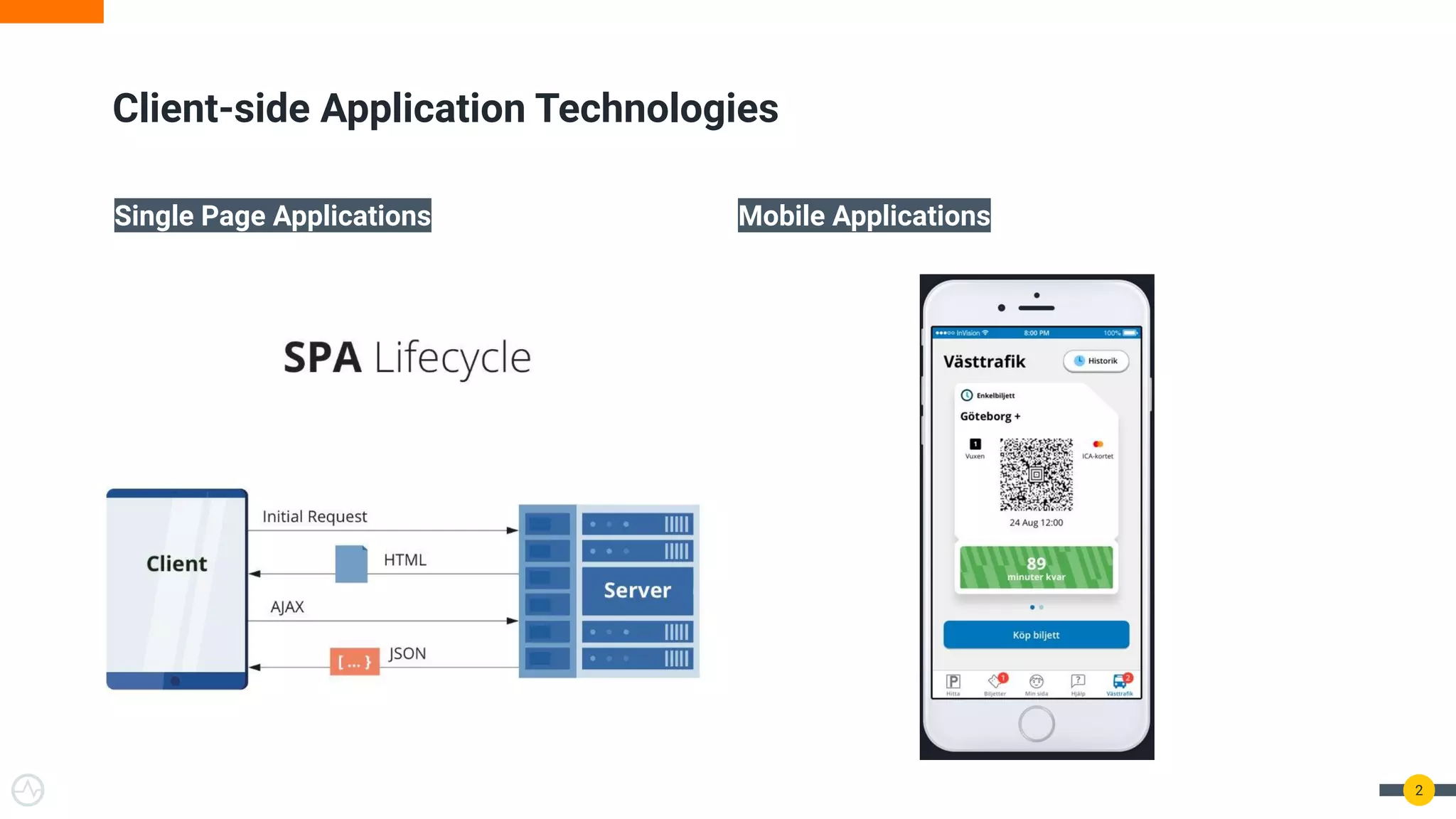
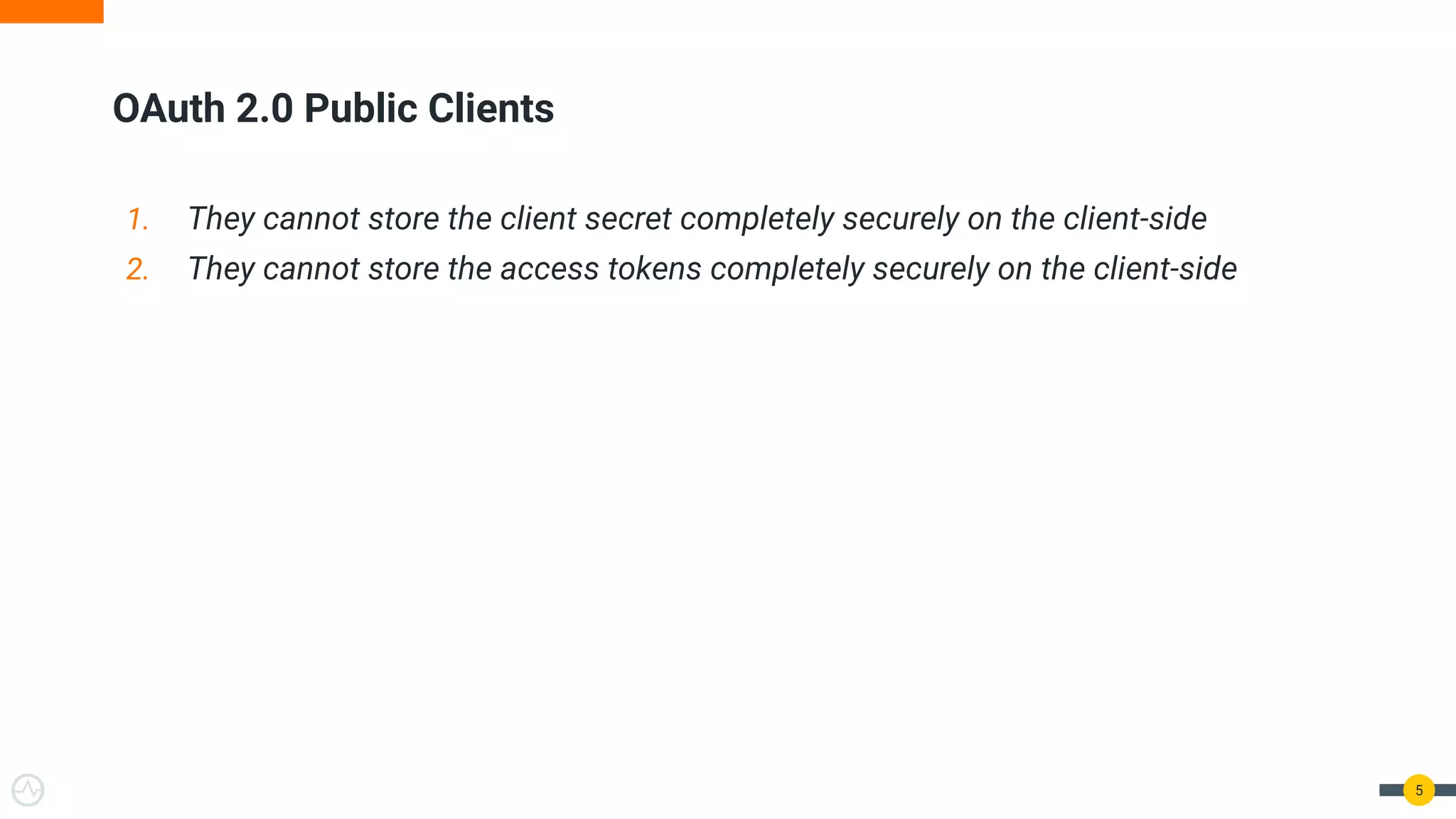
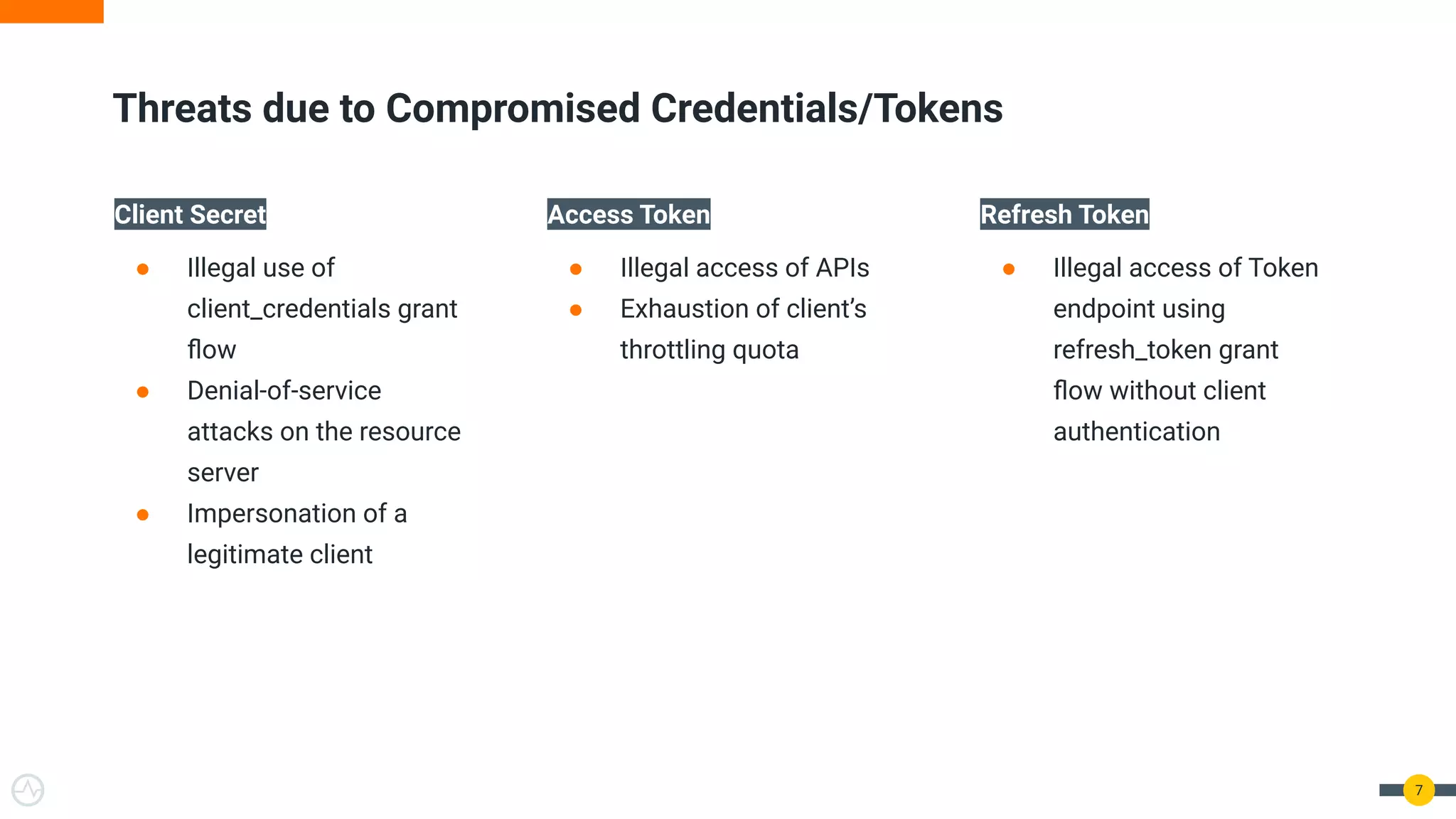
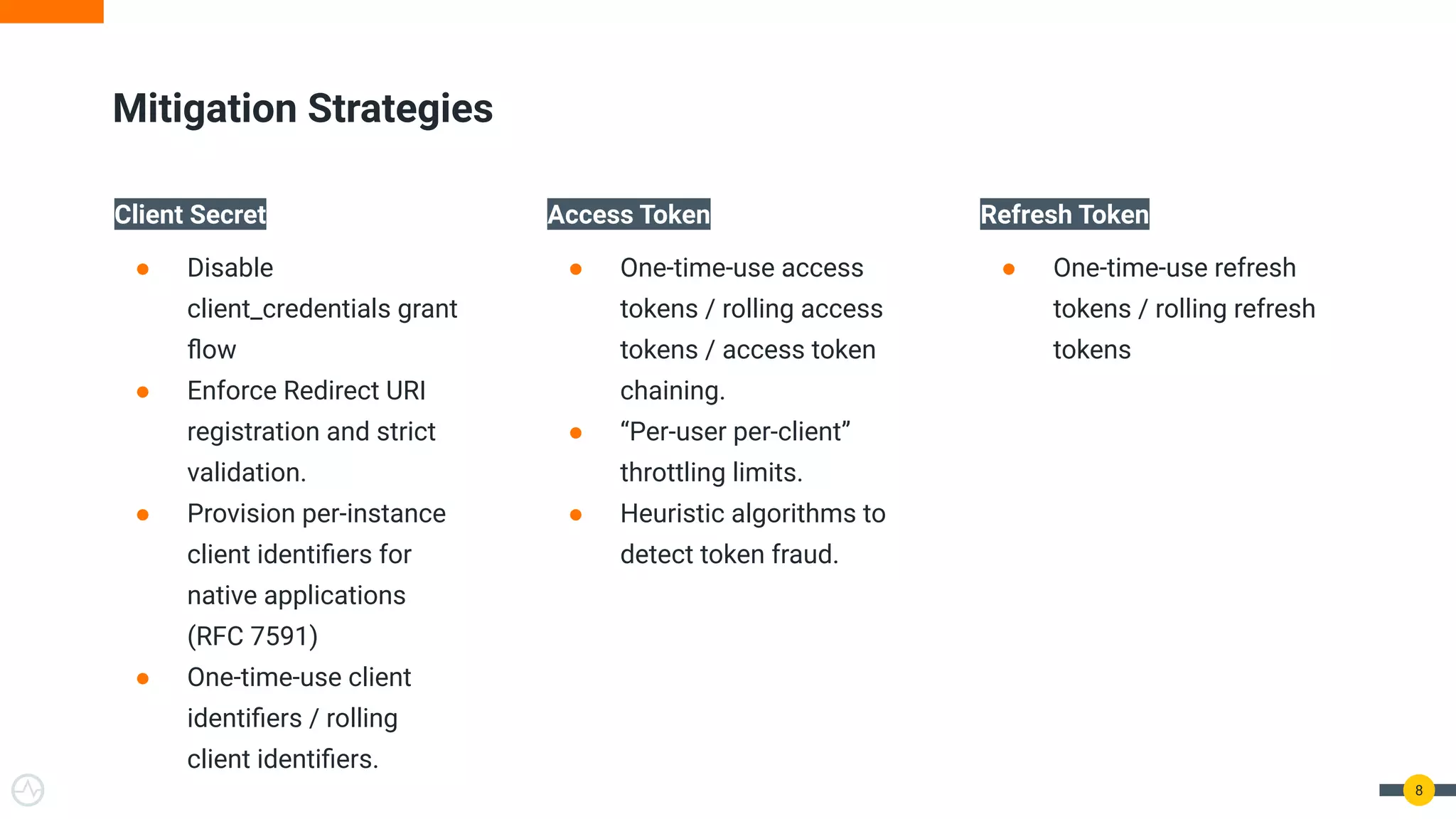
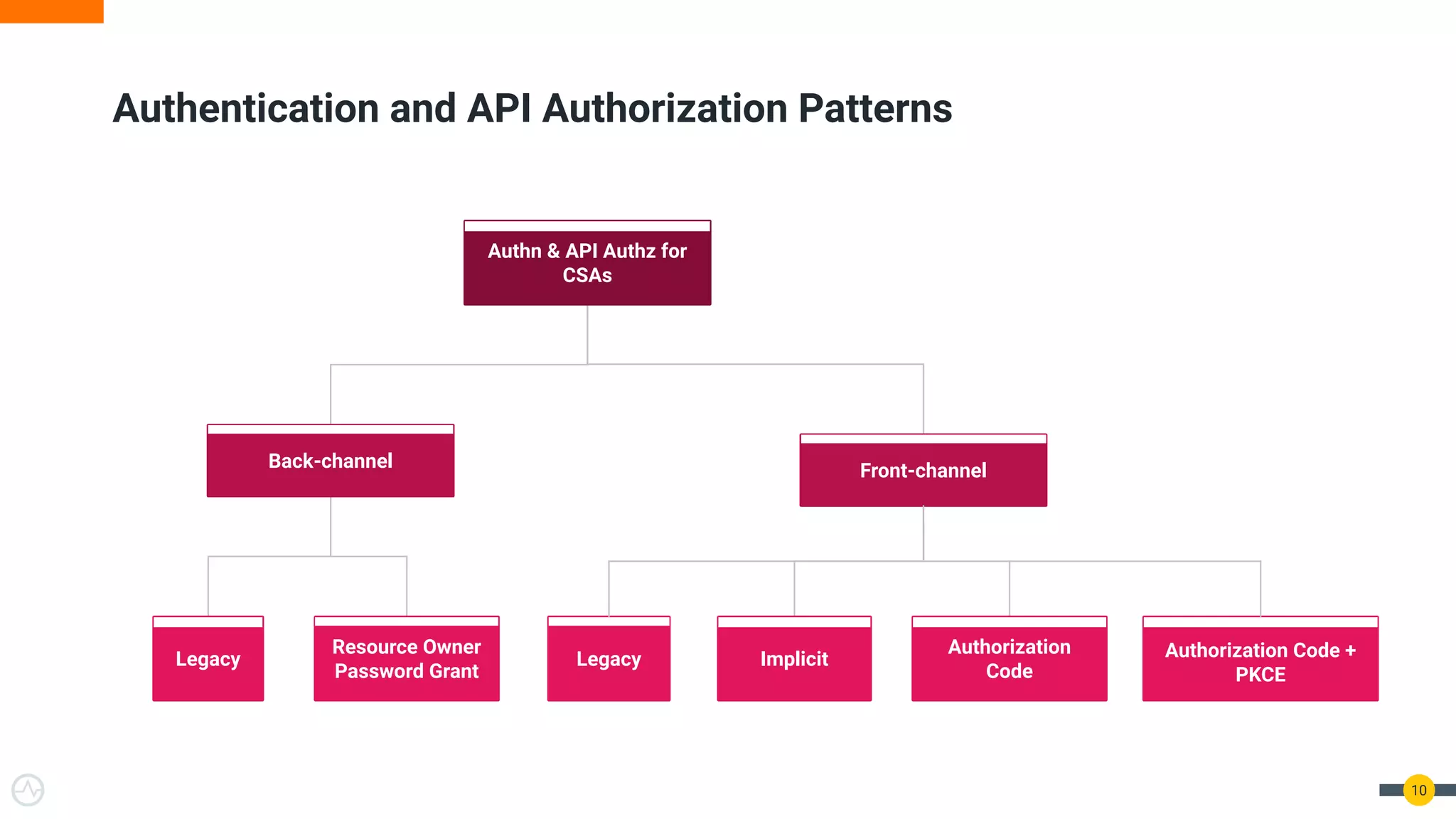
