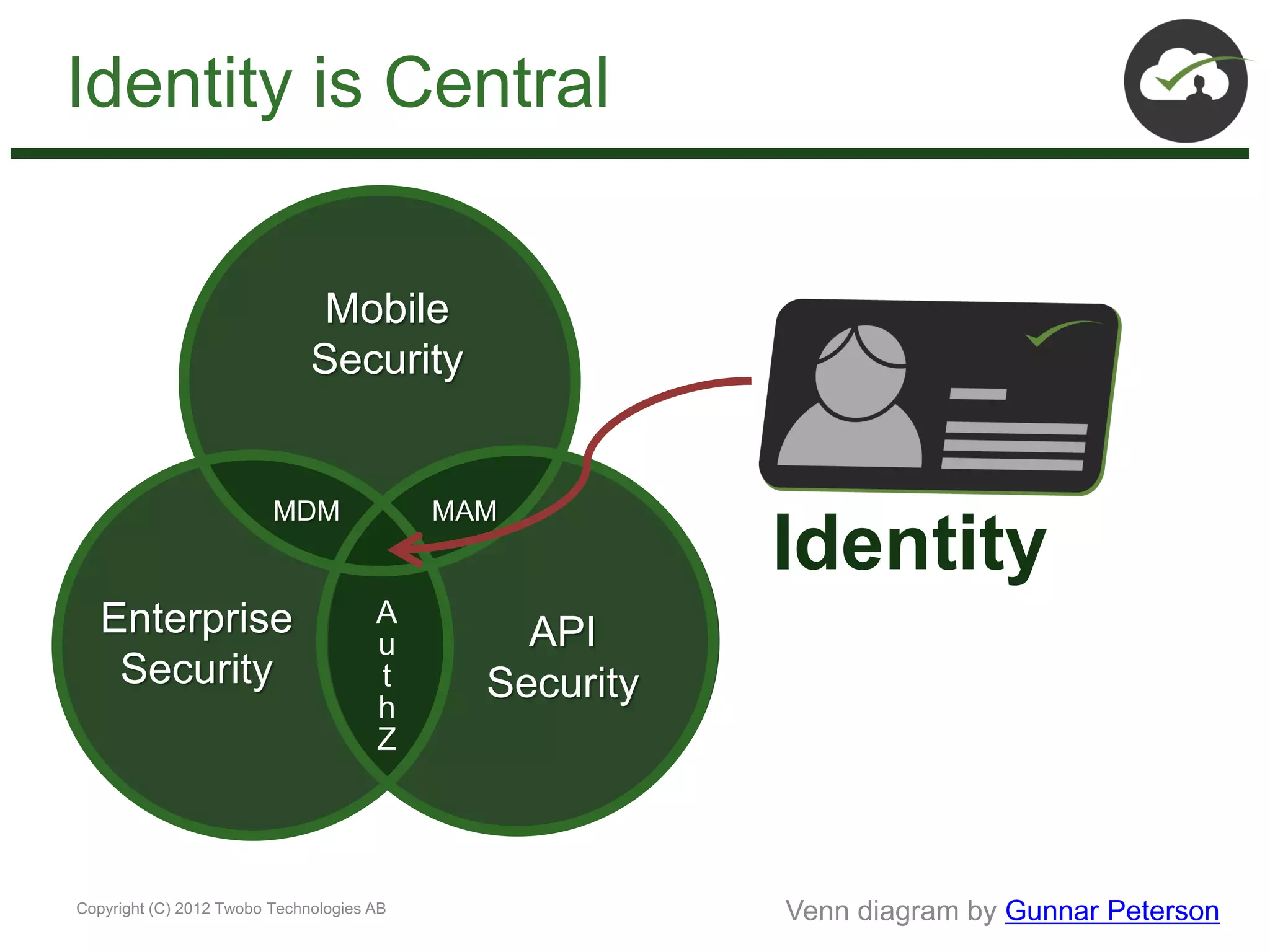
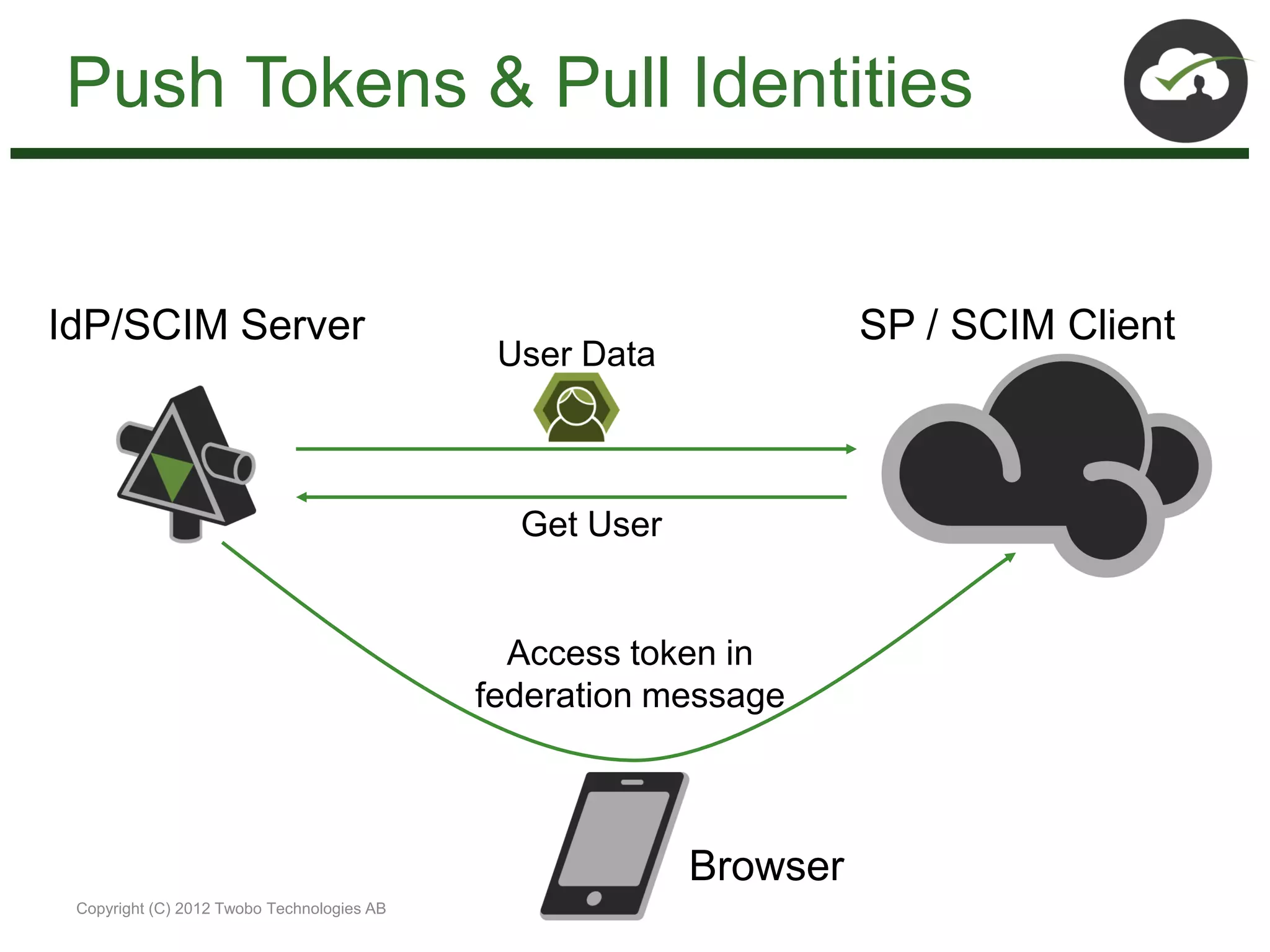
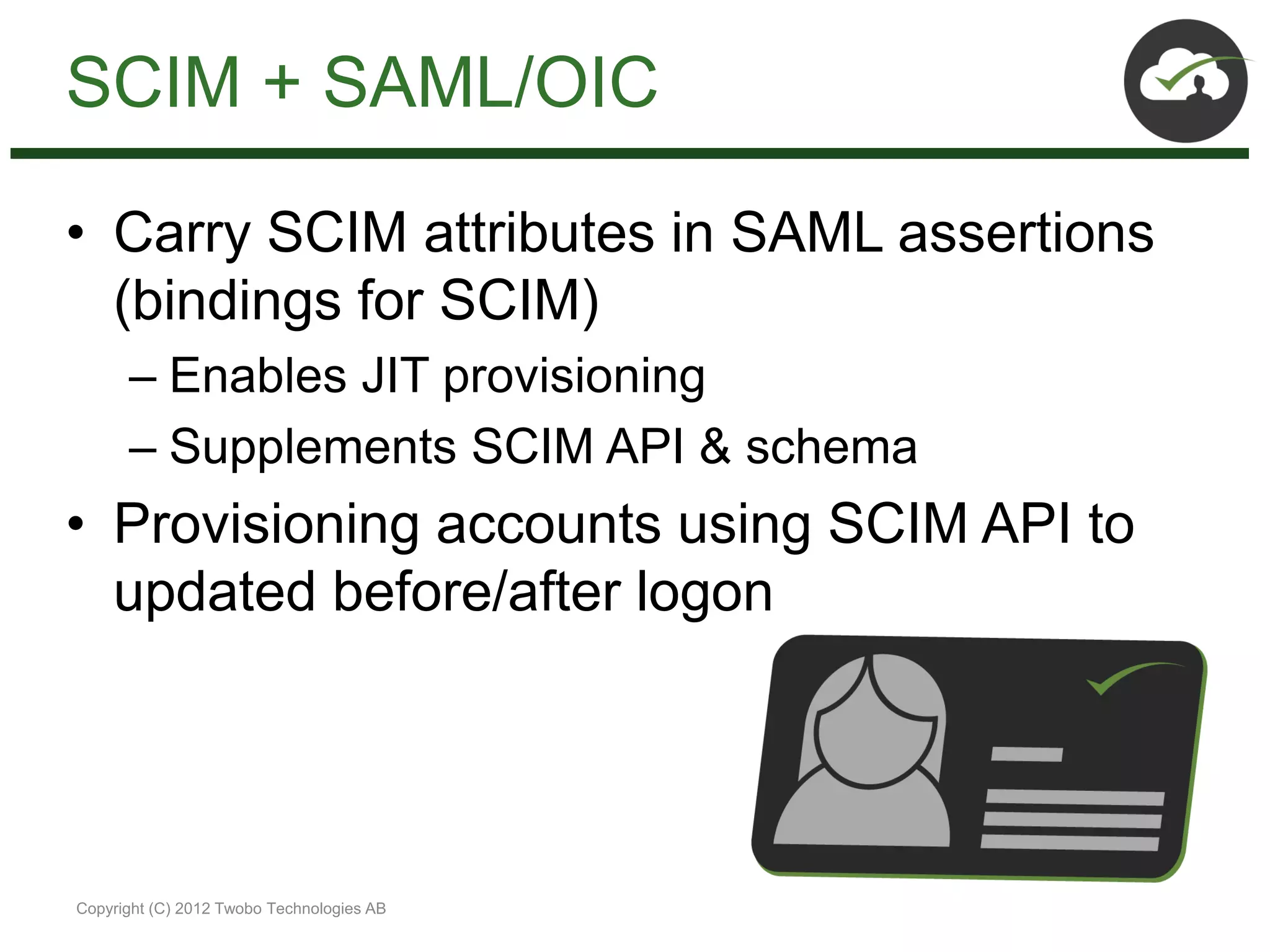
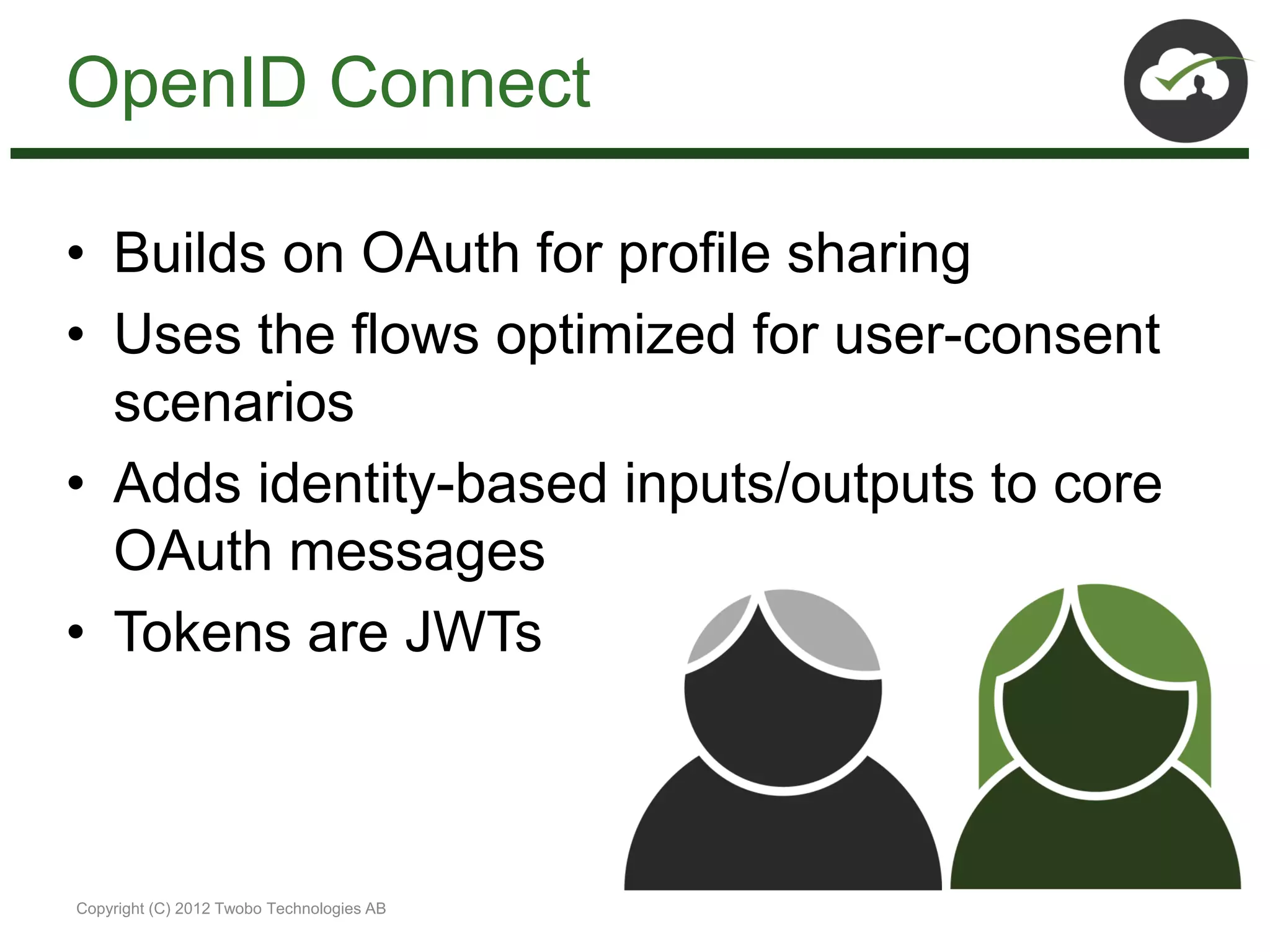
