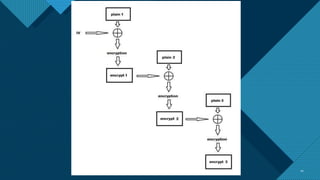
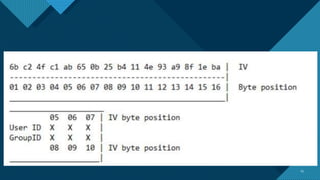
Cryptography is an important but often neglected part of security testing. The presentation discusses different attacks against cryptographic ciphers and encryption modes. It demonstrates bit-flipping attacks against cipher block chaining and padding oracle attacks. Padding is used to standardize message lengths for encryption and proper padding can be checked by decryption errors, allowing decryption via known plaintext attacks.