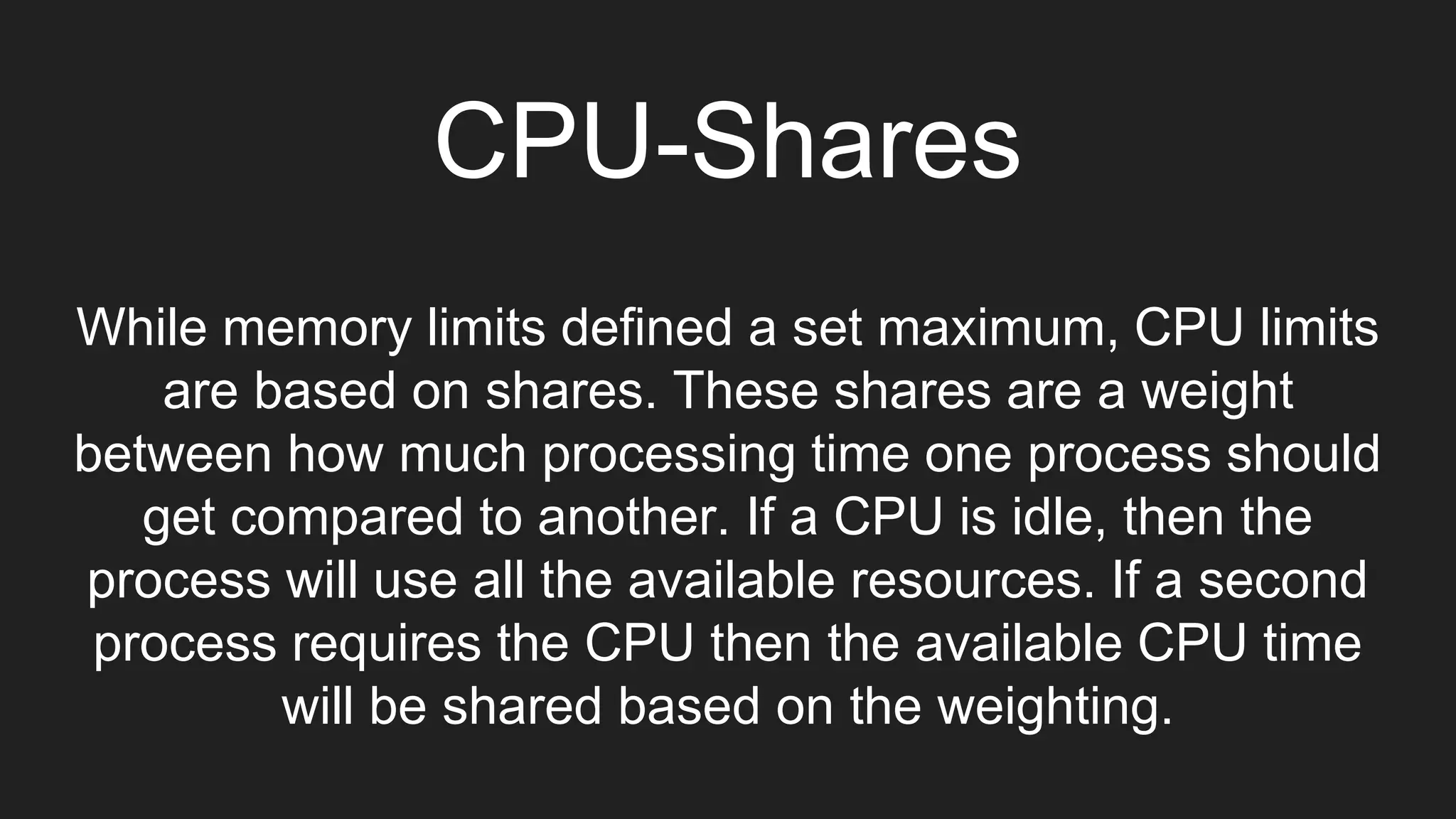
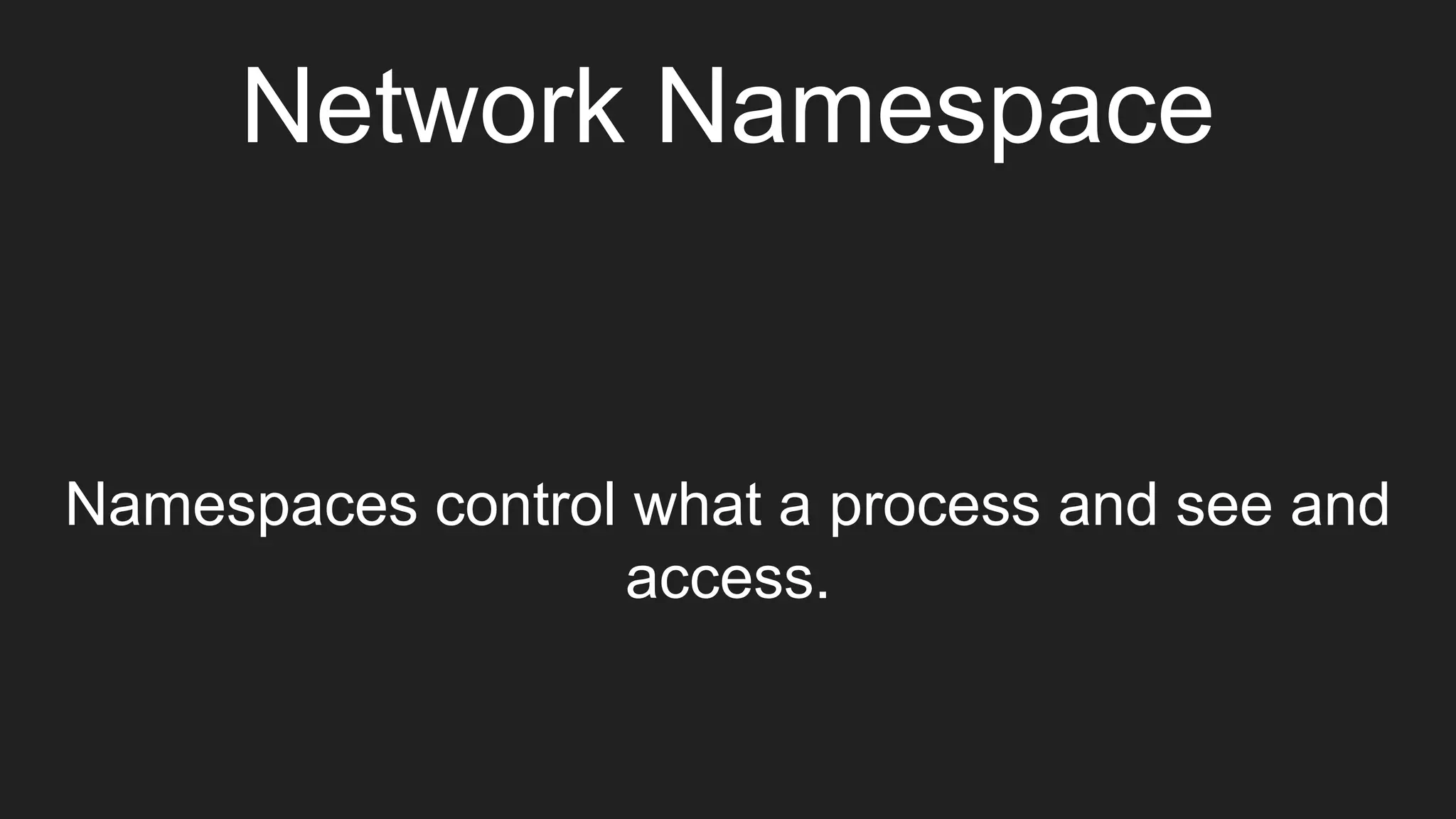
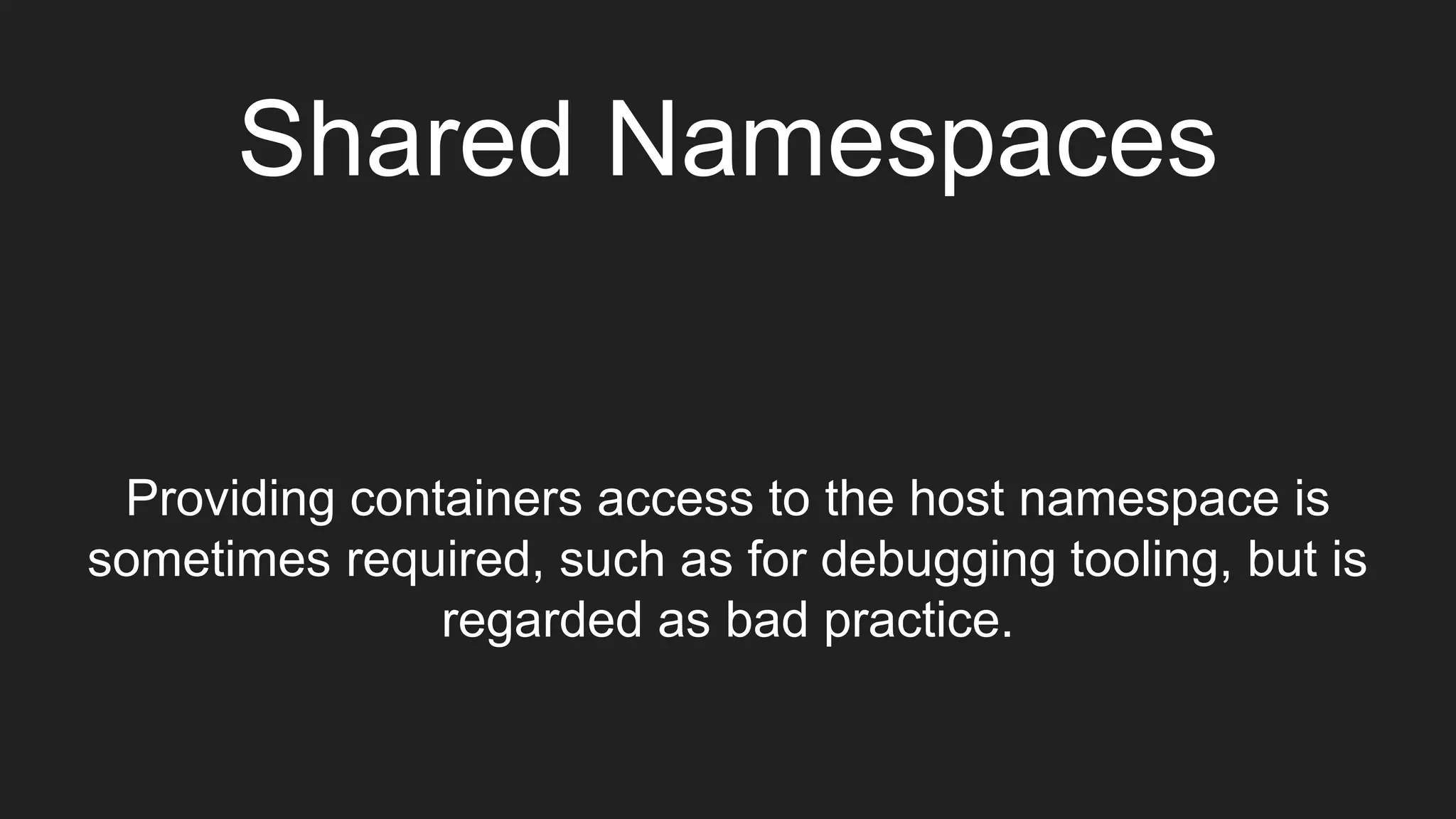
