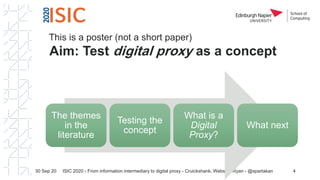
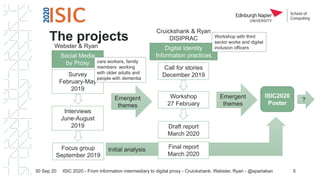
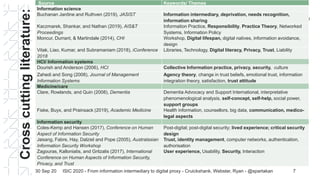
The document discusses the concept of 'digital proxy' as an evolution of the information intermediary role, particularly in the context of assisting older adults and people with dementia. It highlights emergent themes such as digital identity and trust within proxy relationships, and outlines potential future research directions related to digital proxy practices. The authors emphasize the complexities and implications of digital identity management and the role of various stakeholders in these processes.