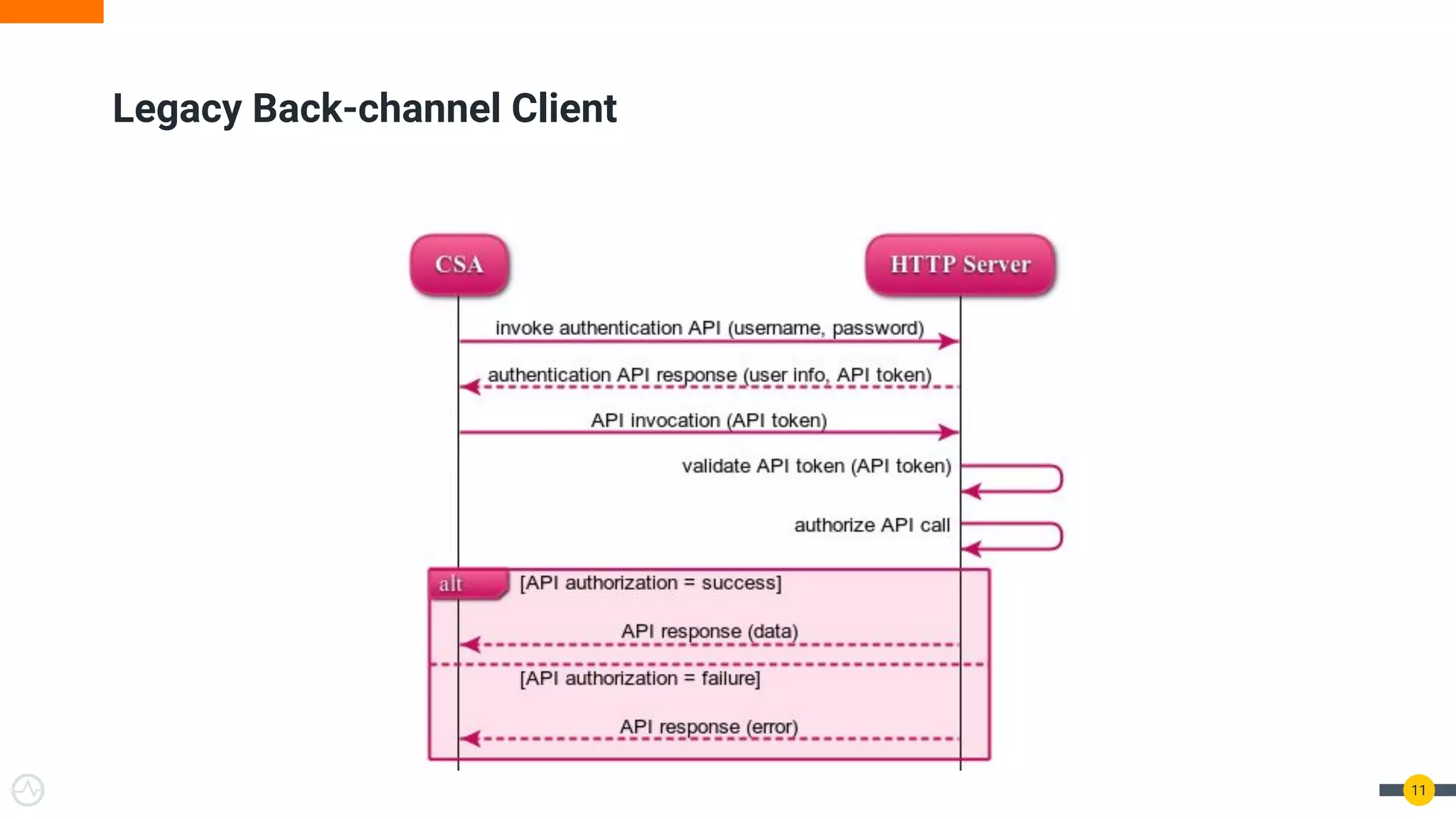
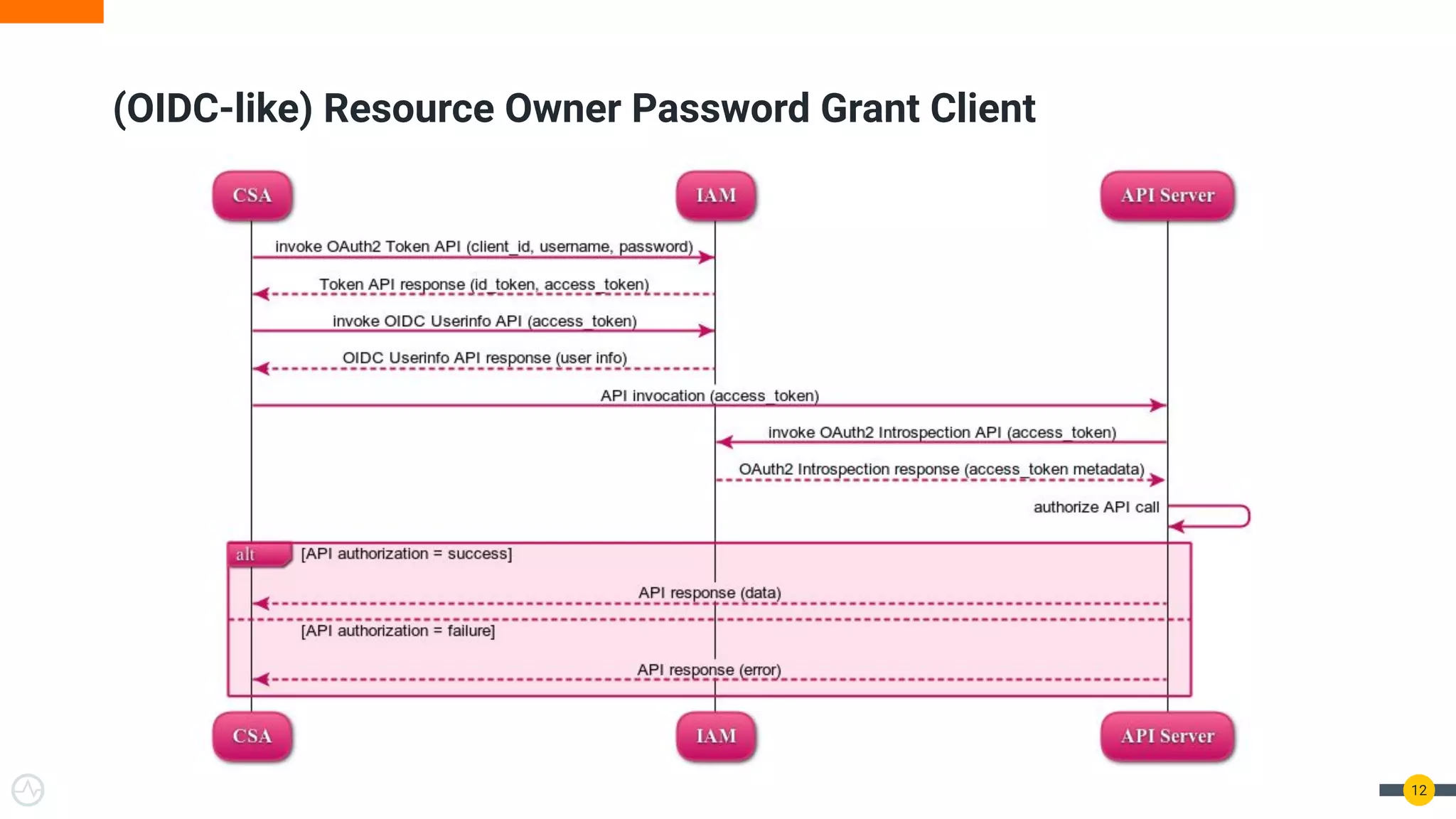
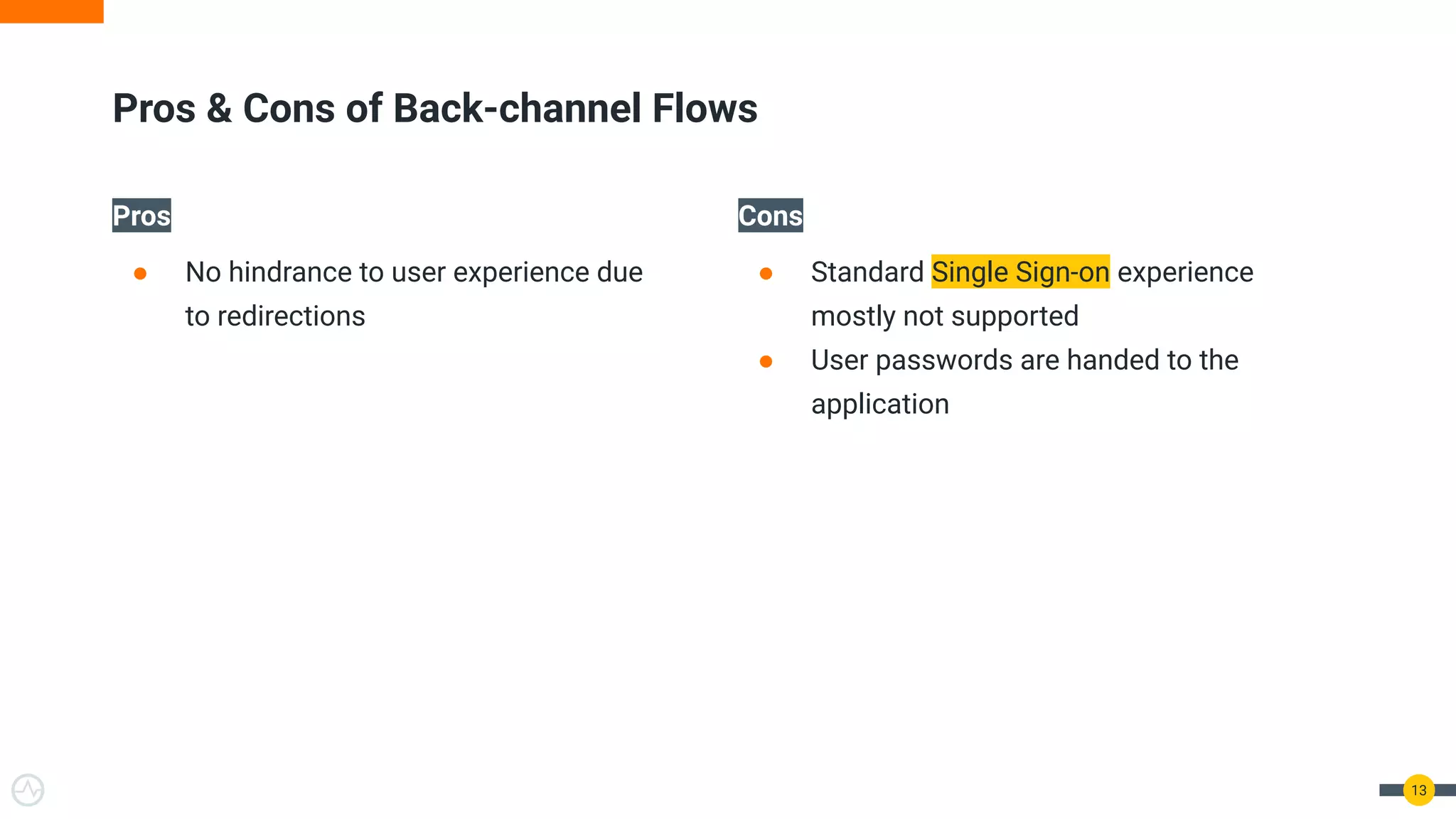
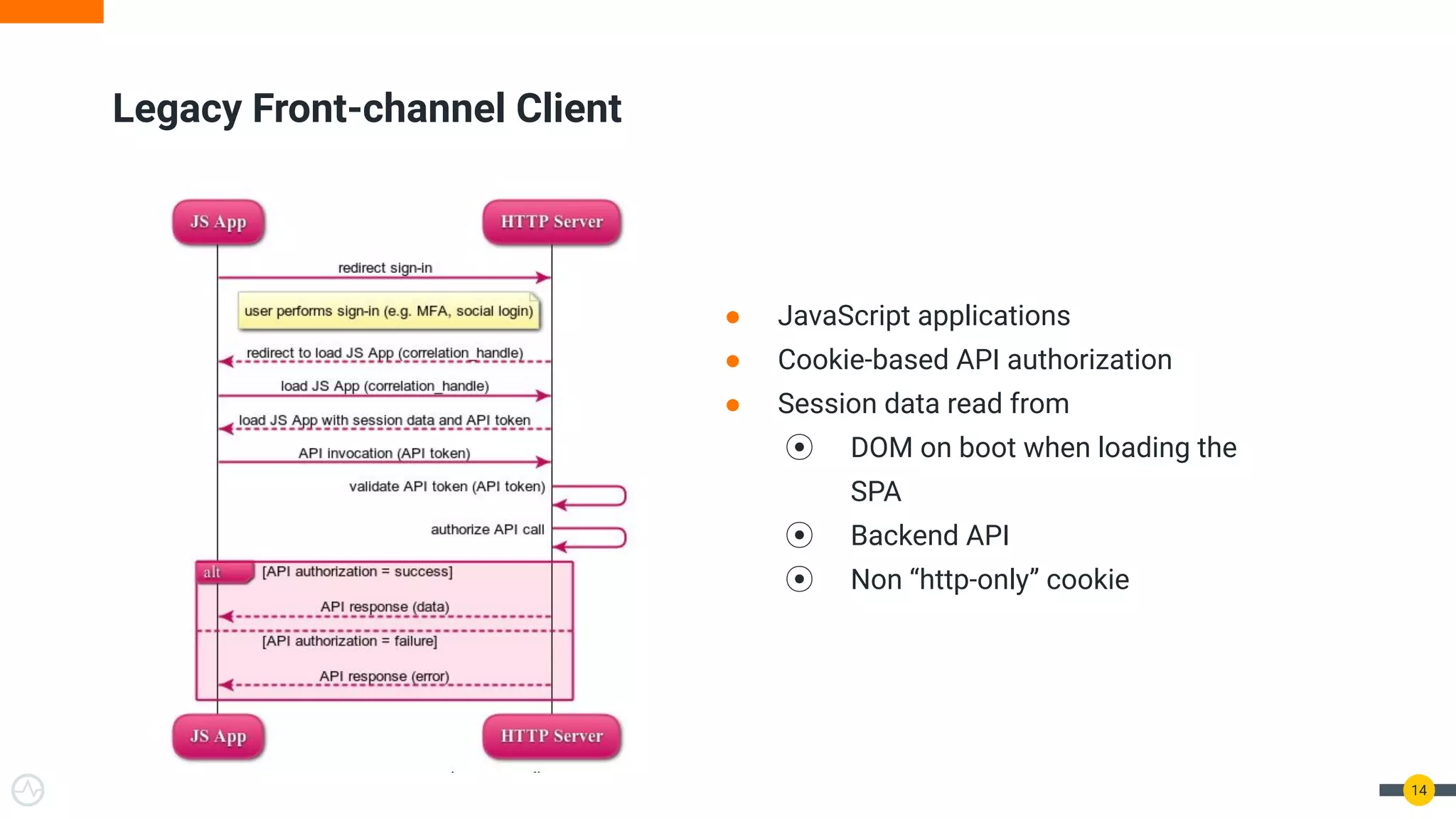
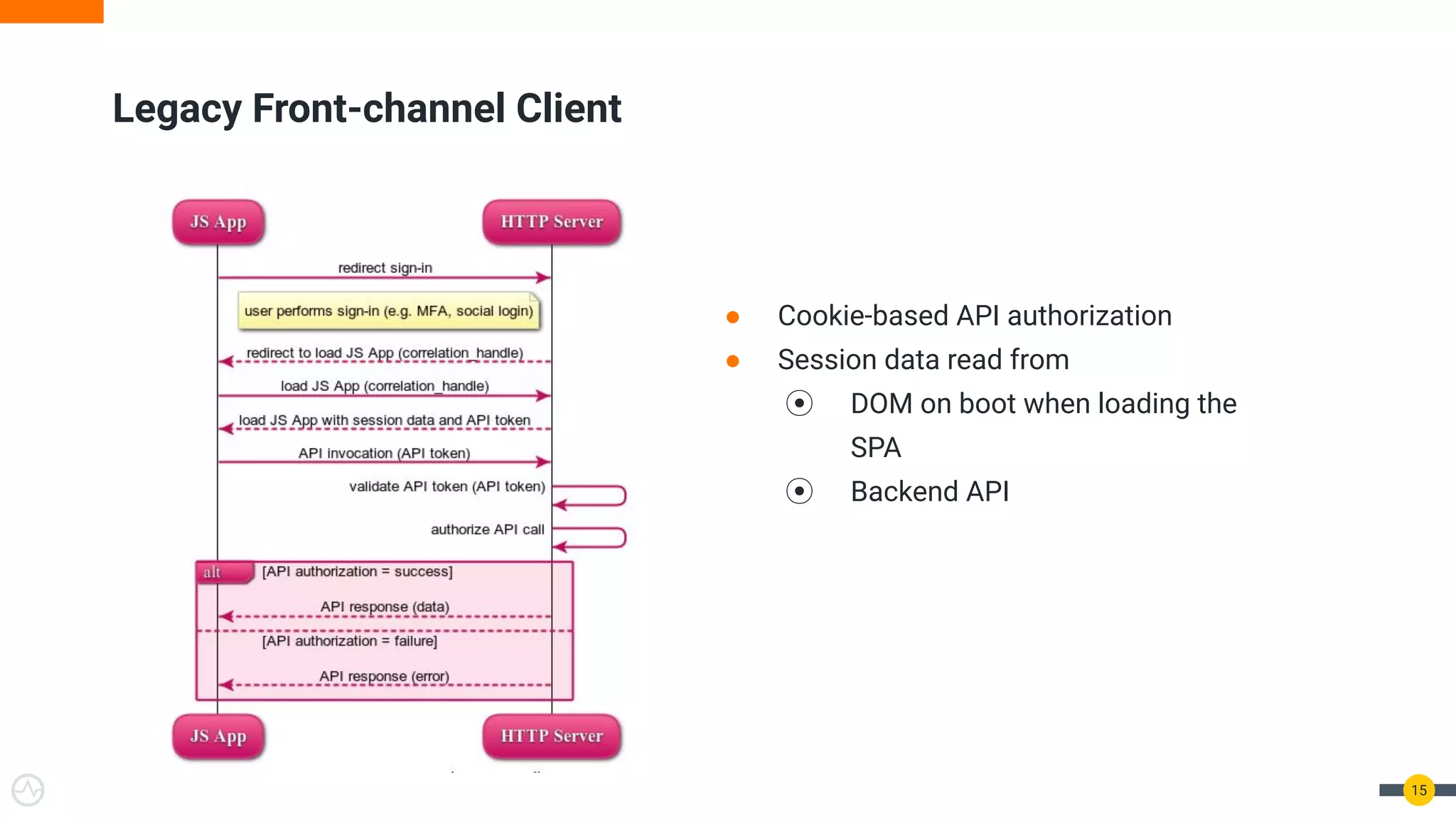
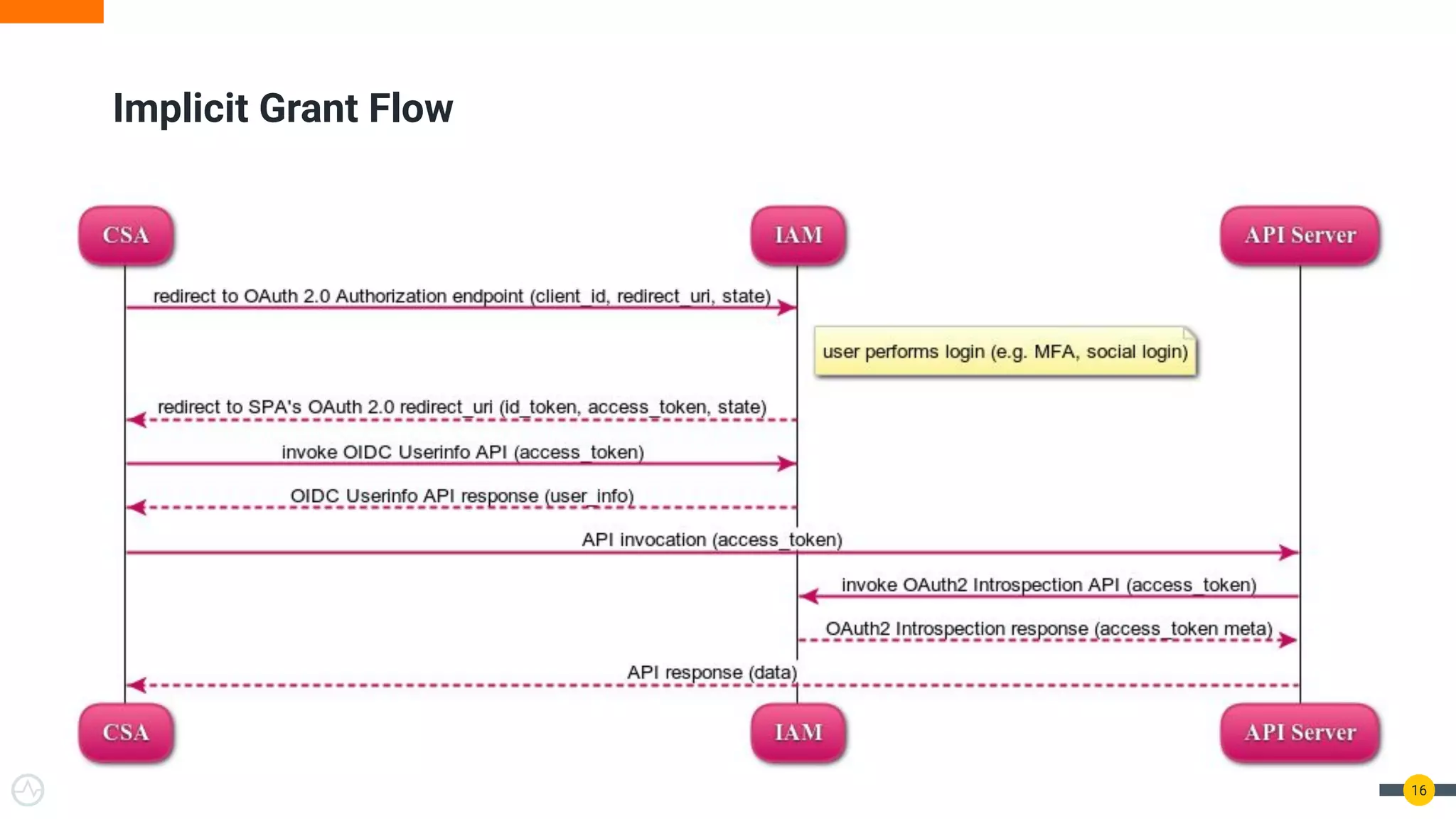