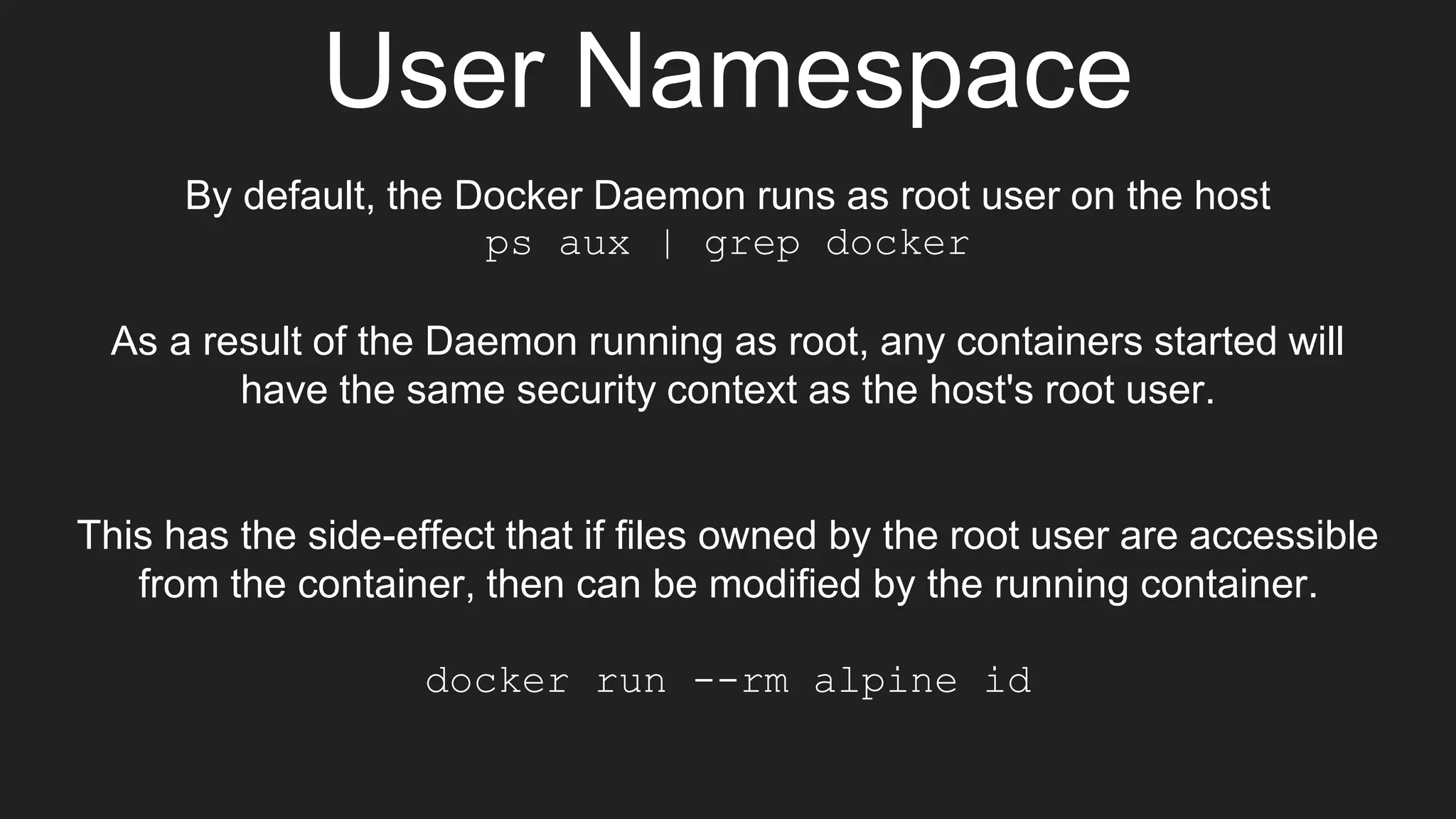
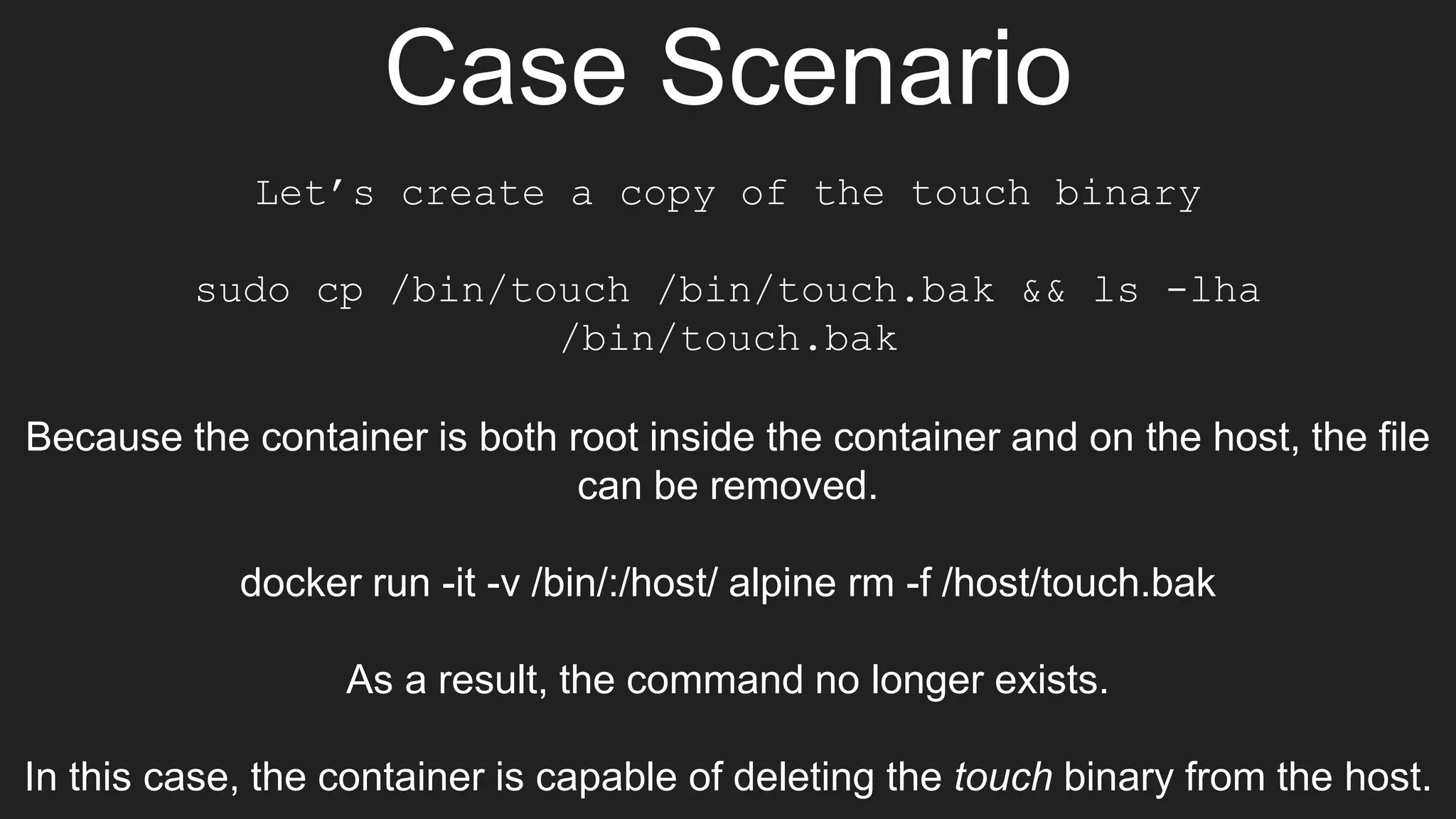
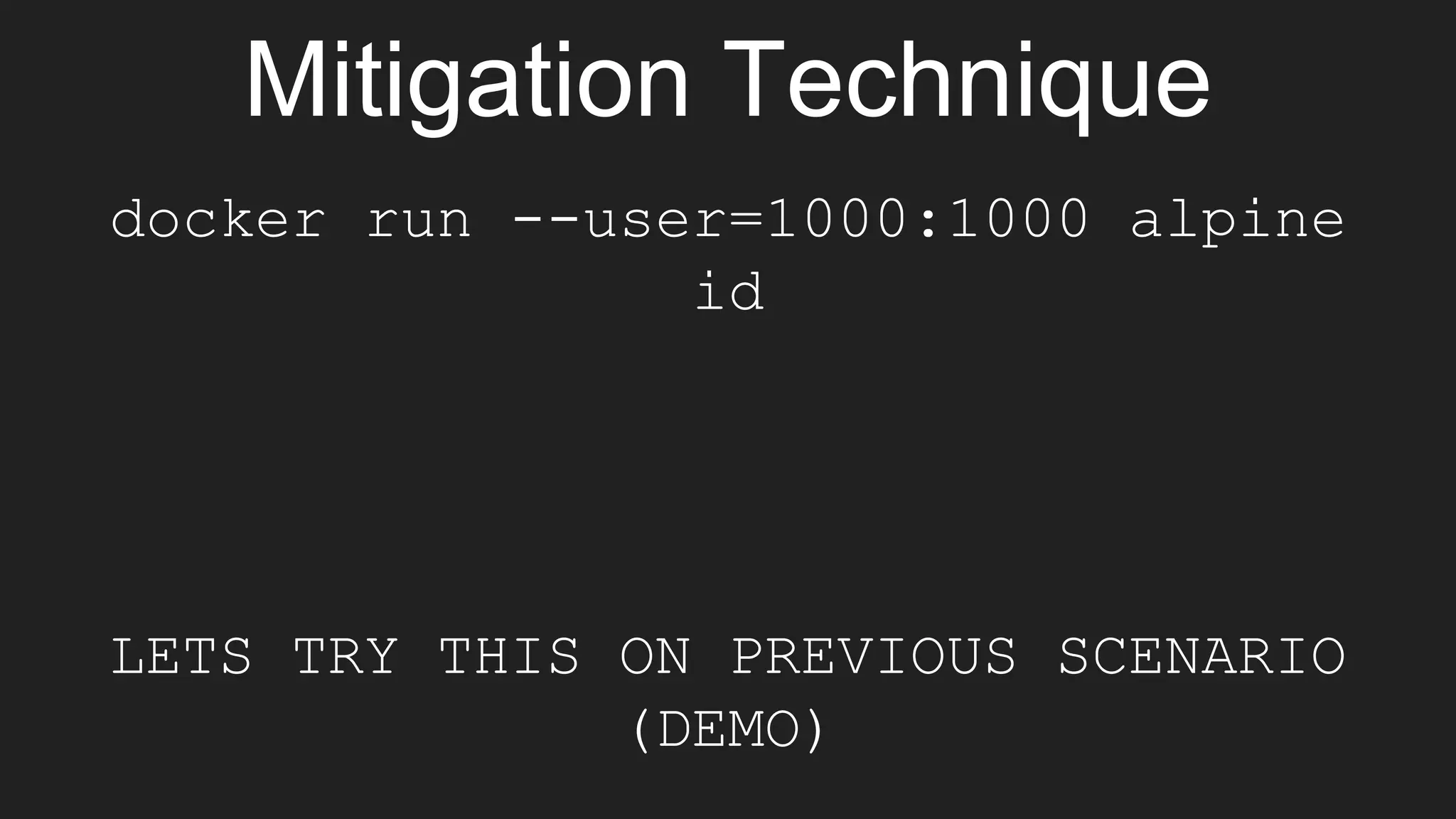
