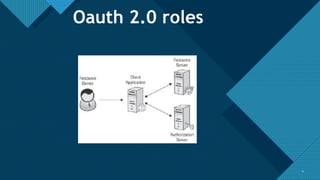
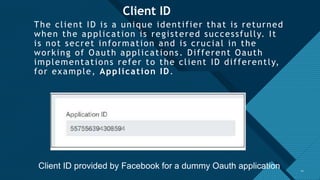
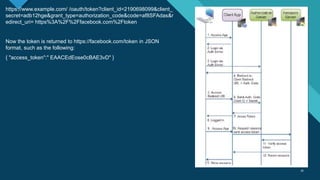
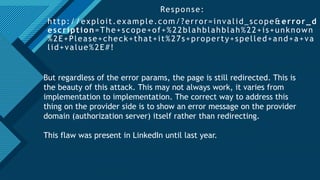
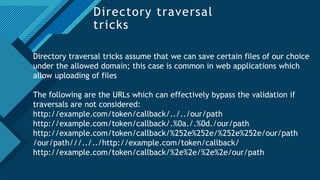
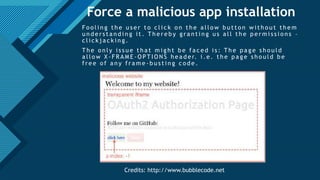
The document provides a comprehensive overview of the OAuth 2.0 authorization protocol, detailing its key roles such as the resource owner, client, and authorization server. It explains the mechanics of receiving grants, including different types of authorization flows like authorization and implicit grants, and addresses potential exploitation risks associated with OAuth implementations. Additionally, it highlights common vulnerabilities and attack vectors, such as open redirects and improper validation of redirect URIs.