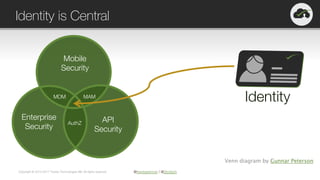
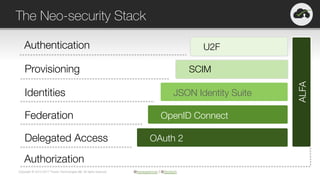
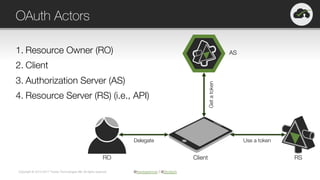
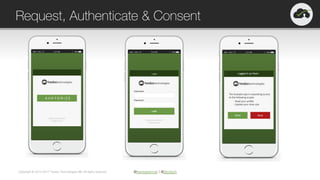
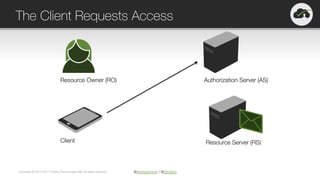
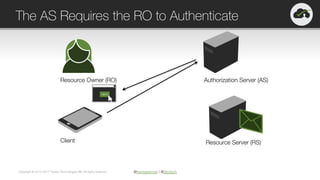
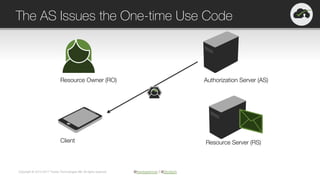
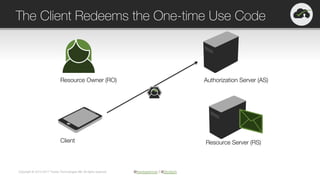
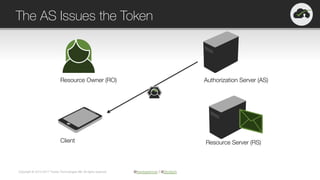
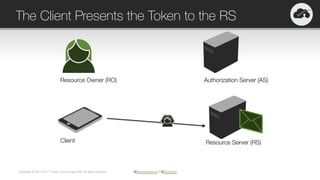
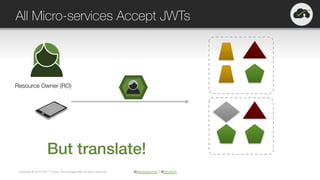
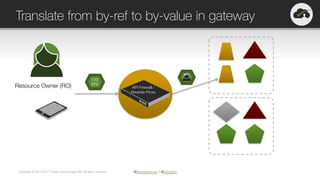
The document provides an overview of OAuth 2.0 and OpenID Connect, highlighting their significance in API security by clarifying misconceptions around API keys and focusing on delegated access, identity management, and token types. It outlines the OAuth 2.0 protocol, its actors, and the token issuance process, while also discussing the importance of using JWTs and the proper applications of OAuth. Additionally, it explores how these technologies can be implemented in microservices architectures and offers resources for further information.