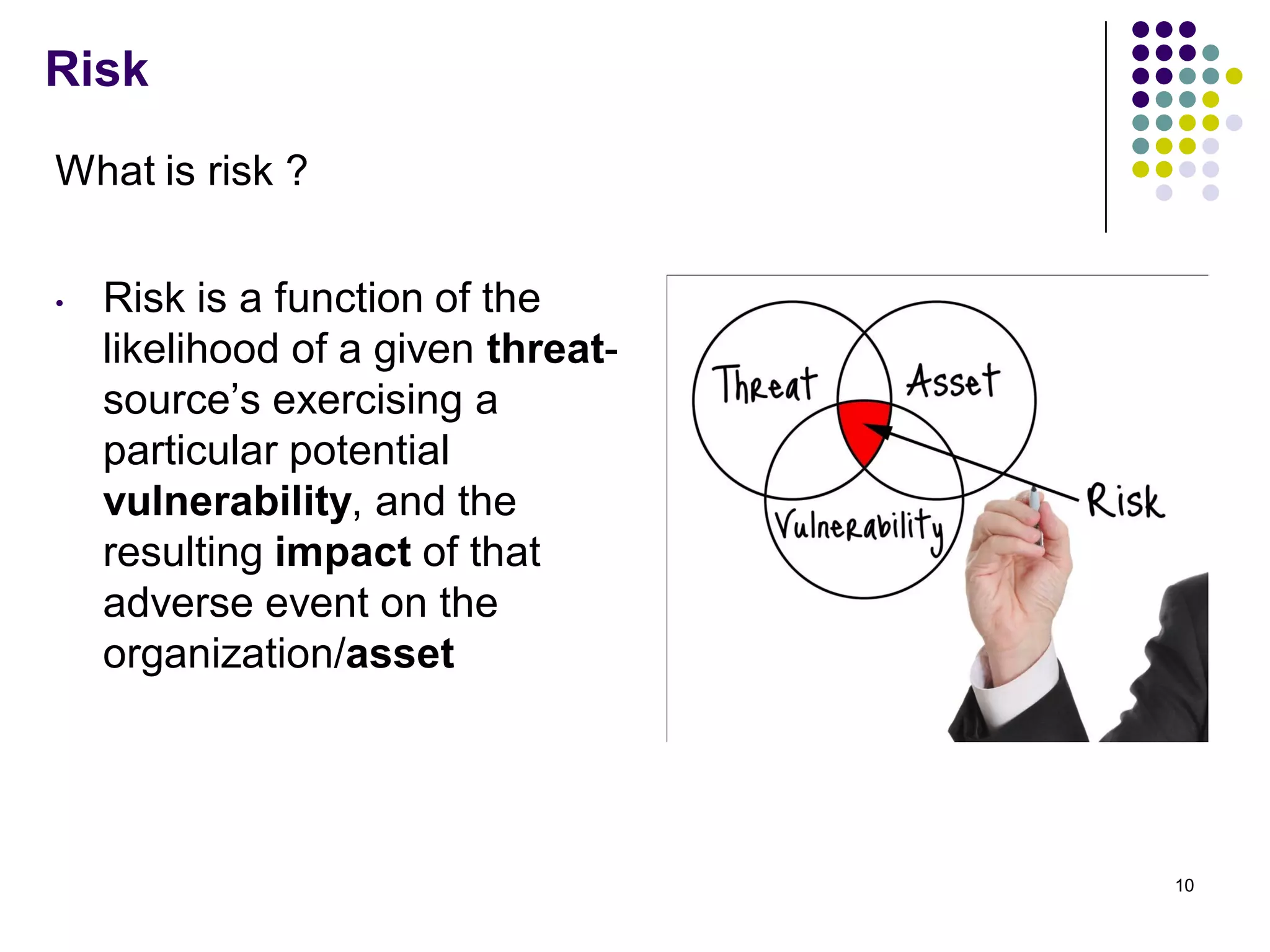
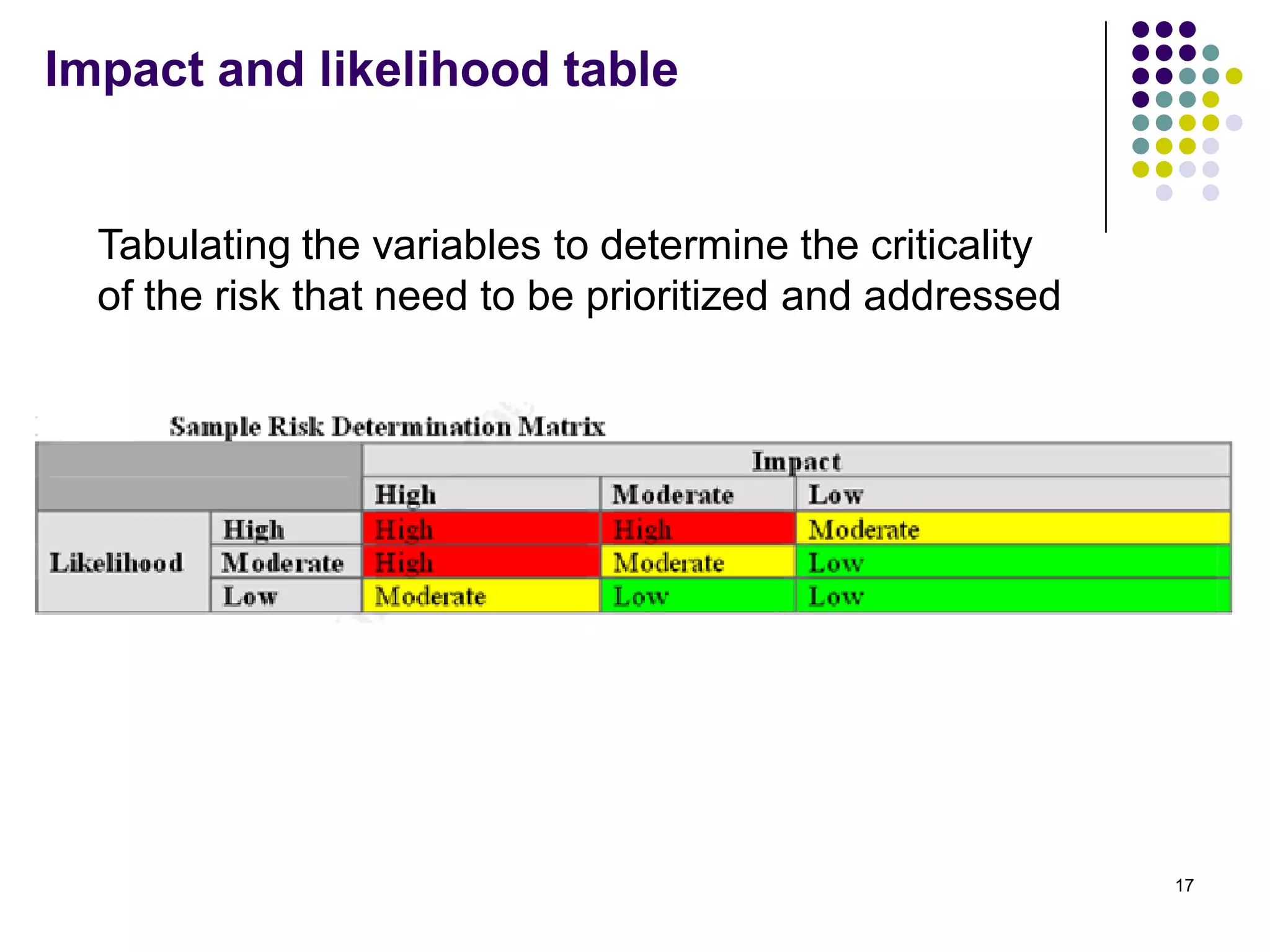
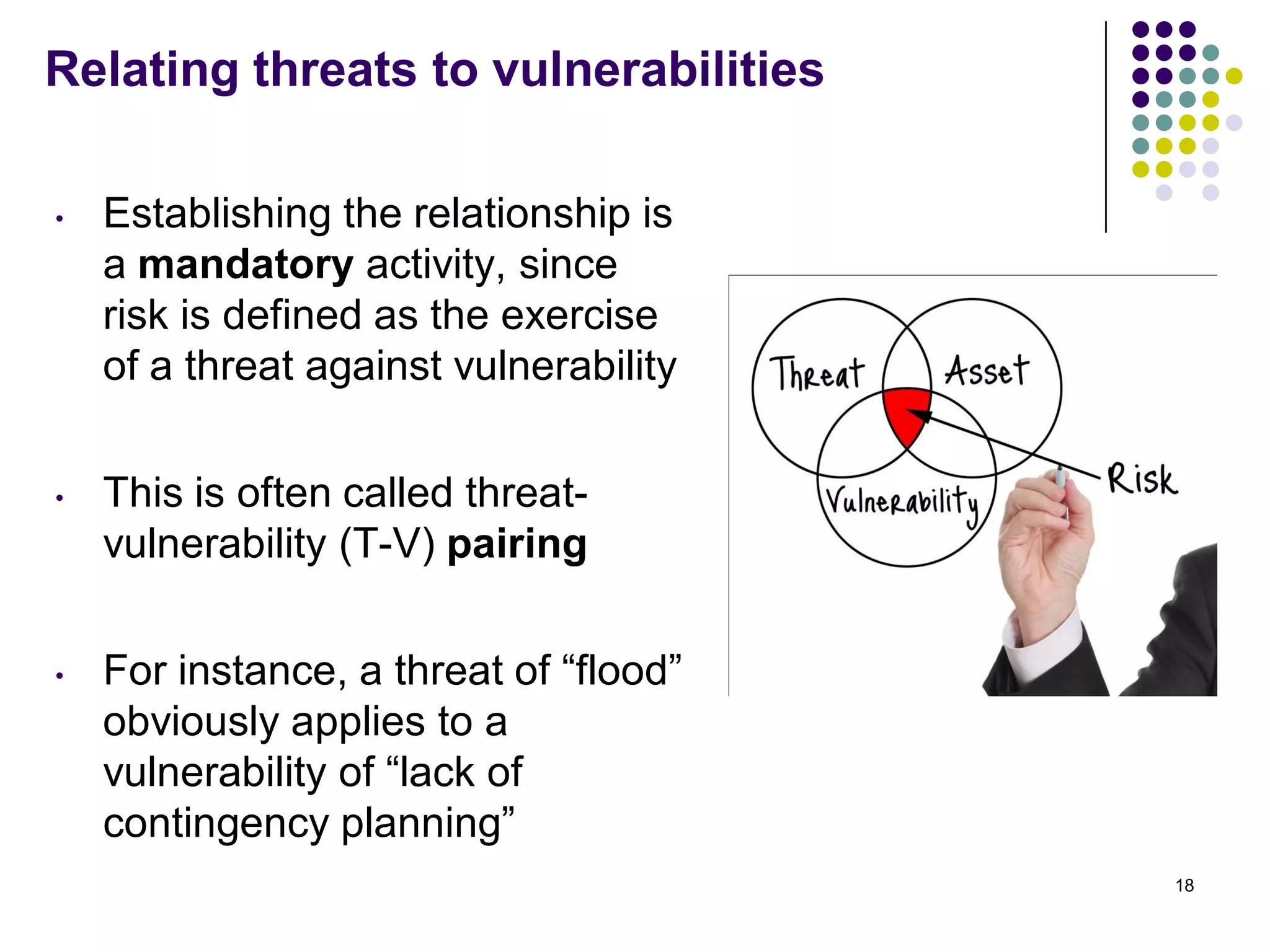
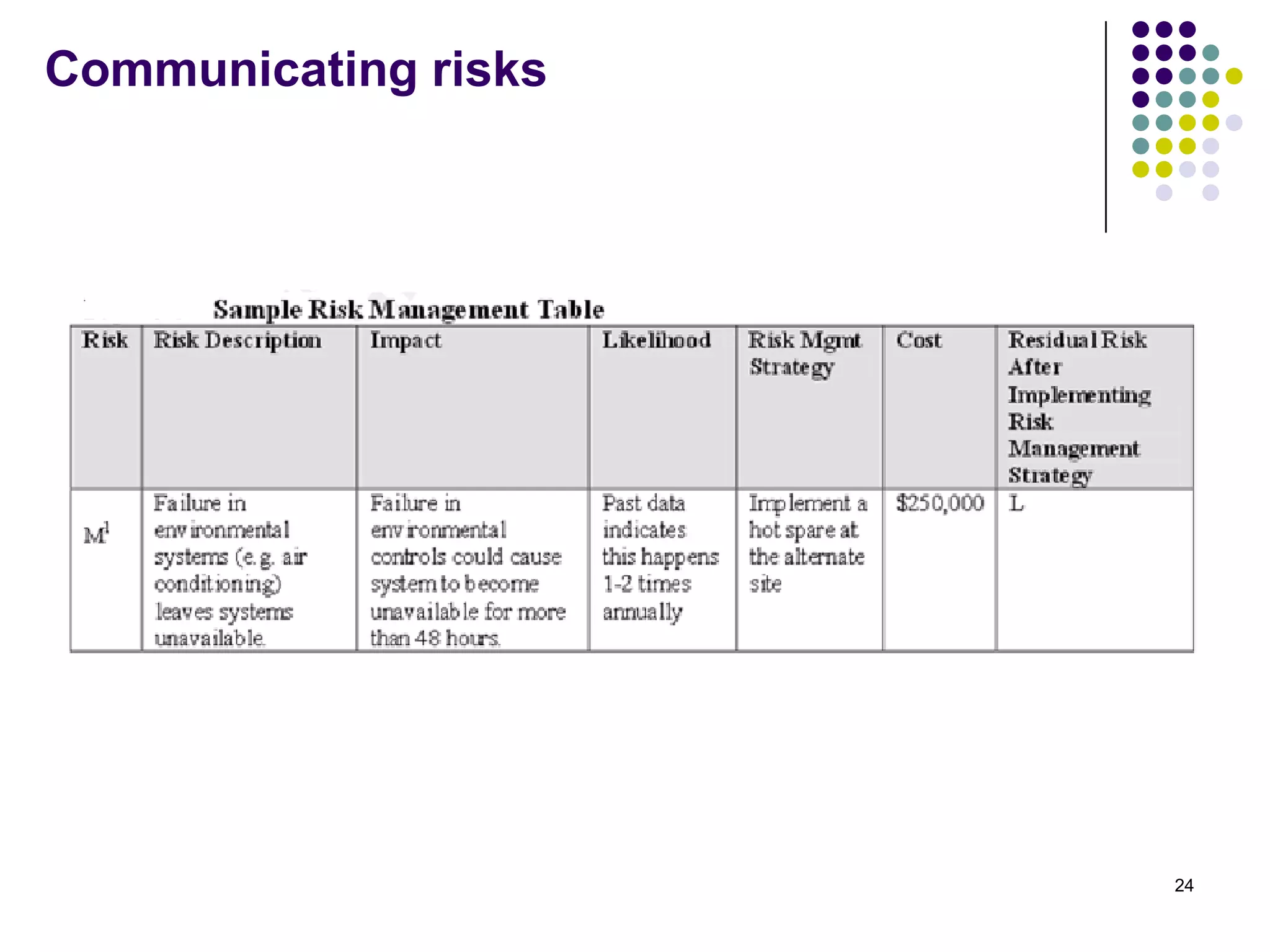
