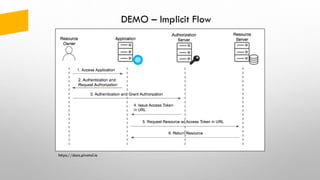
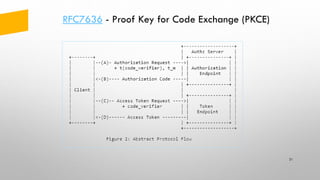
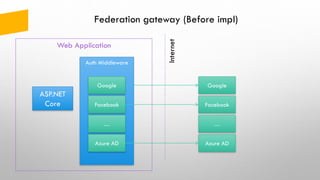
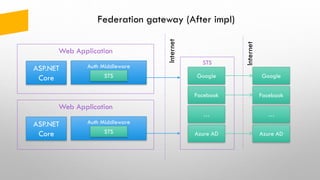
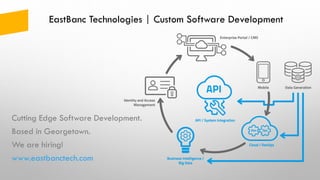
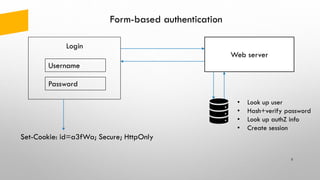
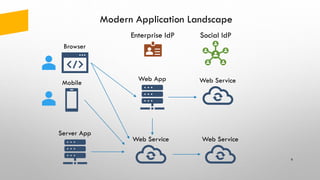
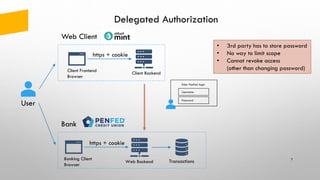
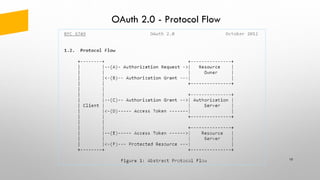
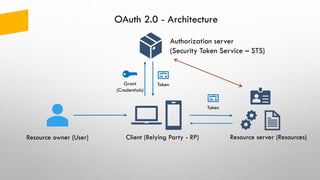
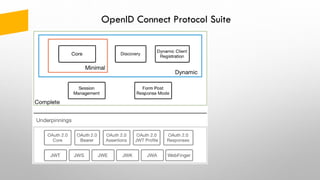
The document provides an overview of token-based security for web applications using OAuth 2.0 and OpenID Connect, presented by Vladimir Bychkov. It explains the architecture, protocols, and flows involved in delegated authorization and includes details on various grant types and security concerns for web applications. A demo section illustrates the practical applications of these concepts, showcasing different authorization flows and endpoints.







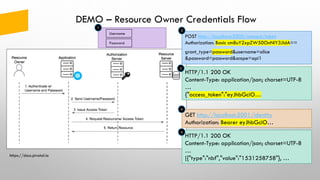
![DEMO – Authorization Code Flow
https://docs.pivotal.io
GET /Home/Secure
1
HTTP/1.1 302 Found
Location: http://localhost:5000/connect/authorize?
client_id=mvc
&redirect_uri=http//localhost:5002/signin-oidc
&response_type=code id_token
&scope=openid profile api1 offline_access
&response_mode=form_post …
2
GET /connect/authorize?client_id=mvc&…
3
302 /account/login… 302 /account/consent…
HTTP/1.1 200 OK
…
<form method='post' action='http://localhost:5002/signin-oidc’>
<input type='hidden' name='code’ value=‘deba7f4c87….’ /> …
<script>(function(){document.forms[0].submit();})();</script>
4
POST http://localhost:5000/connect/token
client_id=mvc&client_secret=secret
&code=deba7f4c87…&grant_type=authorization_code
5
HTTP/1.1 200 OK
Content-Type: application/json; charset=UTF-8
…
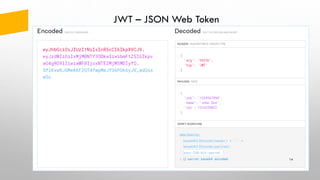
{“id_token”=…, "access_token":"eyJhbGciO…”
6
GET http://localhost:5001/identity
Authorization: Bearer eyJhbGciO…
7
HTTP/1.1 200 OK
Content-Type: application/json; charset=UTF-8
…
[{"type":"nbf","value":"1531258758"}, …
8](https://image.slidesharecdn.com/2019-techtalkdc-token-basedsecurityforwebapplicationsusingoauth2andopenidconnect-191031194242/85/2019-Tech-Talk-DC-Token-based-security-for-web-applications-using-OAuth2-and-OpenID-Connect-18-320.jpg)