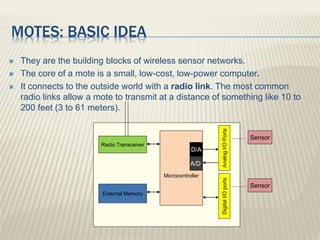
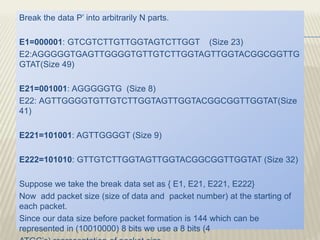
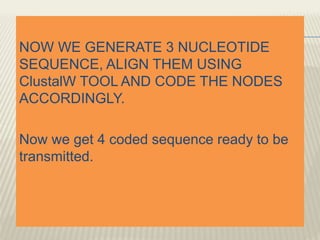
The document discusses secured communication in the context of the Indian defense system. It presents on secured communication using wireless sensor networks for effective border monitoring. The key points discussed are security issues on the border, using wireless sensor networks with motes for data collection, and a proposed secure data transmission algorithm using DNA sequencing and frequency-hopping spread spectrum.