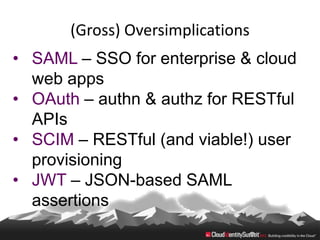
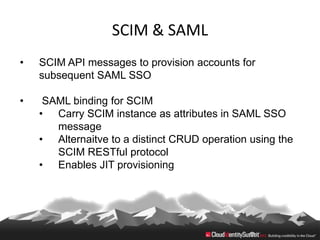
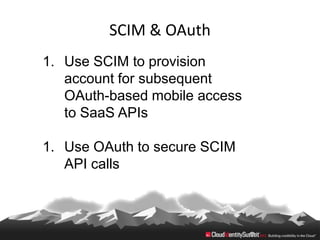
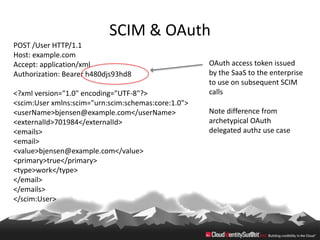
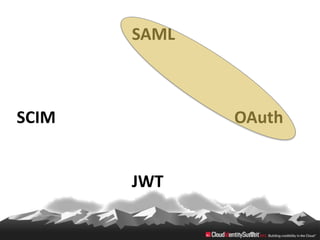
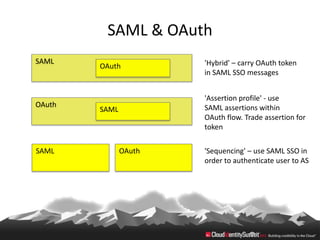
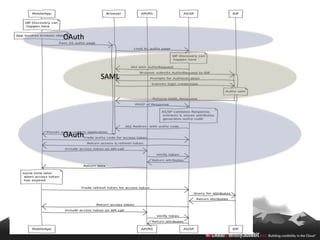
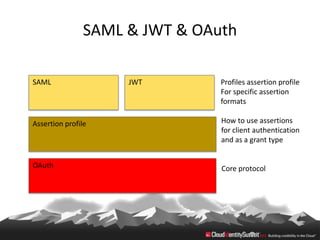
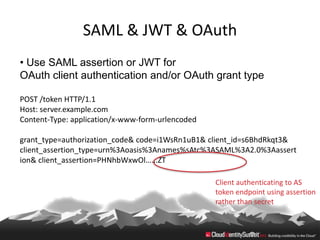
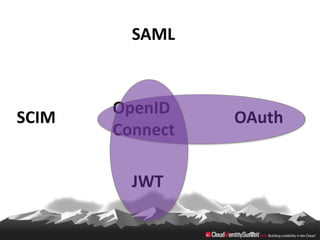
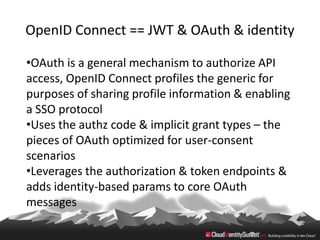
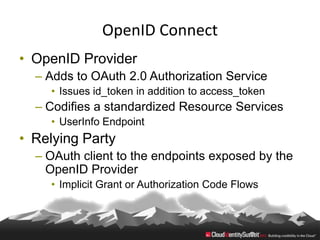
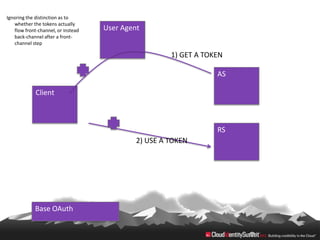
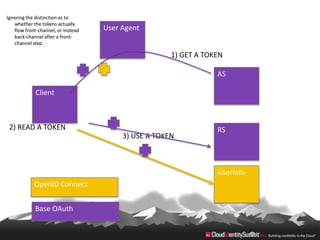
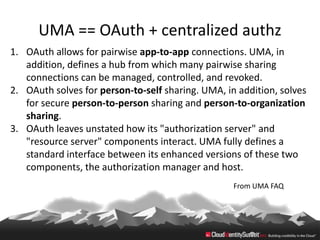
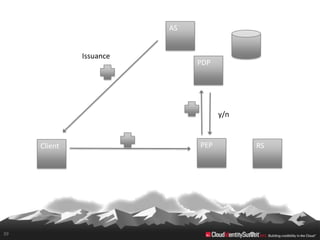
This document provides an overview of common standards used for cloud identity management, including SAML, OAuth, SCIM, and JWT. It describes how each standard addresses aspects of authentication, authorization, and user provisioning. The document also discusses some ways these standards can be combined, such as using SCIM for user provisioning and SAML assertions for single sign-on authentication, or carrying SCIM user profiles within SAML messages. It acknowledges challenges around mapping complex SCIM schemas to SAML's attribute model and notes that further work is needed to fully define interoperability between the standards.