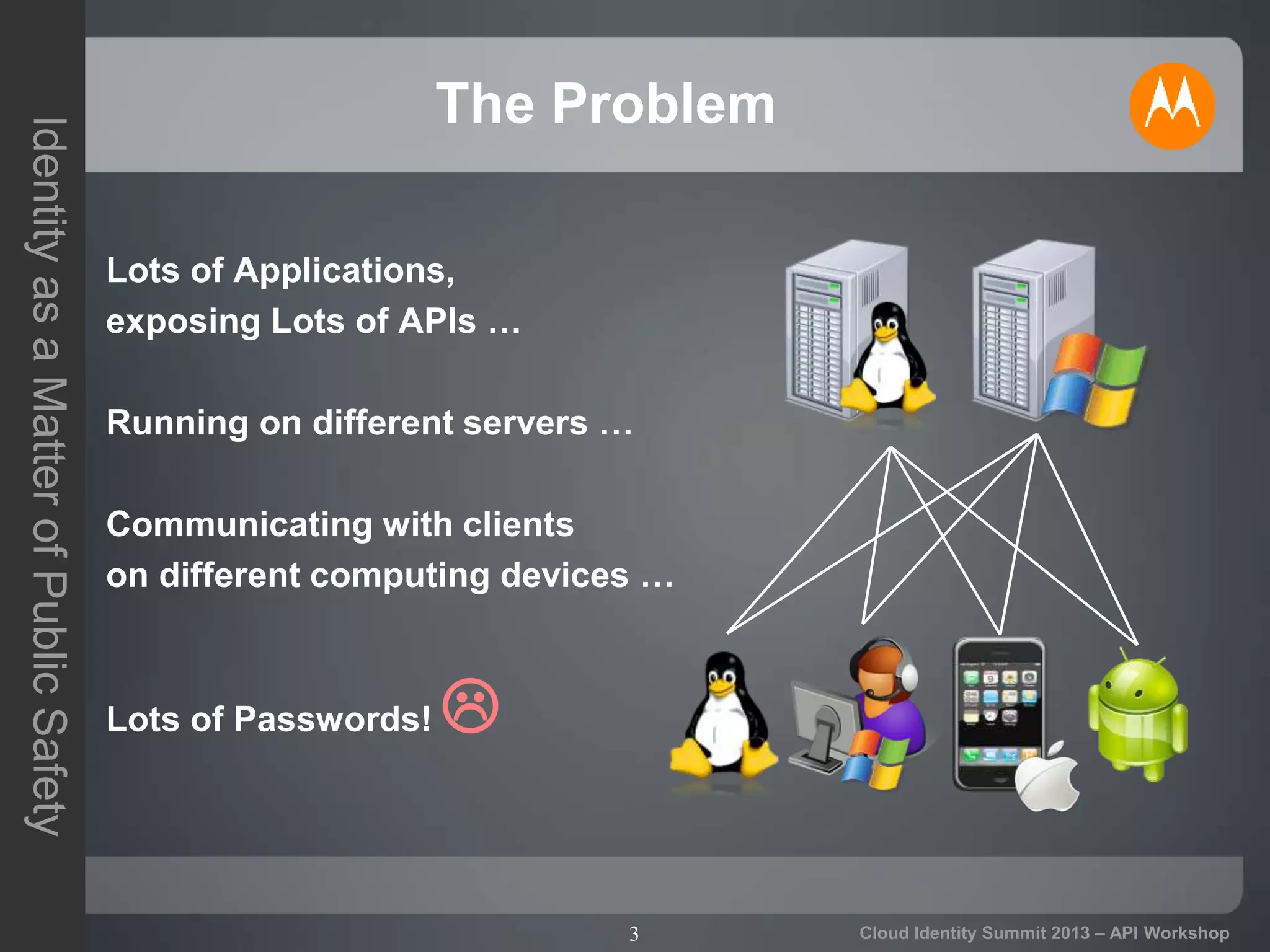
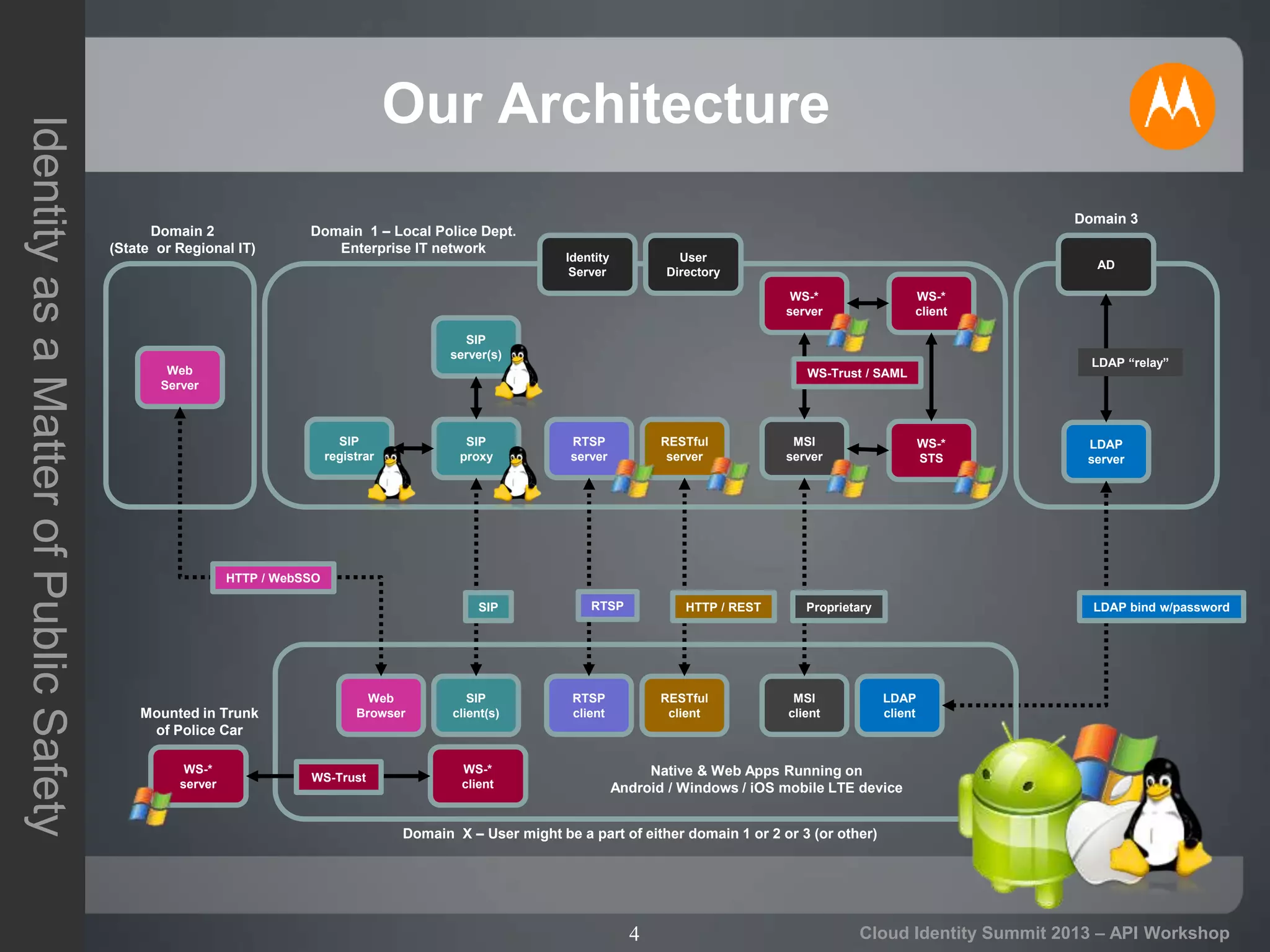
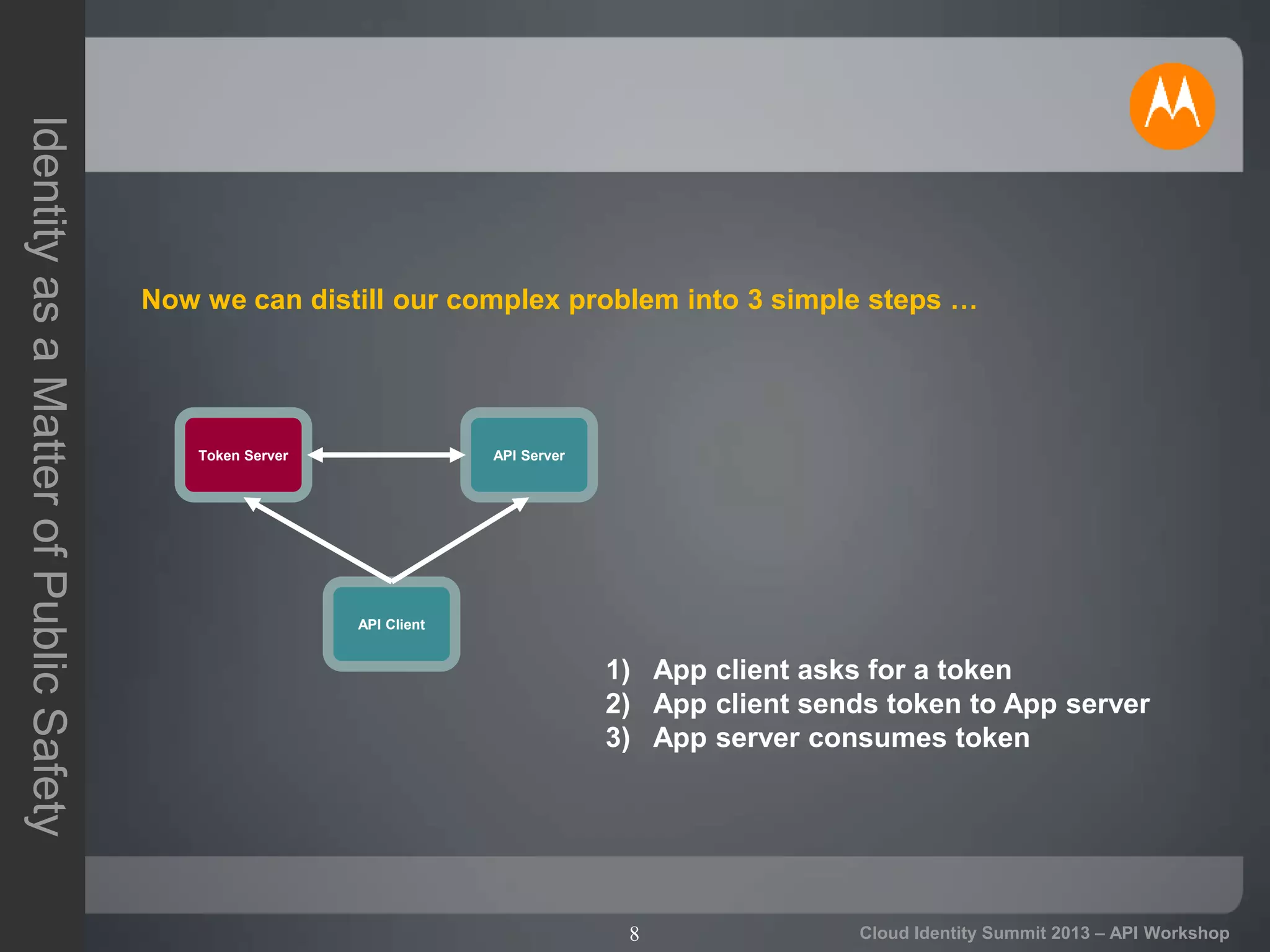
