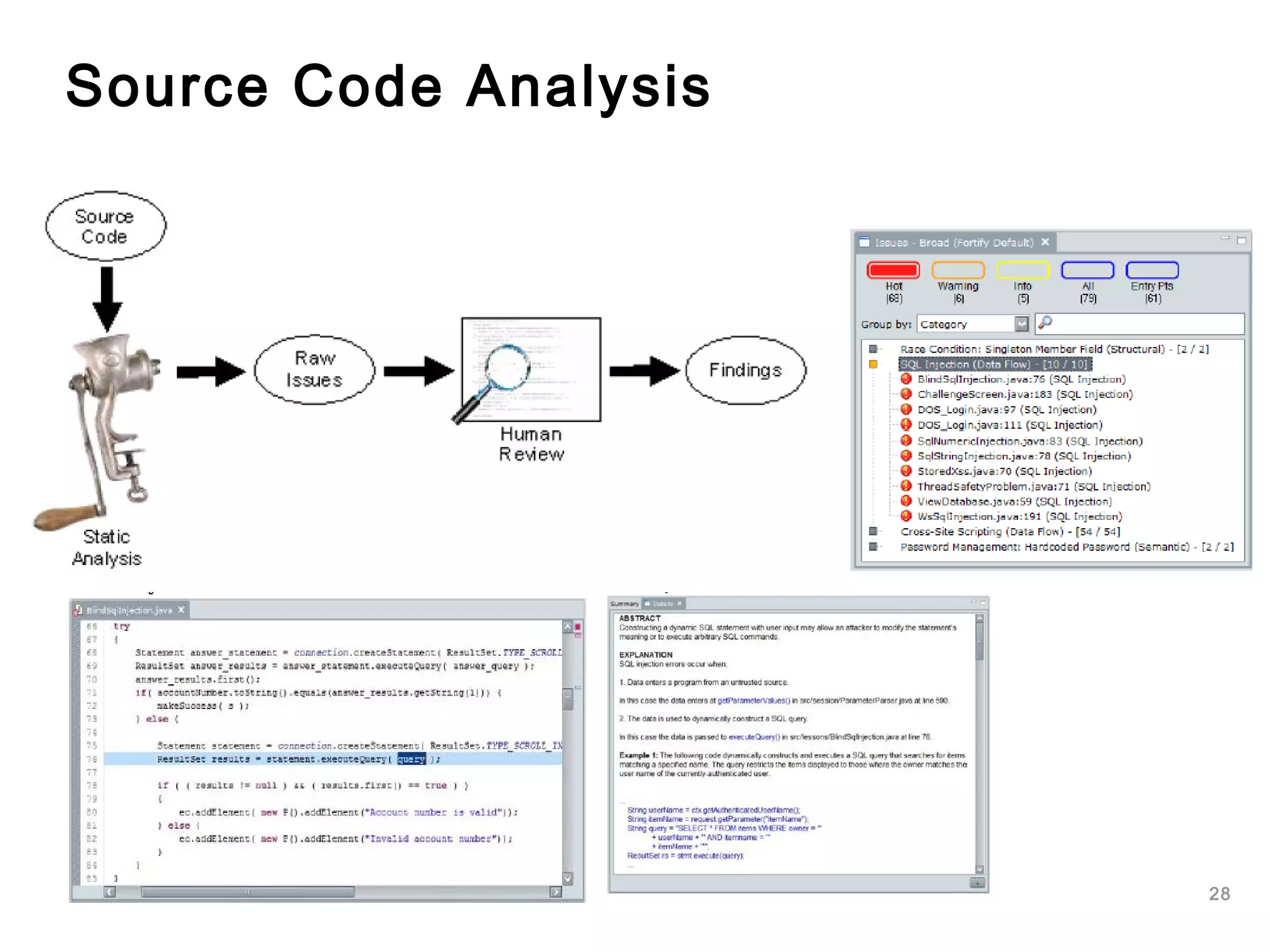
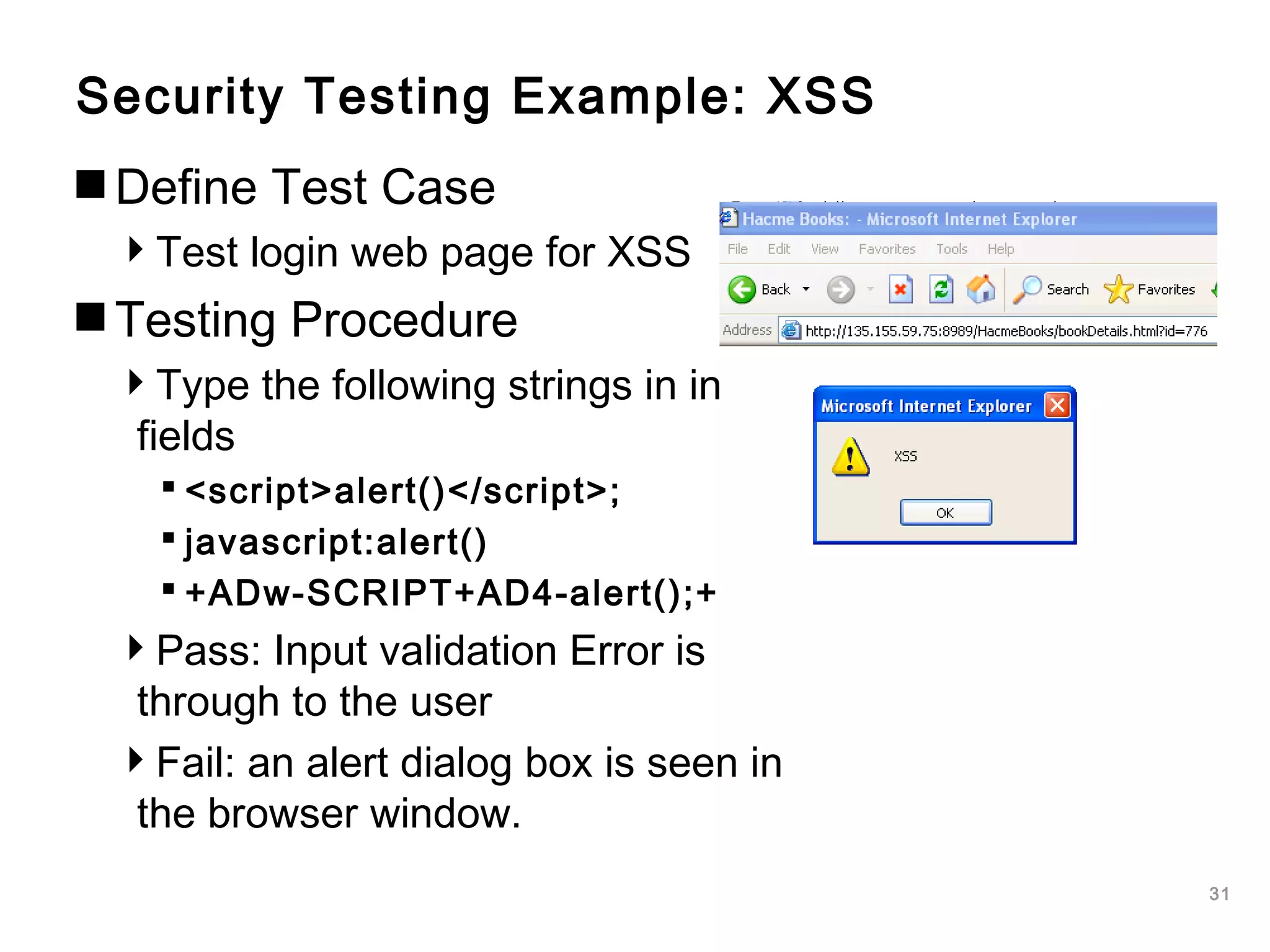
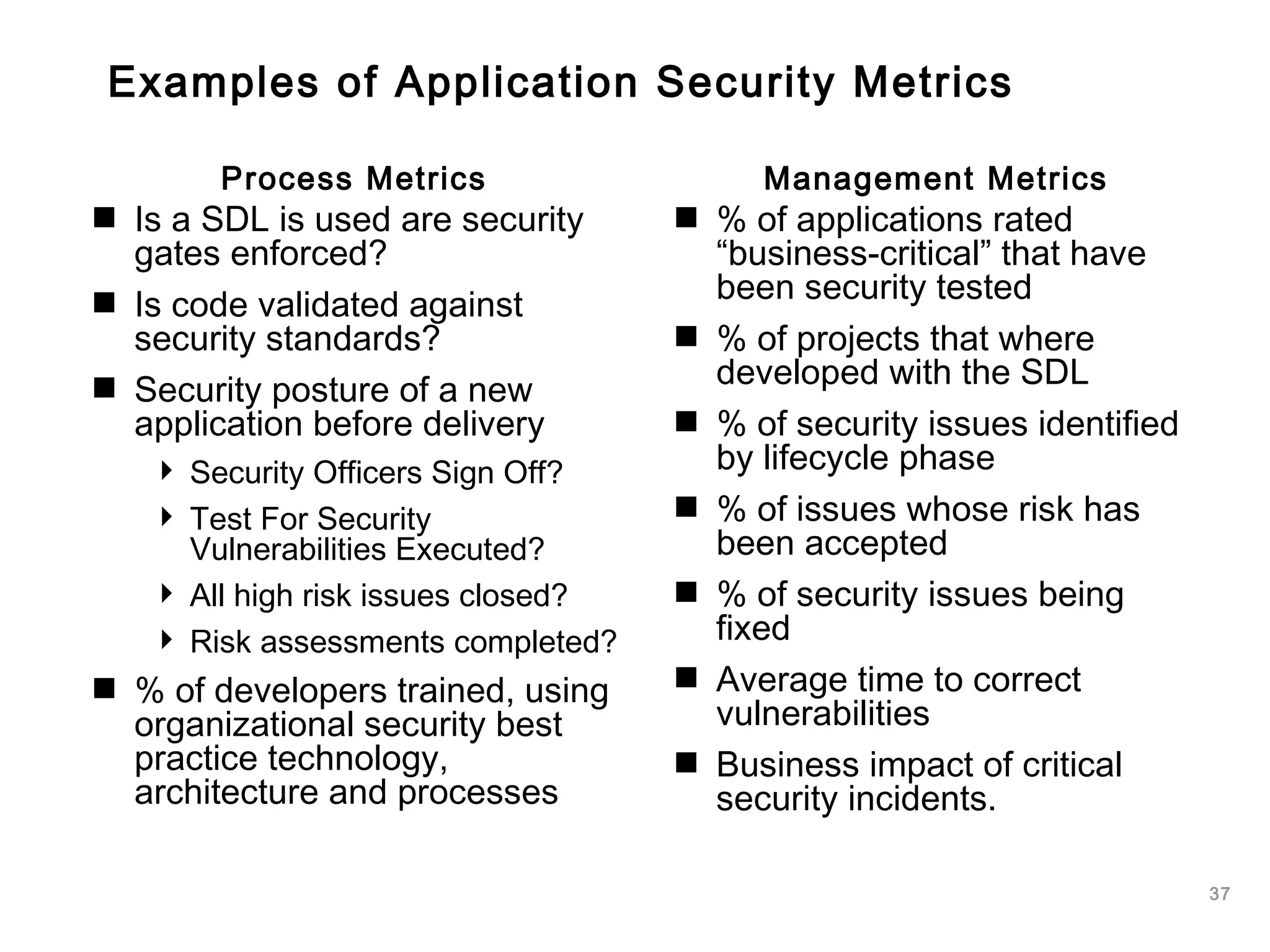
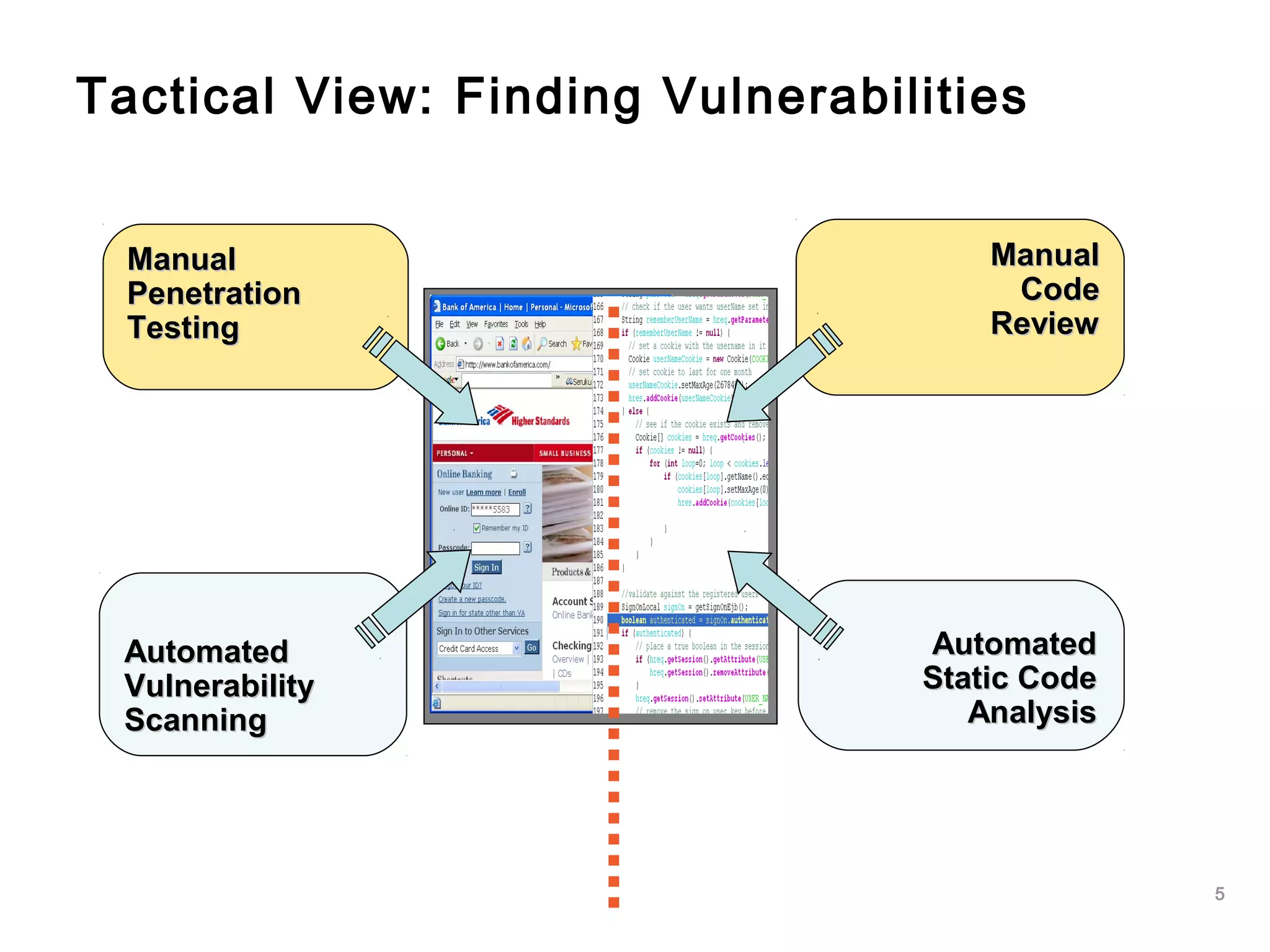
