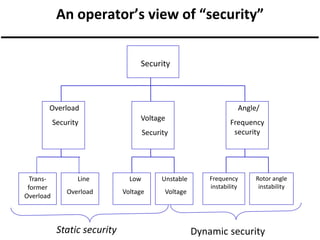
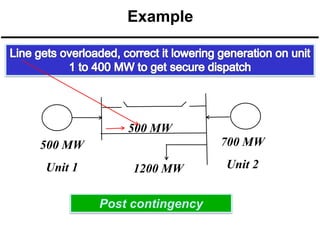
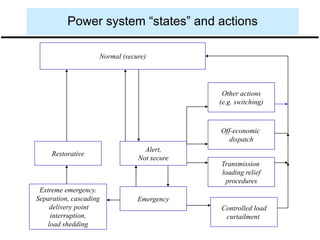
The document discusses power system security, which includes maintaining reliability and preventing contingencies from causing violations. It is broken into three main functions: system monitoring, contingency analysis, and security constrained optimal power flow. Contingency analysis models different outages to operate the system defensively. Security constrained optimal power flow seeks optimal dispatches to prevent violations from any contingencies. The document defines different system states like normal, alert, emergency and explains control actions taken to transition between states or restore the system.