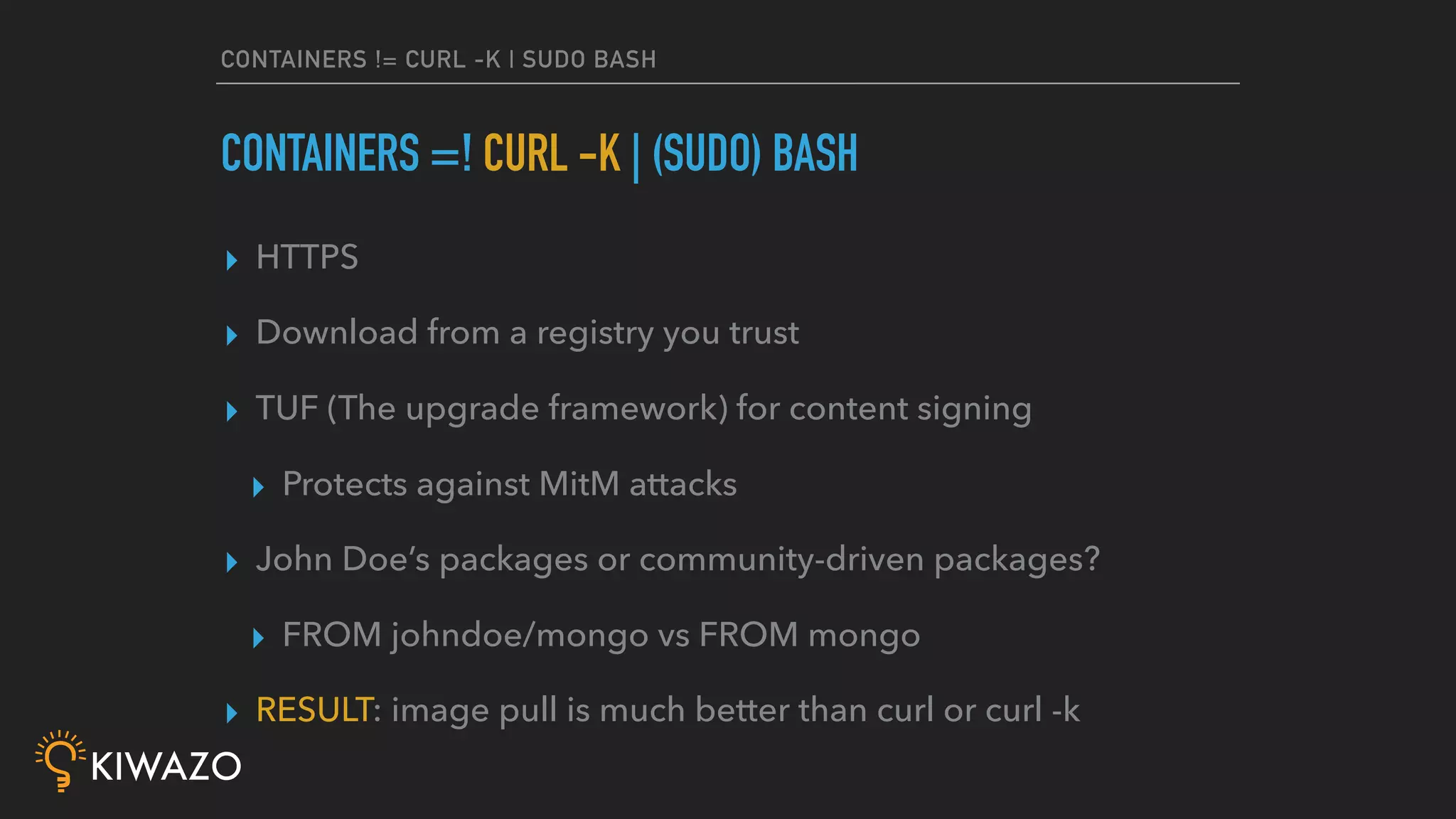
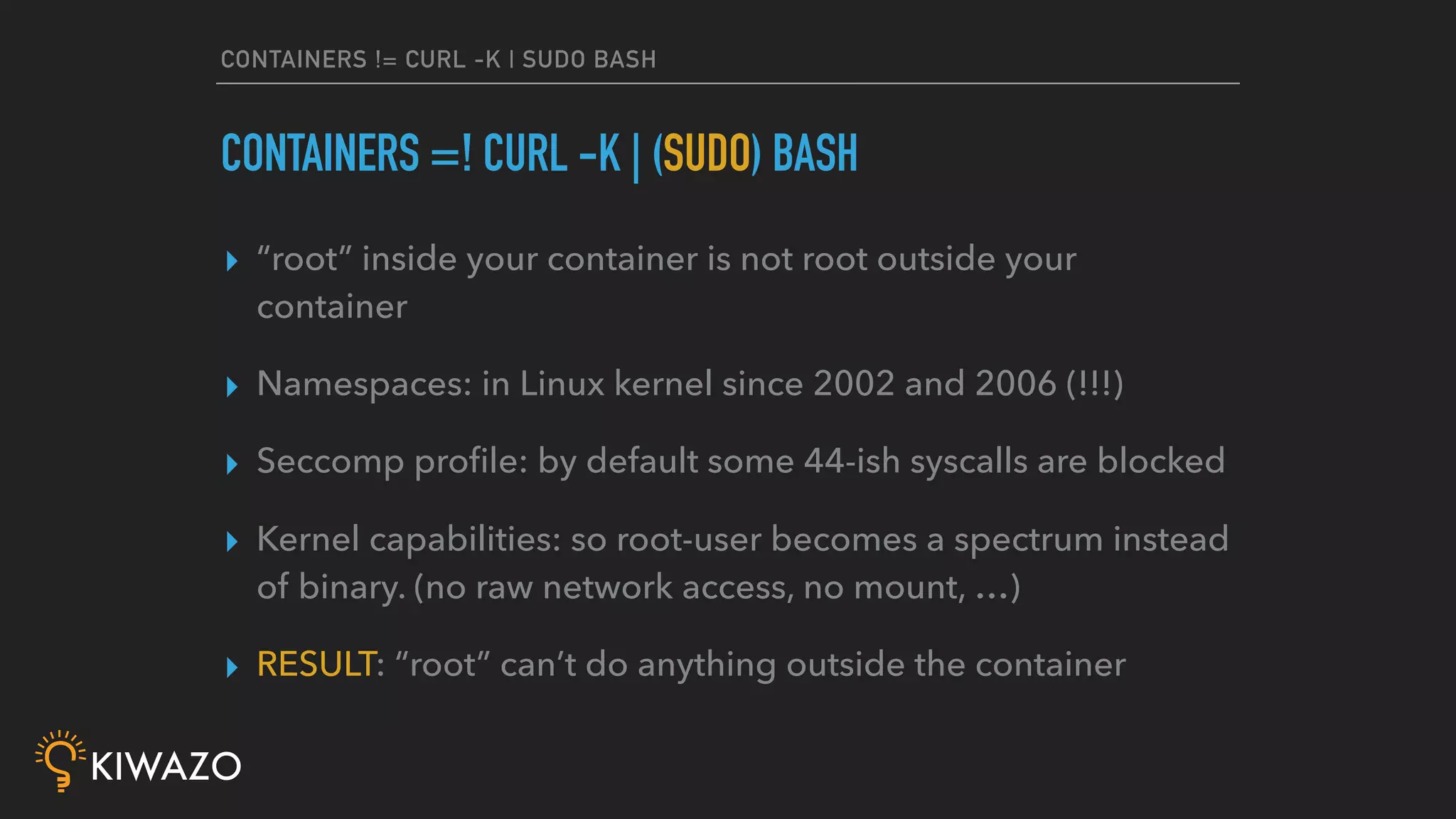
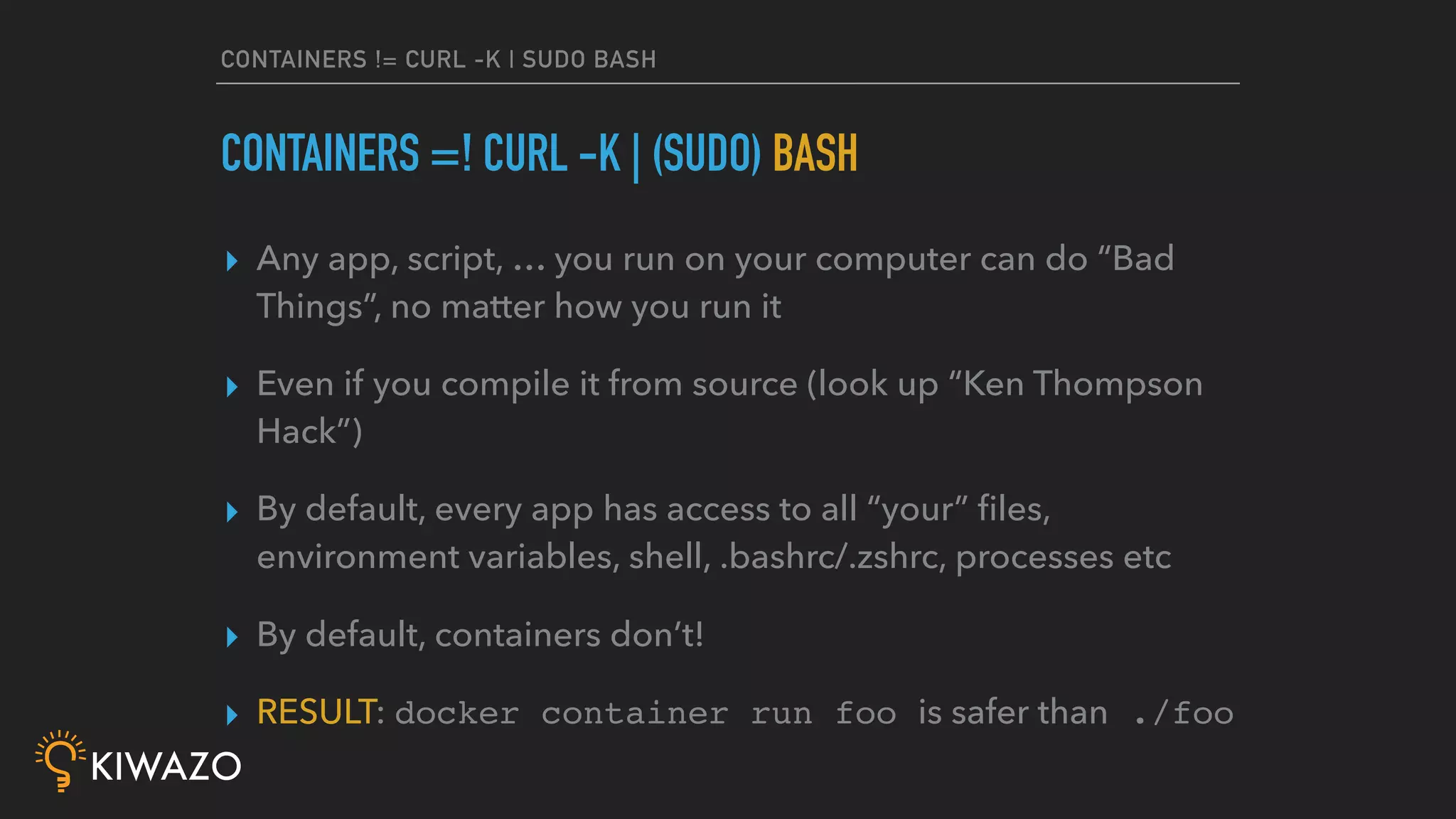