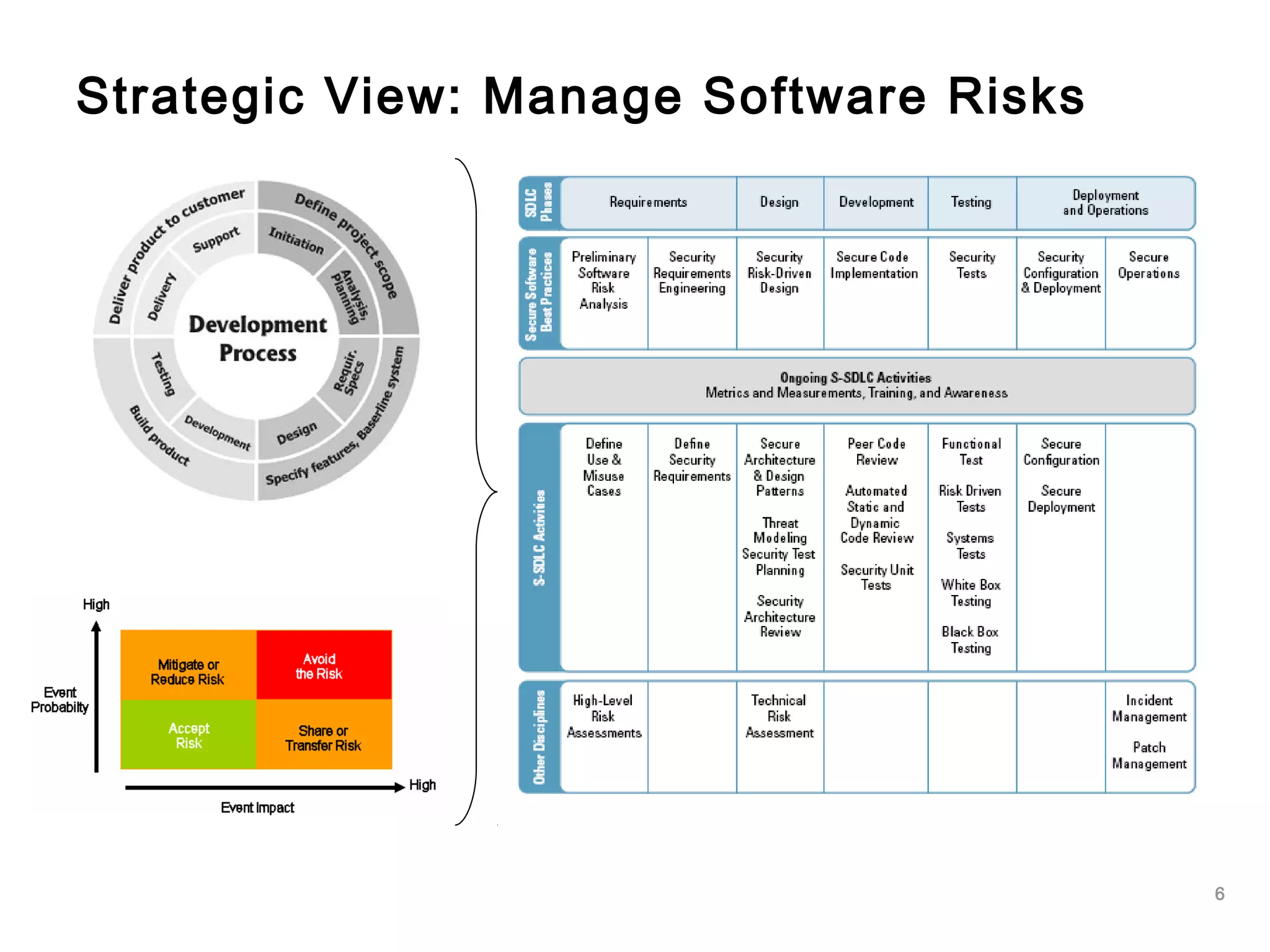
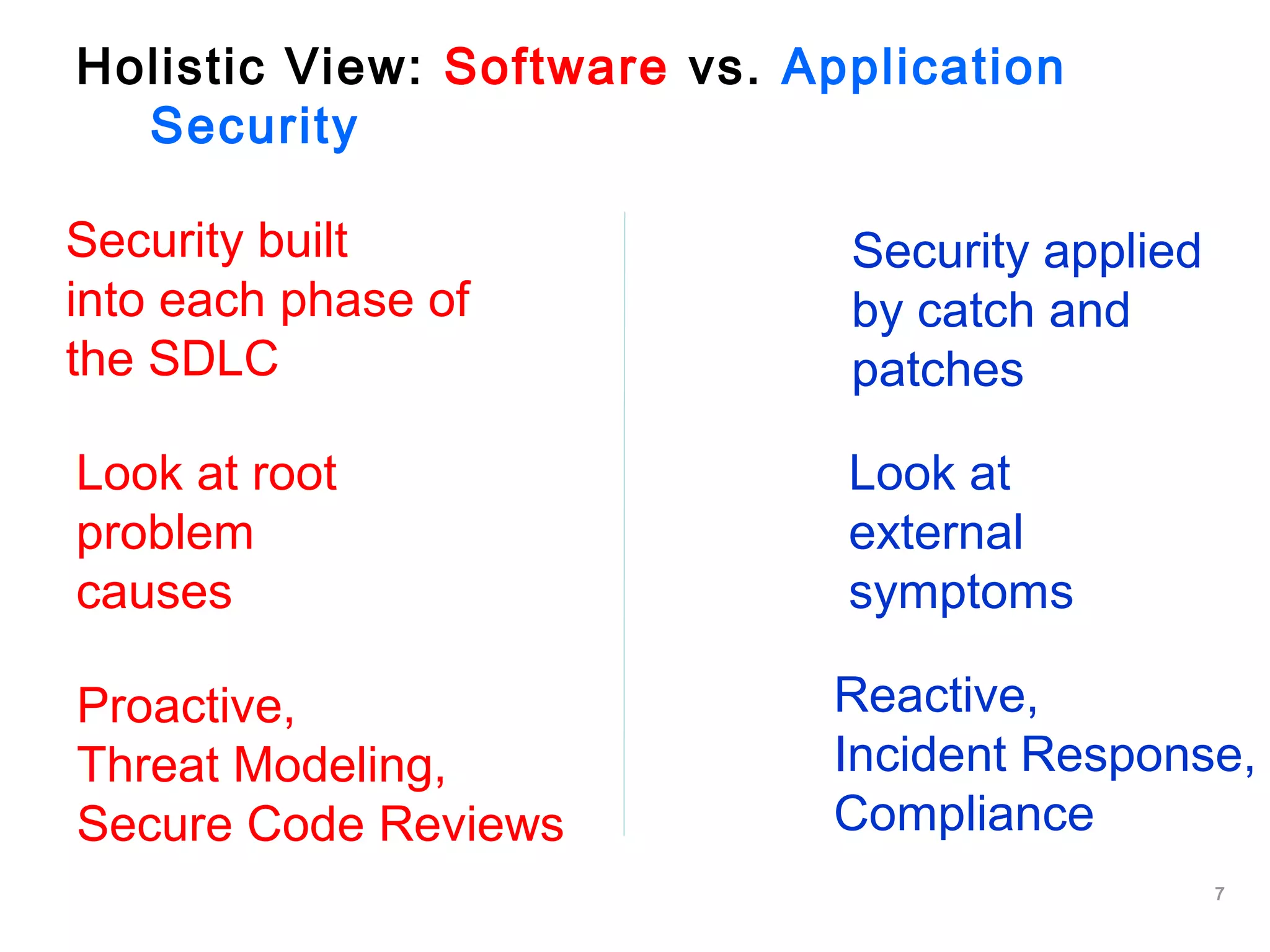
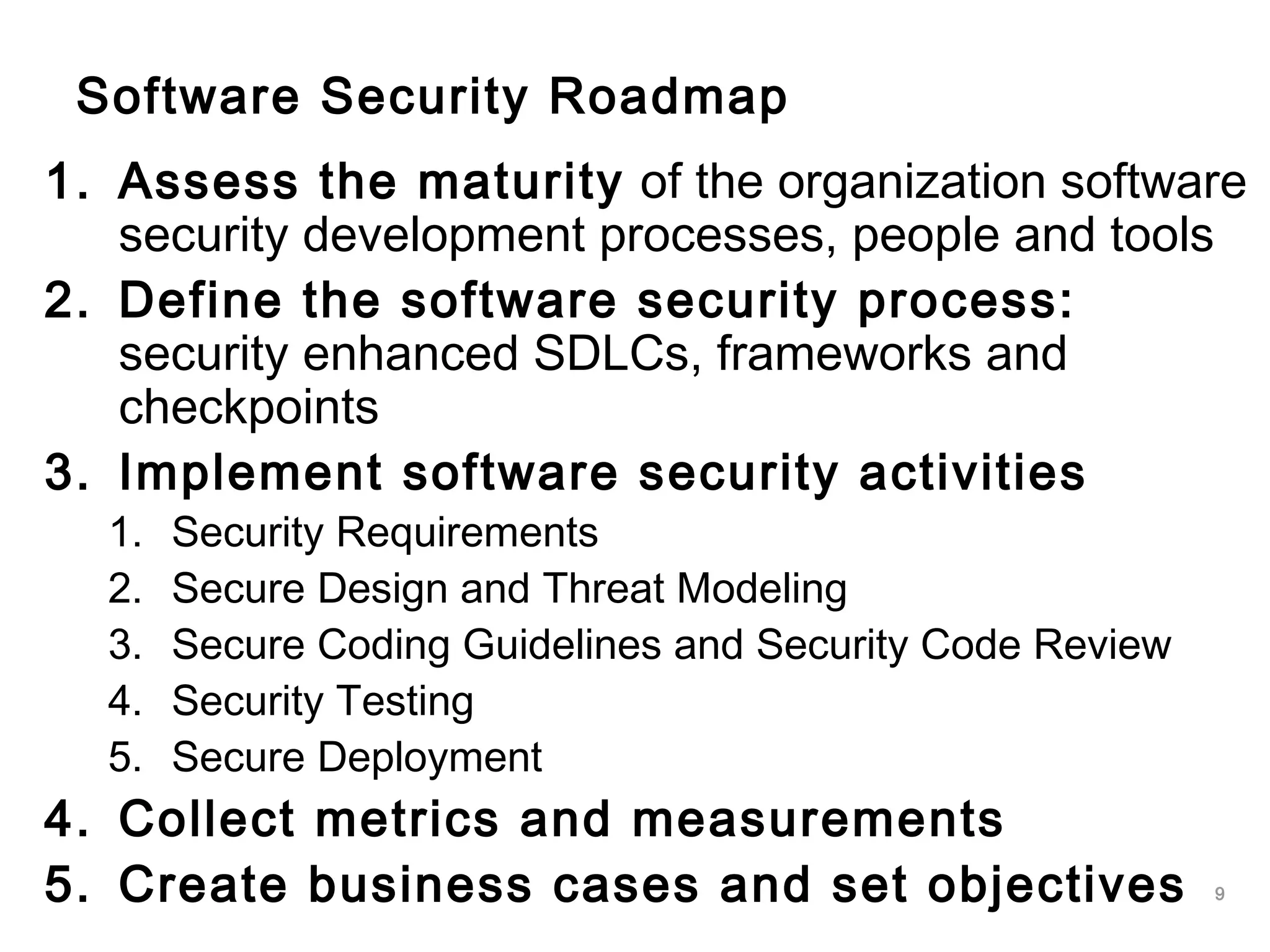
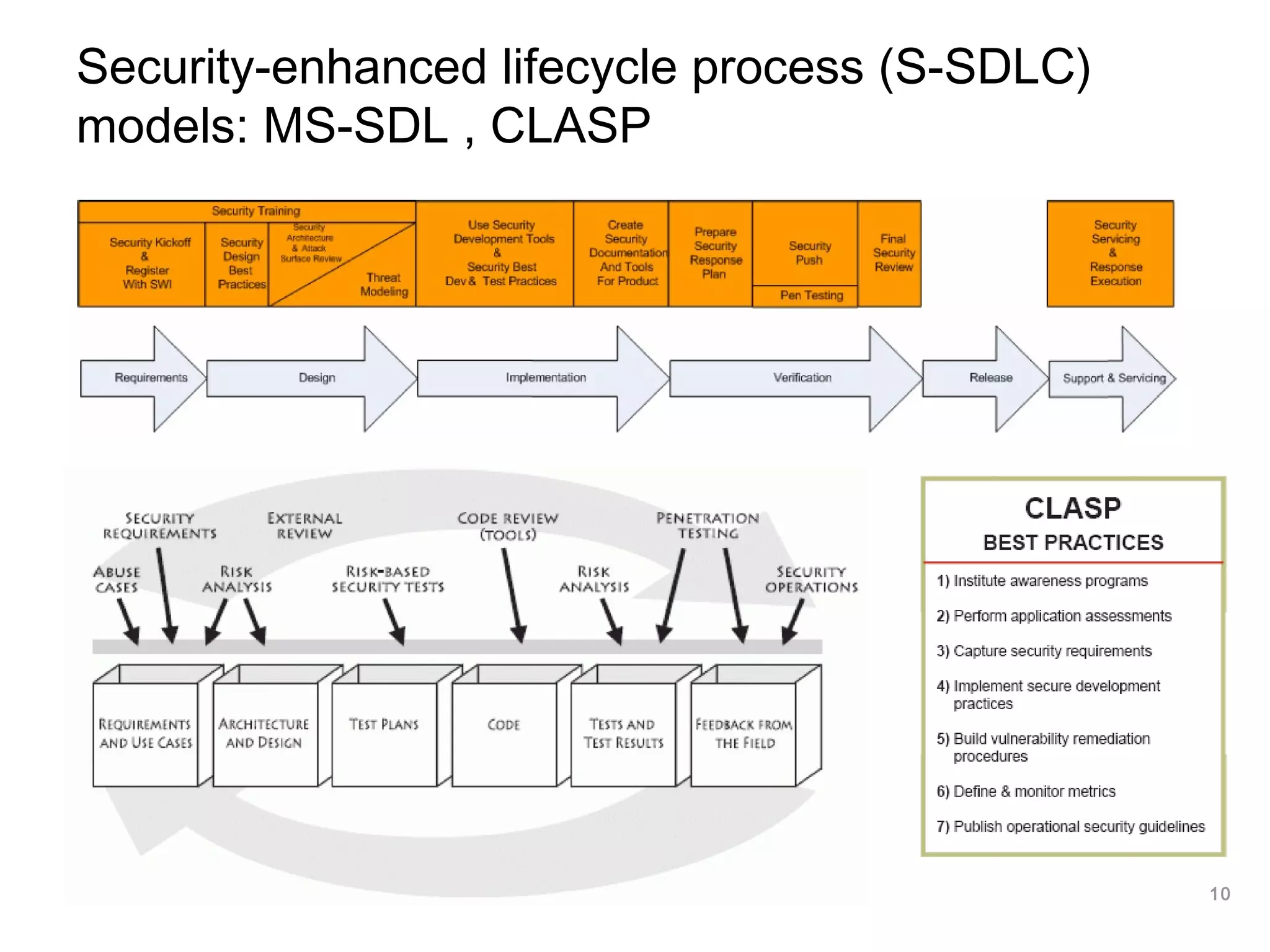
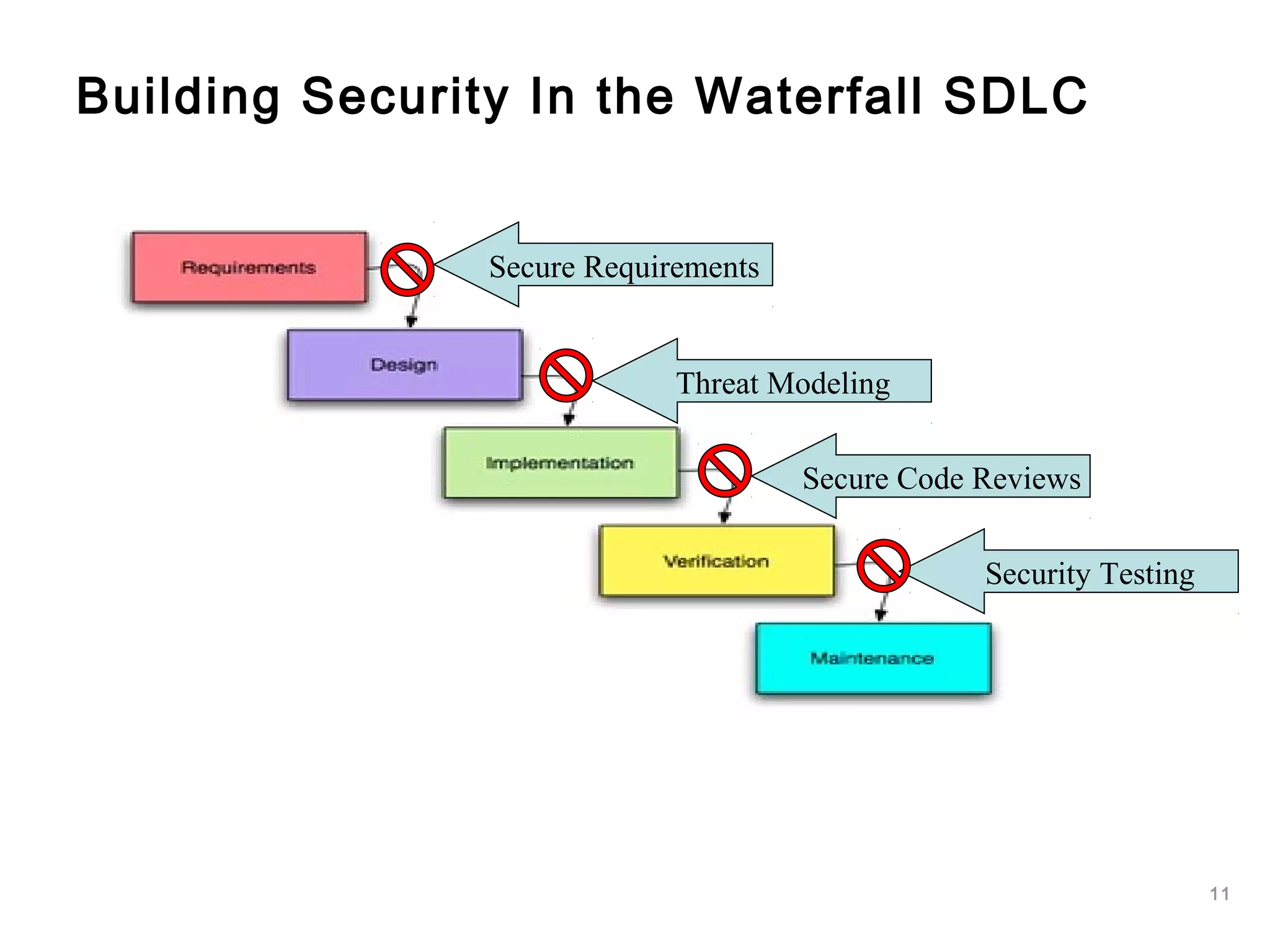
