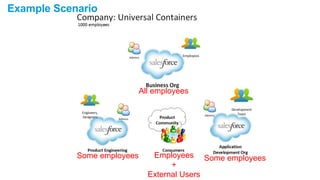
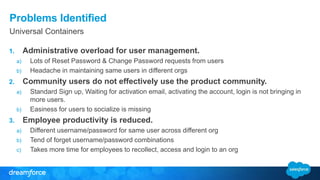
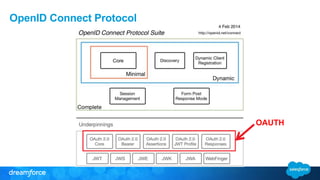
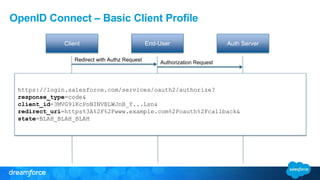
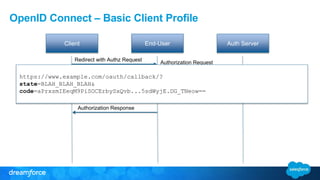
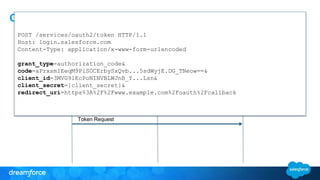
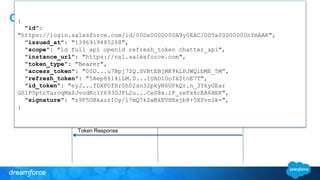
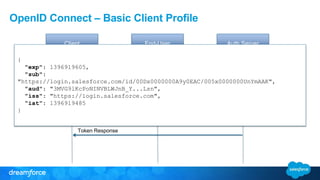
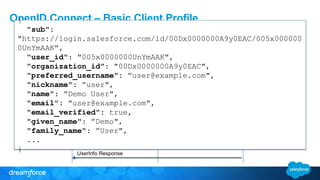
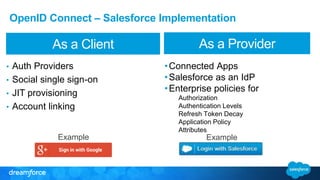
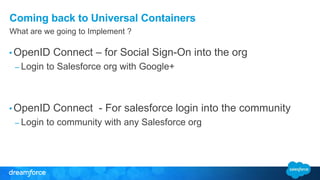
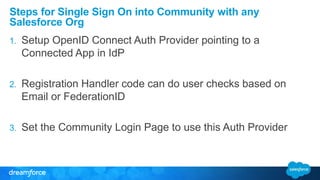
The document discusses OpenID Connect and its application in single sign-on (SSO) for Salesforce environments. It highlights problems faced by Universal Containers around user management and employee productivity, proposing solutions like implementing OpenID Connect for SSO. The presentation also outlines practical implementation steps and key takeaways on how Salesforce can function as both an OpenID Connect client and provider.