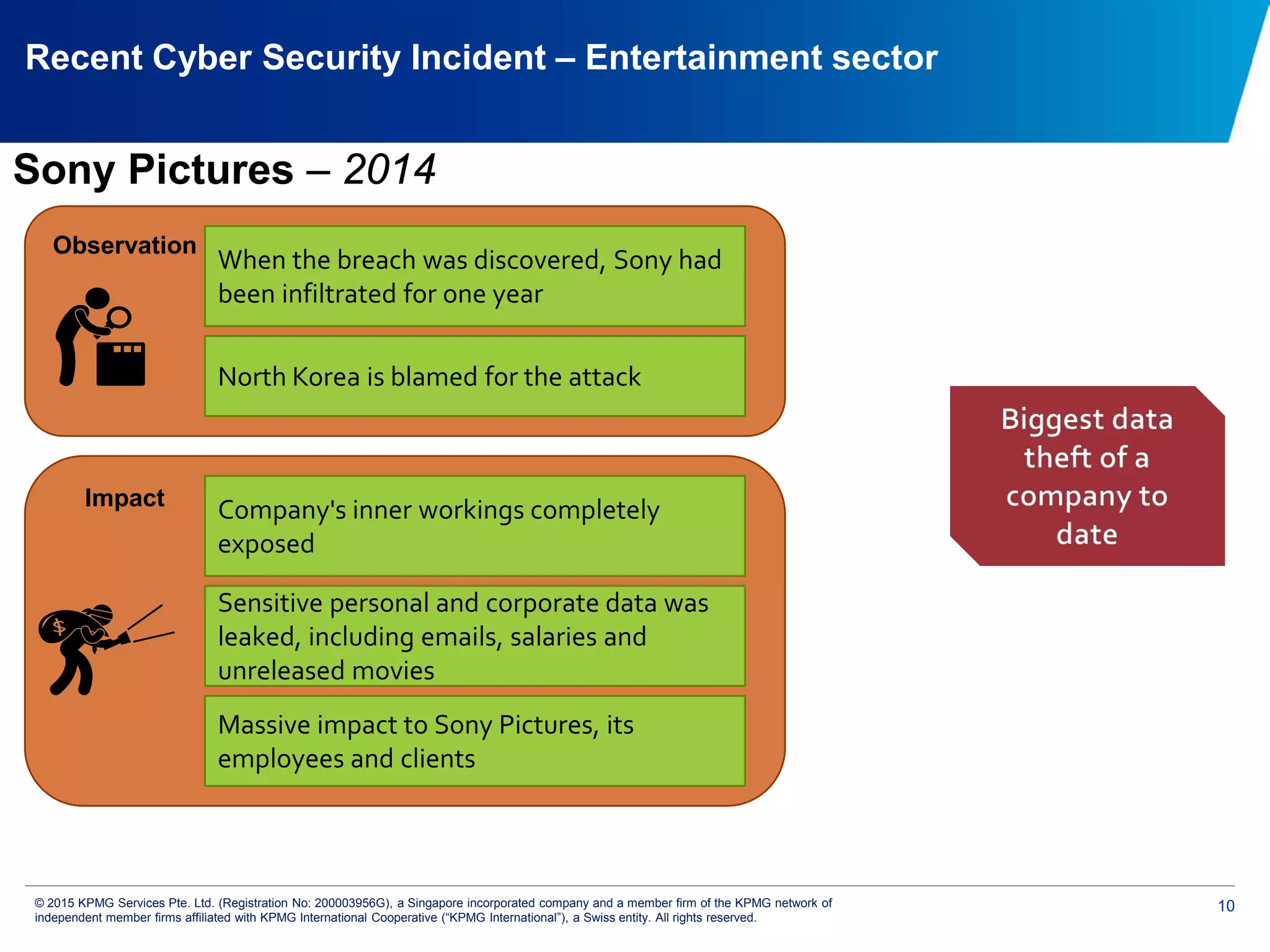
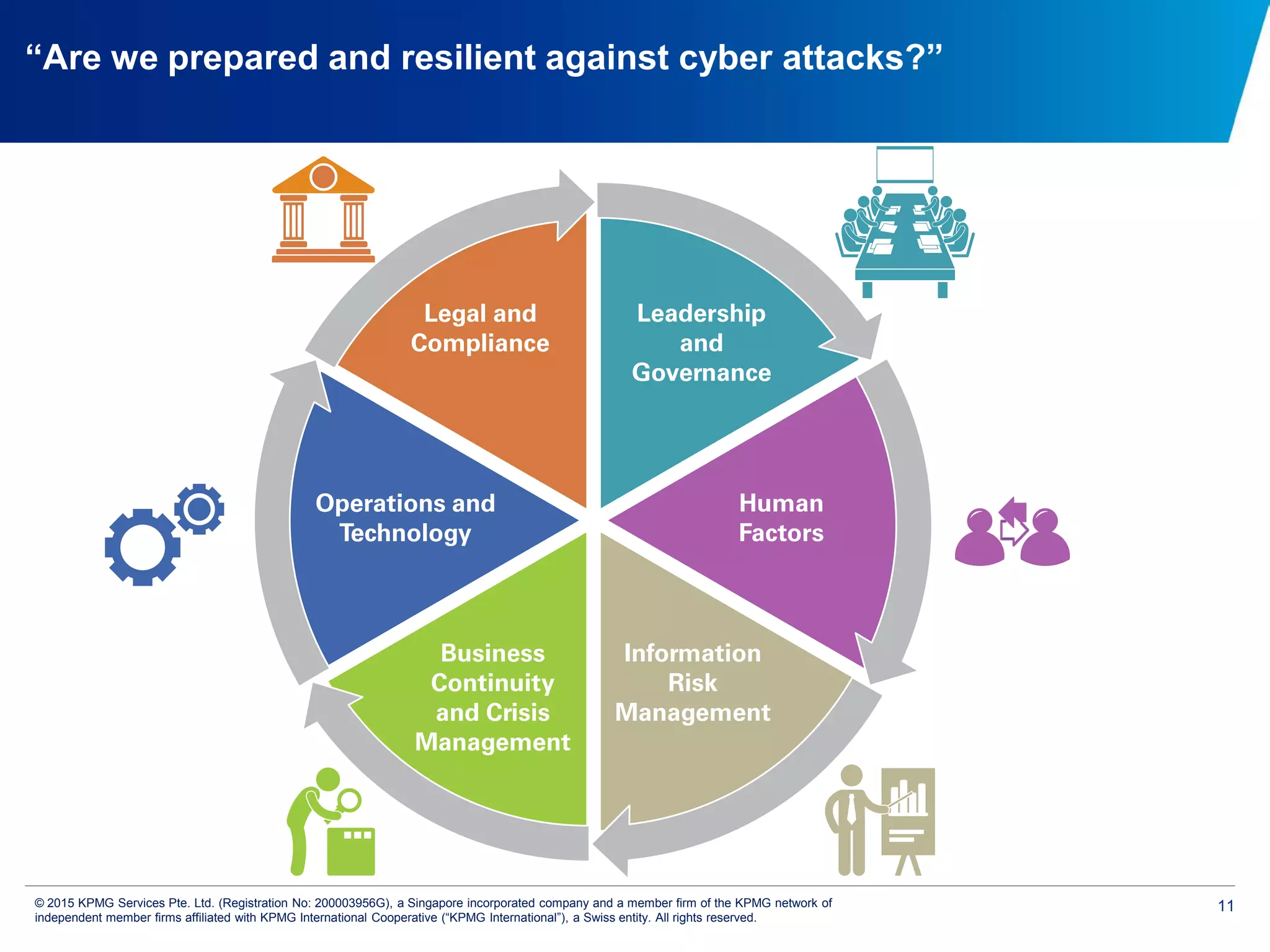
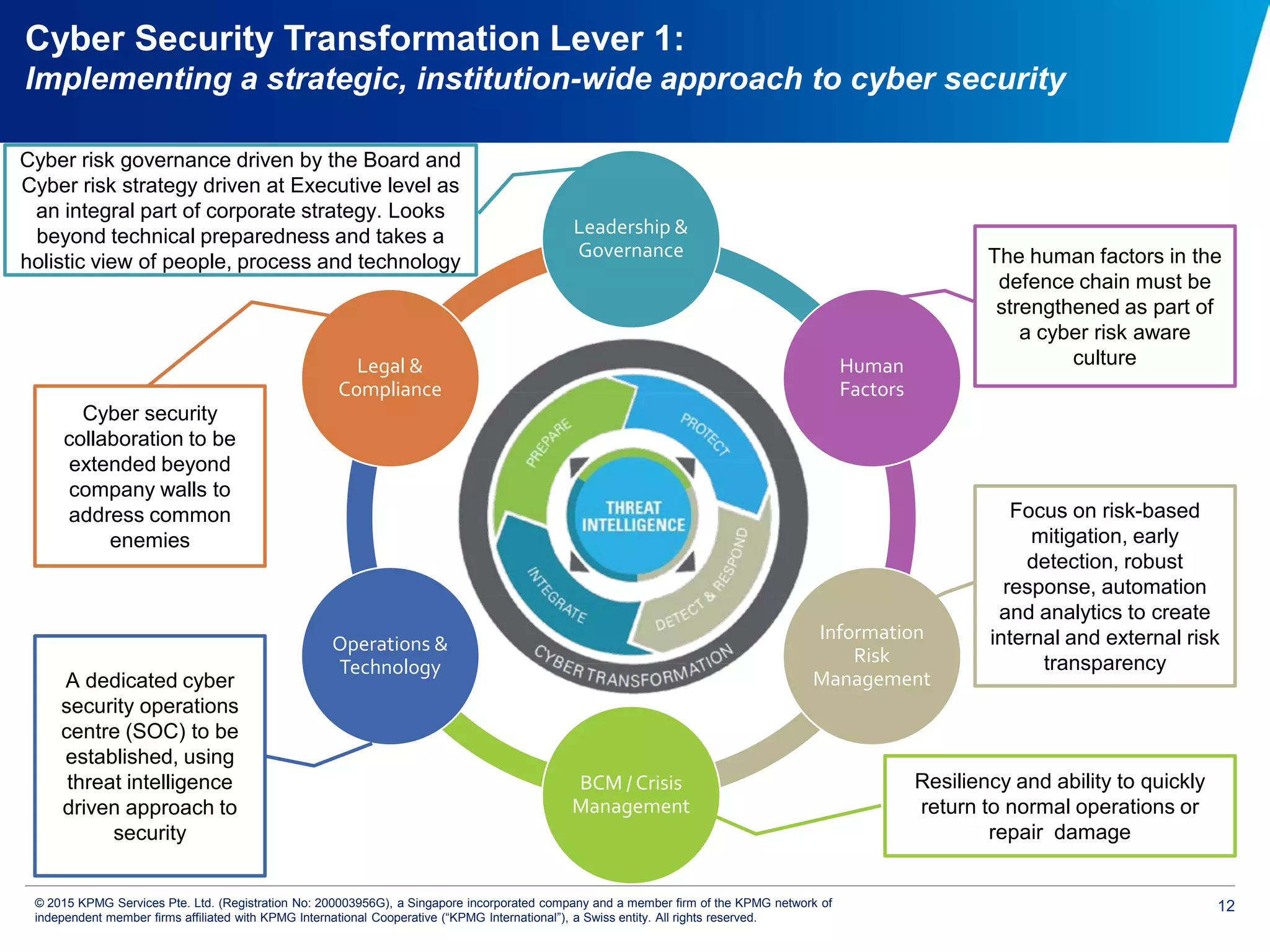