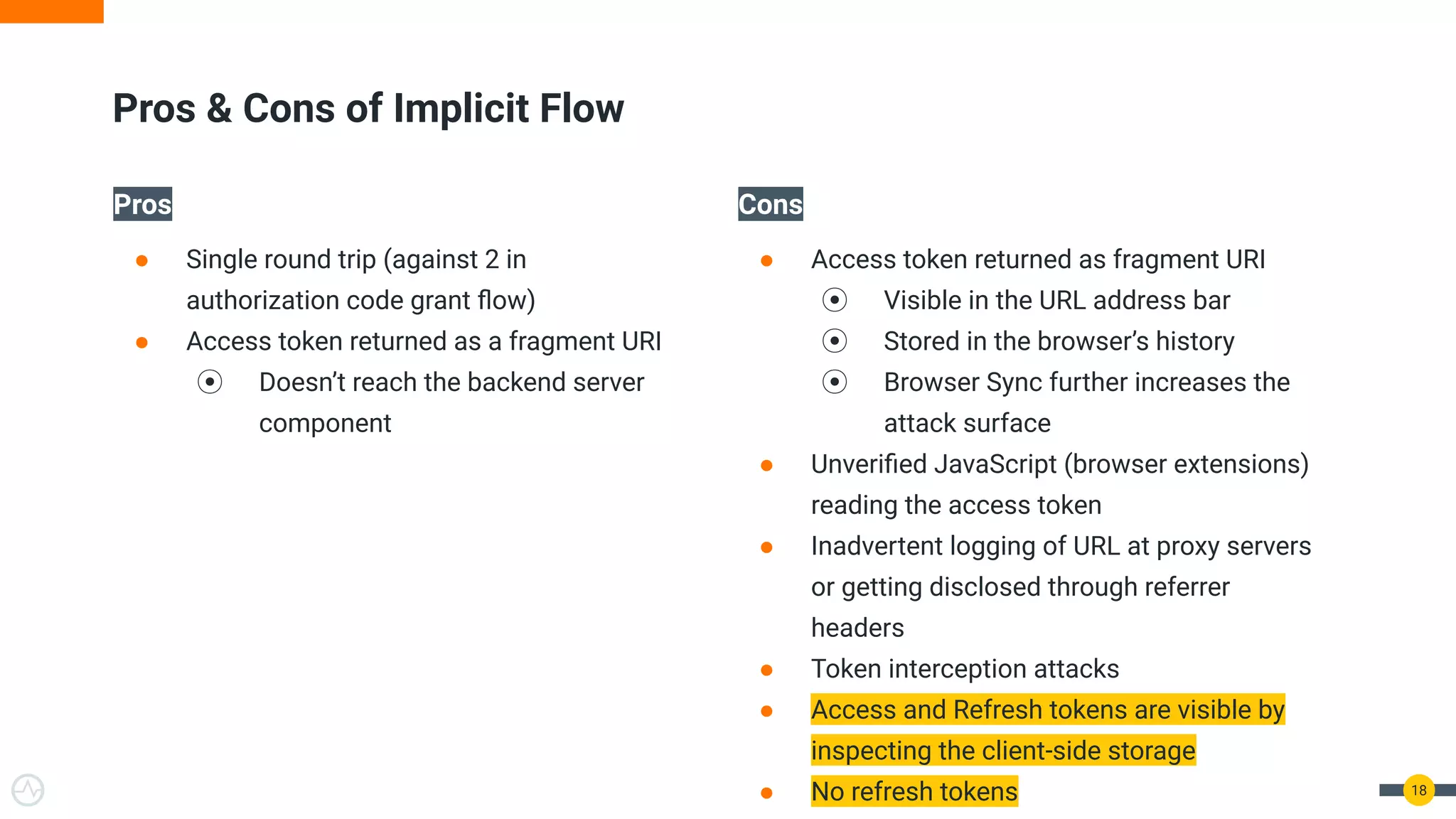
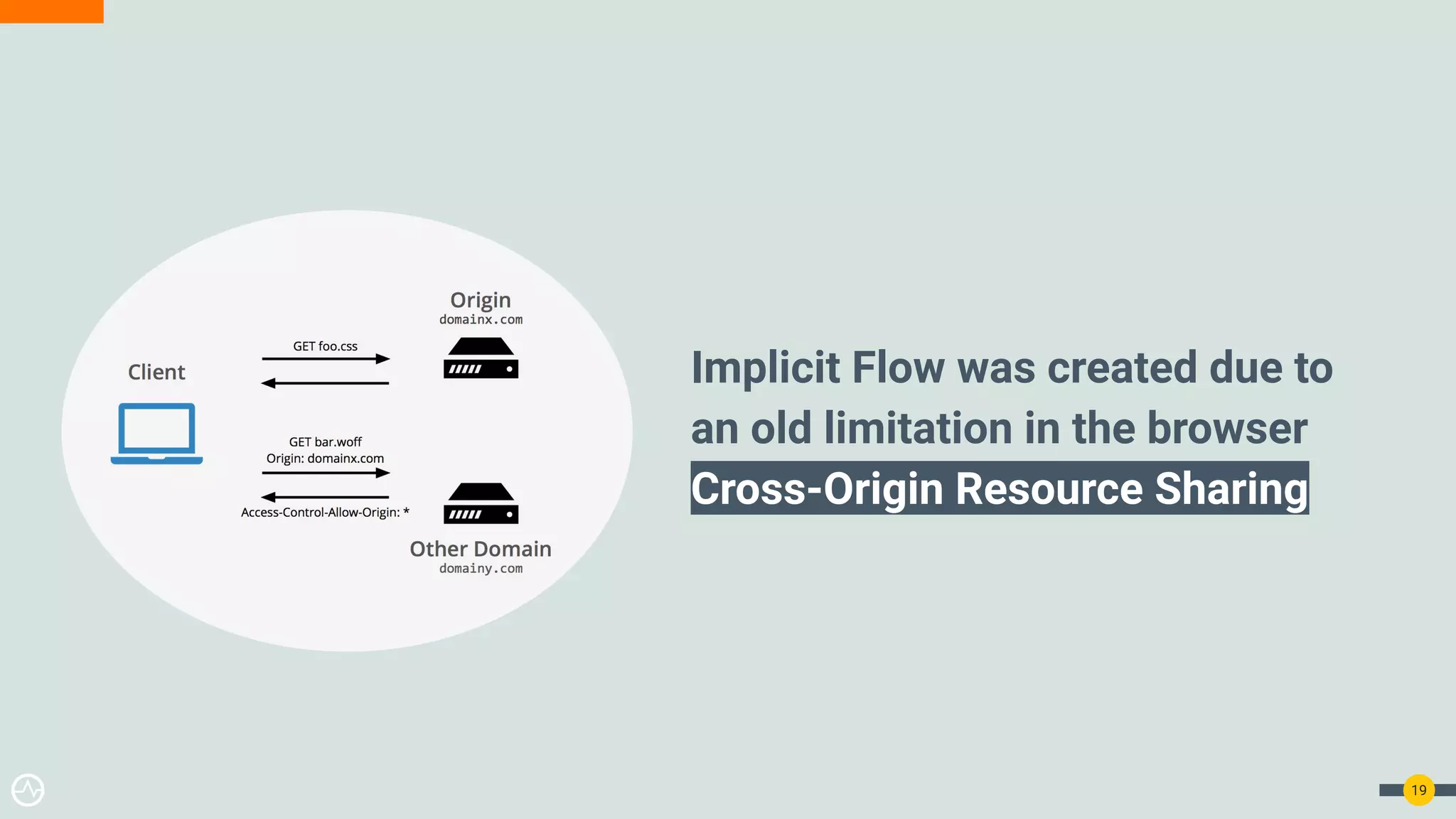
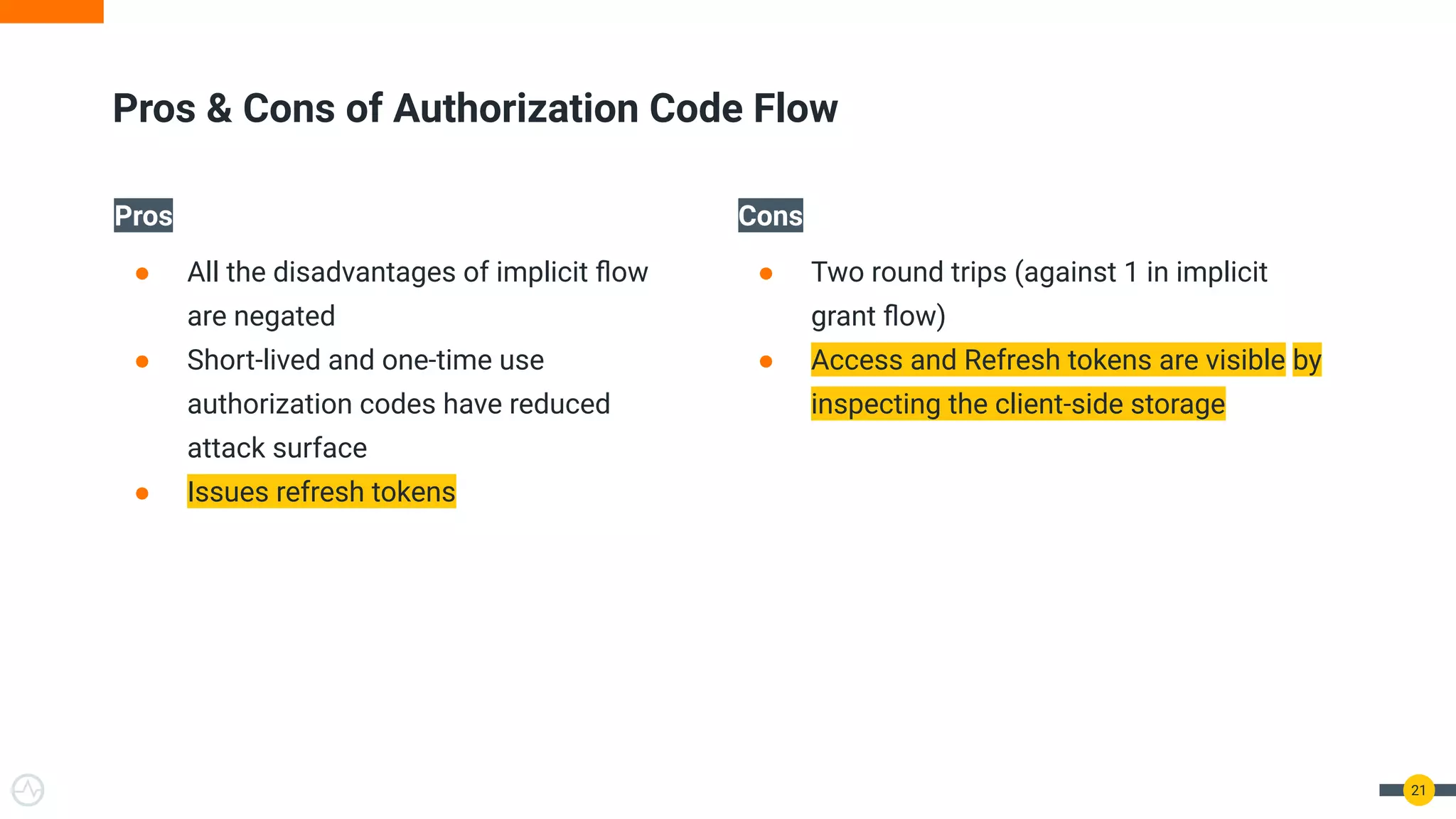
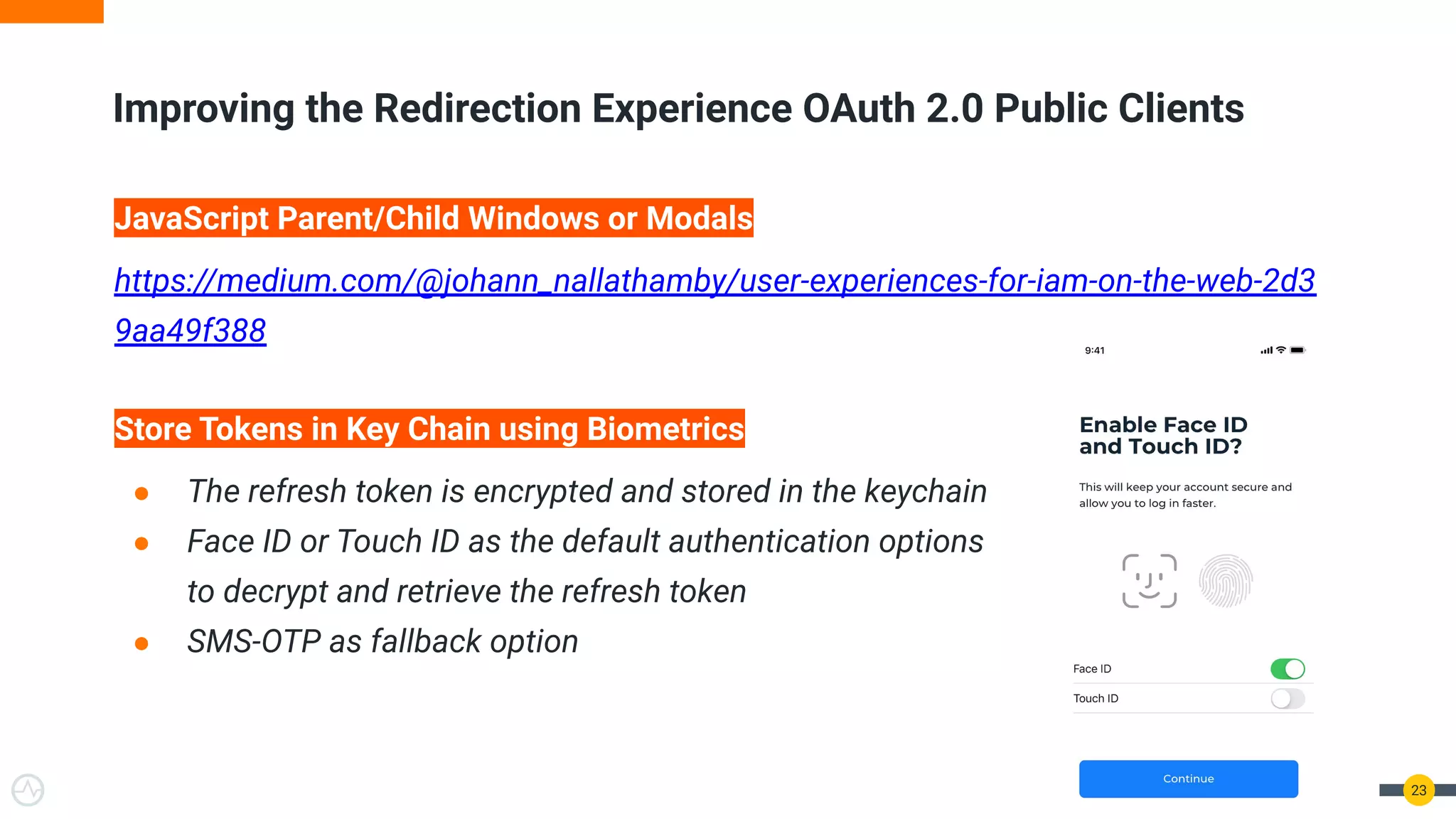
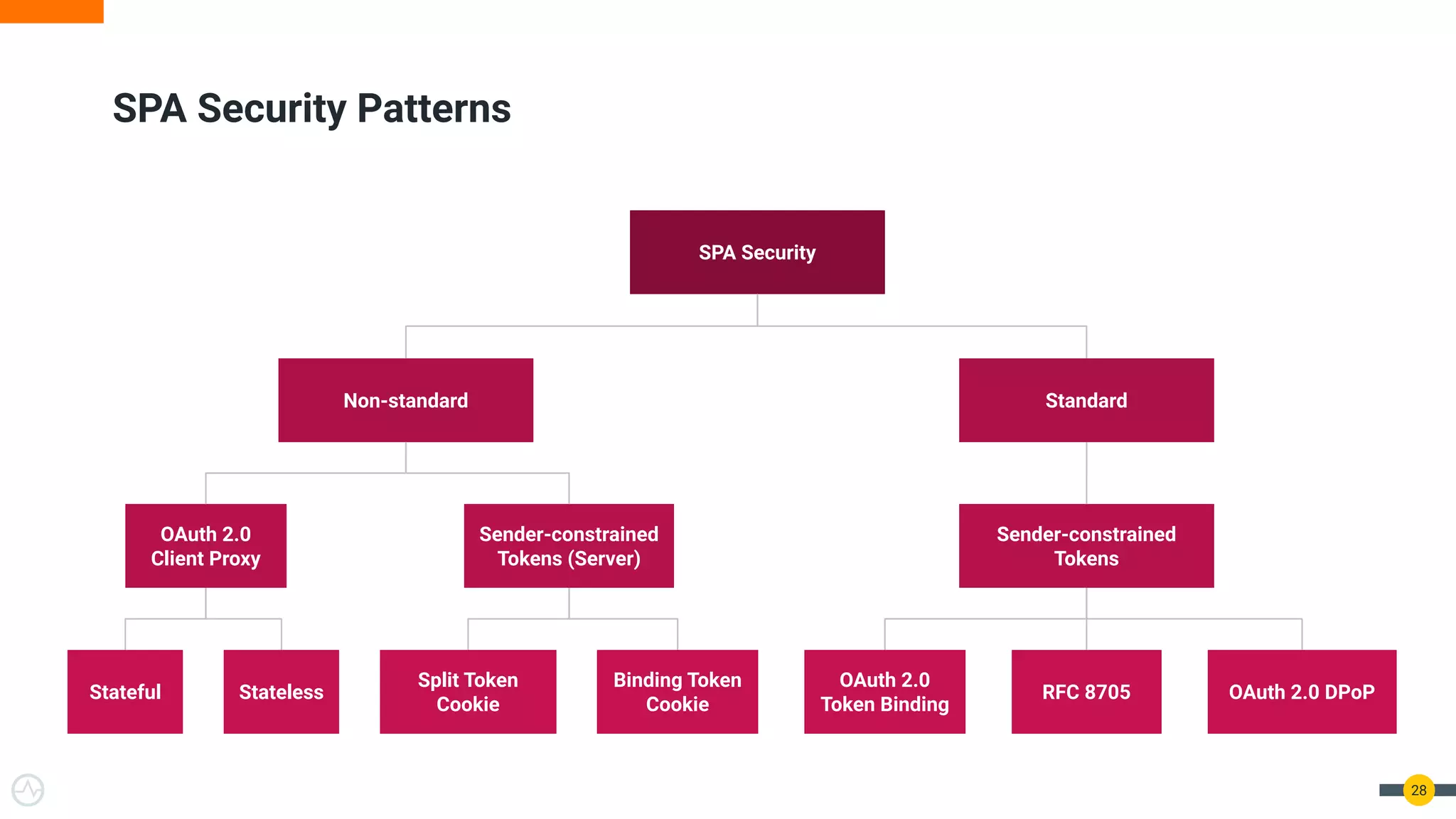