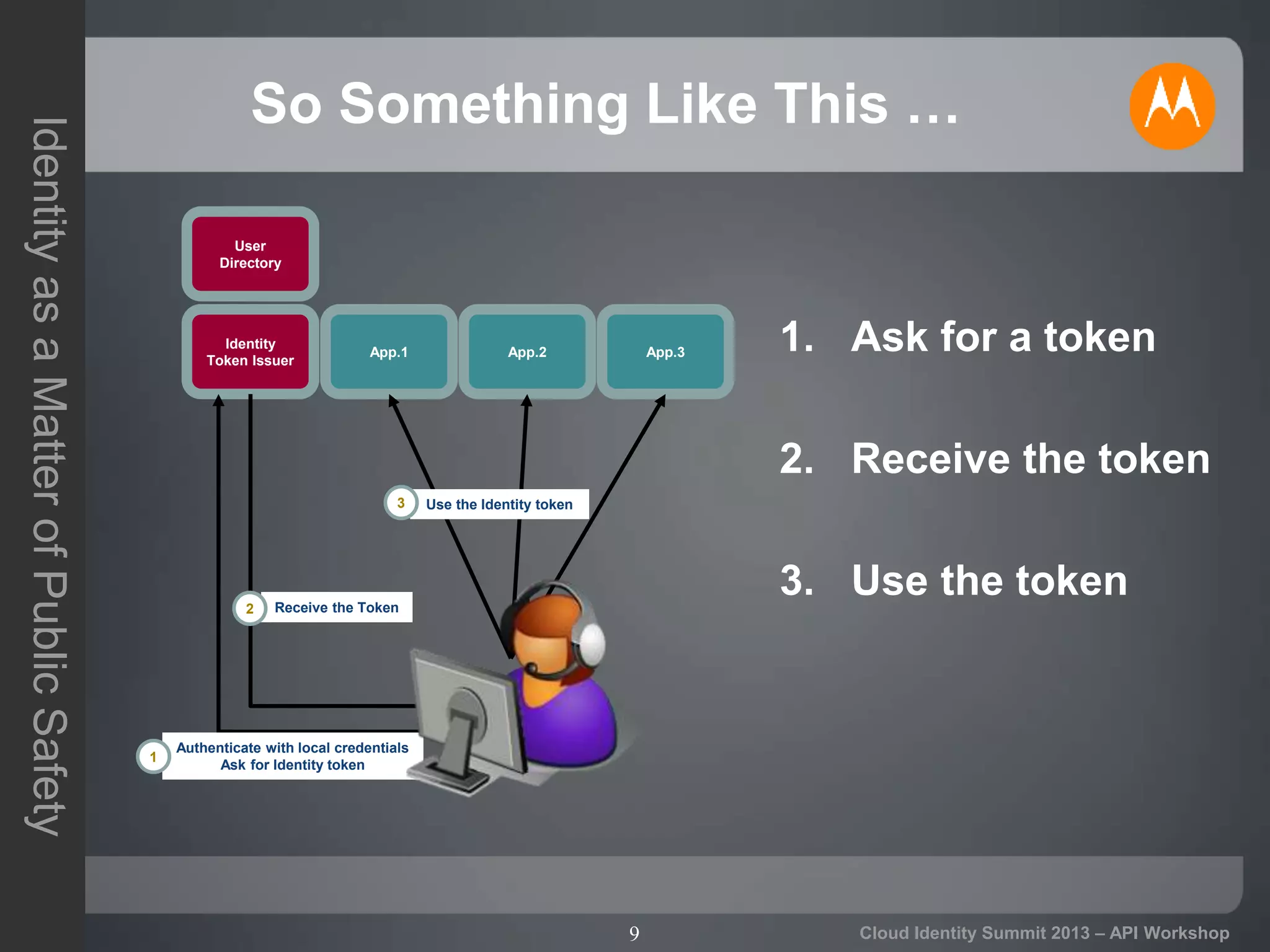
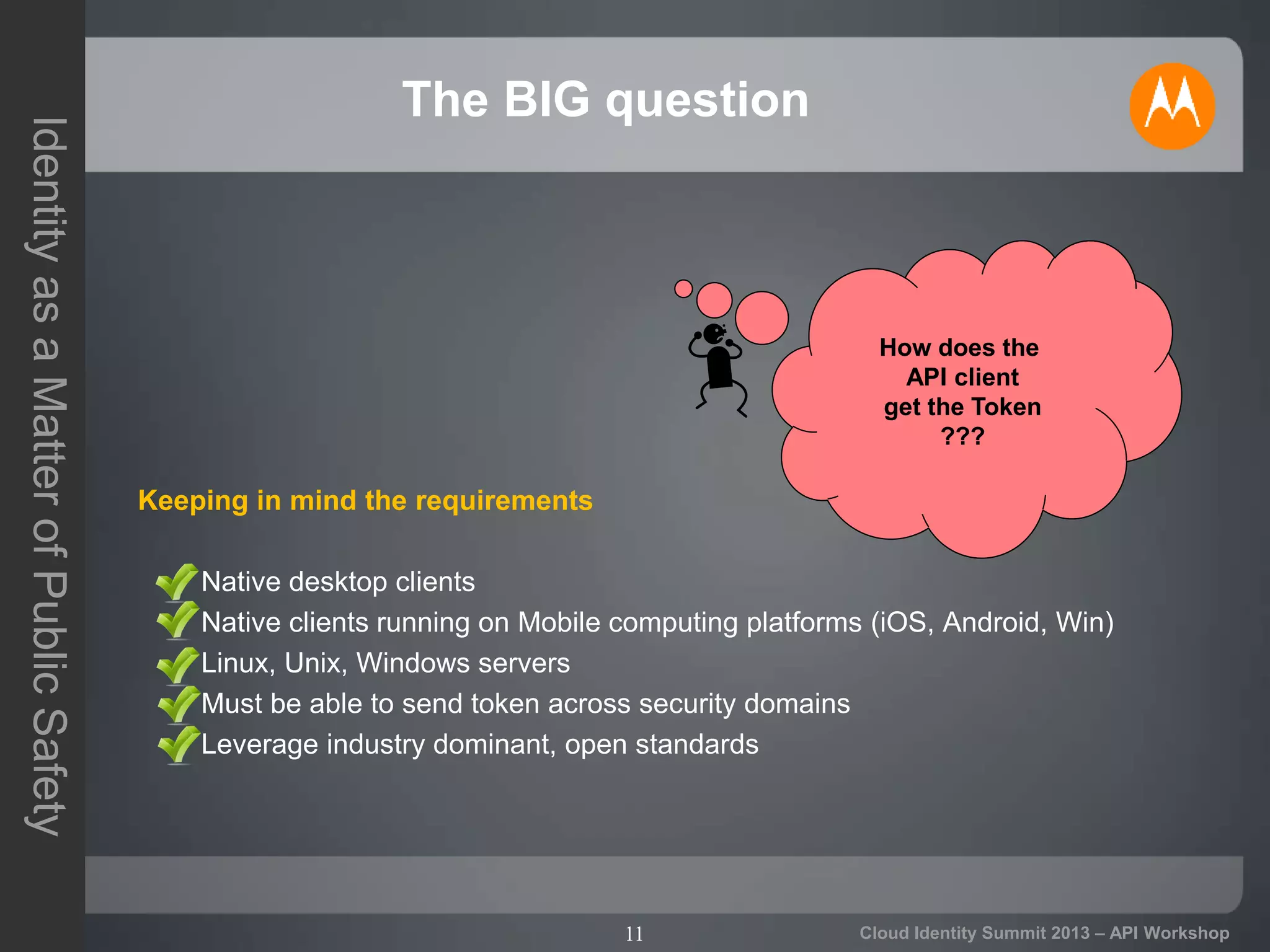
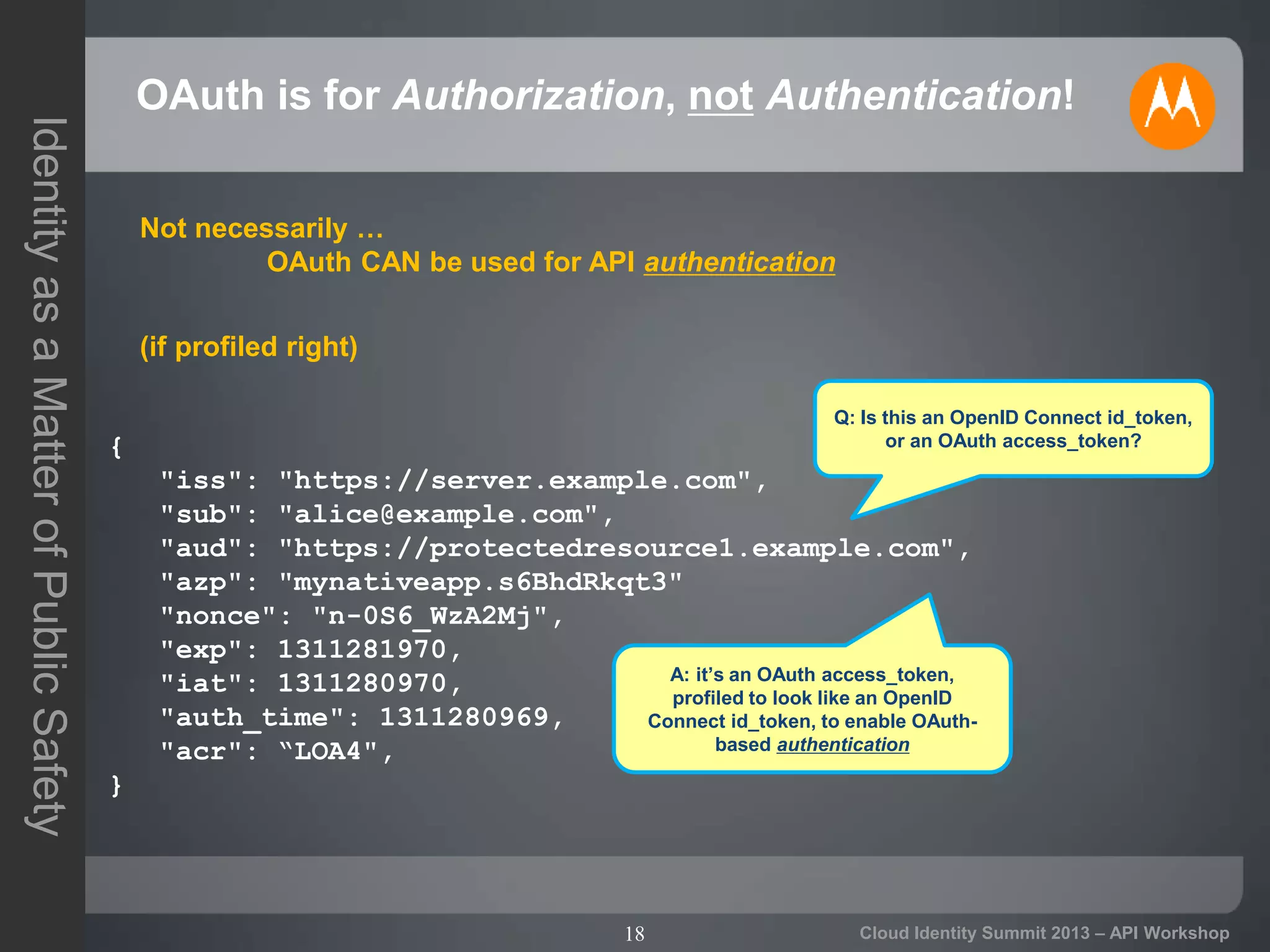