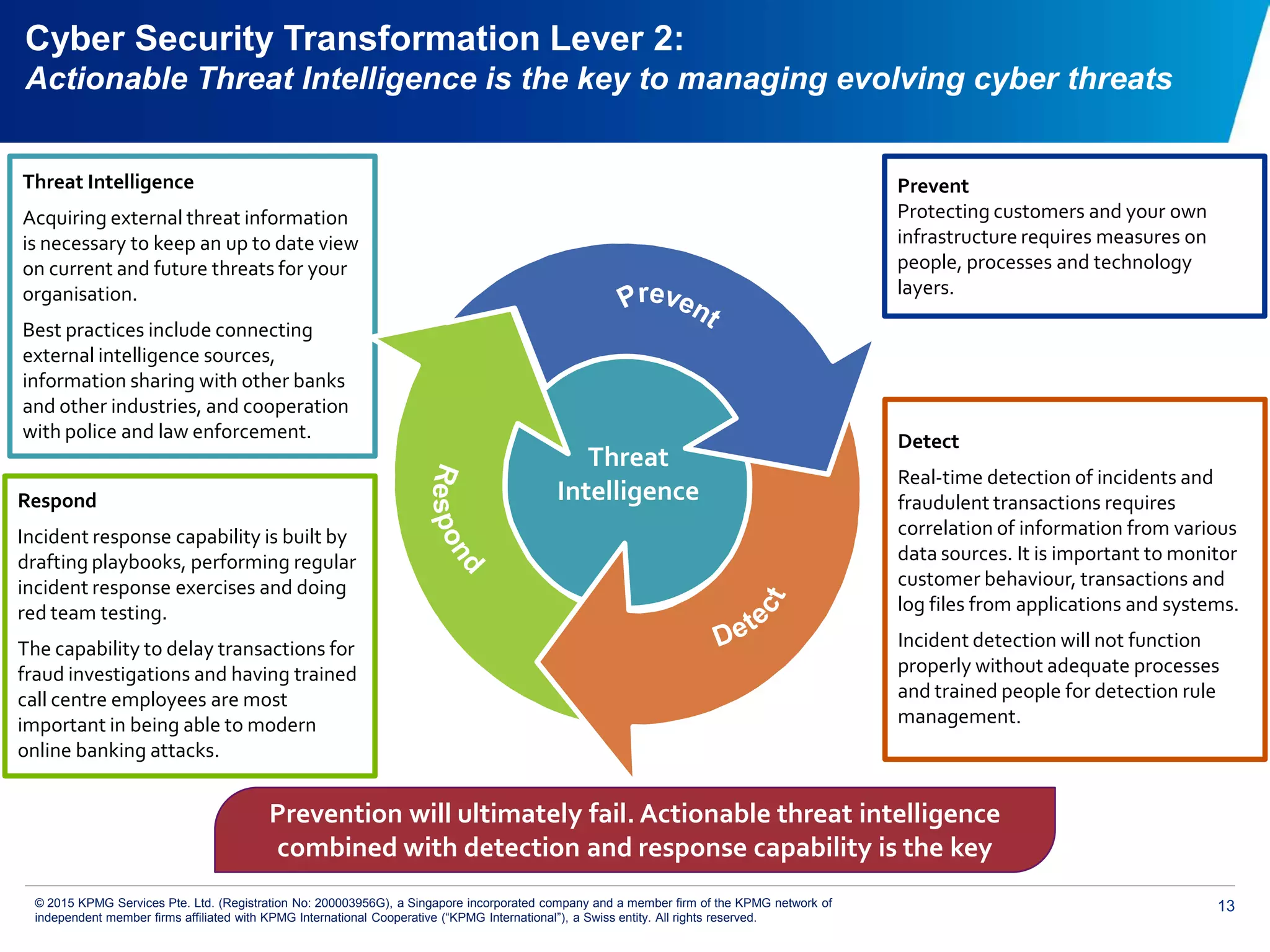
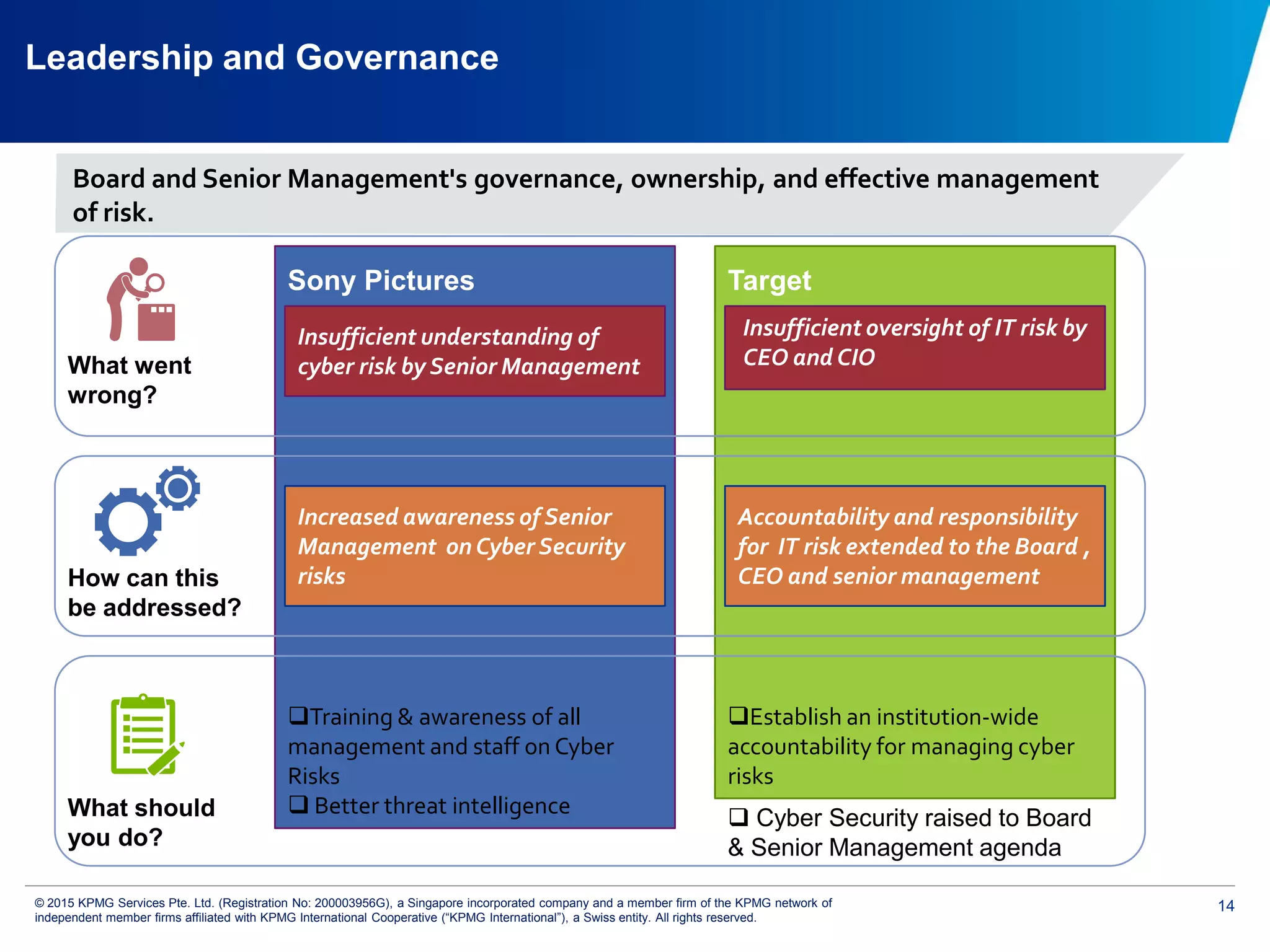
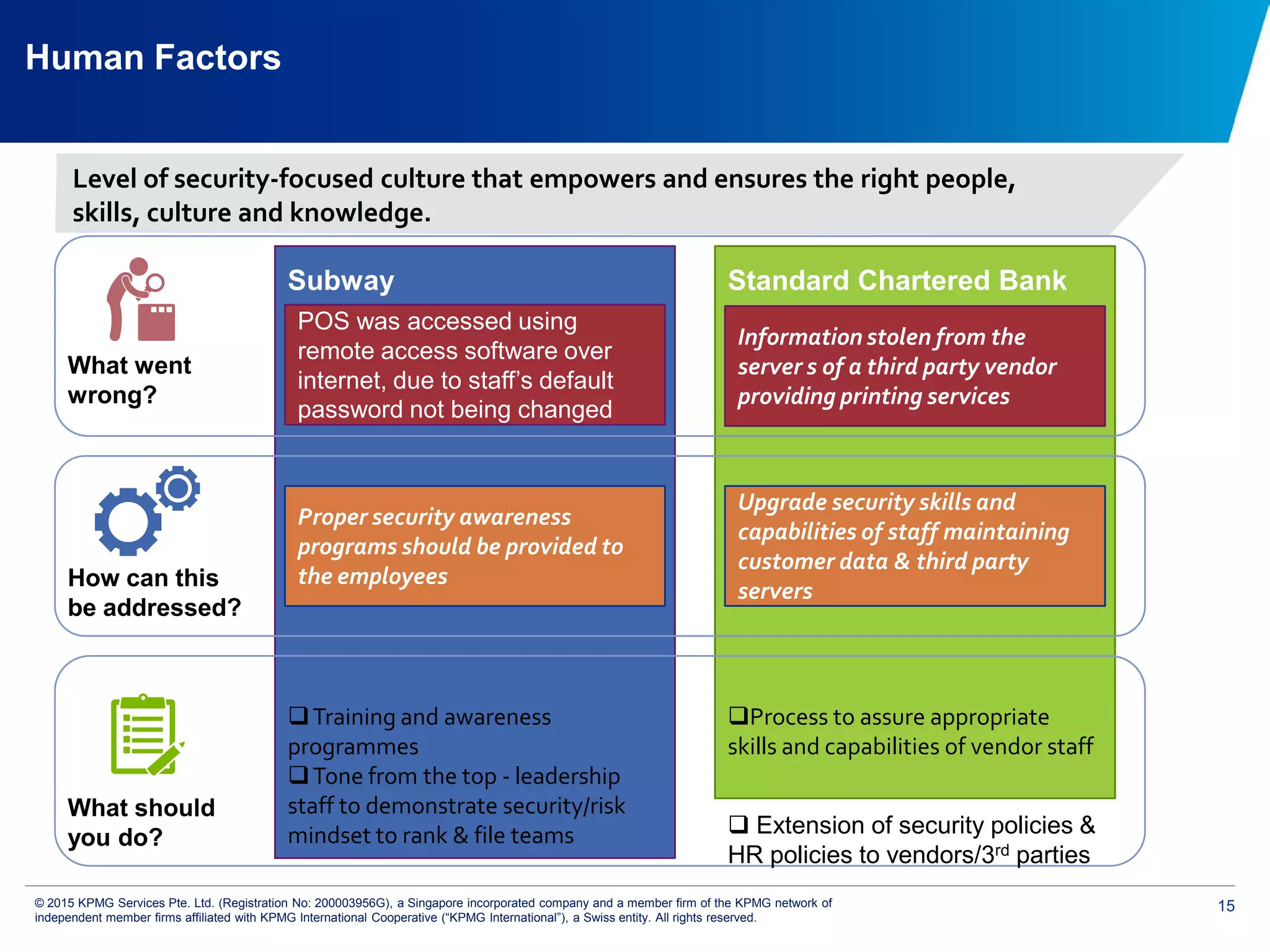
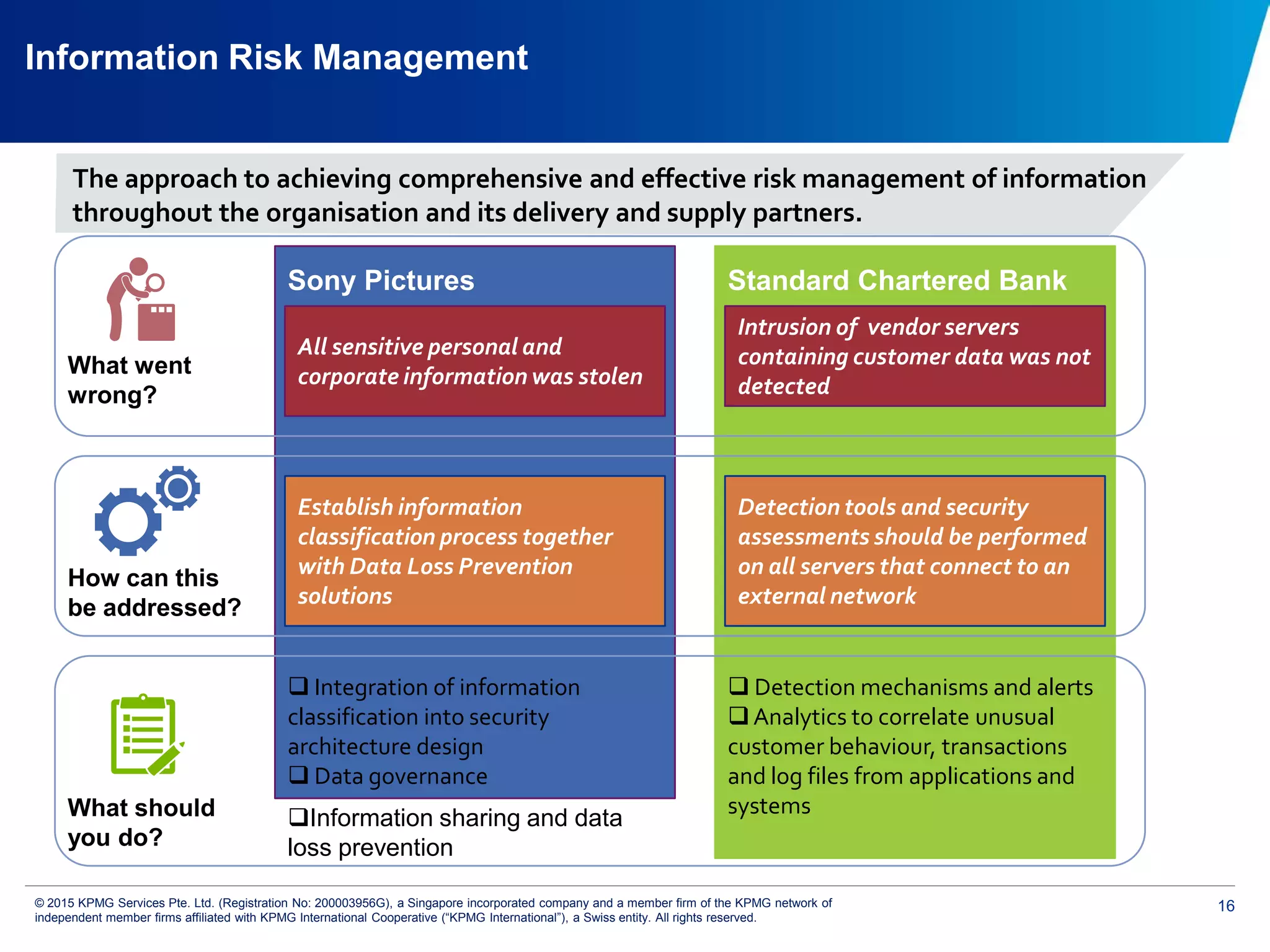