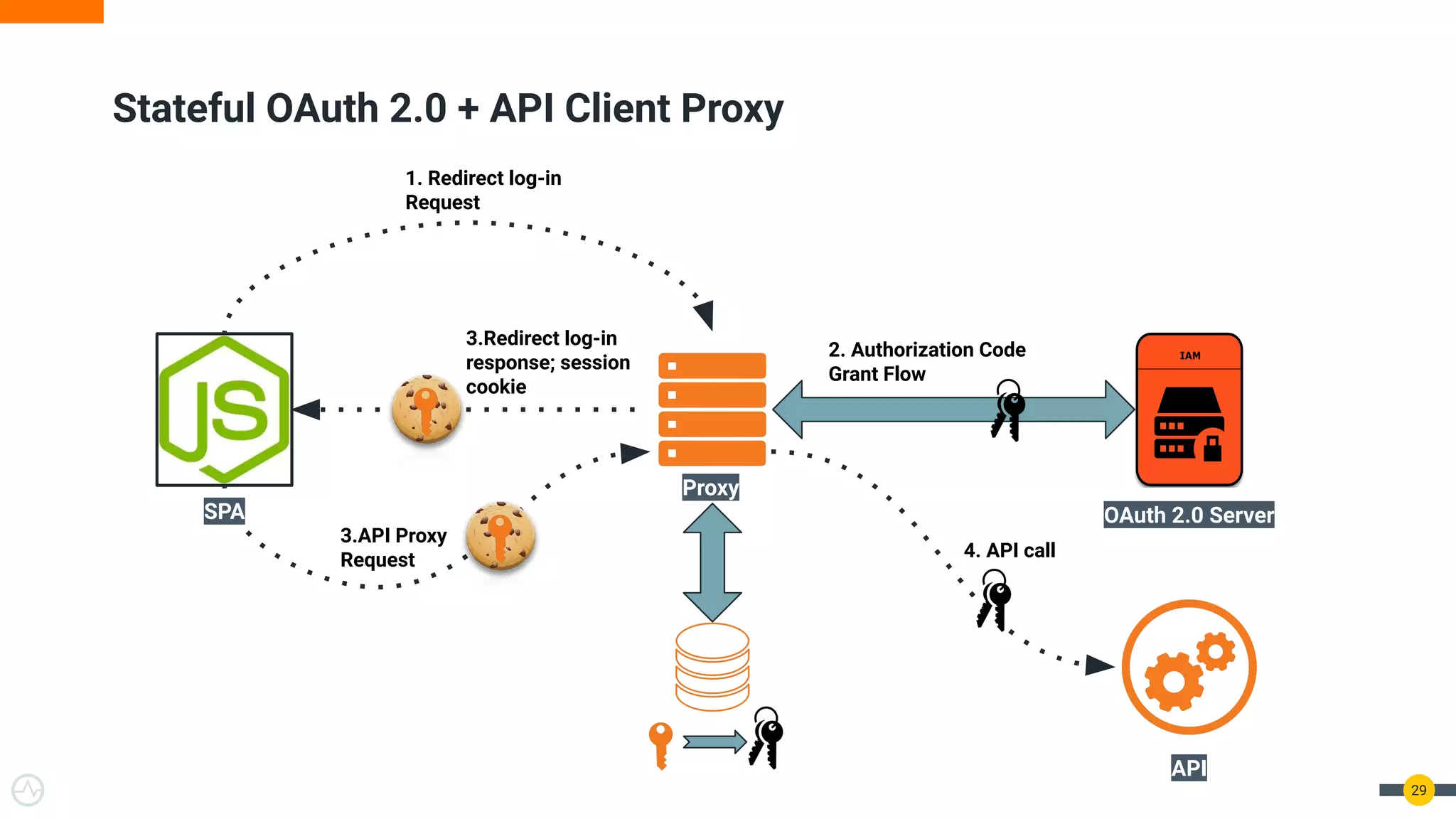
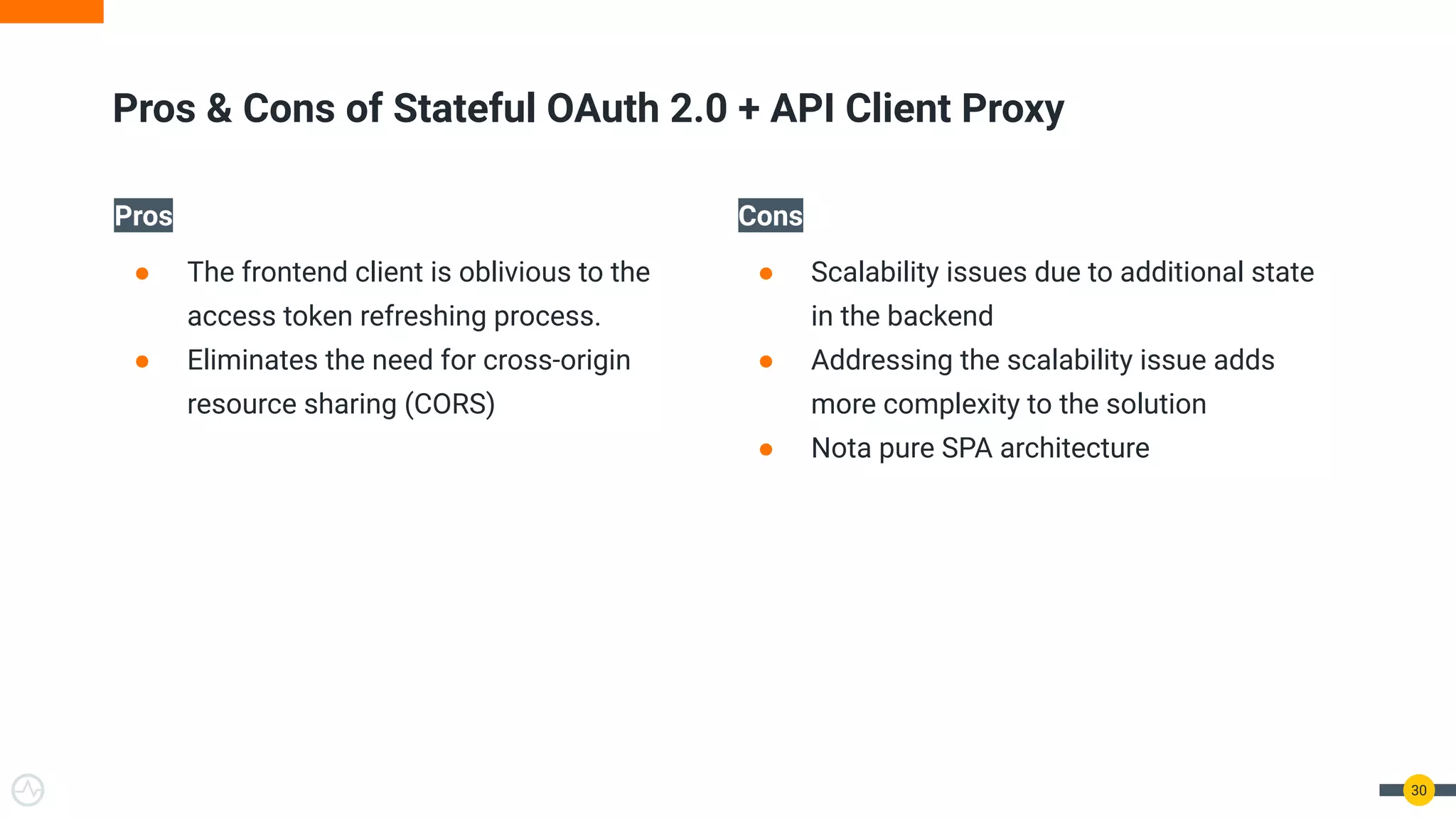
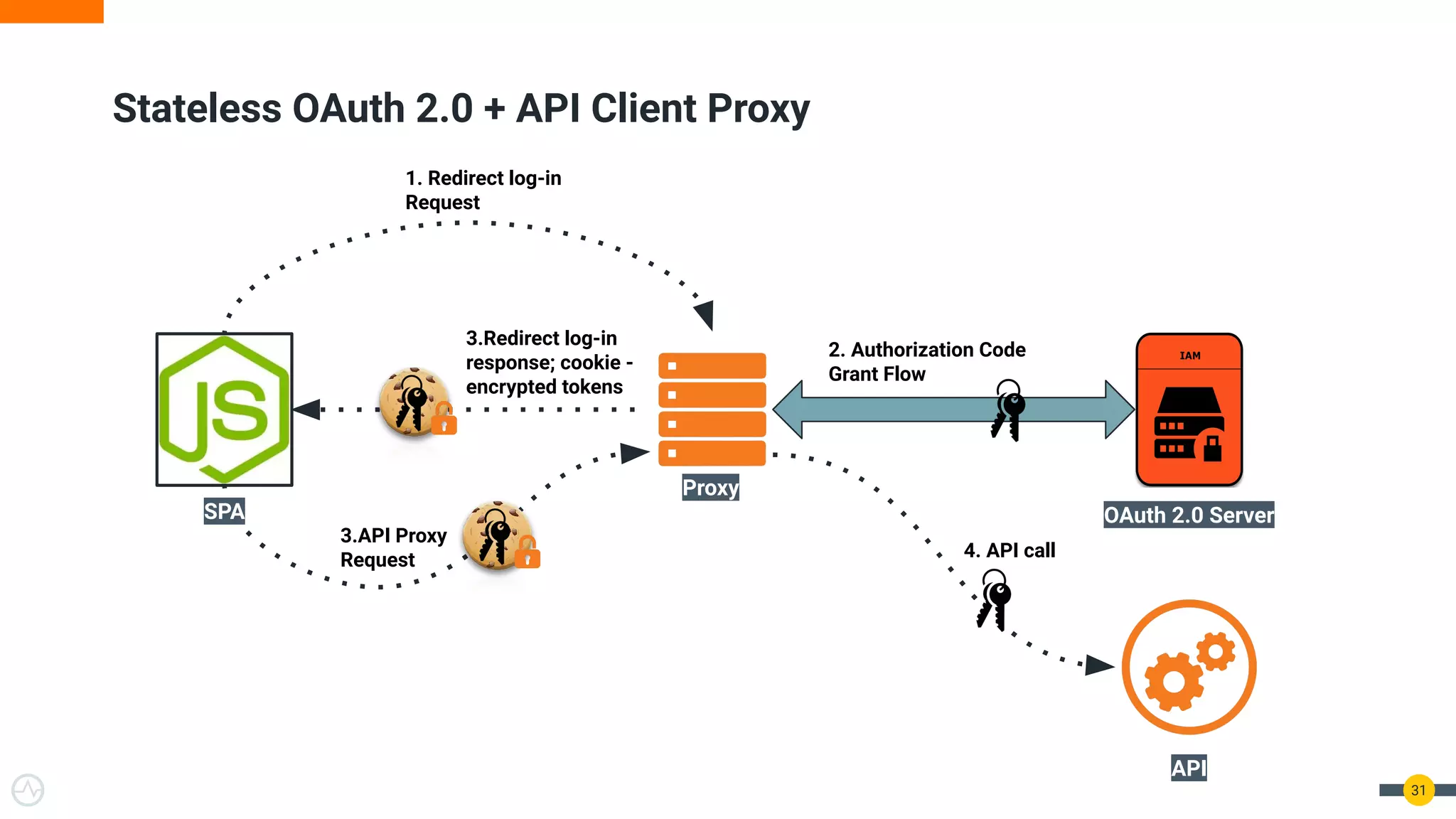
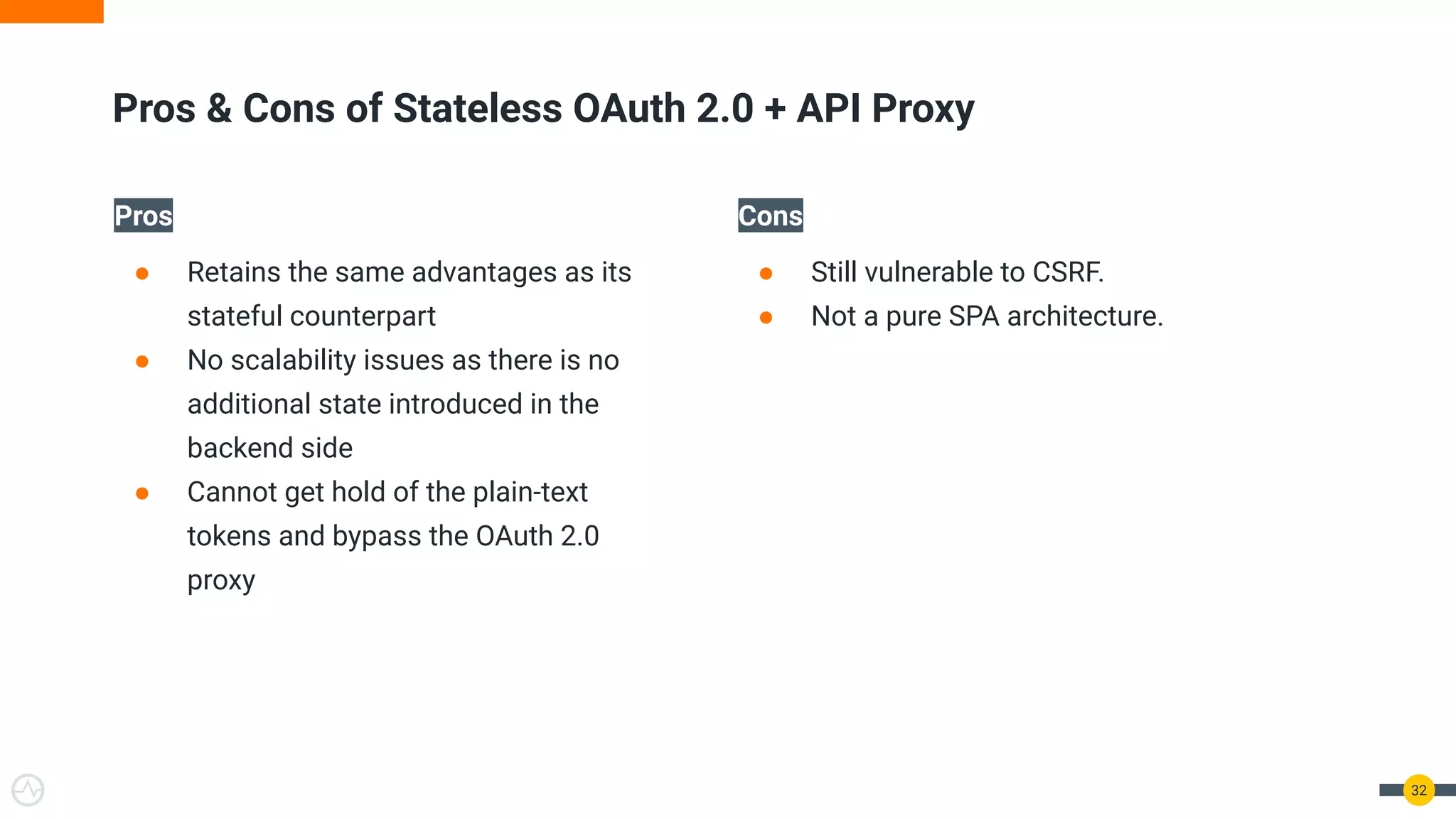
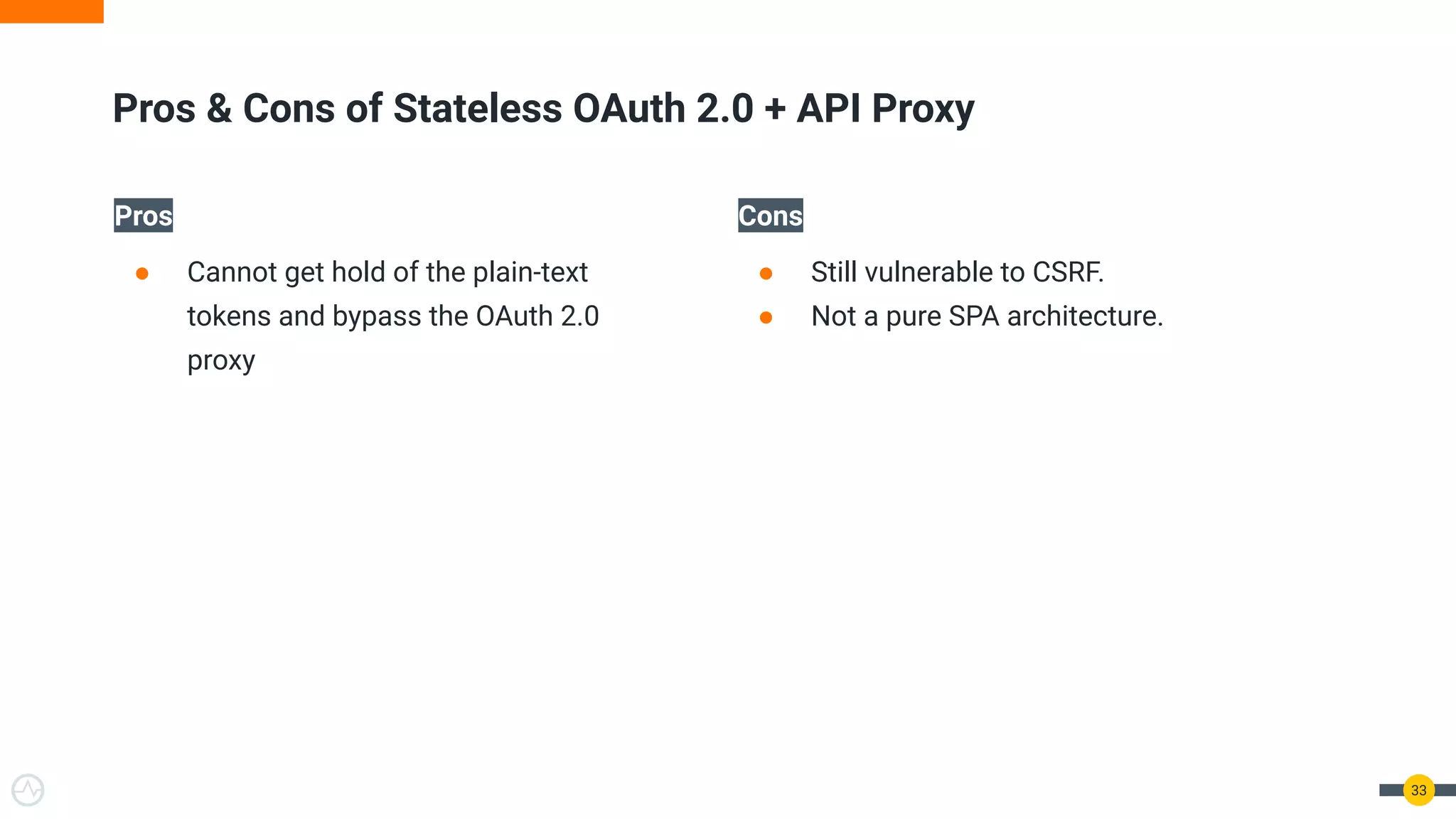