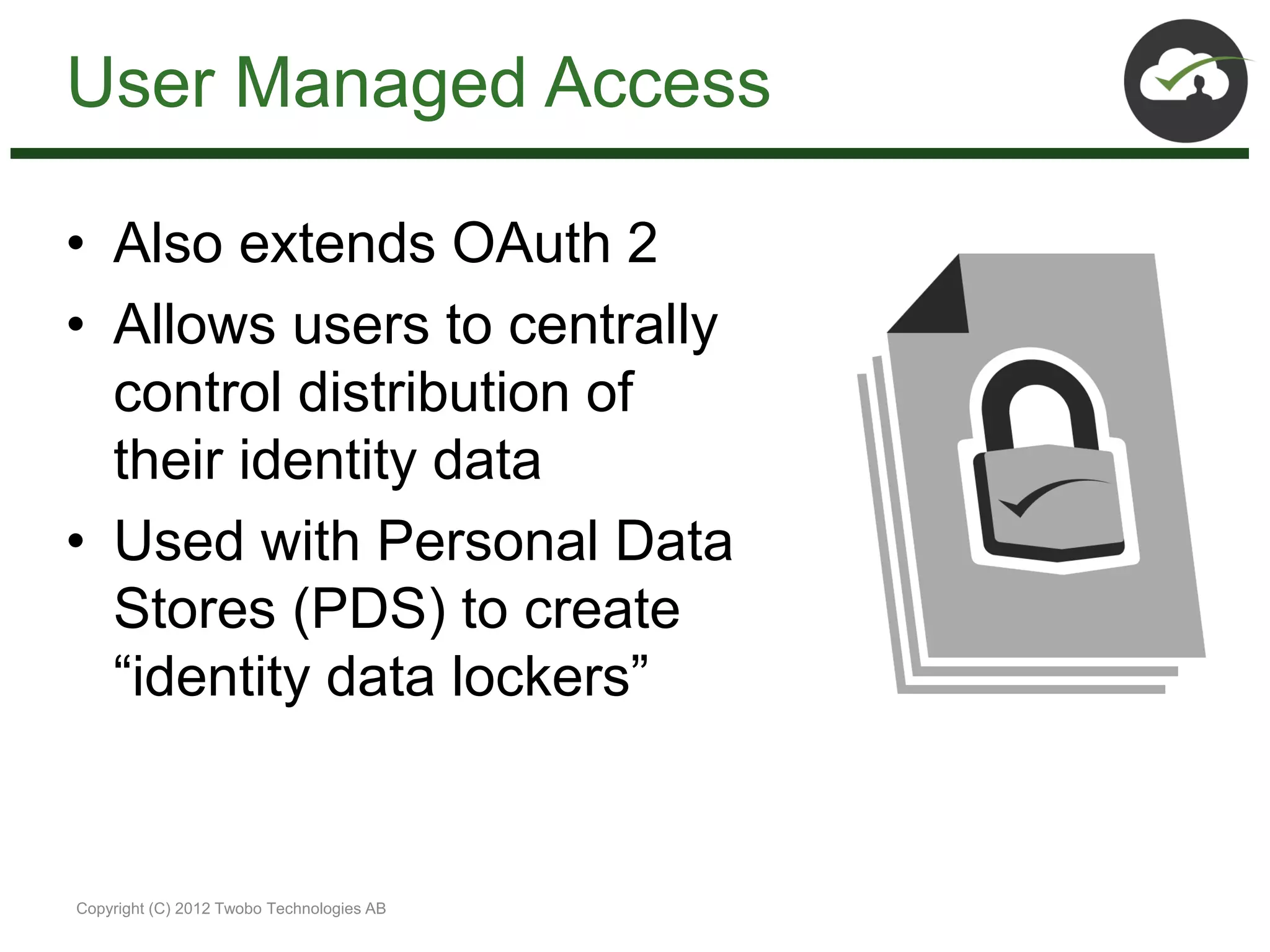
The document discusses the impact of mobile and cloud technologies on business operations, emphasizing the centrality of identity management in this transformation. It highlights the need for seamless access to cloud applications while addressing security concerns, and introduces new standards such as OpenID Connect, SCIM, SAML, and OAuth for managing identity and access. The author advocates for integrating existing technologies with these new standards to optimize workflows and enhance security in mobile environments.