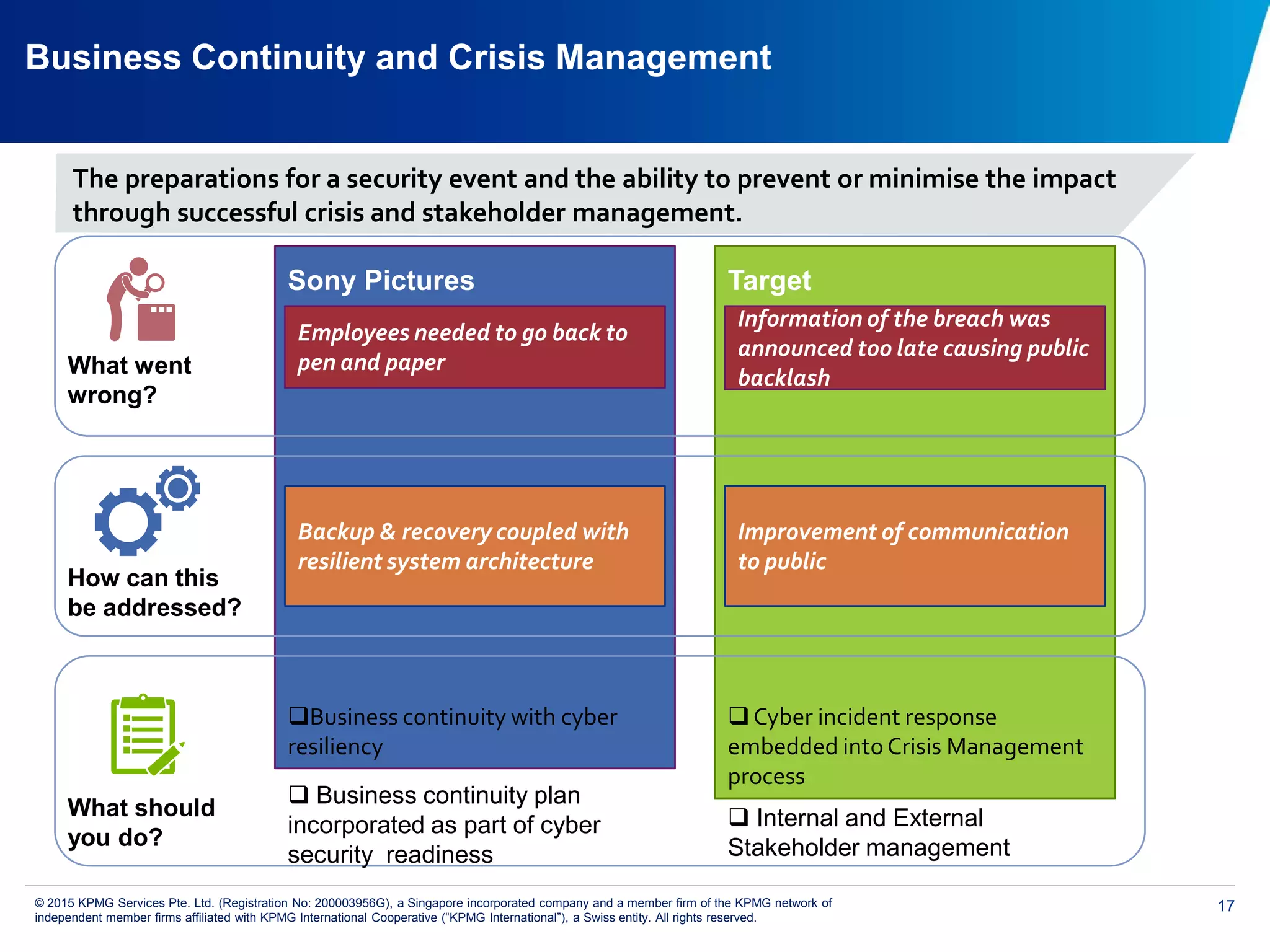
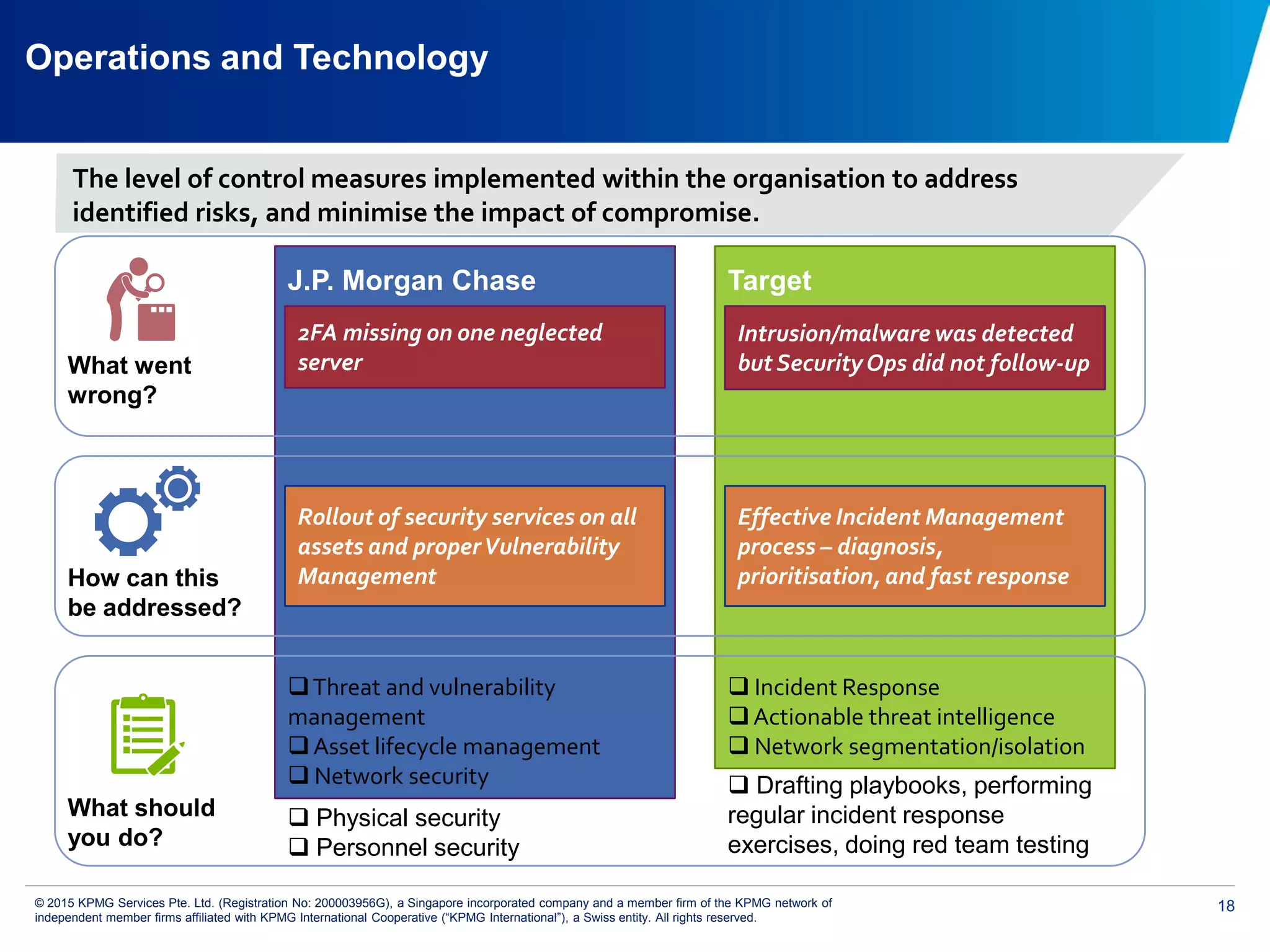
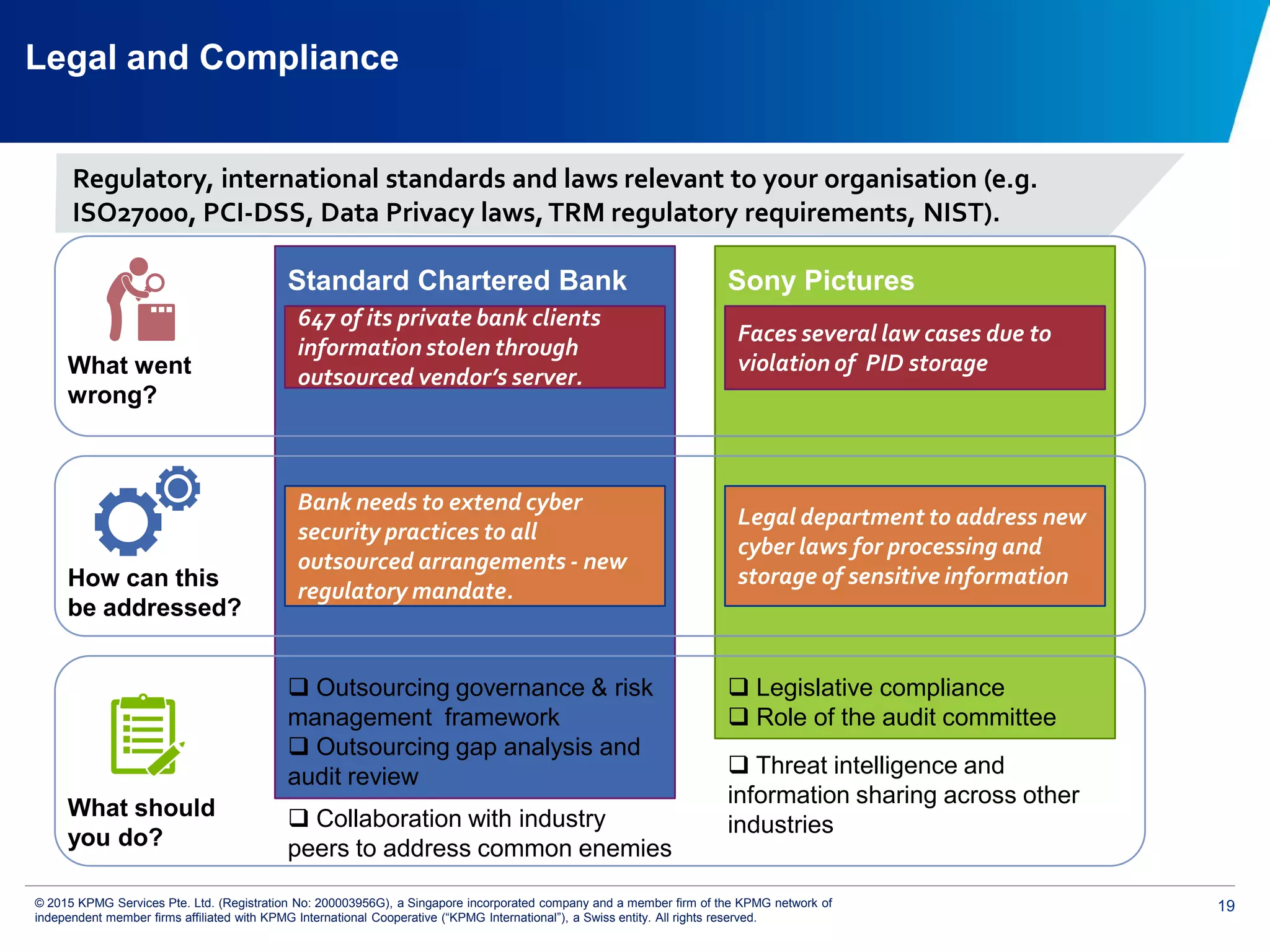