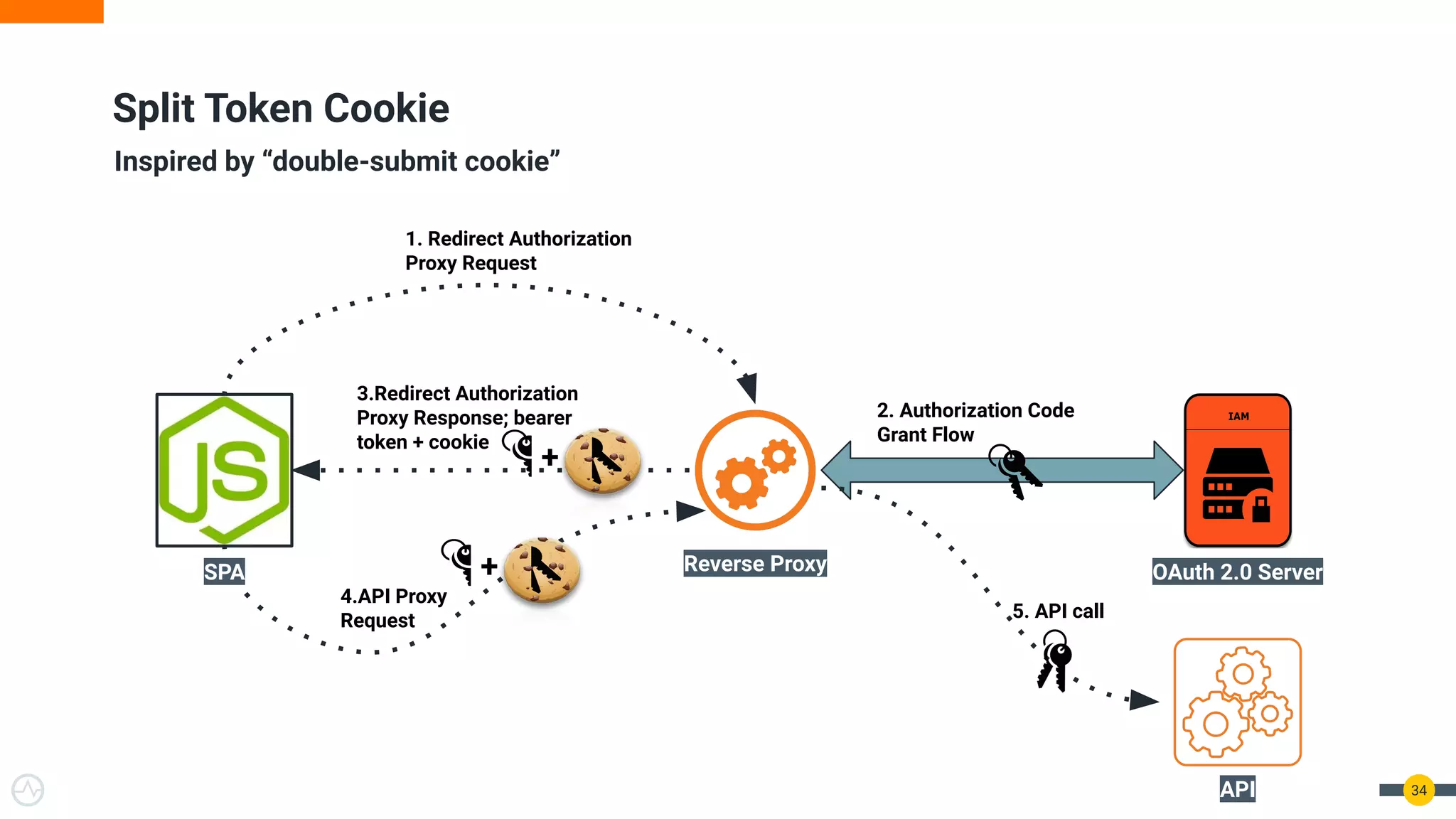
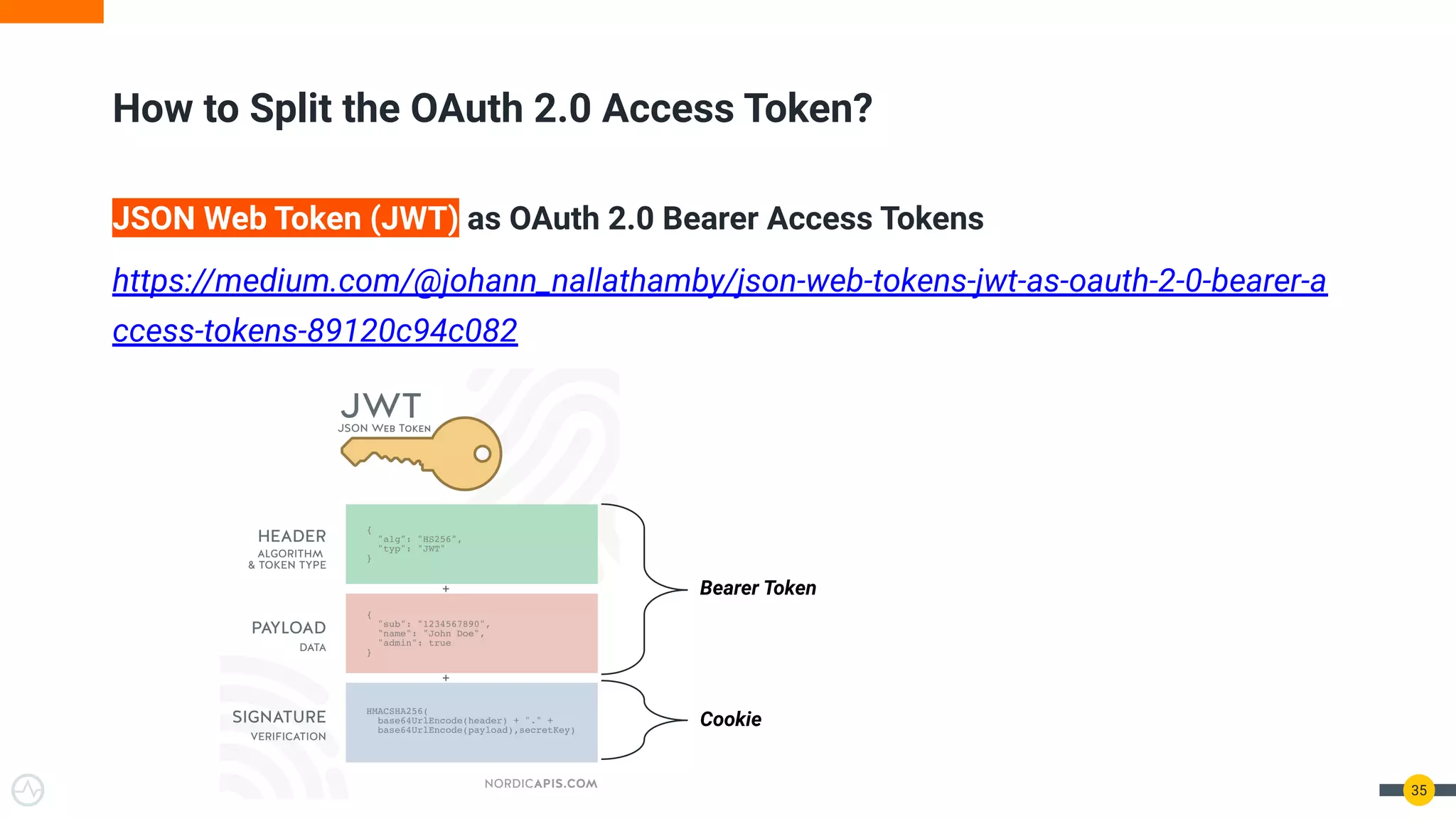
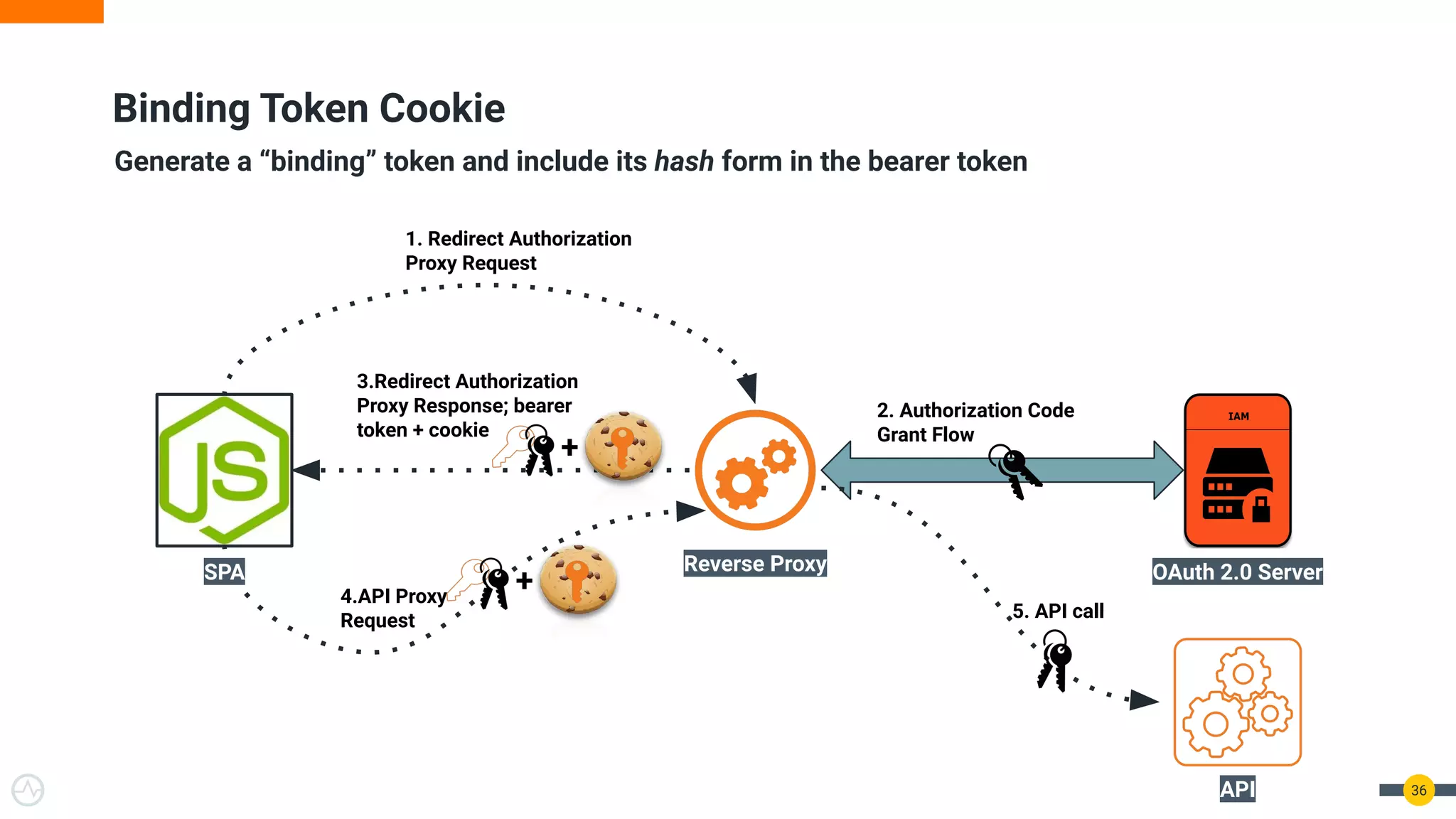
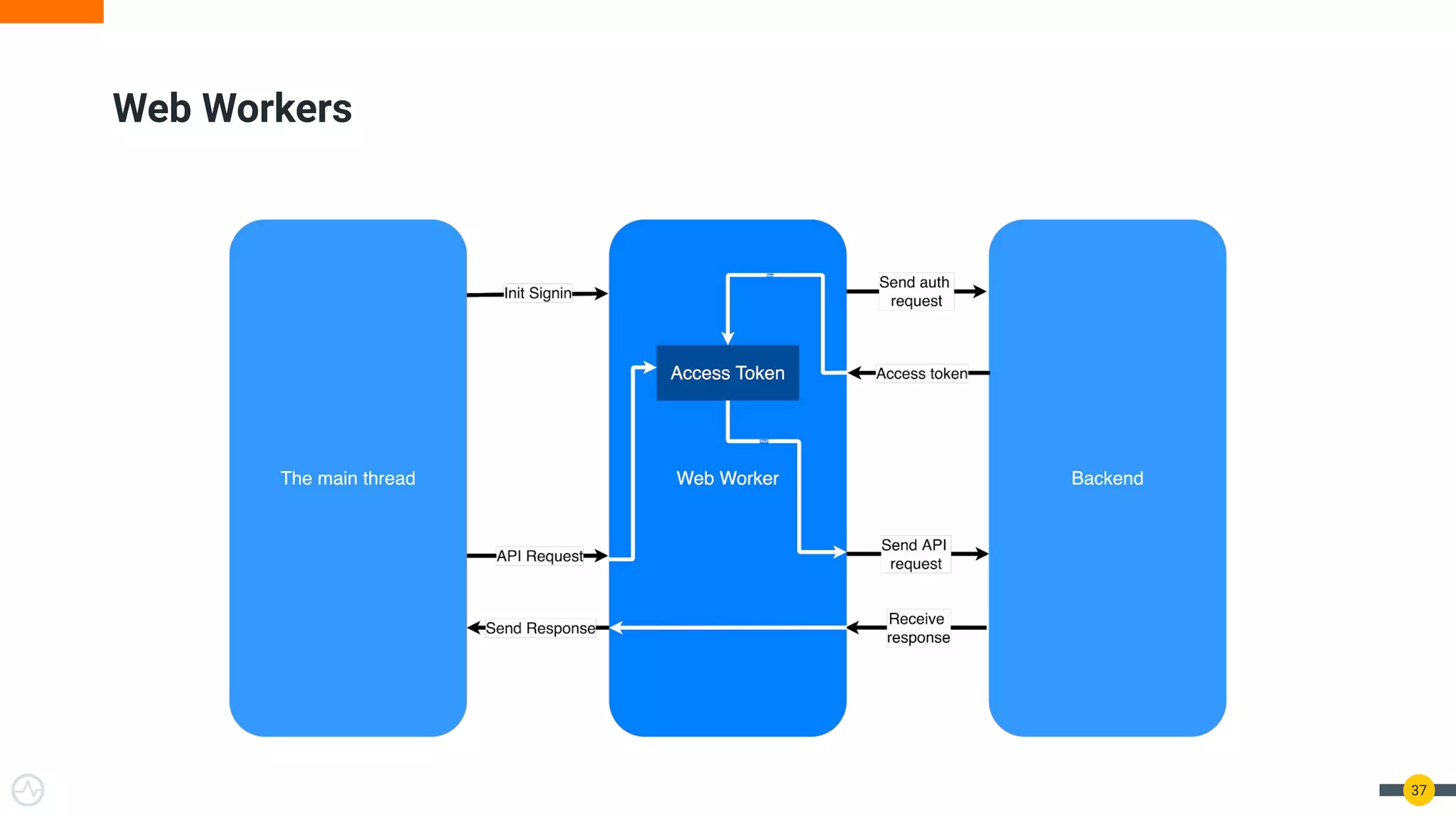
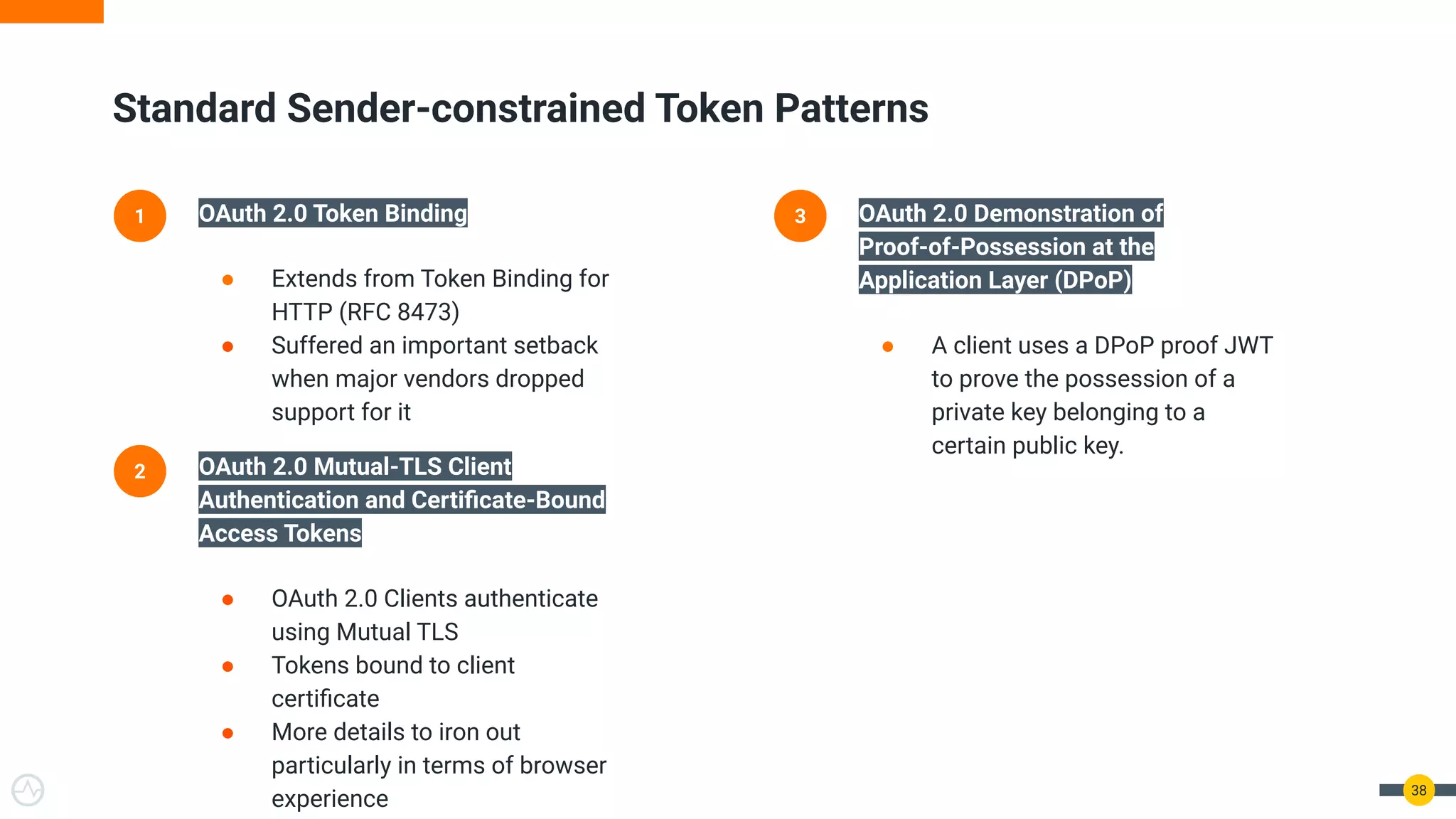
