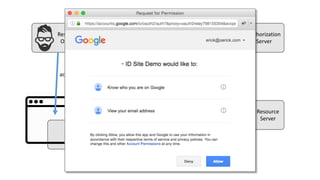
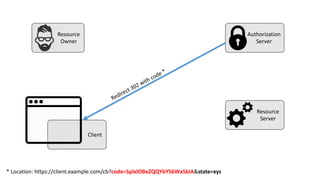
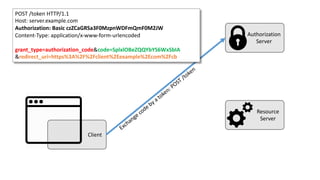
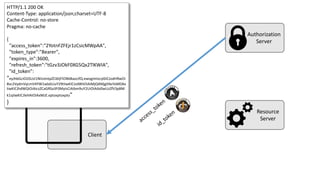
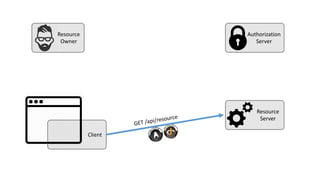
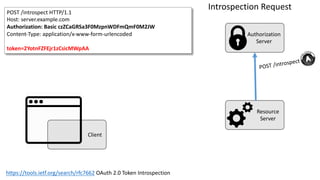
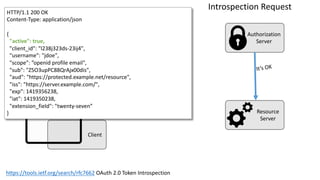
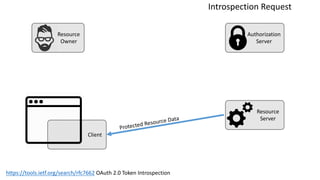
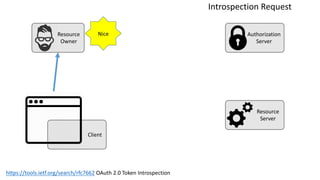
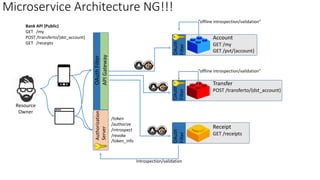
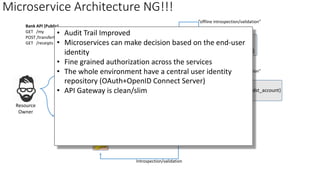
The document discusses microservices architecture with a focus on security, specifically the implementation of OAuth 2.0 and OpenID Connect for user authentication and authorization. It outlines the roles of tokens, JWTs, and the responsibilities of API gateways within a microservices framework, emphasizing the need for improved logging and user identification. Additionally, it provides examples of access and ID tokens, and resources for further understanding of OAuth 2.0 and OpenID Connect.



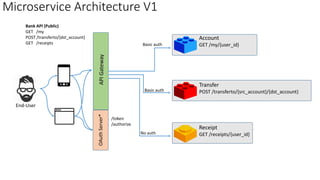


![JWT
– JSON
Web
Token
eyJ0eXAiOiJKV1QiL
CJhbGciOiJIUzI1NiJ
9.eyJpc3MiOiJodH
RwczovL215LnNlcn
ZpY2UuY29tIiwiaW
F0IjoxNDM1MTc5N
jAzLCJleHAiOjE0Mz
UxODE0MjEsImF1Z
CI6Ind3dy5zZXJ2a
WNlLmNvbSIsInN1
YiI6ImpvaG5kb2VA
Z21haWwuY29tIiwi
Um9sZSI6WyJhcHB
yb3ZlciIsInZpZXdlci
JdfQ.91GLvtMhhnI
Cmqlf_RVONGw5I
M9i8eeAPx2s_Wp
MObU
{
"typ":
"JWT",
"alg":
"HS256"
}
{
"iss":
"https://my.service.com",
"iat":
1435179603,
"exp":
1435181421,
"aud":
"www.service.com",
"sub":
"johndoe@gmail.com",
"Role":
[
"approver",
"viewer"
]
}
HMACSHA256(
base64UrlEncode(header)
+
"."
+
base64UrlEncode(payload),sharedsecret)
JWT
Header
JWT
Payload
JWT
Signature](https://image.slidesharecdn.com/imasters-intercon2016newversion-161024125609/85/iMasters-Intercon-2016-Identity-within-Microservices-7-320.jpg)


![How
an
access_token looks
like?
(by
value
-‐ JWT)
// JWT Payload
{
"sub": "alice", // user id
"cid": "000123", // client id
"iss": "https://as.domain.com", // who issued
"aud": "https://rs.domain.com",
"exp": 1460345736, // expiration date
"scp": ["openid","email","profile"] // scopes
}](https://image.slidesharecdn.com/imasters-intercon2016newversion-161024125609/85/iMasters-Intercon-2016-Identity-within-Microservices-12-320.jpg)

![How
an
id_token looks
like?
(by
value
-‐ JWT)
{
"iss": ”InstIdentRicardoGumbletonDaunt", // who issued
"sub": ”4.444.444", // user identification
"aud": ["cops","bank"], // where it’s used
"nonce": "n-0S6_WzA2Mj",
"exp": 1311281970, // 10 years
"iat": 1311280970,
"auth_time": 1311280969,
"amr": "sign+fingerprint” //auth-methods-ref
}](https://image.slidesharecdn.com/imasters-intercon2016newversion-161024125609/85/iMasters-Intercon-2016-Identity-within-Microservices-14-320.jpg)