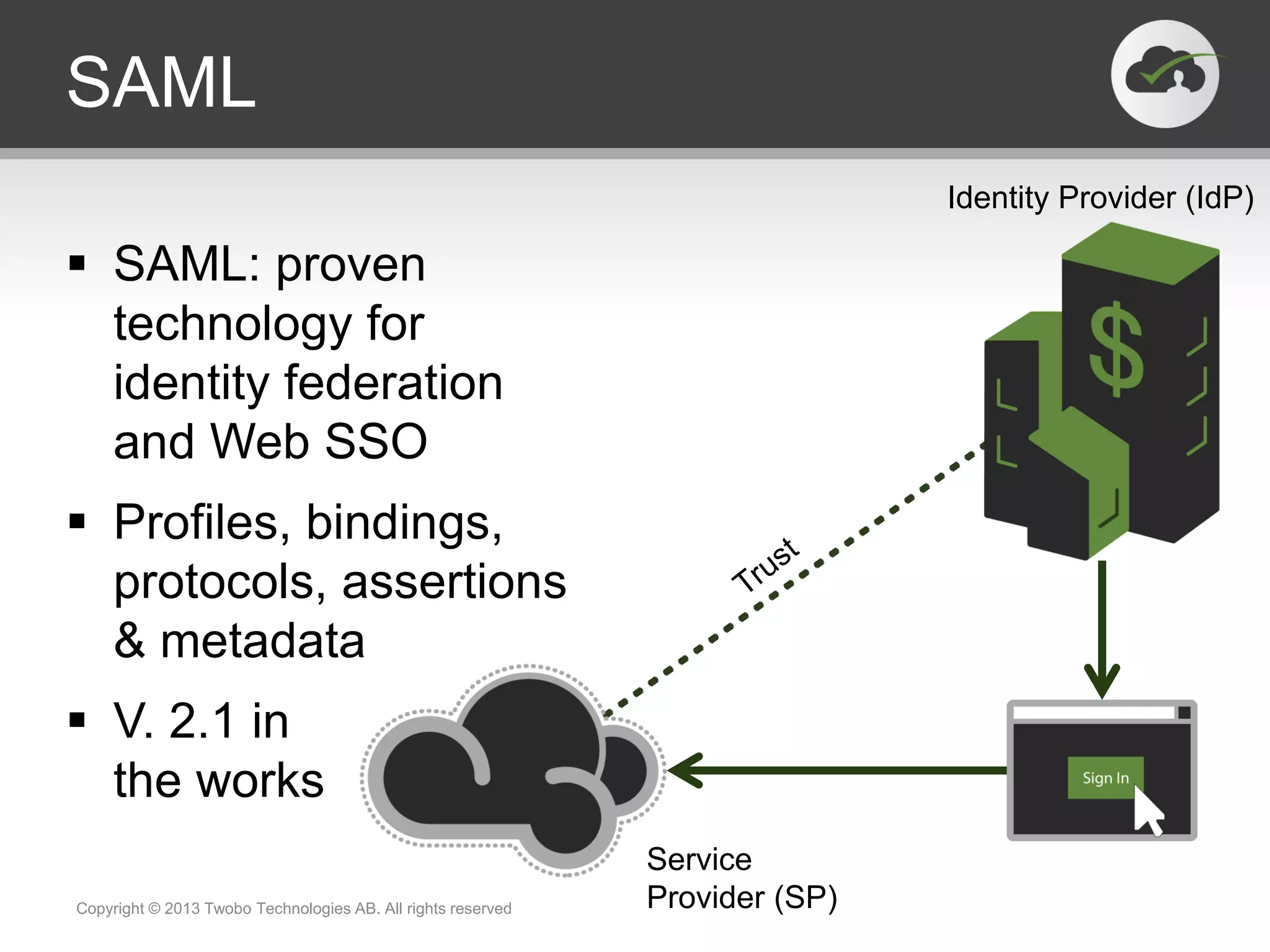
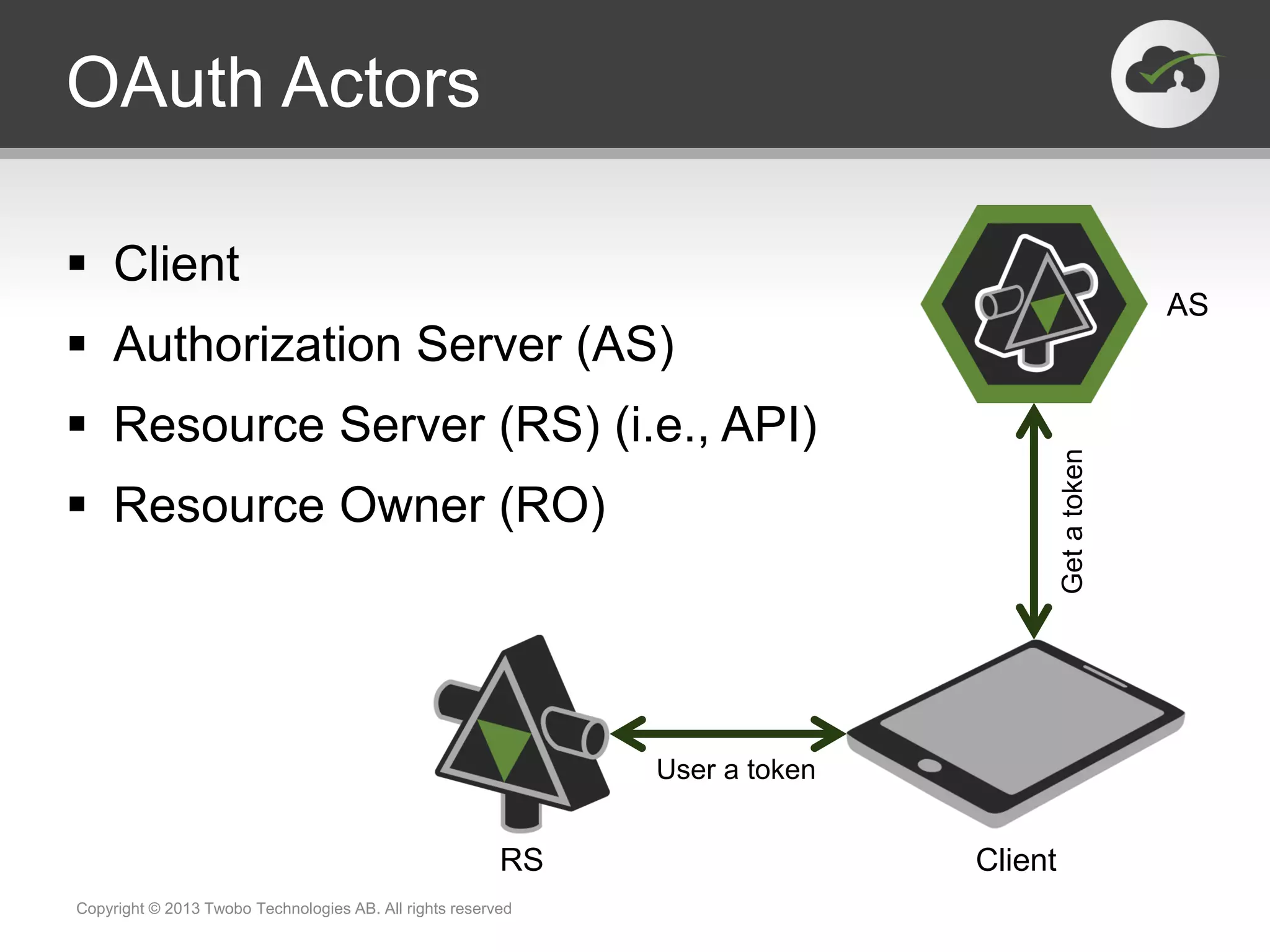
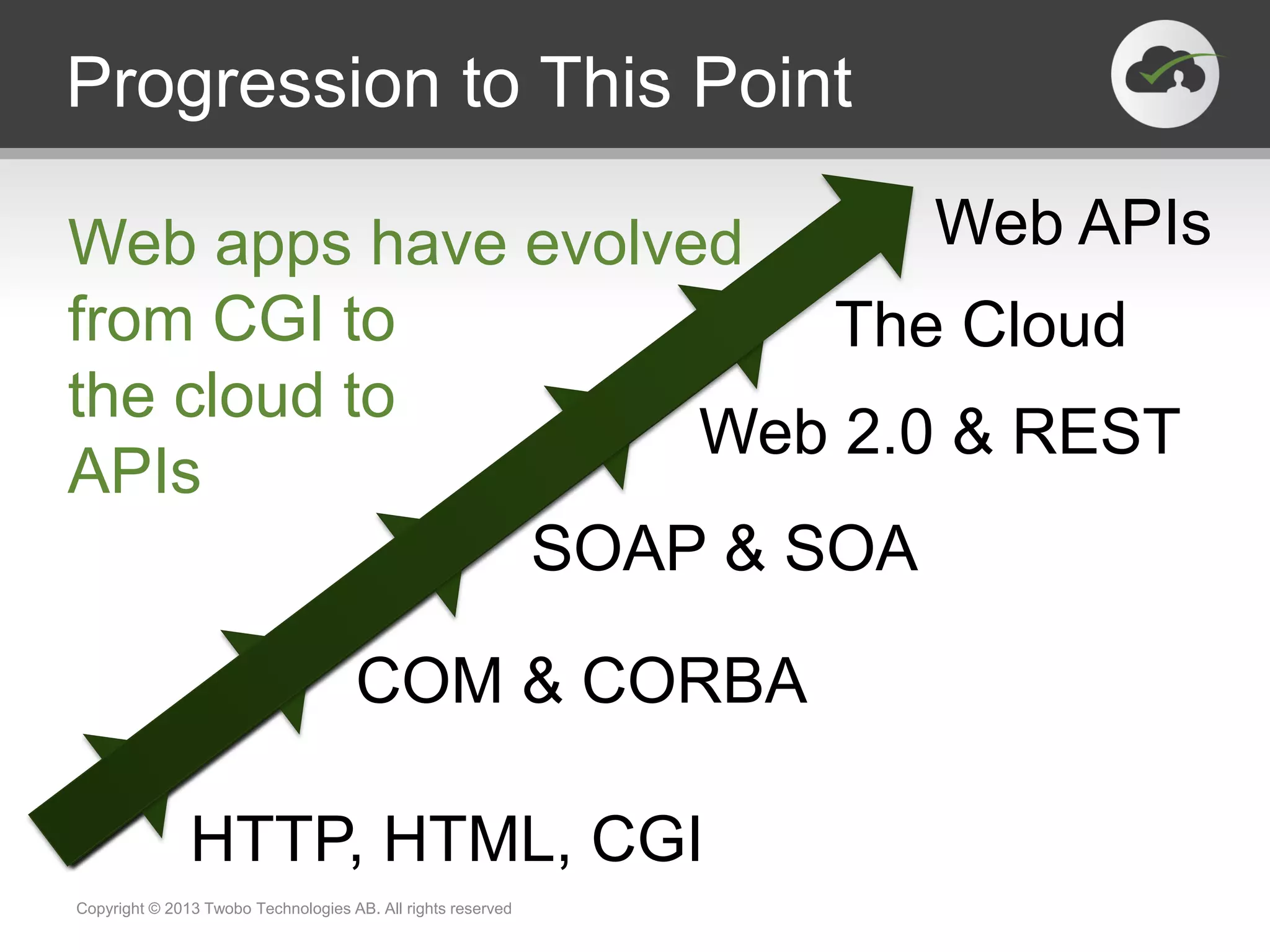
The document outlines the effective launch of secure, RESTful APIs using the 'neo-security stack', discussing disruptive trends like cloud computing and social networks. It provides examples of successful API implementations from companies such as Pearson, Salesforce, and AT&T, highlighting benefits such as new revenue streams and innovation. Critical components like OAuth, SAML, and OpenID Connect are explored for managing identity and authorization within API ecosystems.