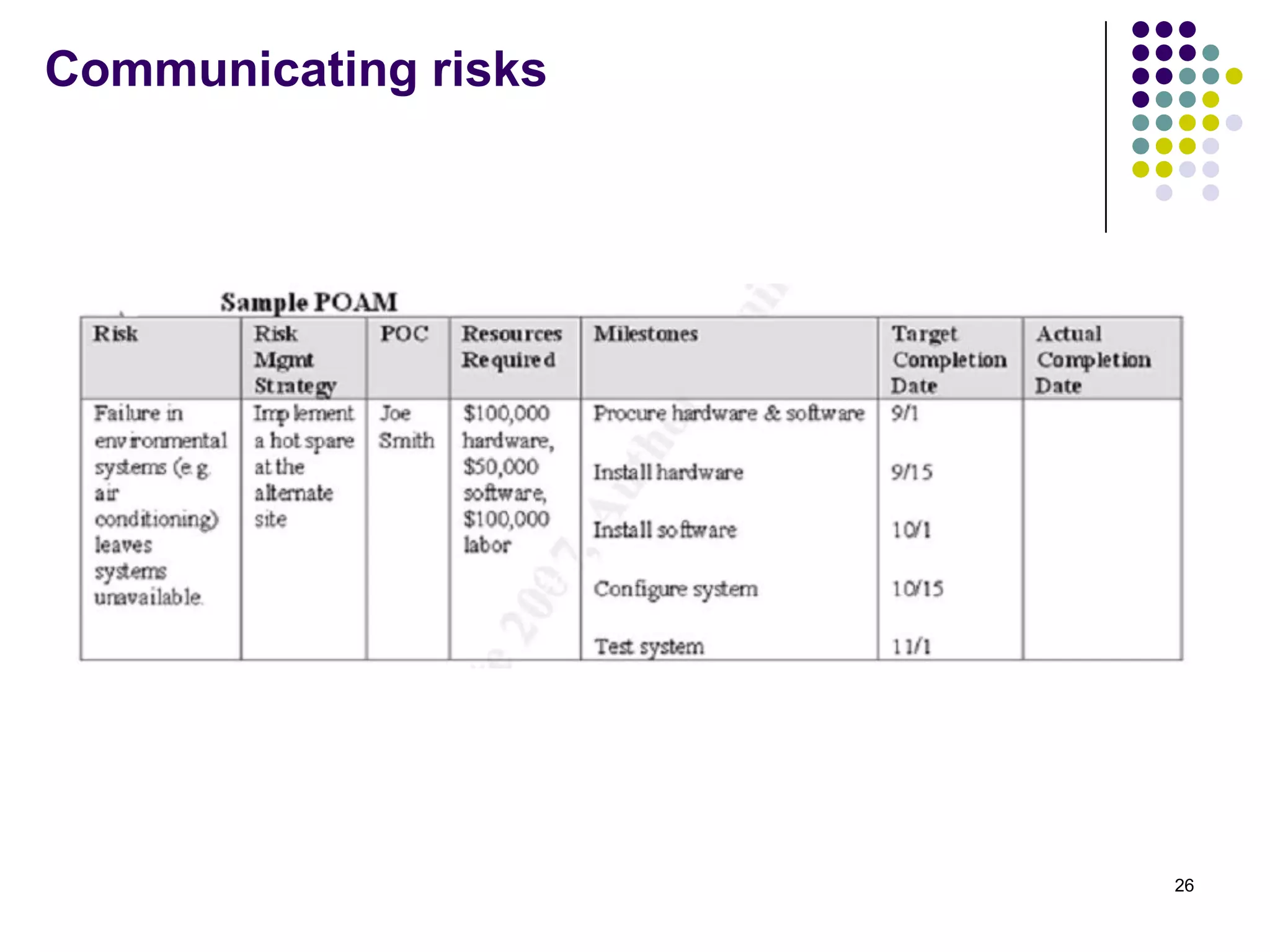
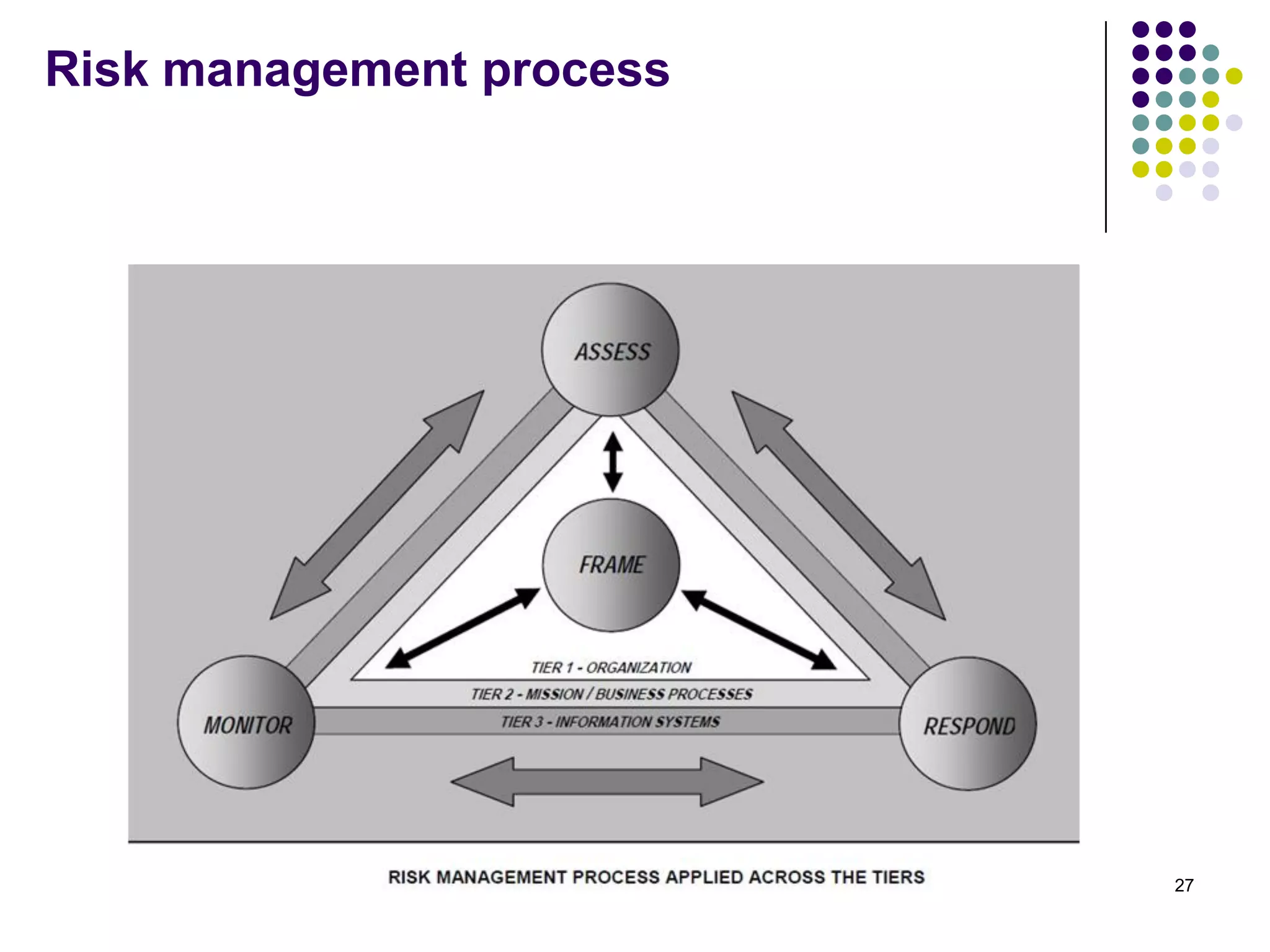
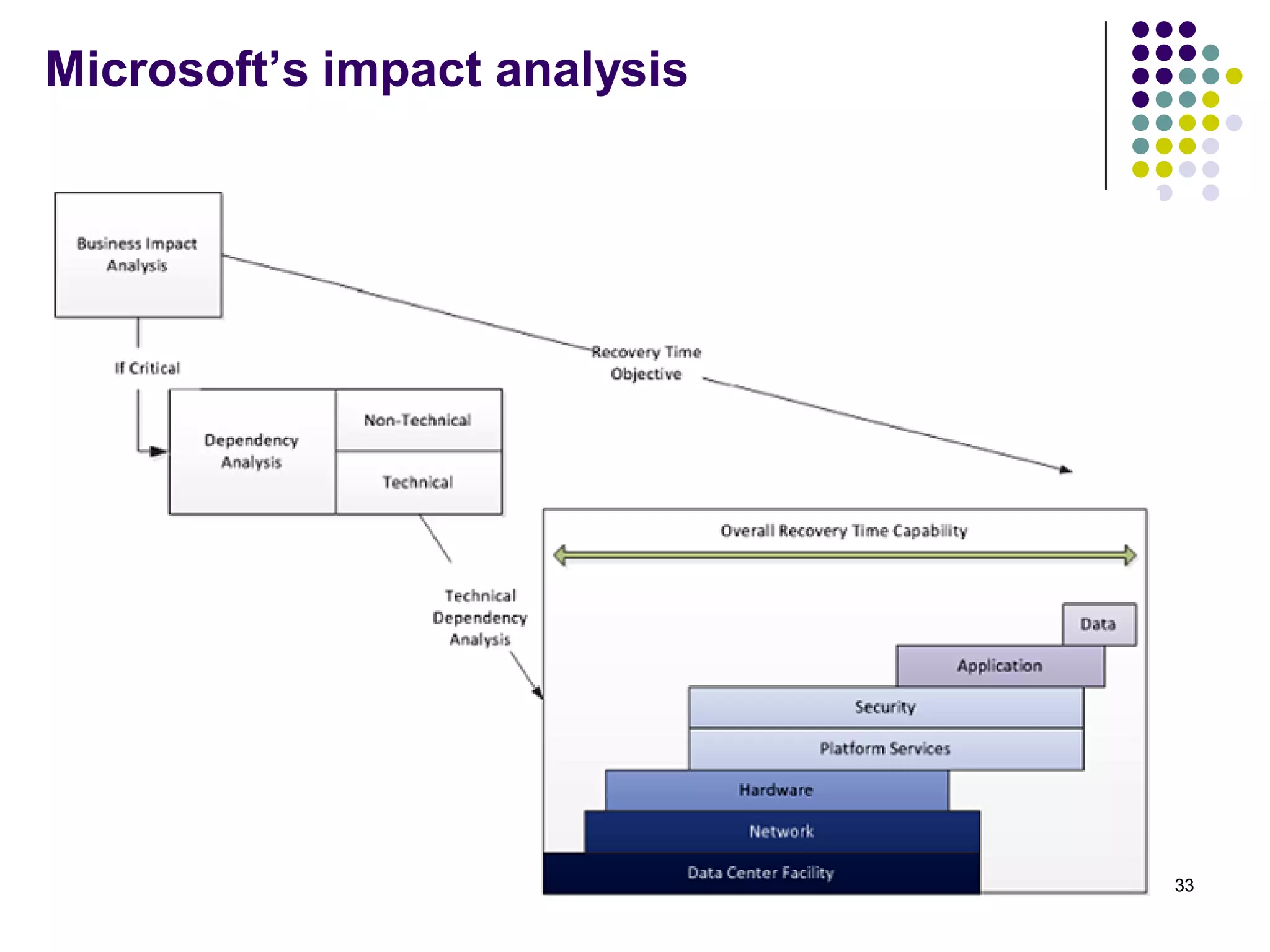