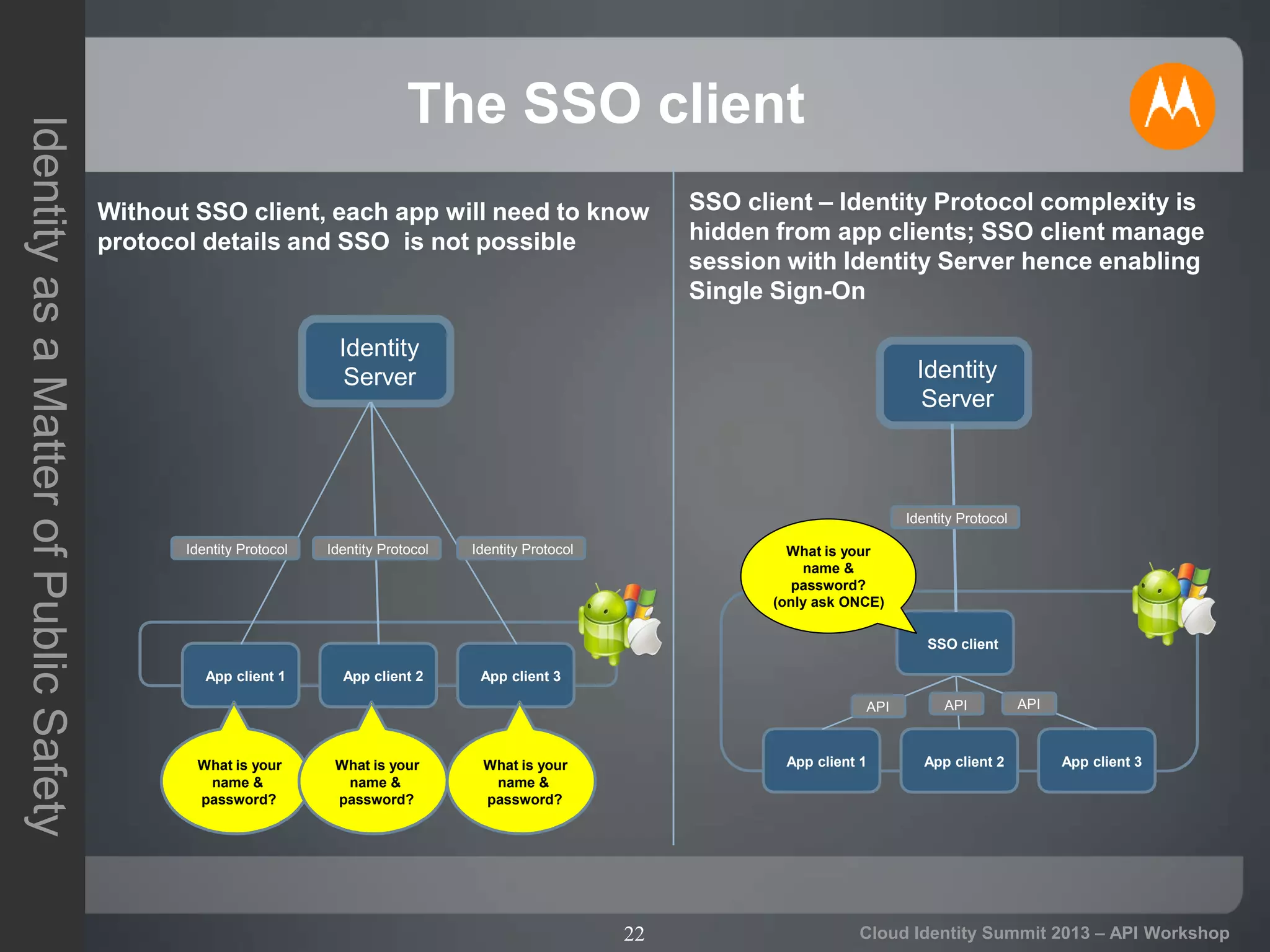
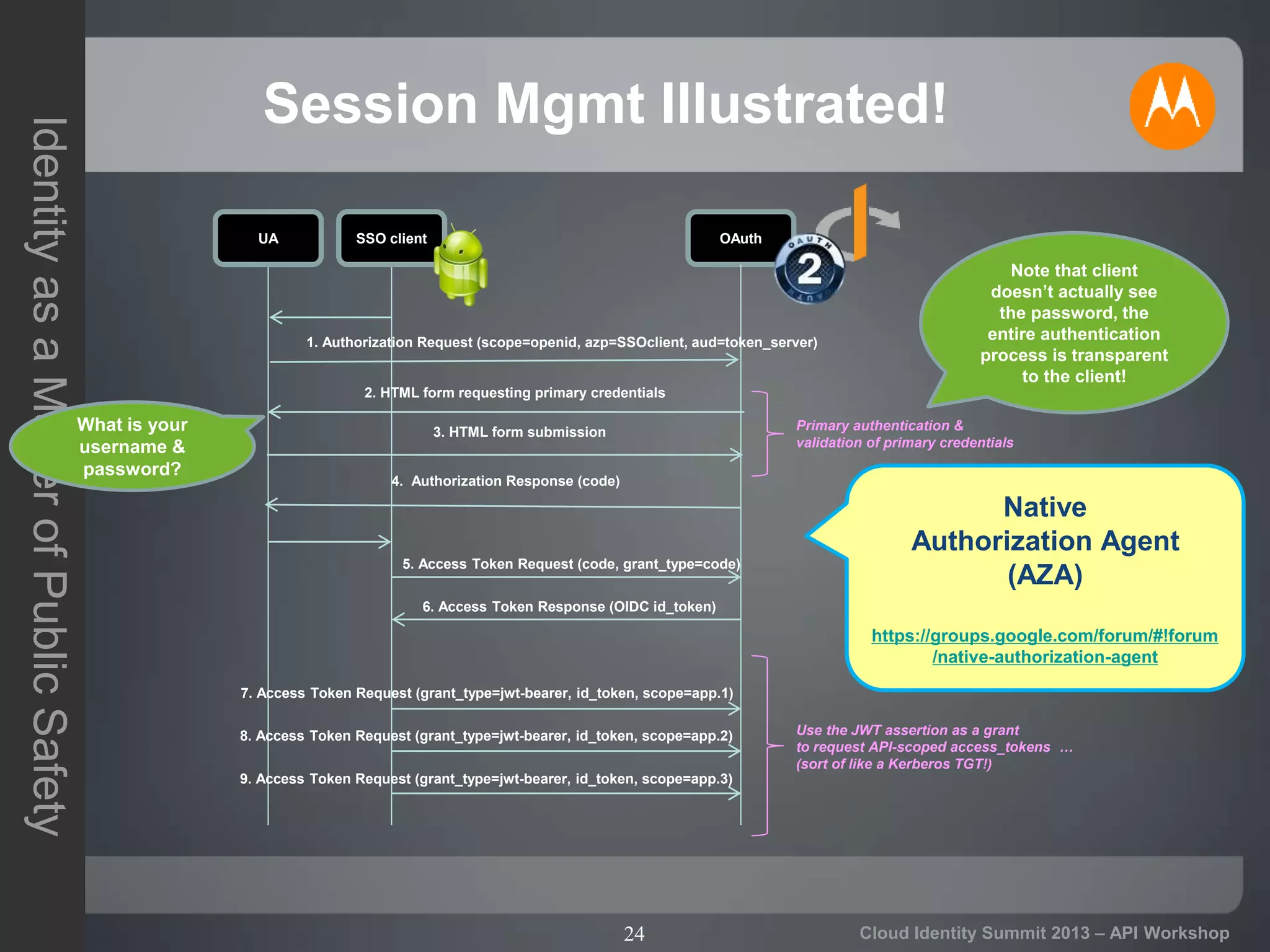
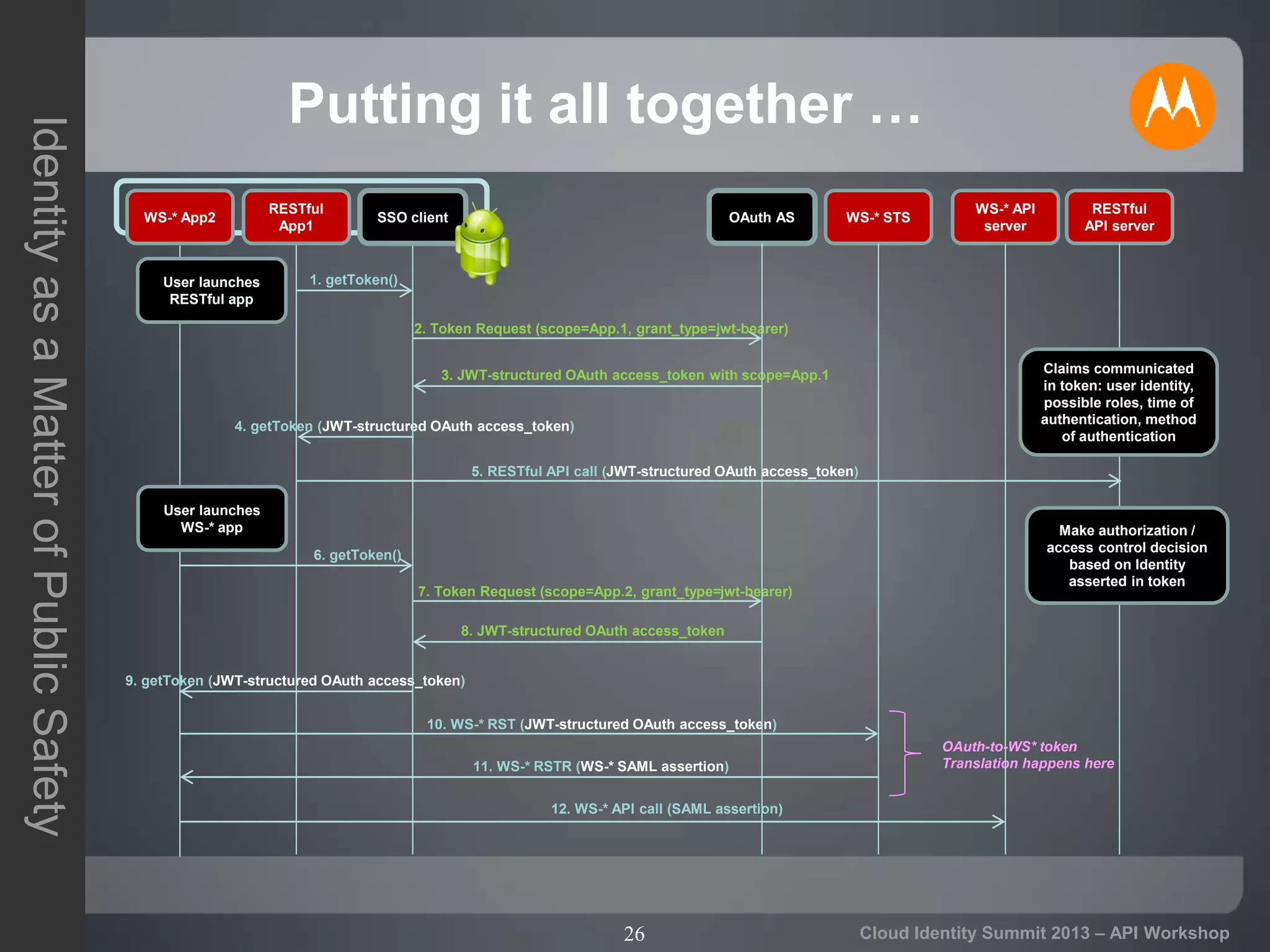