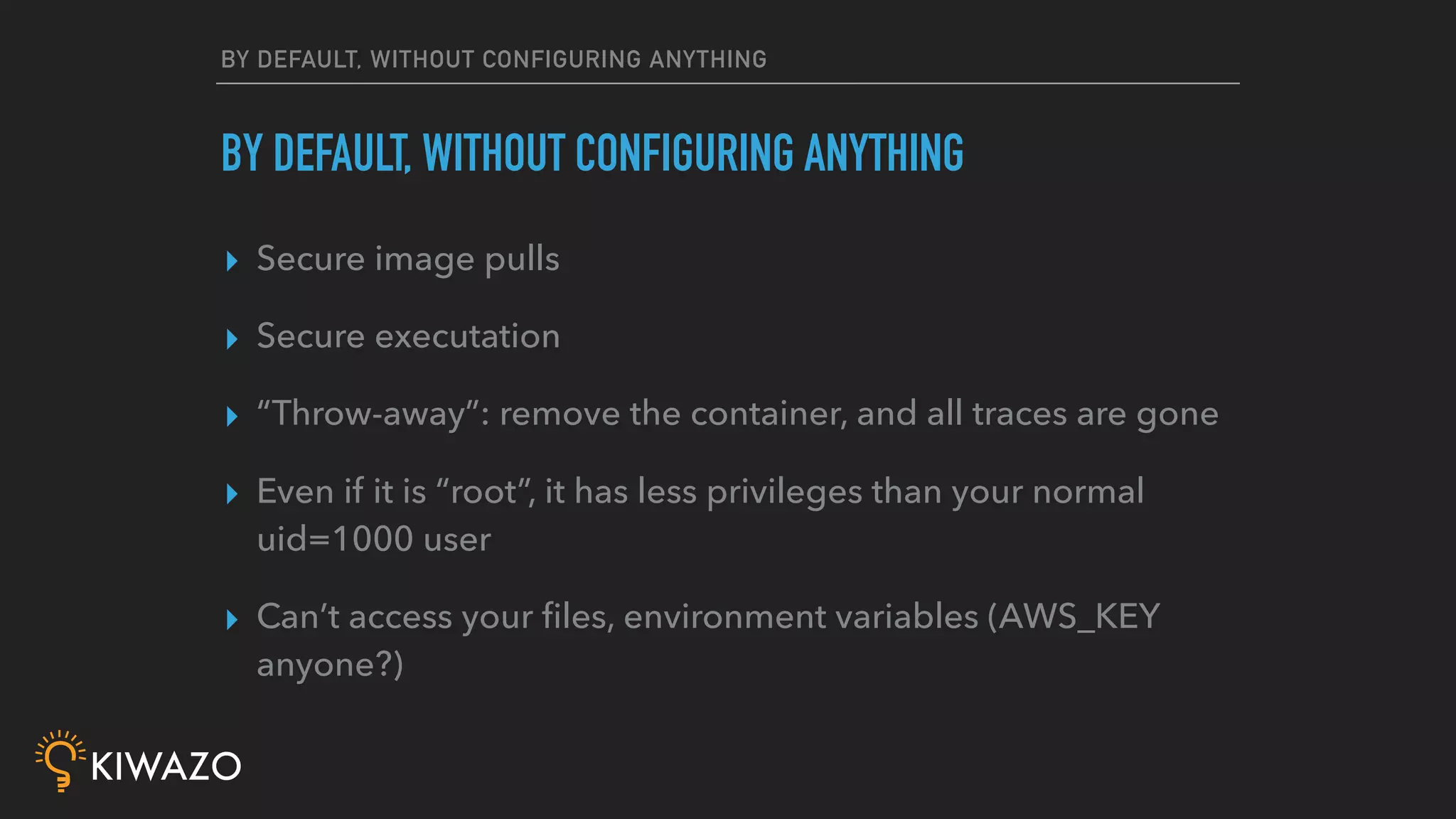
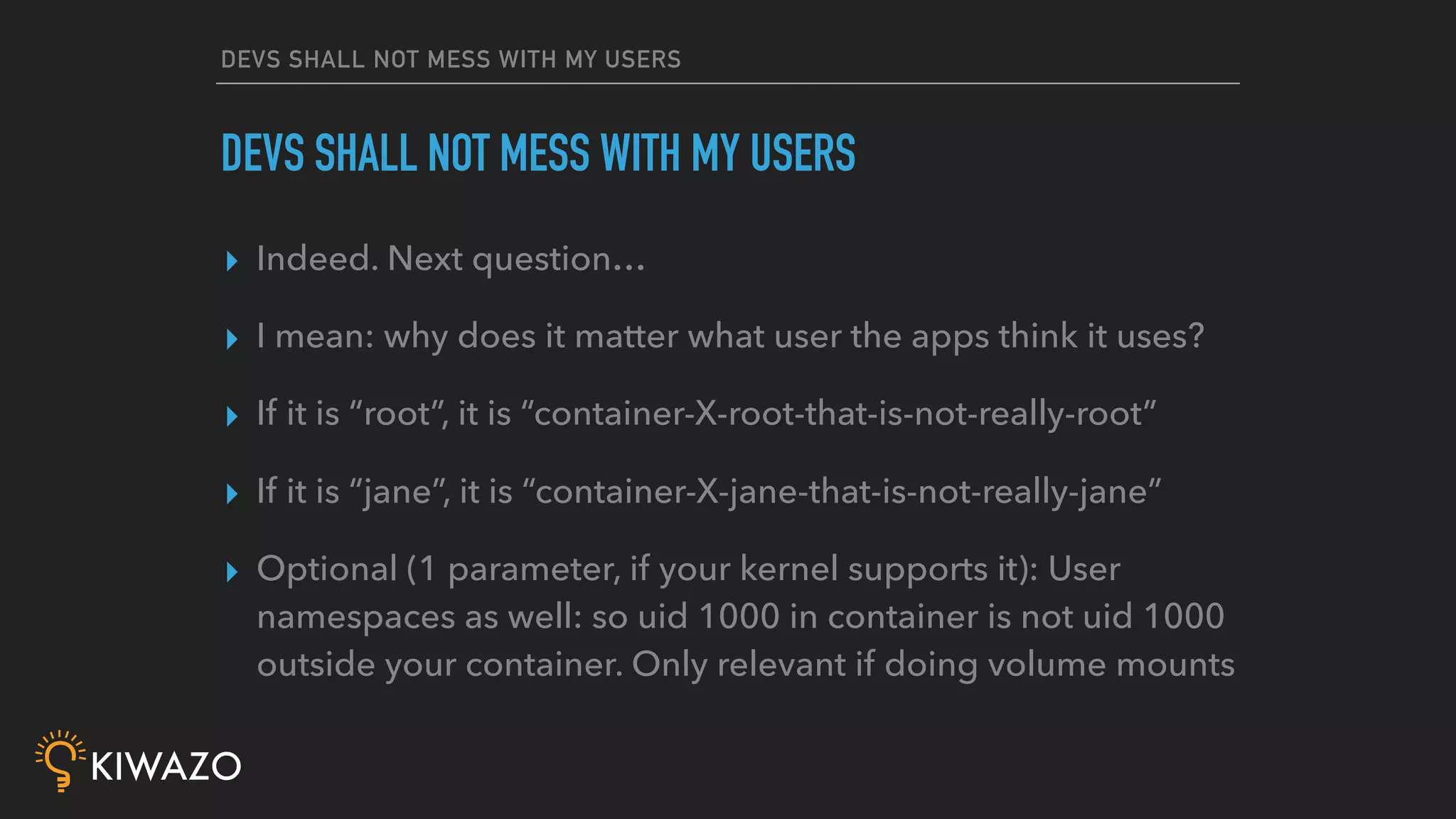
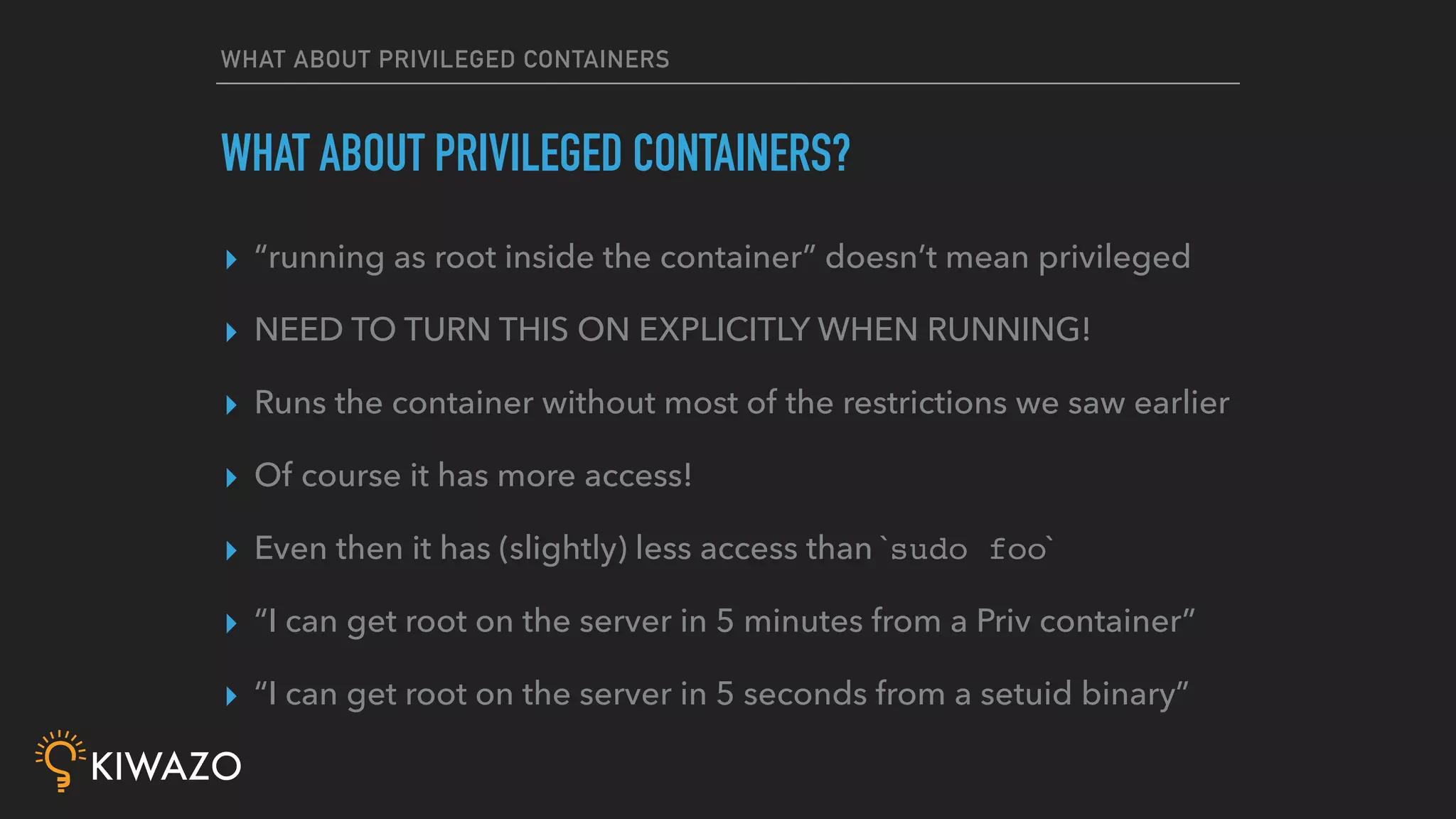