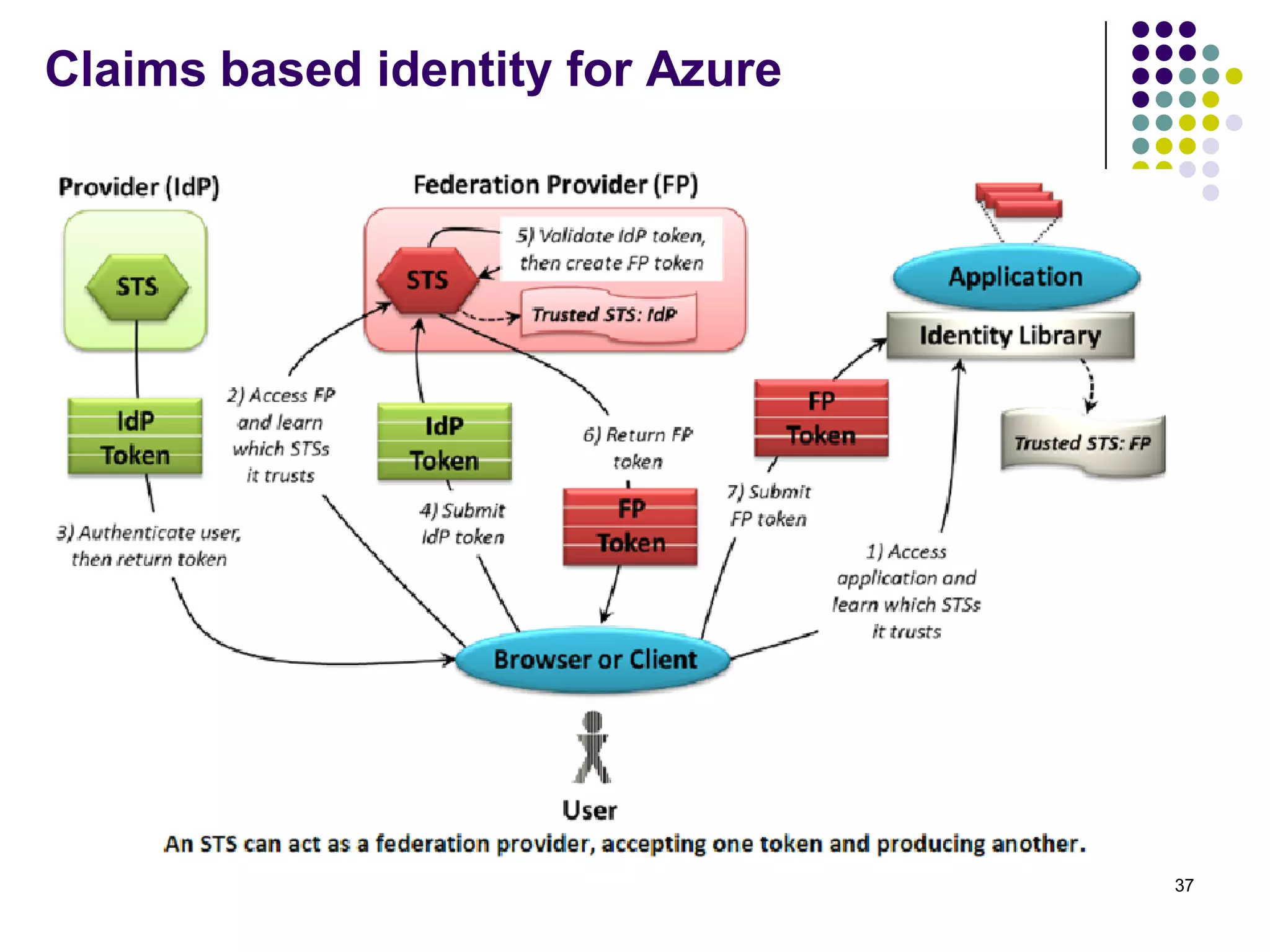
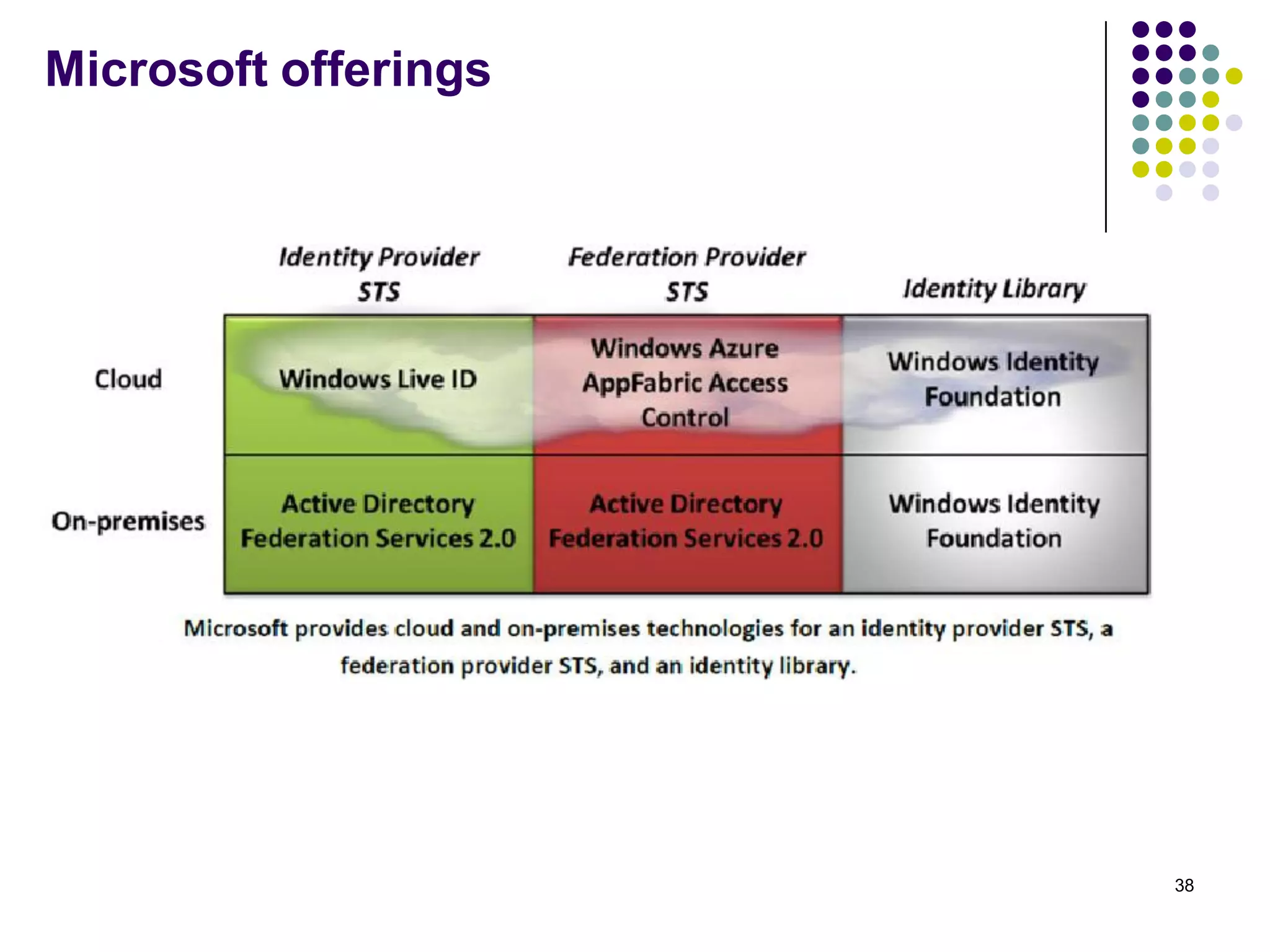
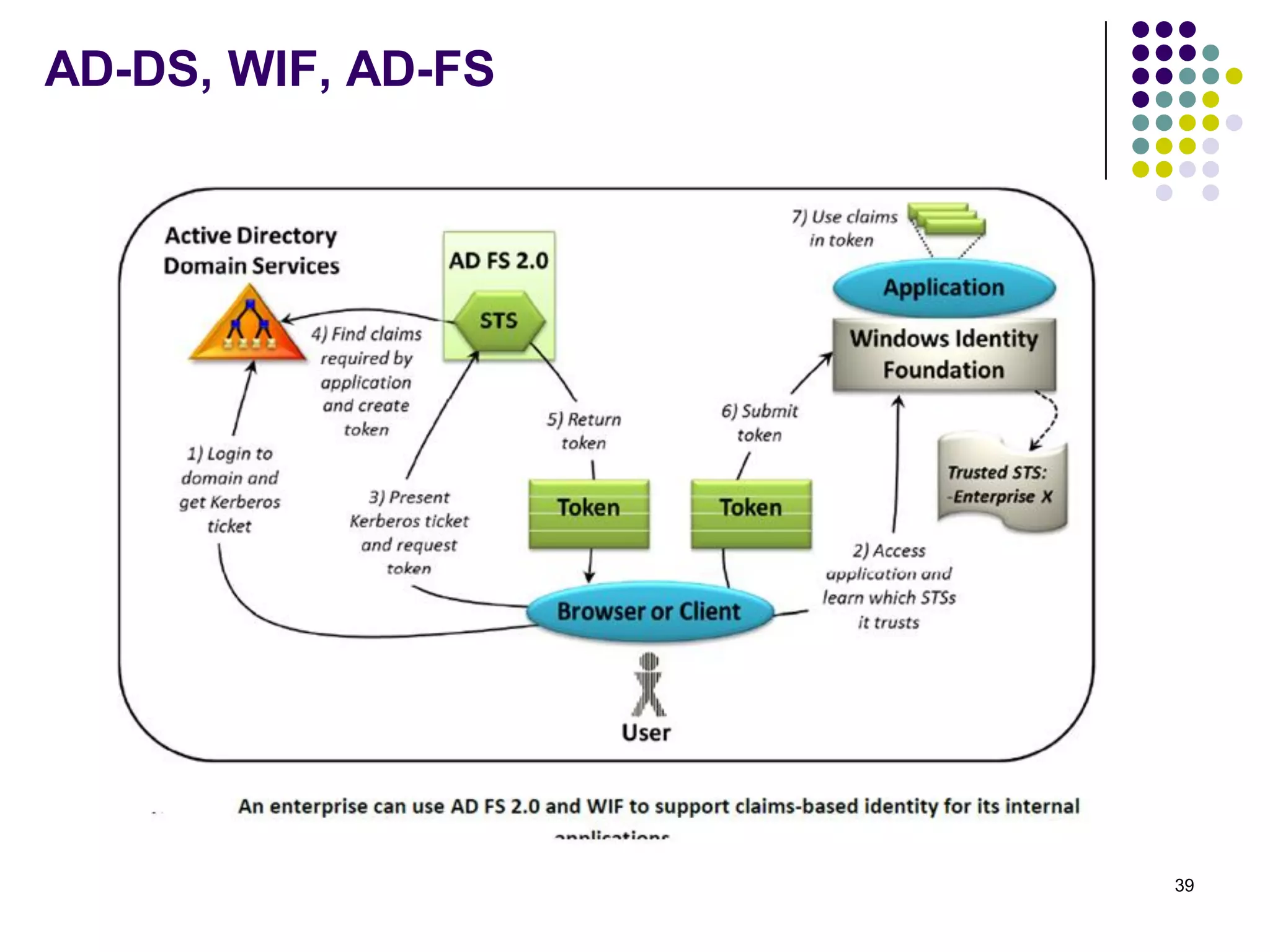
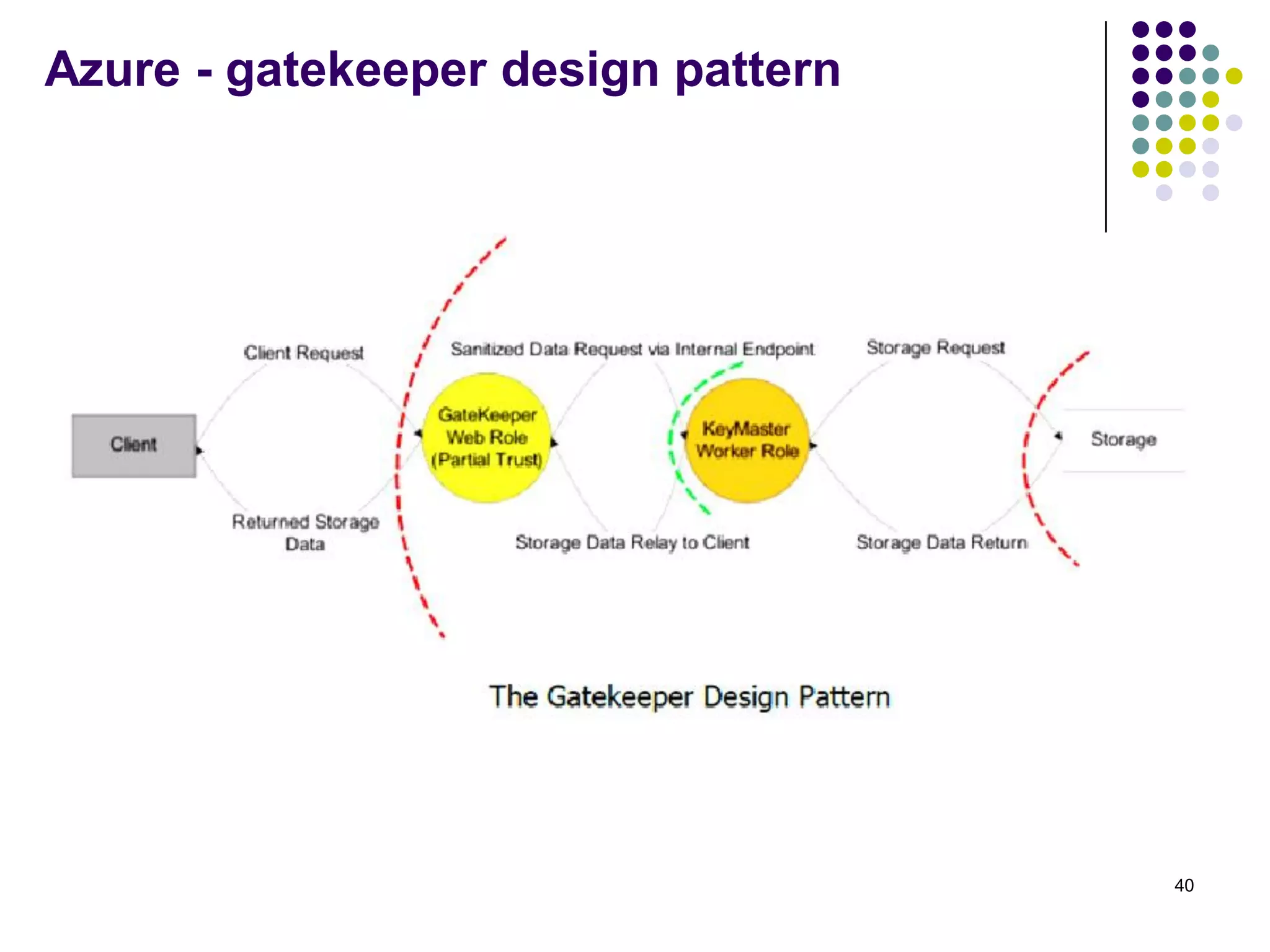
