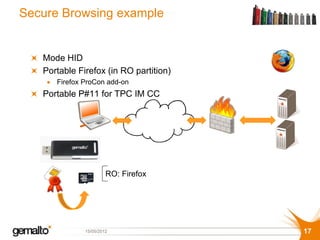
This document discusses securing cloud computing and identity management. It summarizes that there are three models of cloud computing: Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS). It also discusses that identity management is key to success in the cloud and addresses challenges around balancing security and convenience. The document introduces Protiva Confirm as a solution that can bring adaptable trust to cloud services by providing strong authentication, single sign-on, and other advanced security services while also providing convenience.