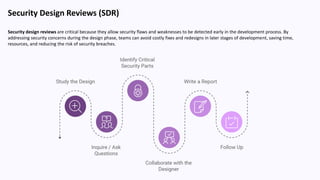
The document discusses secure software design and programming, emphasizing the integration of security throughout the software development lifecycle (SDLC). It outlines phases such as planning, design, implementation, testing, deployment, and maintenance, focusing on identifying and mitigating risks and vulnerabilities at each stage. Additionally, it highlights challenges in secure software development and offers recommendations for best practices, including threat modeling and security design reviews.






















![preencoded.png
• Pressman, R. S. (2010). Software engineering: A practitioner's approach (7th ed.).
McGraw-Hill Education.
• Kohnfelder, L., & Schuyler, P. (2001). Designing secure software: A guide for
developers. Addison-Wesley.
• Andress, J., & Winterfeld, S. (2011). Cyber warfare: Techniques, tactics and tools
for security practitioners. Elsevier.
• Dafydd, S., & Stuttard, M. (2011). The web application hacker's handbook: Finding
and exploiting security flaws (2nd ed.). Wiley Publishing.
• Ugnichenko, A. V. (2009). Secure software design [E-book]. Retrieved November
28, 2024, from
https://masters.donntu.ru/2009/fvti/ugnichenko/library/EFLVSecSysDes1.pdf
• Umair, M., Shah, H., & Khan, Z. A. (2010). A survey on requirements and design
methods for secure software development. ResearchGate. Retrieved November
28, 2024, from https://www.researchgate.net/publication/228804937
• IEEE Computer Society. (2007). The IEEE secure design principles: Developing tools
to strengthen software. IEEE Xplore. Retrieved November 28, 2024, from
https://ieeexplore.ieee.org/abstract/document/4529475
• Semantics Scholar. (n.d.). Techniques for software system design security.
Semantics Scholar. Retrieved November 28, 2024, from
https://pdfs.semanticscholar.org/ac51/7c1c09b4db636a3e278d46175d12c99158c
0.pdf
Reference](https://image.slidesharecdn.com/secure-software-design-and-secure-programming-241129115808-2fb08ad9/85/Secure-Software-Design-and-Secure-Programming-24-320.jpg)