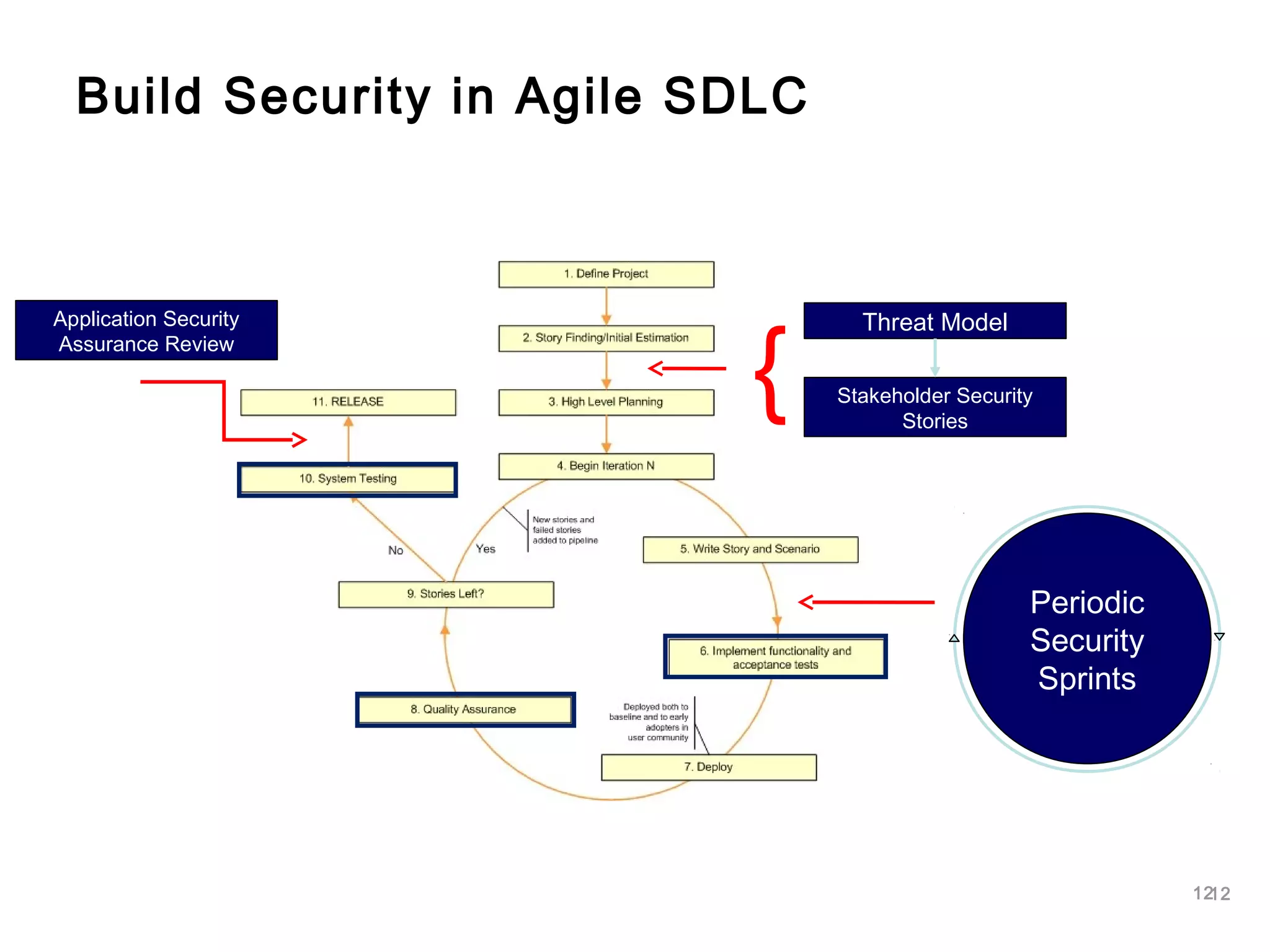
The document outlines an approach to application security that involves establishing a software security roadmap. It discusses assessing maturity, defining a security-enhanced software development lifecycle (S-SDLC), and implementing security activities such as threat modeling, secure coding practices, security testing, and metrics. The goal is to manage software risks through a proactive and holistic approach rather than just reacting to vulnerabilities.












![26
Example SQL Injection - Secure coding
requirements
Use SQL parameterized queries, avoid
dynamic SQL generation:
SELECT * FROM users WHERE username=?
JAVA EE use strongly typed “PreparedStatement”
in .NET use “SqlCommand” with “SqlParameters”
Sanitize input, remove special characters:
' " ` ; * % _ =&|*?~<>^()[]{}$nr
Use custom error messages:
No SQL exception information in error messages](https://image.slidesharecdn.com/softwaresecurityengineering-160330055343/75/Software-security-engineering-26-2048.jpg)