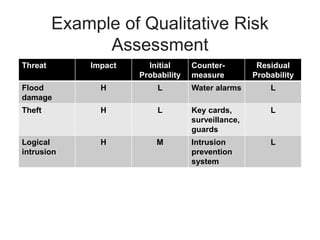
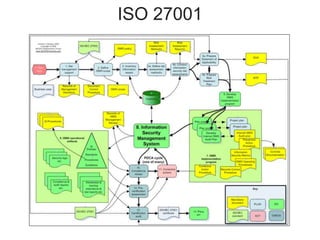
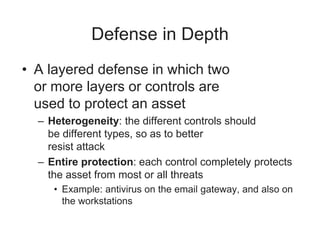
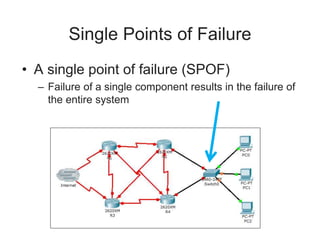
This document provides an overview of key concepts in information security and risk management. It discusses how security supports organizational mission, objectives and goals. It also covers risk management concepts like qualitative and quantitative risk assessment, and risk treatment strategies like risk acceptance, avoidance, reduction and transfer. Additional security management concepts explained include the CIA triad, defense in depth, single points of failure, and privacy. The role of policies, governance, and executive oversight in security management are also summarized.