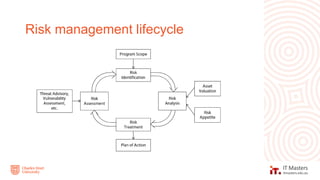
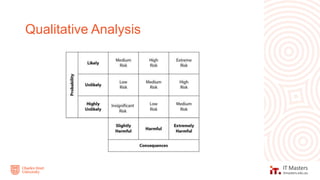
The document discusses concepts related to information security governance and risk management. It covers identifying risks through frameworks and assessments, analyzing risks through likelihood and impact, and treating risks through controls, compliance, and cost-benefit analysis. Maintaining a risk register is important for recording risks, assessments, and mitigation activities over time.