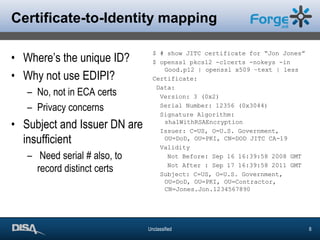
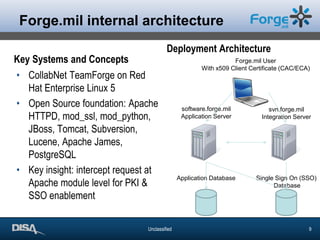
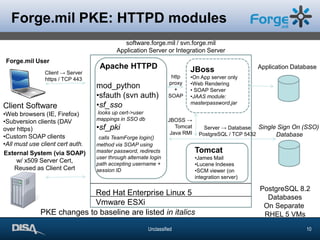
The document discusses the challenges and solutions of enabling web applications for Department of Defense (DoD) security through Public Key Infrastructure (PKI) and Common Access Card (CAC) systems. It highlights the importance of PKI for secure authentication and the complexities involved in integrating legacy systems with certificates. The presentation emphasizes the use of open source tools in achieving these objectives and shares valuable lessons learned during the process.