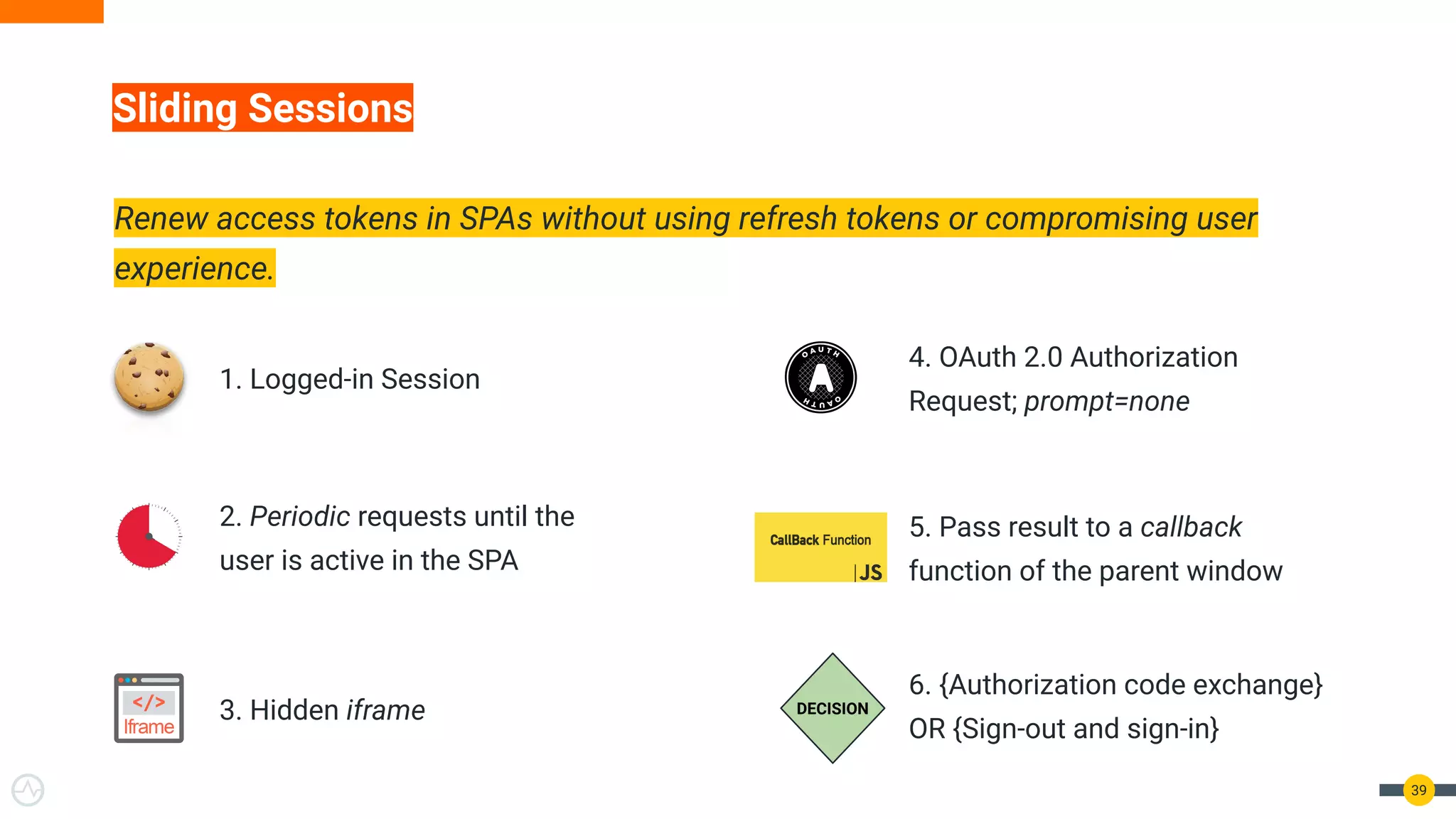
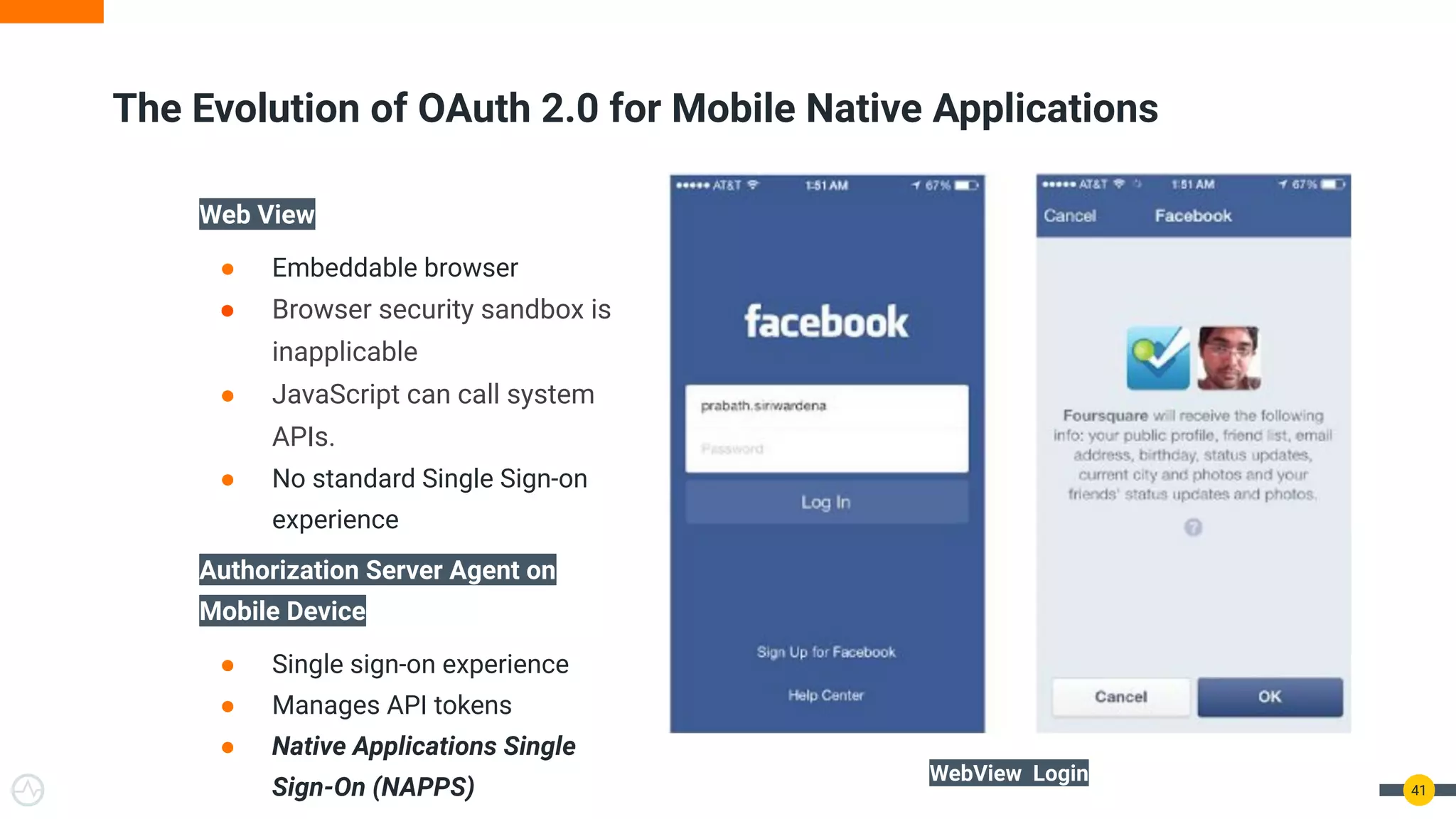
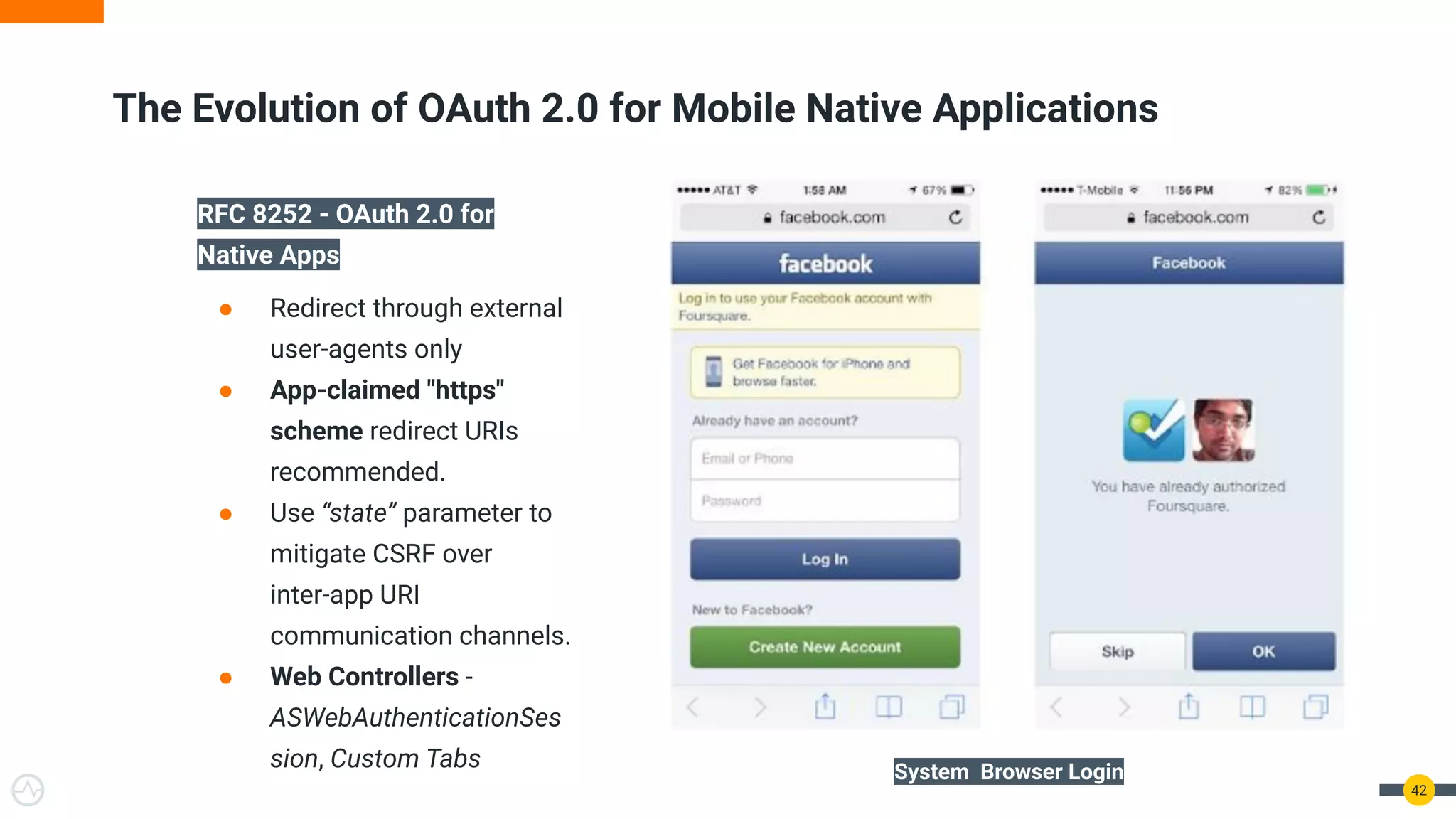
The document discusses the evolution of API security for client-side applications, highlighting the significance of OAuth 2.0 and OpenID Connect as standards for authentication and authorization. It outlines the limitations and vulnerabilities of client-side applications, including token storage issues and potential security threats, while presenting various mitigation strategies. The document emphasizes the importance of secure token management and exploring architectures that enhance security without compromising user experience.