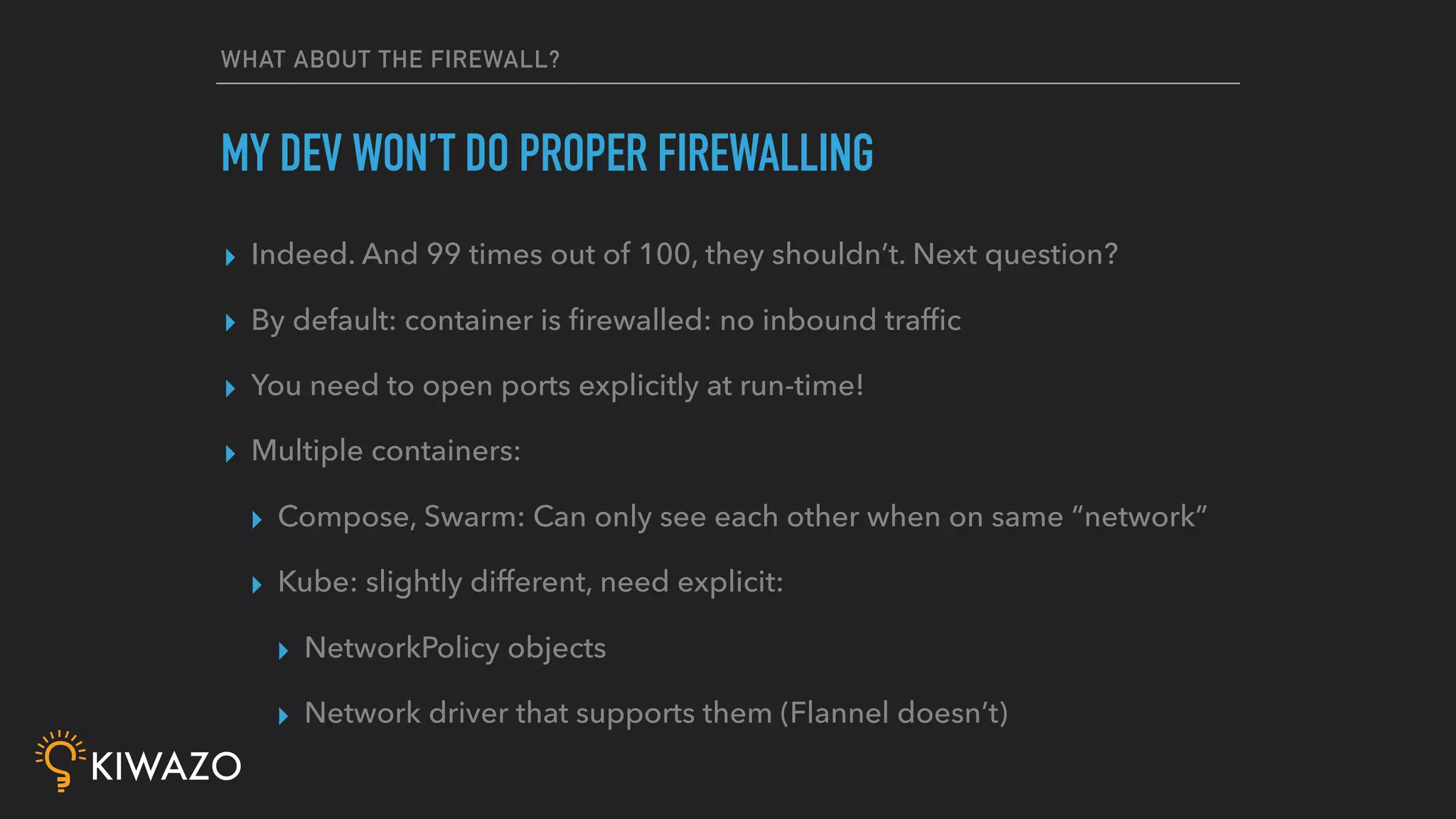
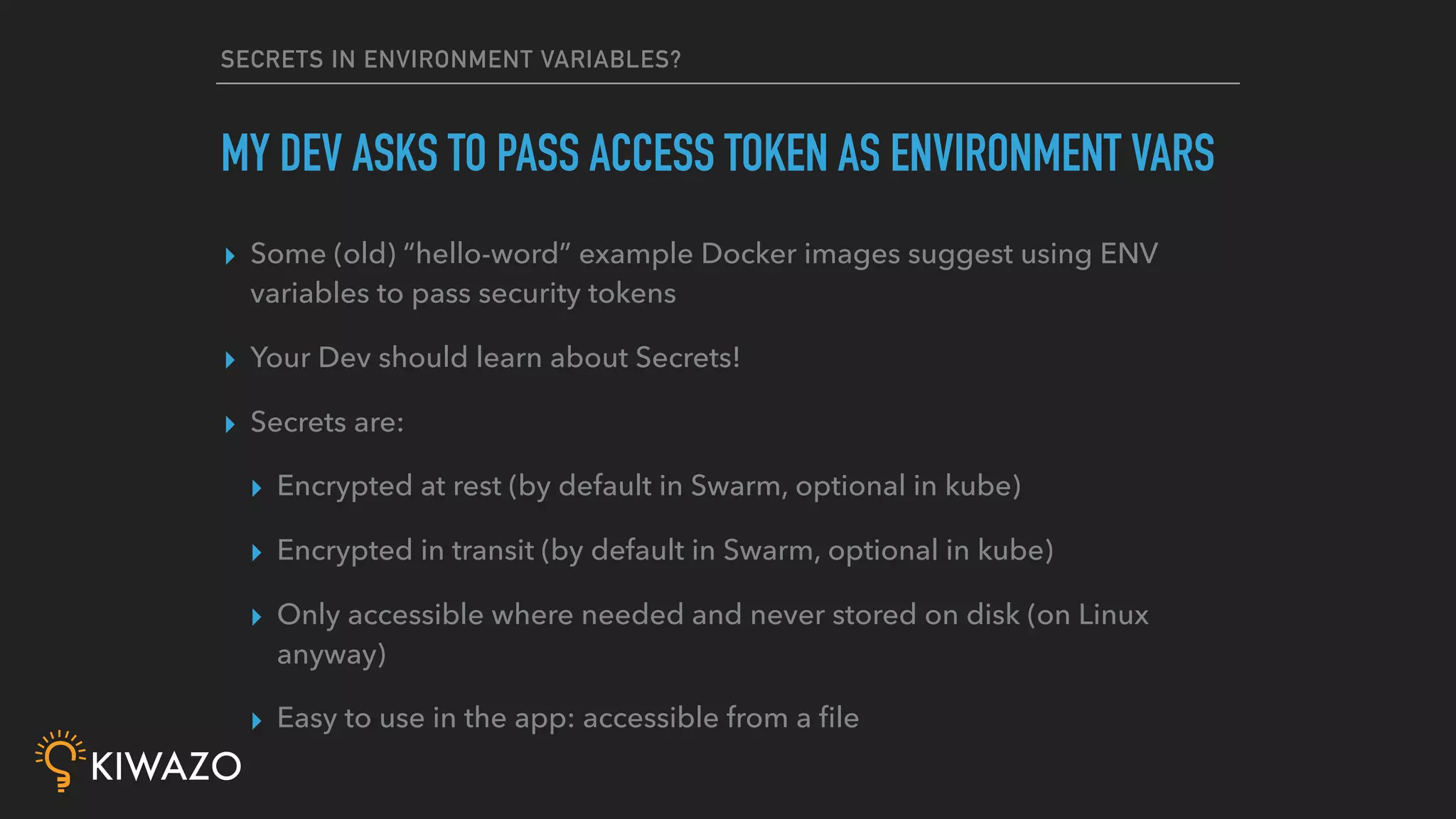
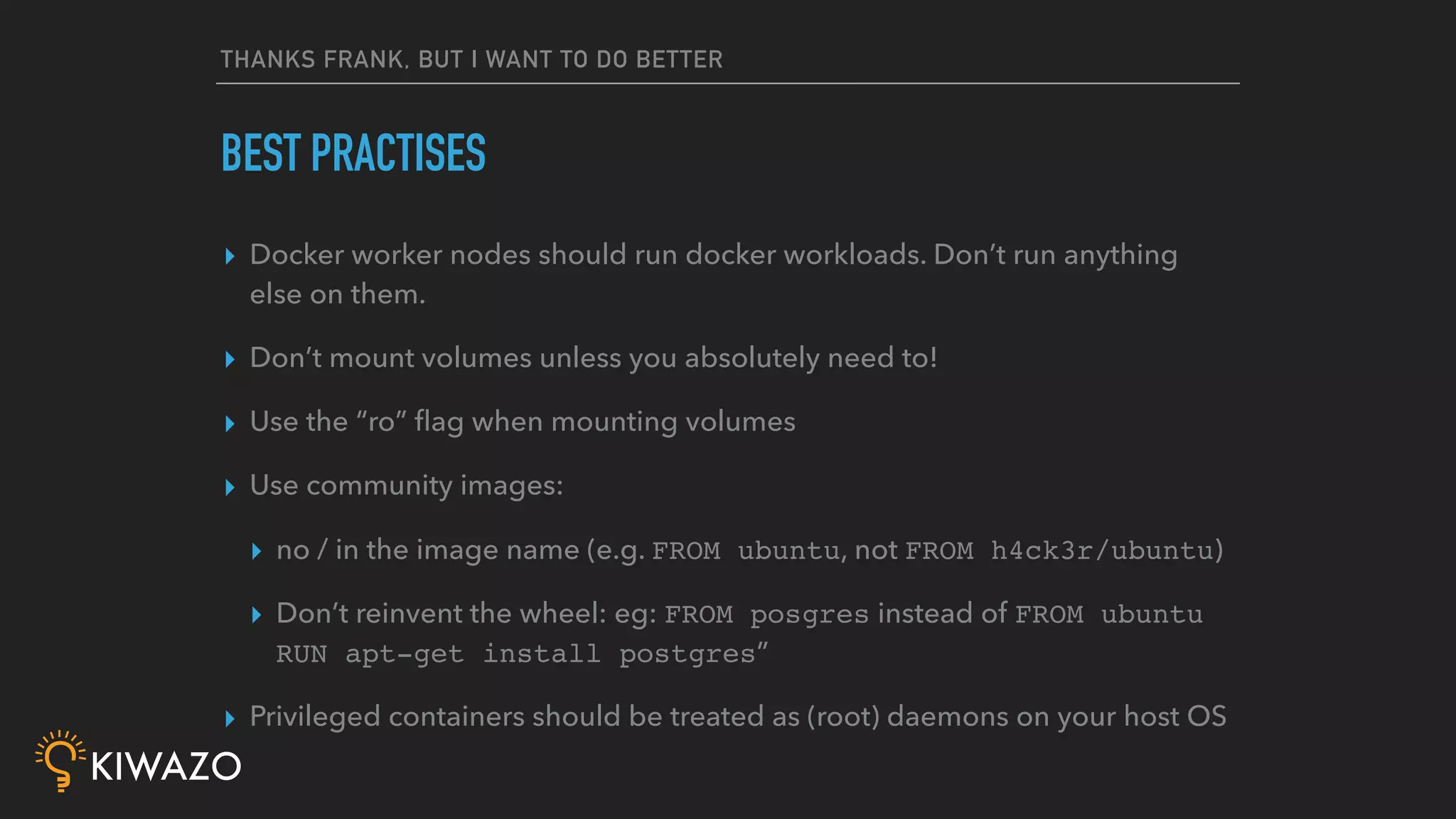