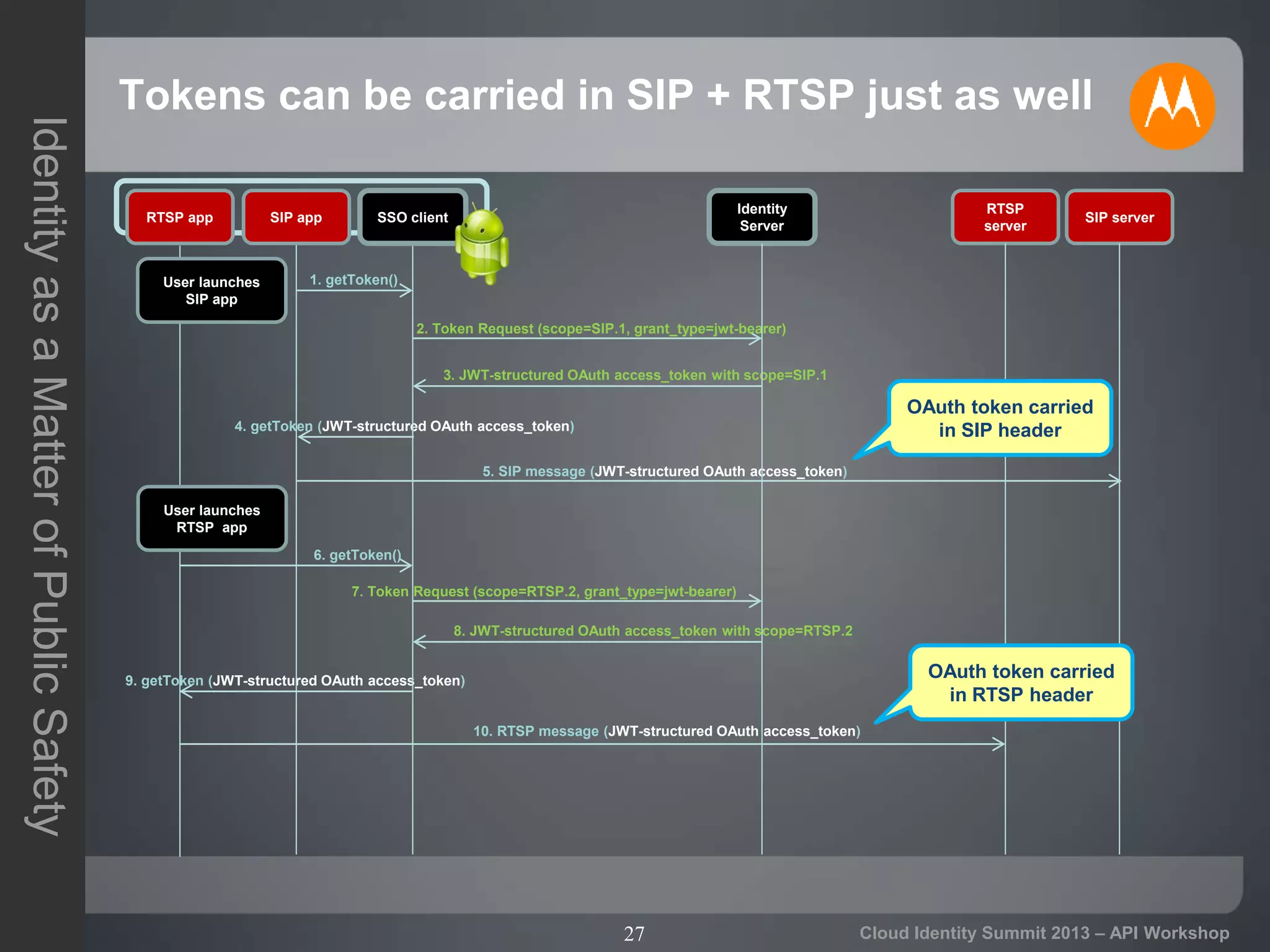
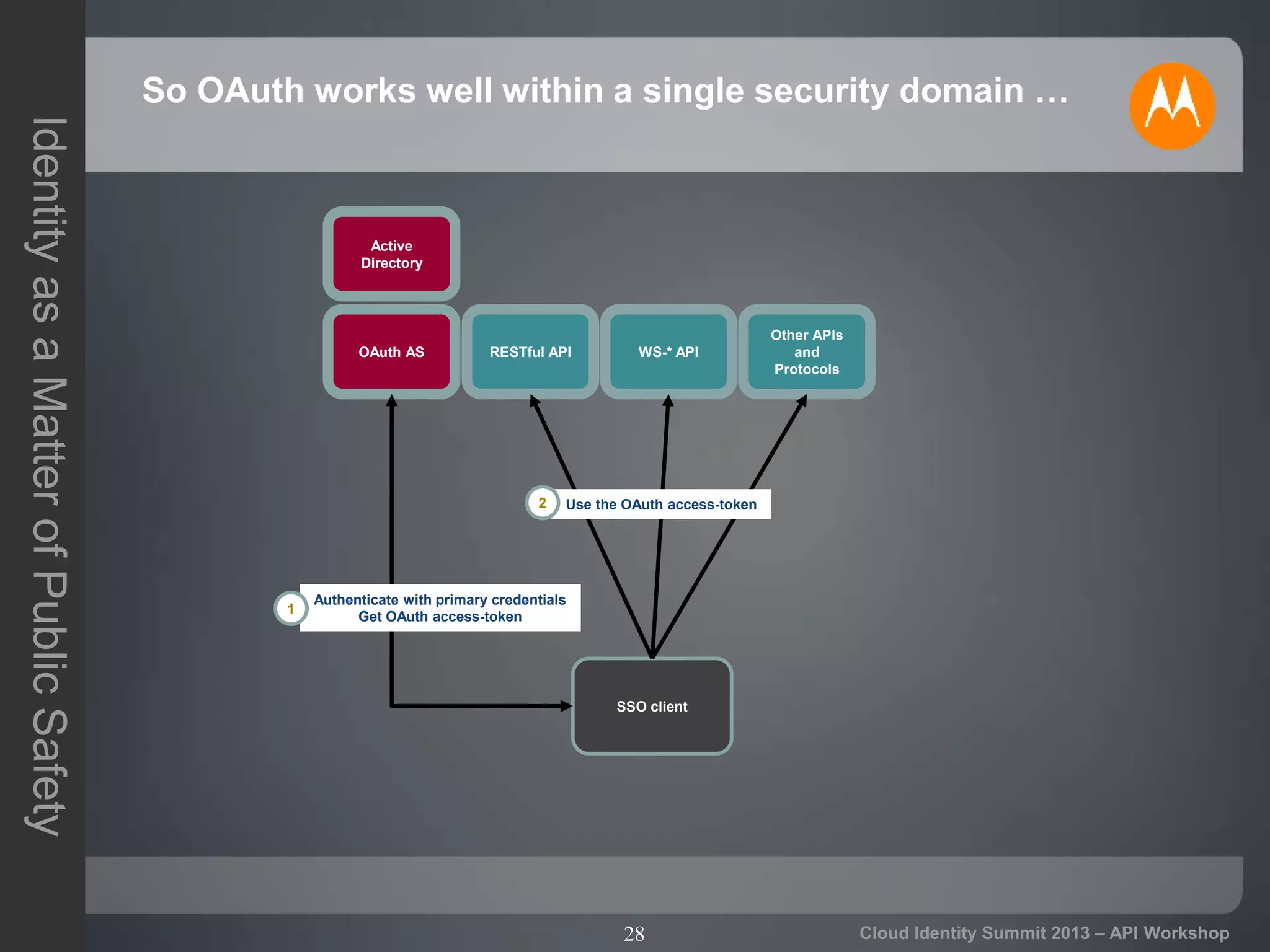
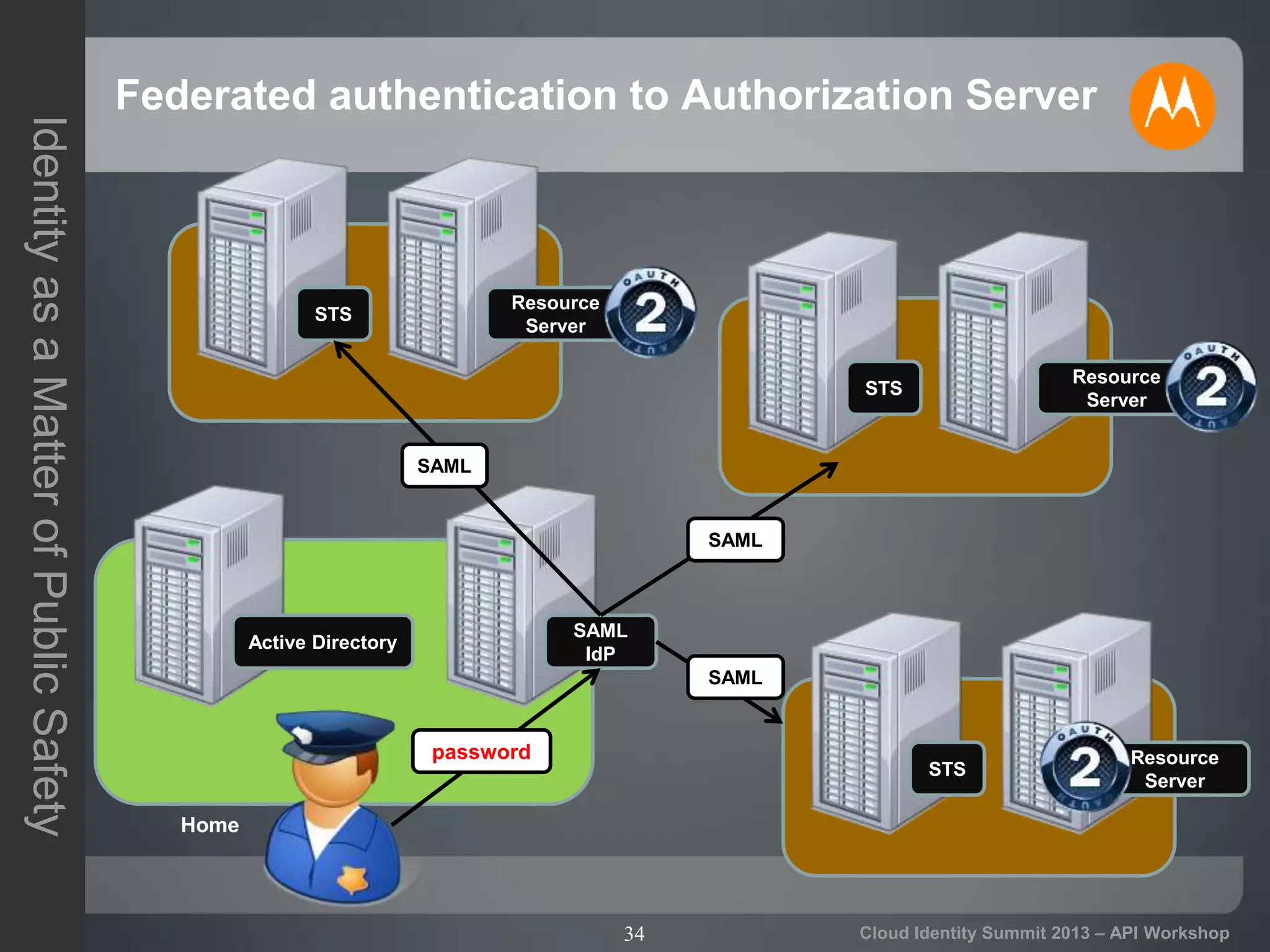
The document discusses secure API access and single sign-on (SSO) across security domains using token-based authentication, with a focus on OAuth as a preferred method over alternatives like Kerberos and SAML. It details the process of tokenization for APIs, highlights the benefits of tokenizing for security and usability, and addresses challenges in cross-domain access. The conclusion emphasizes the need for clearer standards and practices in enterprise authentication using OAuth and structured access tokens.