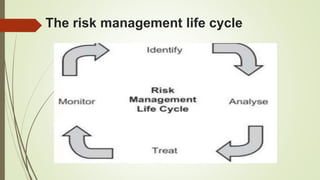
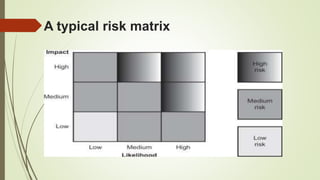
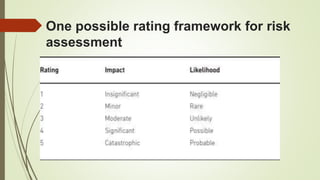
The document discusses information risk and provides examples of common risks such as data breaches, phishing attacks, and malware infections. It then covers threats to information systems, categorizing threats as accidental or deliberate, as well as internal or external. Vulnerabilities are also discussed and categorized. The risk management process involves identifying risks, analyzing impacts, assessing risks, treating risks, and continual monitoring. Risks are assessed qualitatively or quantitatively and tools can help with the assessment process.