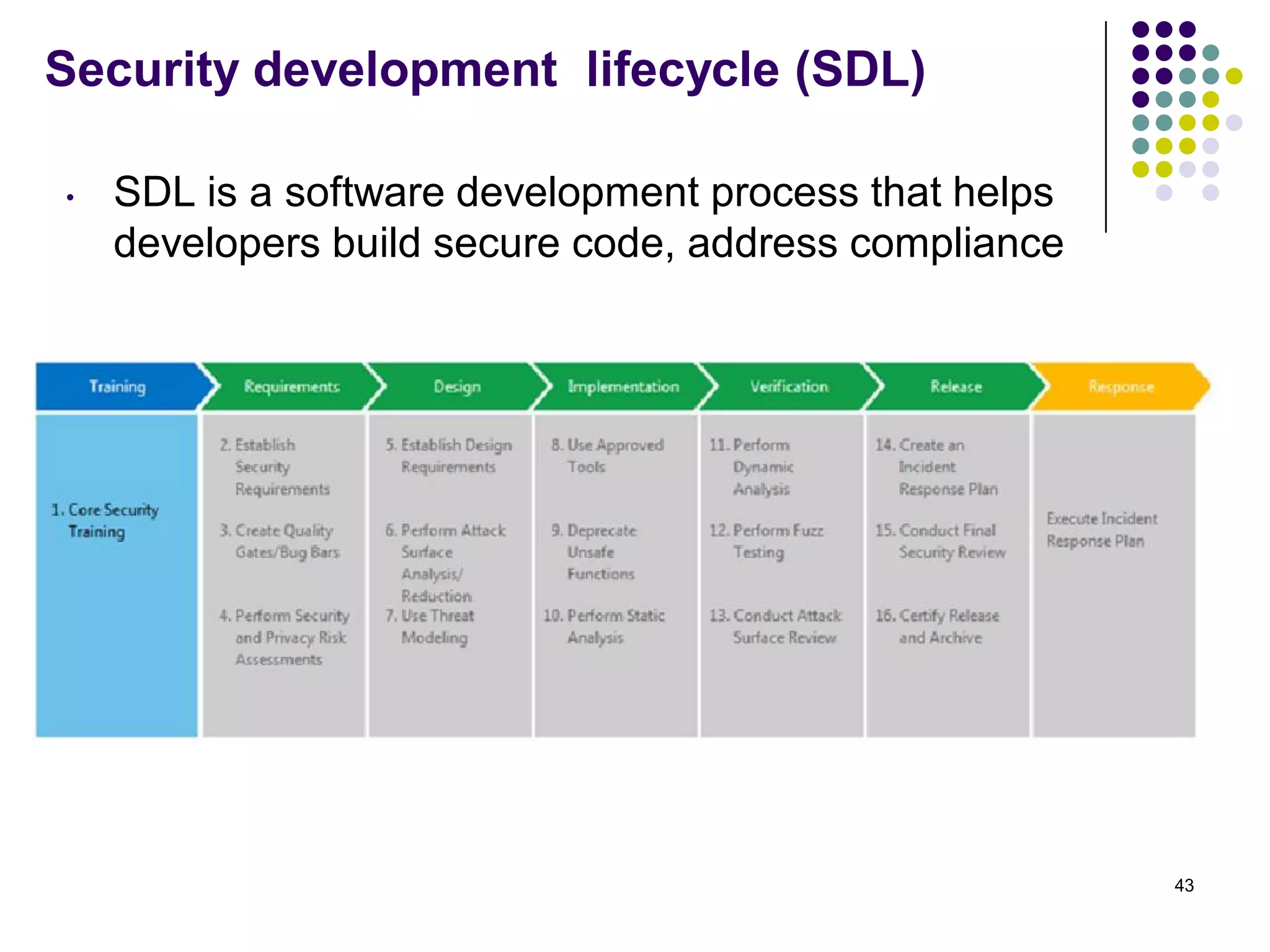
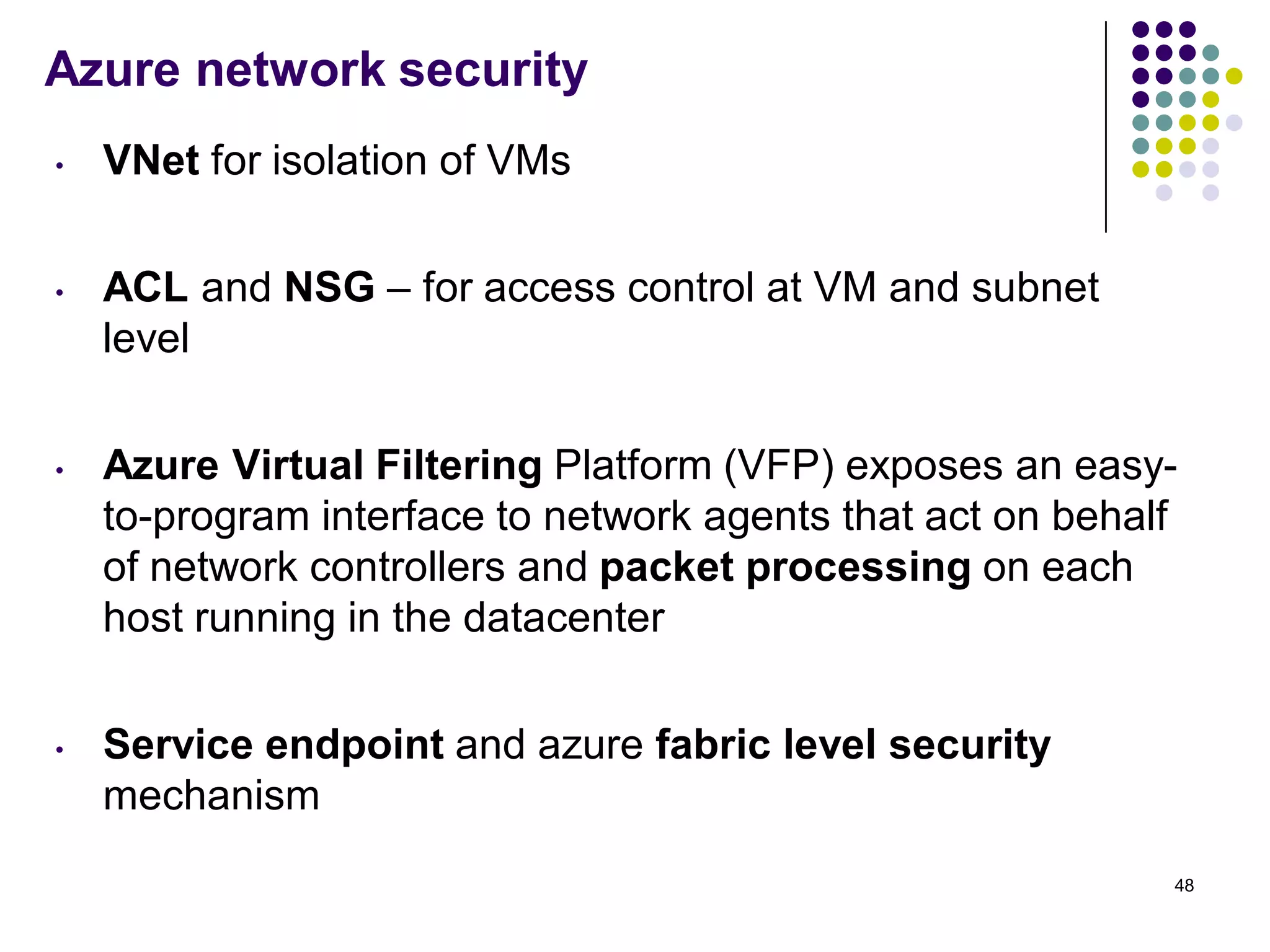
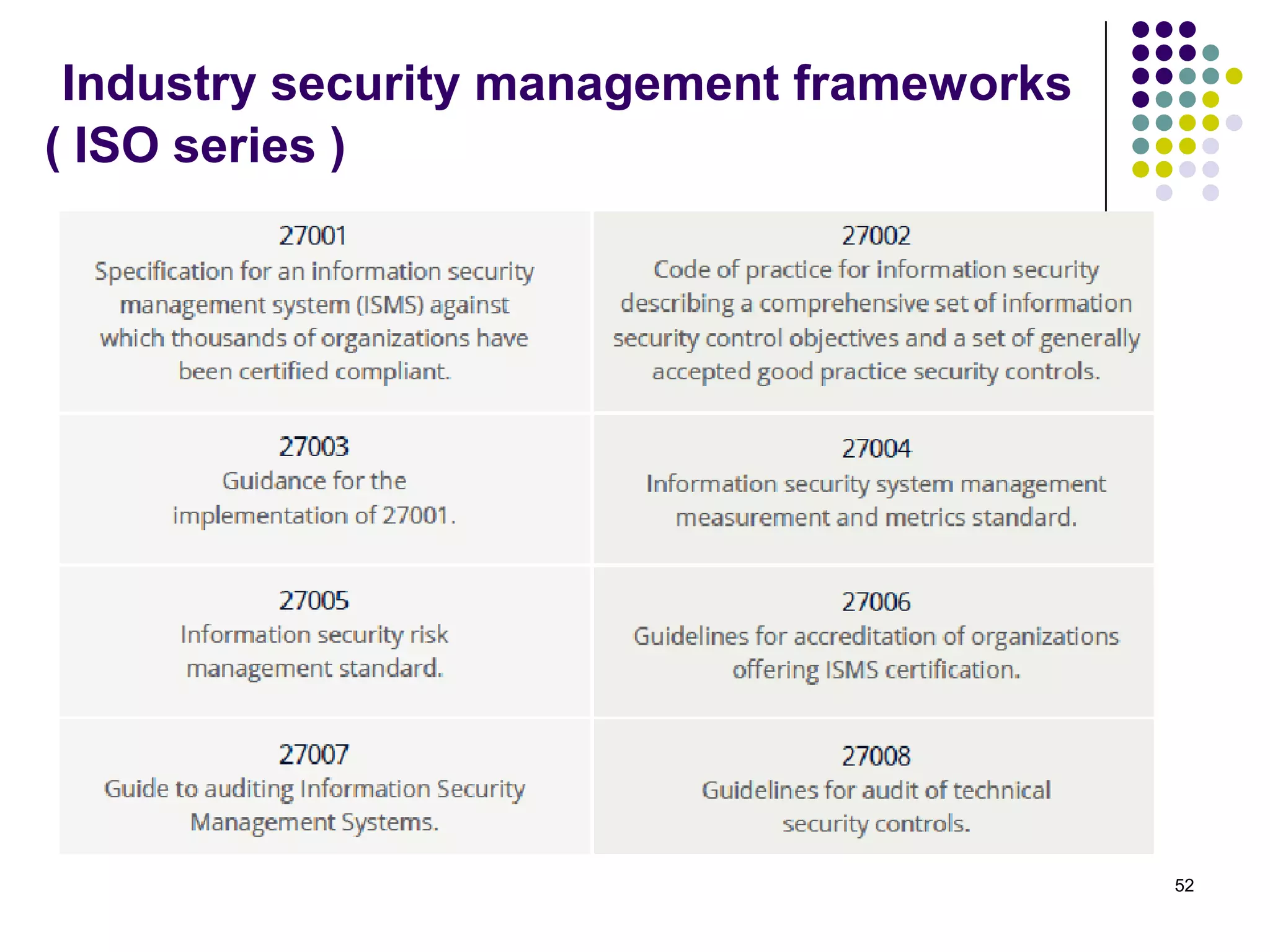
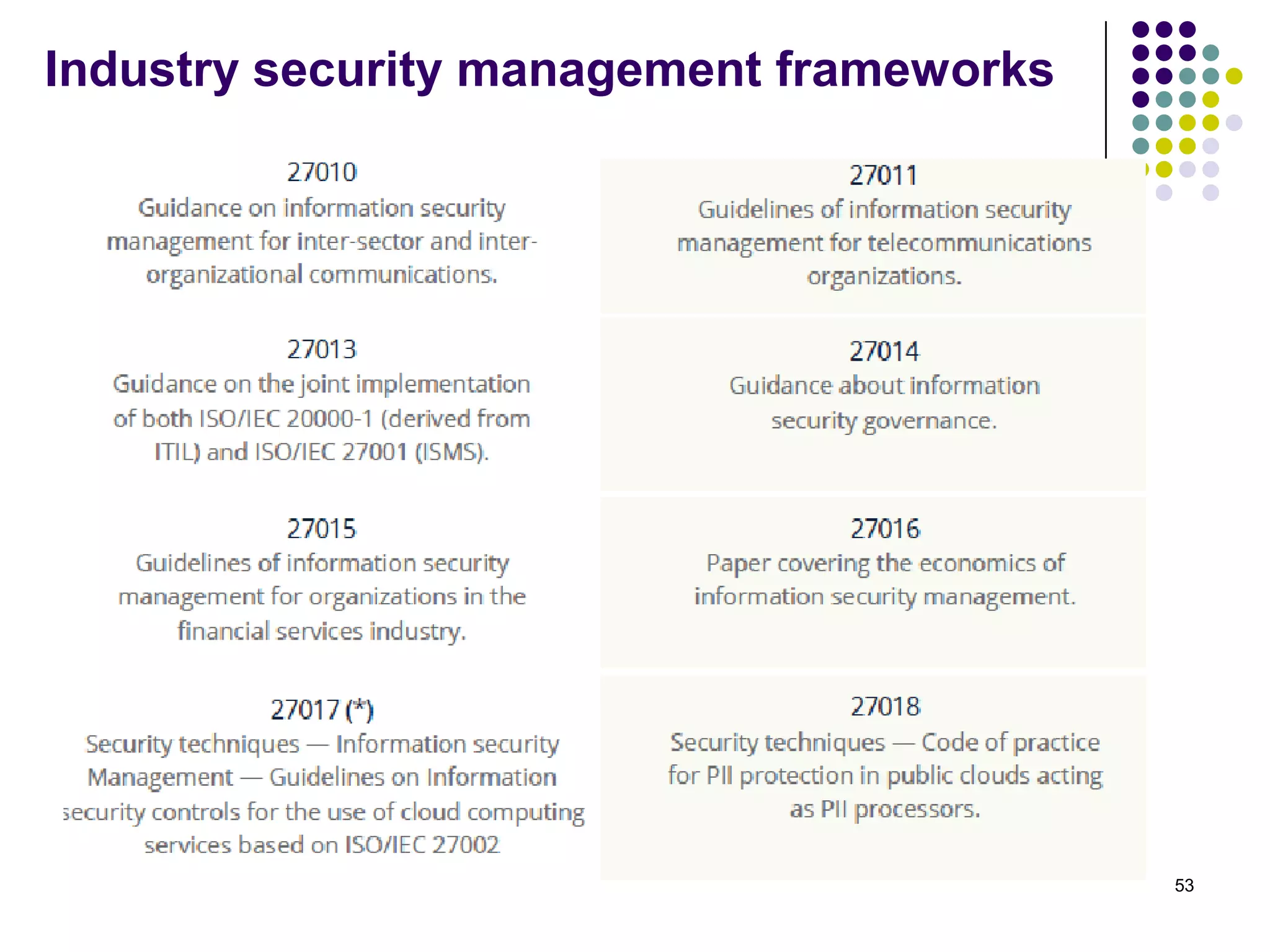