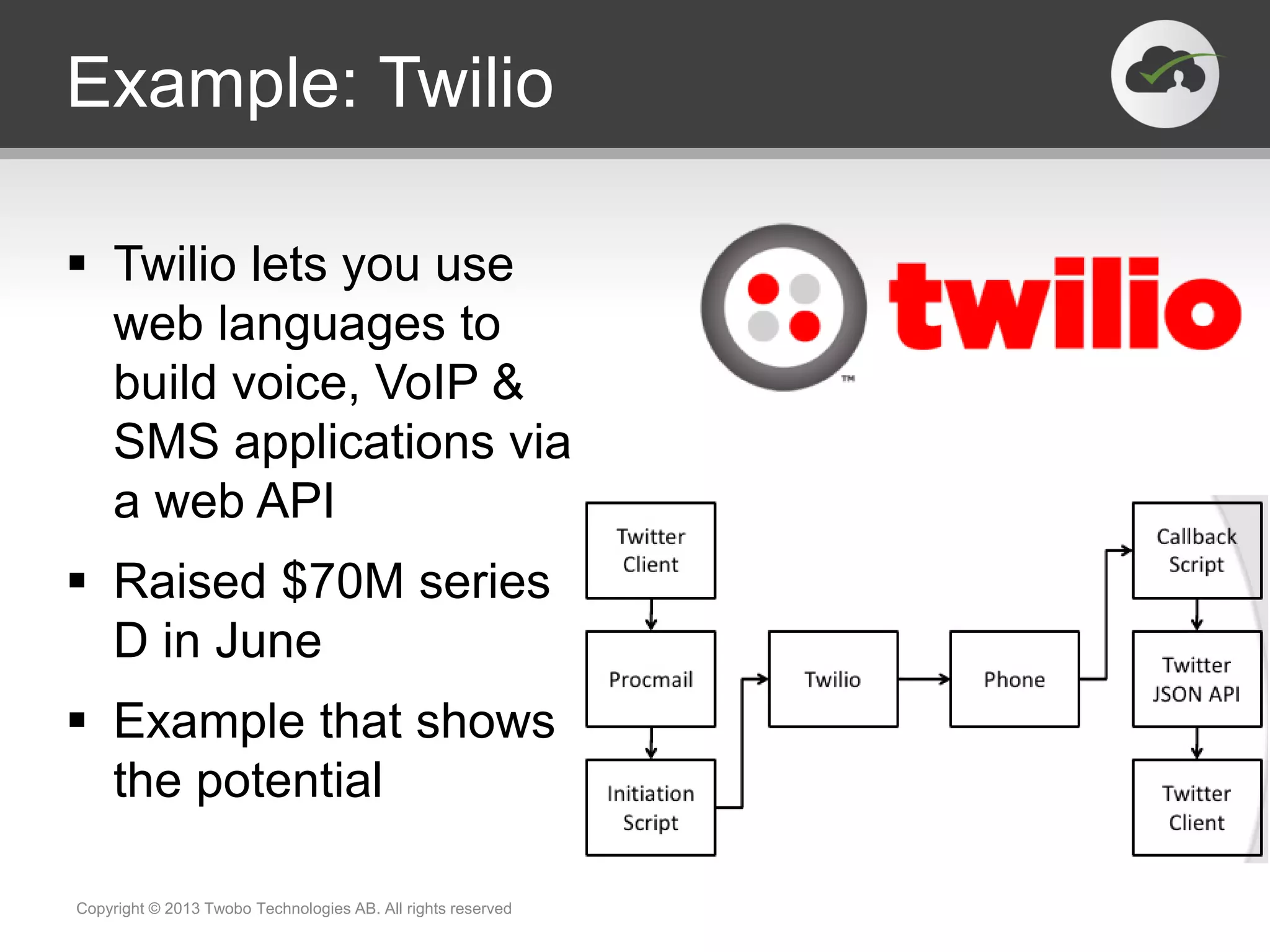
![Example: AT&T
The network is the platform
Examples of their APIs
SMS, MMS, location, speech
TV, healthcare, notary, advertising
Sponsor hackathons, events, blogs
Business benefits
Revenue ▪ Business agility
Time to market ▪ New customer value
Innovation ▪ Efficiency
Copyright © 2013 Twobo Technologies AB. All rights reserved
“[The API program]
is an architectural
choice one makes
for speed.”
— John Donovan,
SEVP, AT&T](https://image.slidesharecdn.com/4-nordic-apis-launchingsuccessfulsecure-apis-130615060508-phpapp02/75/Launching-a-Successful-and-Secure-API-7-2048.jpg)