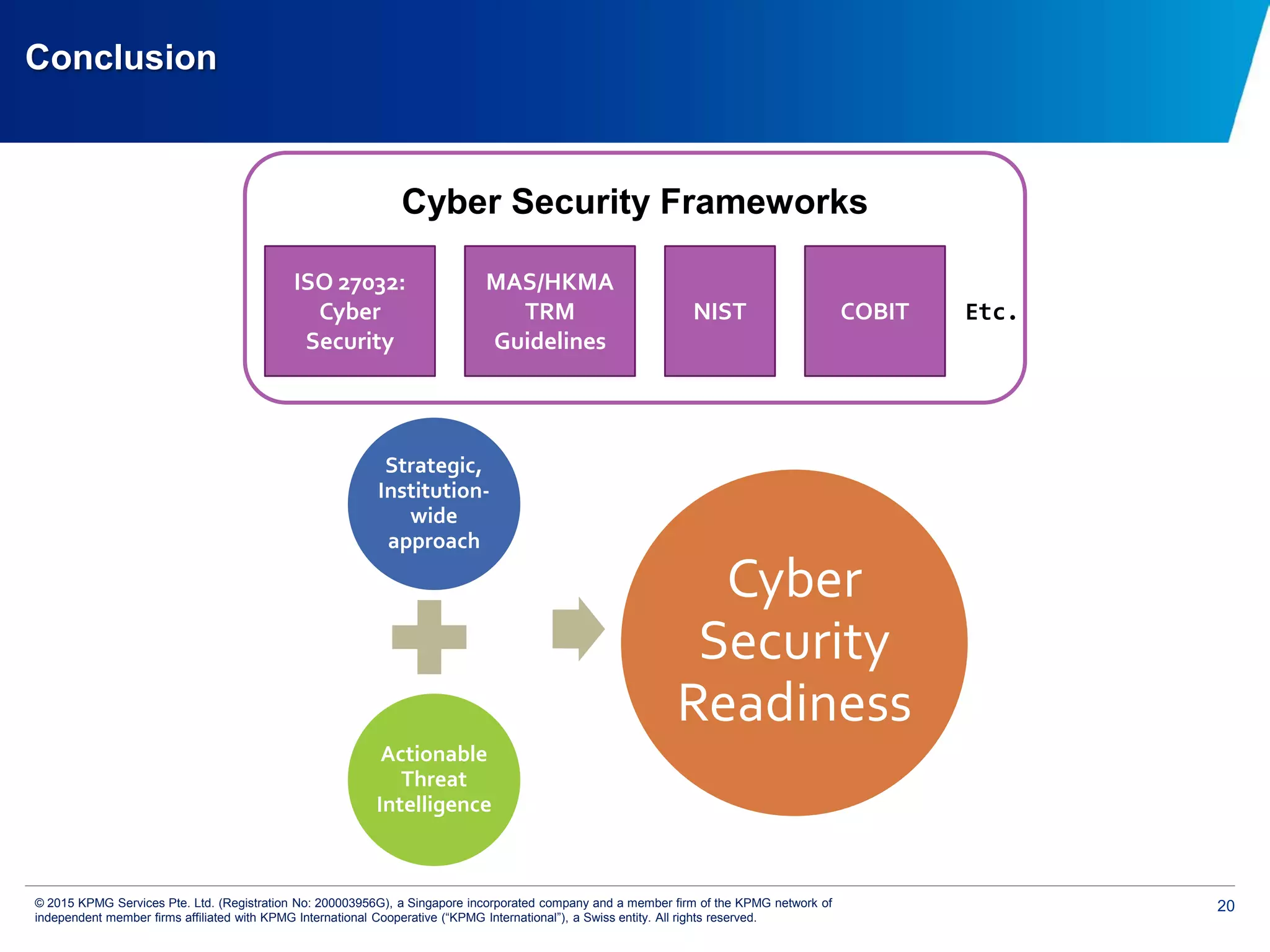
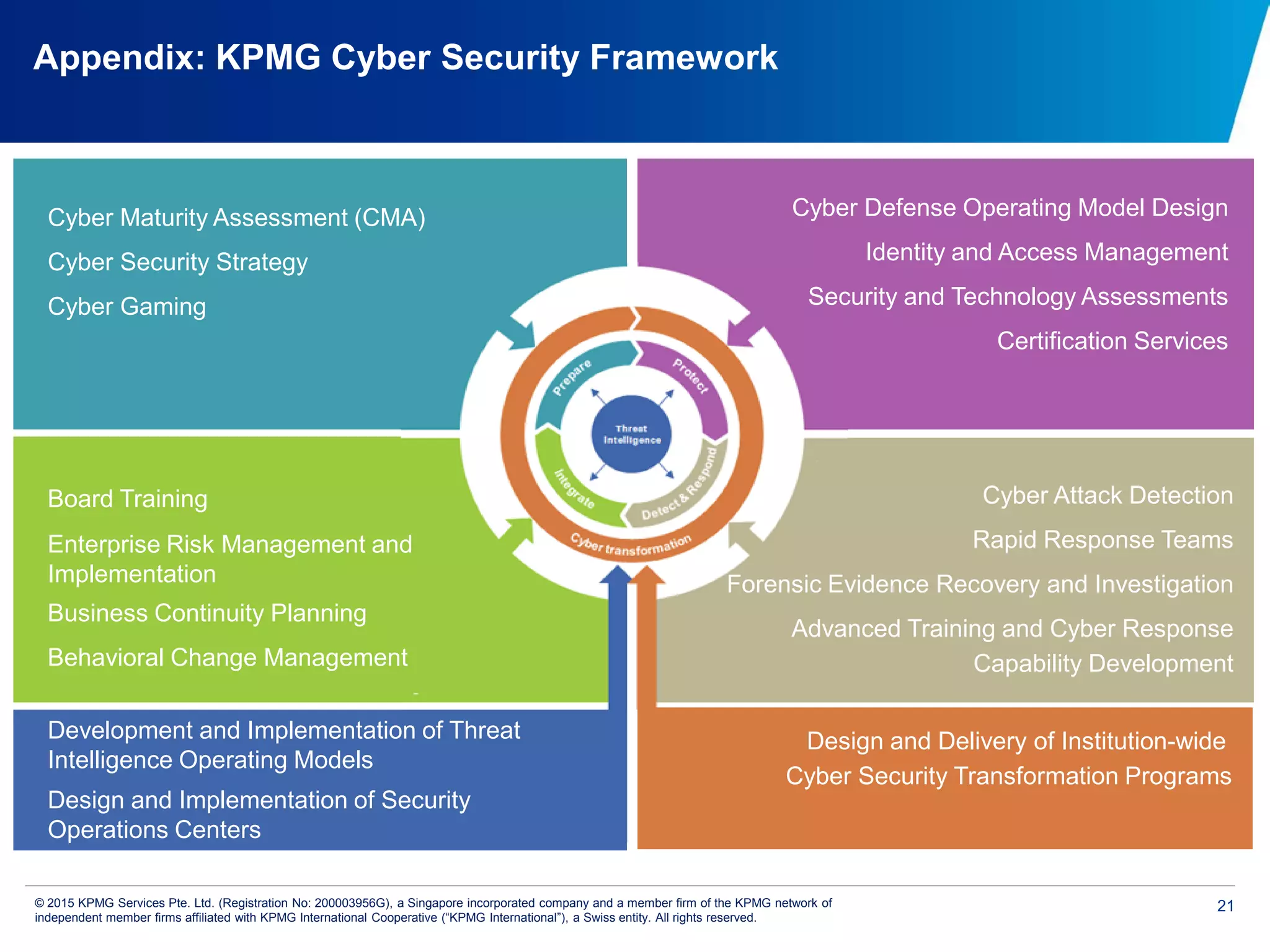
The document discusses the evolving cyber threat landscape and increasing risks posed by cyber attacks. It notes that cyber attacks are now the third largest risk facing corporations. Several high profile cyber attacks on companies like Target, Anthem, JP Morgan Chase, and Sony are summarized to illustrate the rising scale and impact of such incidents. The document advocates for a strategic, institution-wide approach to cyber security involving leadership, risk management, security operations, and resilience to protect against modern cyber threats. Threat intelligence and collaboration are also highlighted as important for effective cyber security.