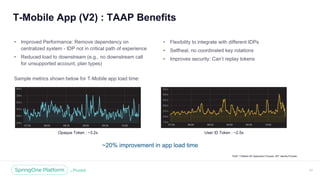
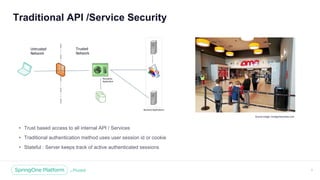
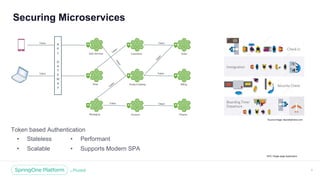
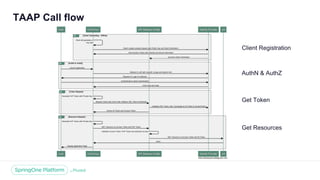
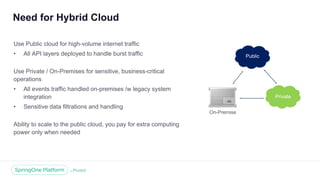
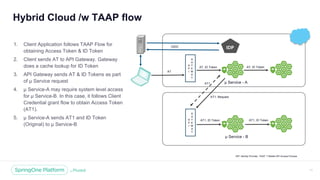
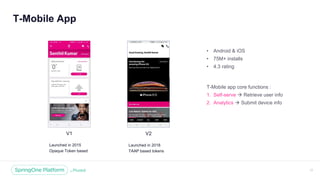
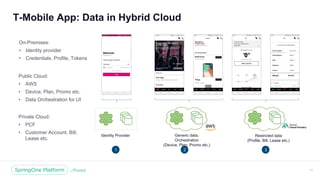
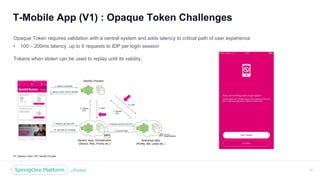
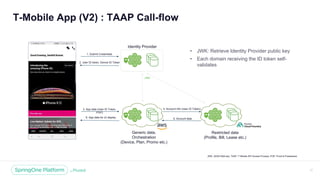
The document discusses the security of microservices within T-Mobile's hybrid cloud architecture, detailing the shift from monolithic systems to microservices with a focus on API access processes. An emphasis is placed on token-based authentication using JWT and OpenID Connect to enhance scalability and performance while ensuring user identity integrity. It also describes the evolution of the T-Mobile app's access mechanism towards a more efficient and secure model through the T-Mobile API Access Process (TAAP).





![Unless otherwise indicated, these slides are © 2013 -2018 Pivotal Software, Inc. and licensed under a Creative Commons
Attribution-NonCommercial license: http://creativecommons.org/licenses/by -nc/3.0/
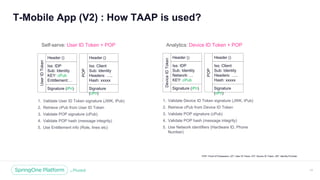
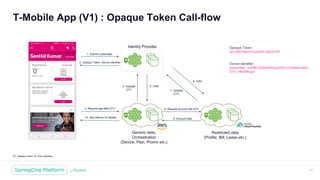
T-Mobile App (V2) : TAAP Tokens
18
{
"iss": "https://xxxxx.t-mobile.com",
"network": {
id: “35679xxx0011980”
phone: “425xxxyyy”},
"device": {
"cnf": "-----BEGIN PUBLIC KEY-----
nMIIBIjANBgkqhkiG9w0BAQE
FAAOCAQ8AMIIBCgKCAQEA5
oaIEnqExSKXK/J7mvgx...........
n-----END PUBLIC KEY-----"
},
"exp": 1aabc435ddee,
"aud": “TMOApp",
"iat": 1xx6yyy776
}
Device ID Token User ID Token Proof Of Possession (POP)
{
"iat": 1xx6yyy776,
"exp": 1aabc435ddee,
"iss": "https://xxxxx.t-mobile.com",
"aud": "TMOApp",
"auth_time": 1536870785,
"sub": "U-xxxxx-yyyyyy-zzzzzzzz",
"amr": [ "password“ ],
"cnf": "-----BEGIN PUBLIC KEY-----
nMIIBIjANBgkqhkiG9w0BAQE
FAAOCAQ8AMIIBCgKCAQEA5
oaIEnqExSKXK/J7mvgx...........
.........n-----END PUBLIC KEY--
---",
"usn": “abcabcabcabcabc",
"ent": {
"acct": [
{
"r": “XX",
"tst": “YY",
"line_count": 5,
"lines": [
{
"phnum": “1234567890",
"r": “Z"
}
]
{
"iat": 1xx6yyy776,
"exp": 1aabc435ddee,
"ehts": "a11ept;x-tmo-device-os;x-
txx-yym;x-b3-paxxyyyzznid;x-
aao-clixxt-name;x-tmo-model;x-
nno-cvcnt-version;x-dat;x-tmo-
xnbvce-os-
version;authorization;x-tmo-
oem-id;x-b3-spanid;x-tmo-post-
sequence-number;x-b3-
traceid;content-length;content-
type",
"edts":
"109e2ee7xxbbvvefe457bbe3c
1065e3c510744511cnbvg411e
956ea836370d605"
}](https://image.slidesharecdn.com/securingmicroservicehybridcloudv1-181008142450/85/Securing-Microservices-in-Hybrid-Cloud-18-320.jpg)