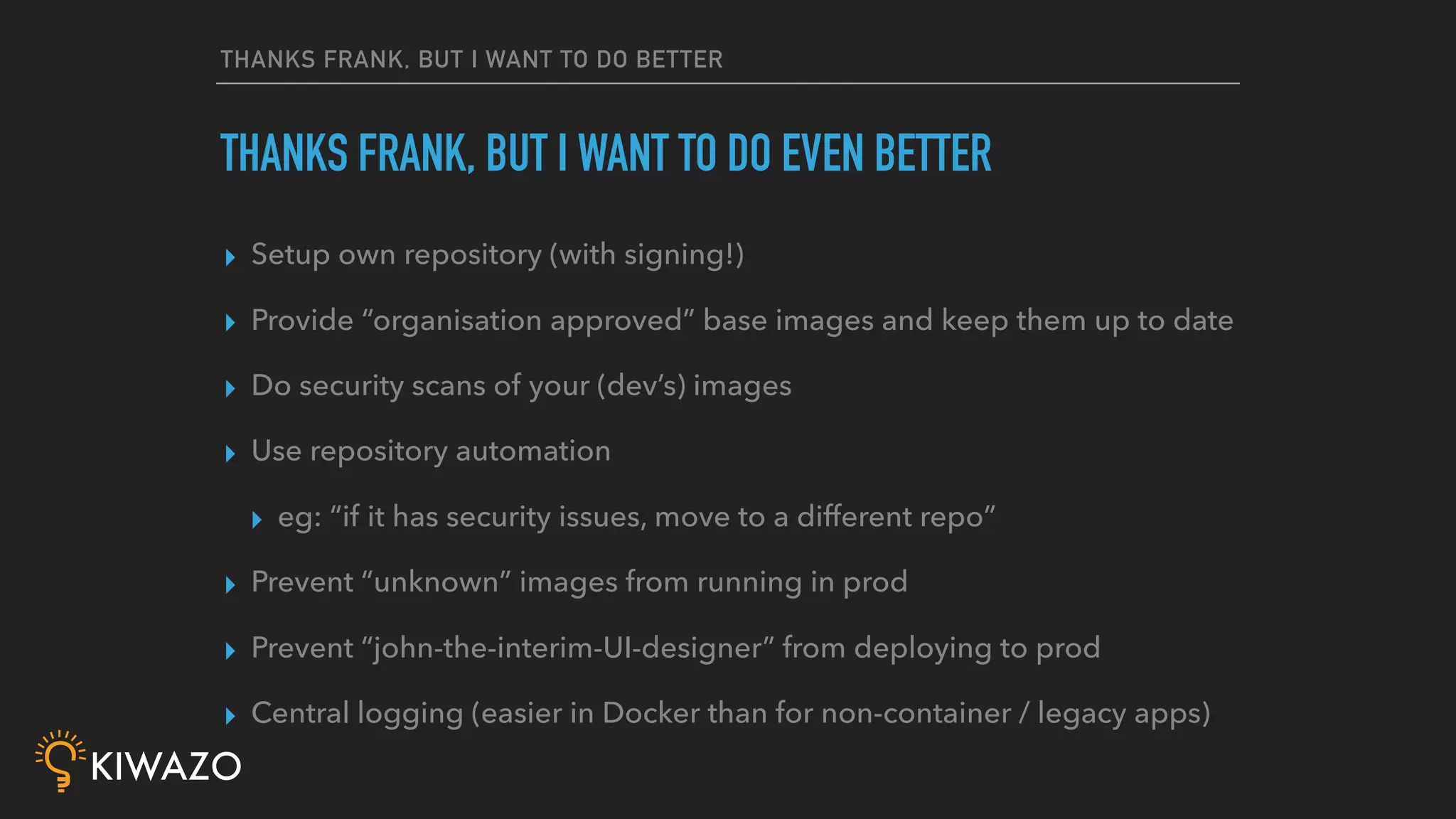
Containers provide security benefits over directly running applications by default, without additional configuration. Namespaces isolate processes inside containers so they cannot access files or resources outside the container. Images are pulled from trusted registries using content signing for integrity. Privileged containers still have fewer privileges than directly running as root. Firewalls also isolate containers by default. Best practices include using signed community images instead of custom images, restricting privileged containers, and centralizing logging.