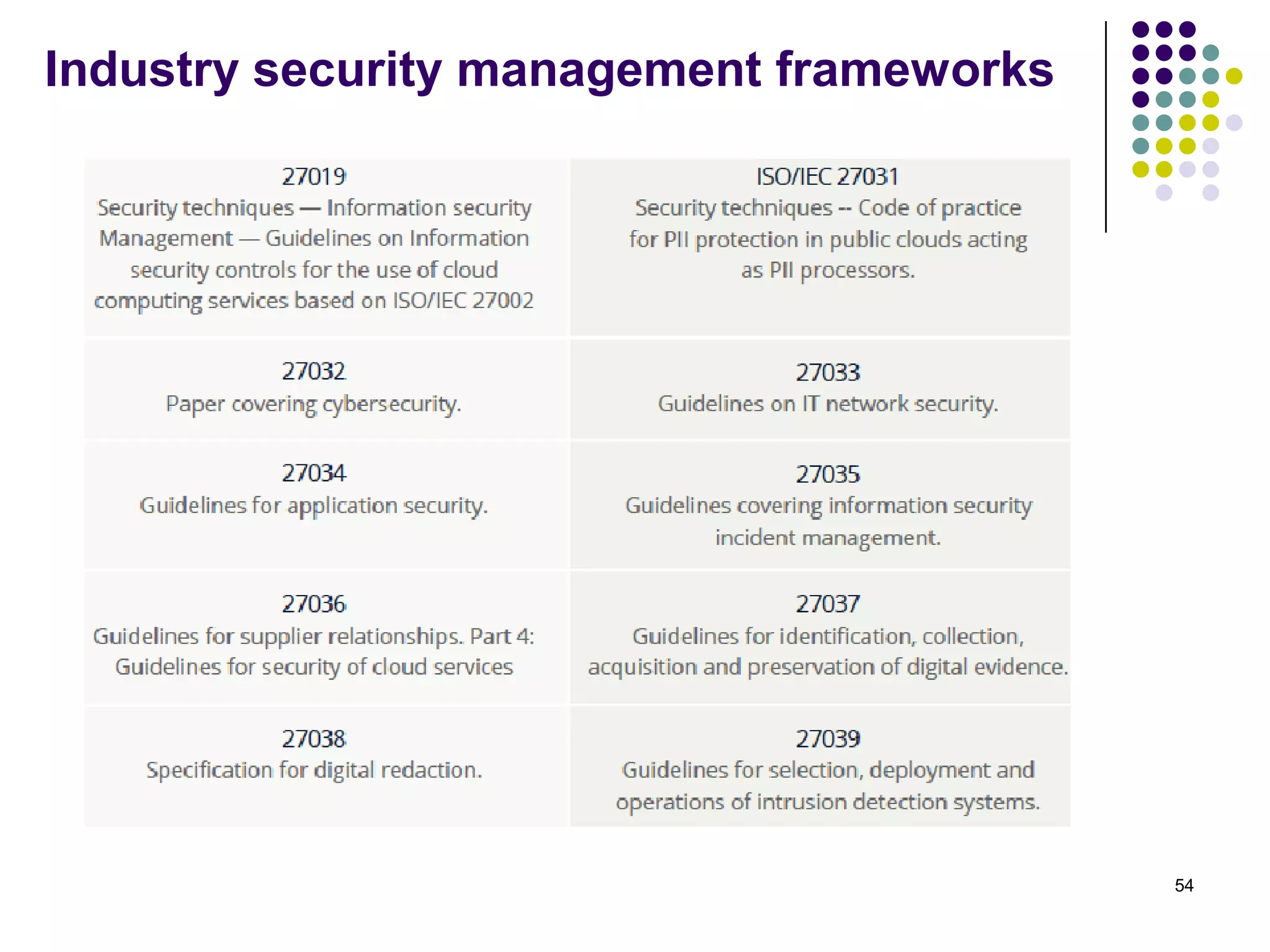
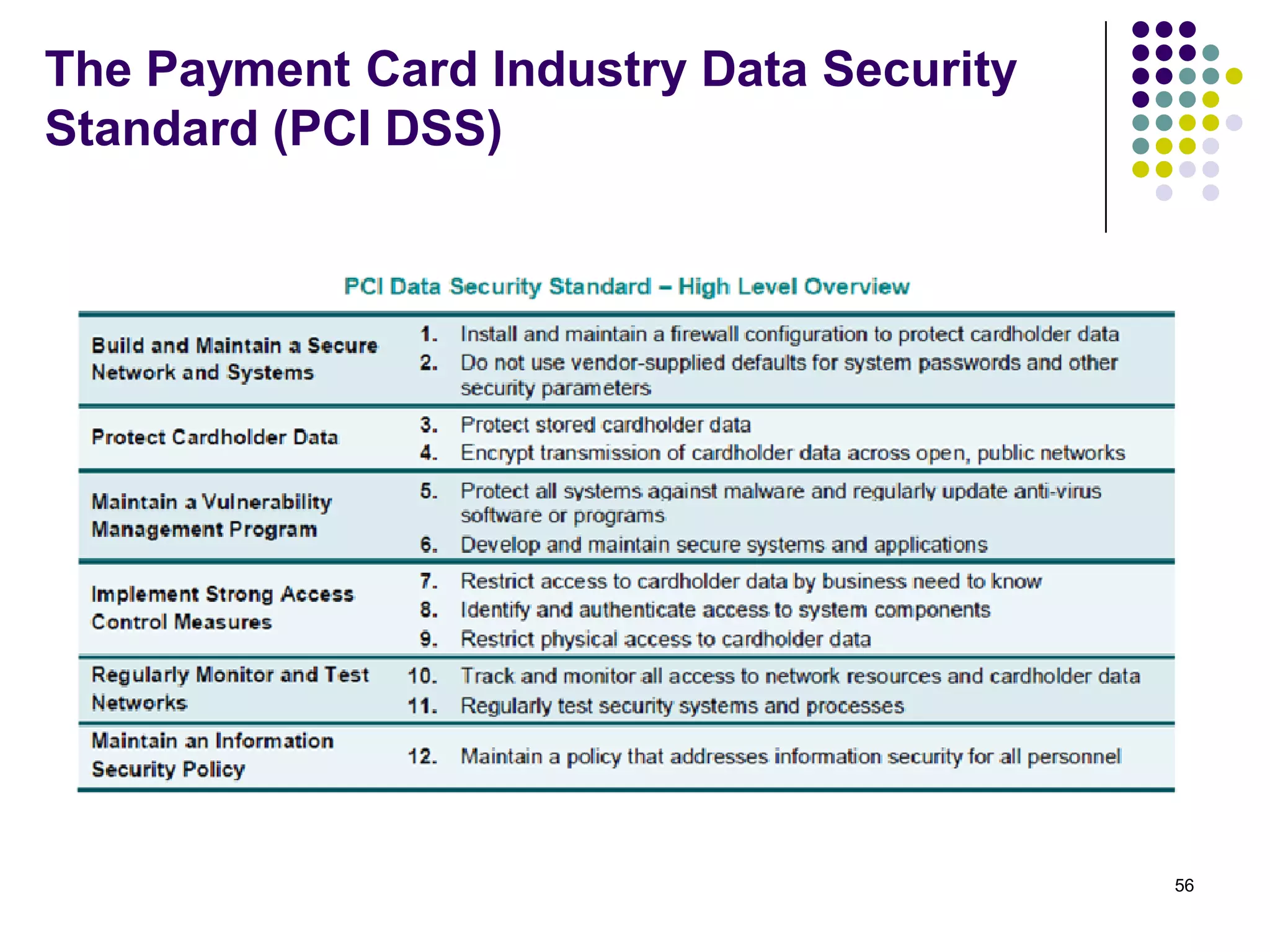
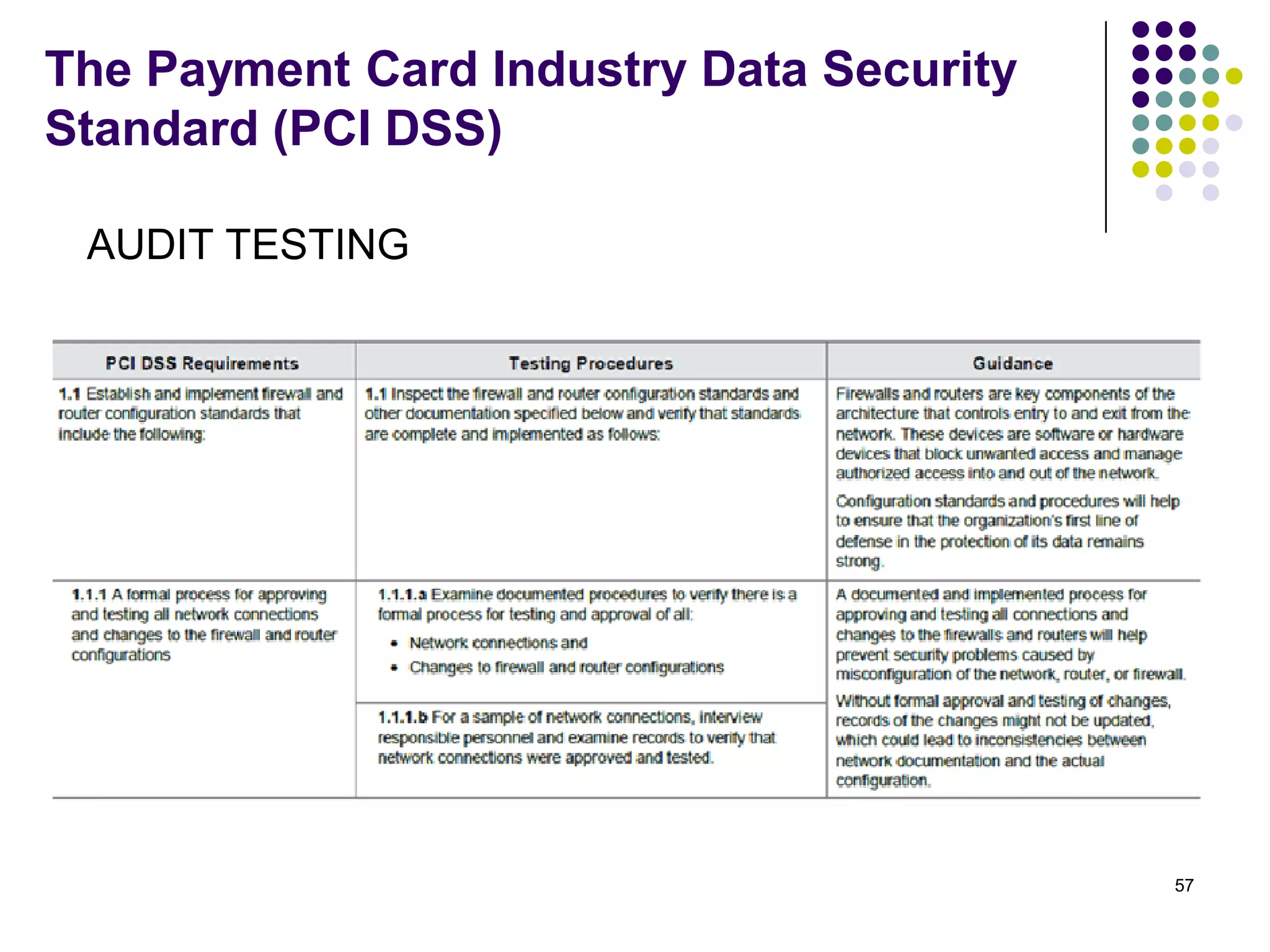
Vijay Mohire presented information on his planned contributions to Microsoft's ACE (Assessment, Consulting & Engineering) team. He outlined how he would assist with risk assessments, compliance checks, security consultations, engineering tasks, and program management. The presentation also provided an overview of Microsoft's information security practices, including its security stack, tools like Azure and Active Directory, and adherence to standards like NIST and PCI DSS.