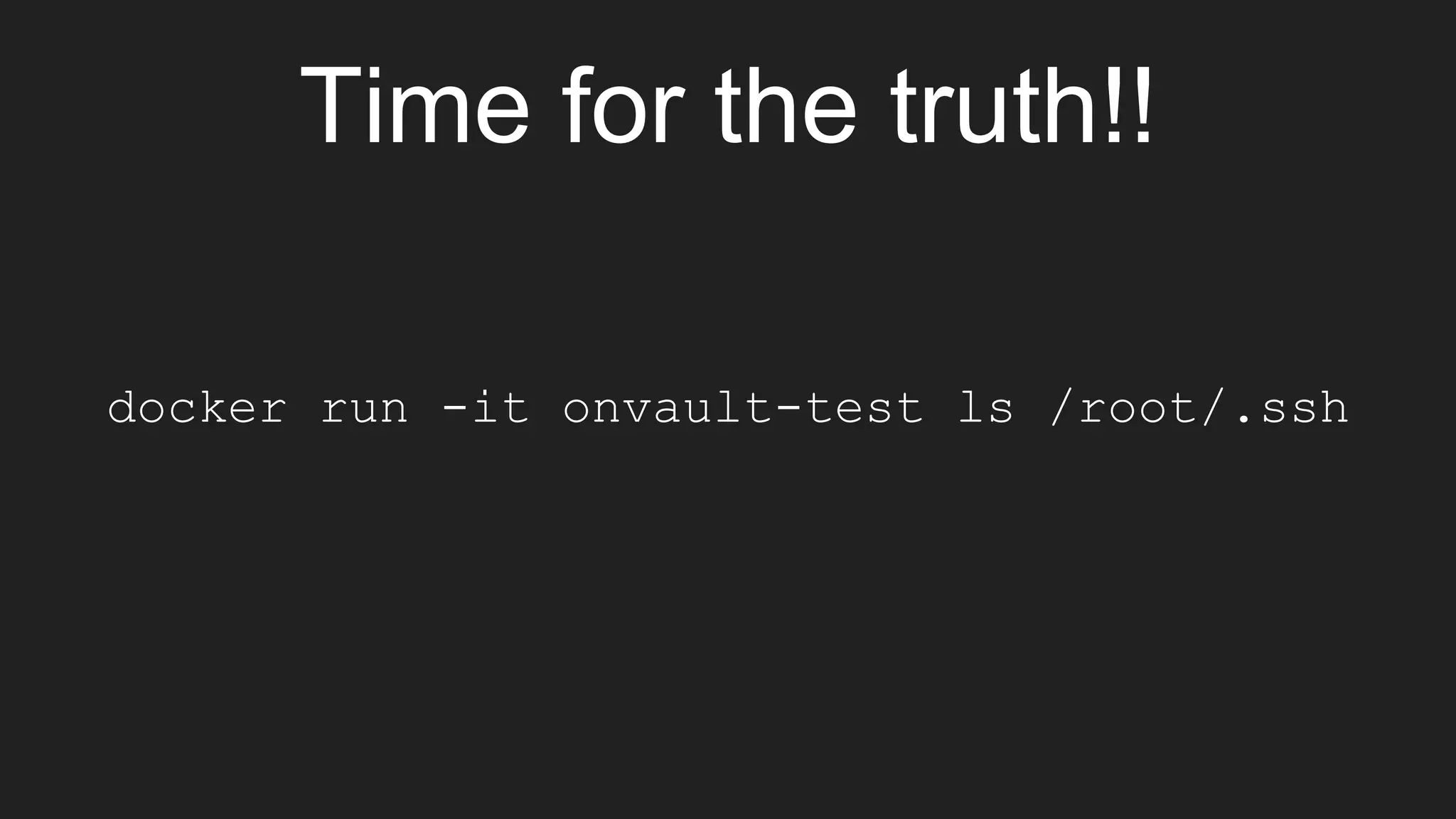
The document discusses exploiting vulnerabilities in Elasticsearch 1.4.2 to run Java code through its search functionality, highlighting various security measures like cgroups and seccomp profiles. It explains concepts such as user and PID namespaces in Docker, illustrating potential security risks when containers run as root on the host. Additionally, the document describes integrating Docker with a secrets management tool, Vault, to securely manage and access sensitive data during container operations.