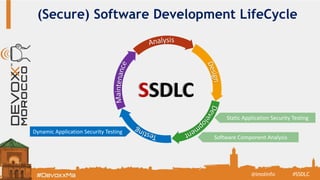
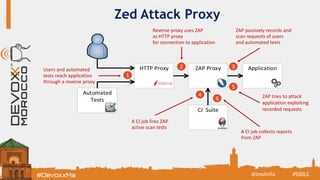
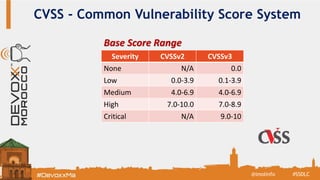
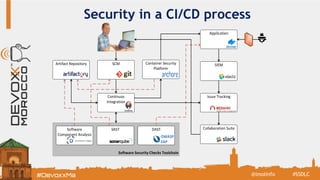
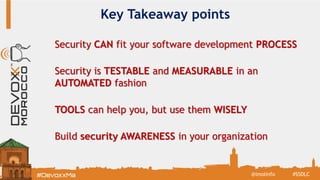
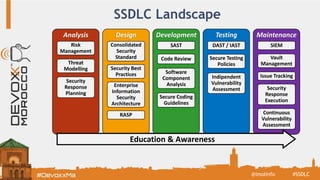
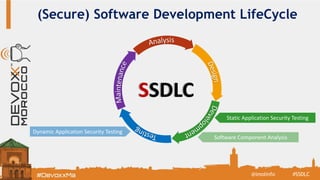
The document discusses the Secure Software Development Lifecycle (SSDL) and its importance in preventing security vulnerabilities throughout the software development process. It highlights the costs associated with data breaches, legal requirements such as GDPR, and key principles of security including the necessity for processes that ensure security is testable and measurable. Additionally, it covers various security testing tools and methodologies, including OWASP's top 10 application security risks and the significance of continuous awareness and education in maintaining security.

















![SAST - Static Application Security Testing
String key = “A Fixed Password"; // 128 bit key
// Create key and cipher
Key aesKey = new SecretKeySpec(key.getBytes(), "AES");
Cipher cipher = Cipher.getInstance("AES");
// encrypt the text
cipher.init(Cipher.ENCRYPT_MODE, aesKey);
byte[] encrypted = cipher.doFinal(password.getBytes());
#SSDLC@imolinfo](https://image.slidesharecdn.com/devoxxma18-ssdlc-181129135214/85/Secure-Software-Development-Lifecycle-Devoxx-MA-2018-23-320.jpg)
![SAST - Static Application Security Testing
String key = “A Fixed Password"; // 128 bit key
// Create key and cipher
Key aesKey = new SecretKeySpec(key.getBytes(), "AES");
Cipher cipher = Cipher.getInstance("AES");
// encrypt the text
cipher.init(Cipher.ENCRYPT_MODE, aesKey);
byte[] encrypted = cipher.doFinal(password.getBytes());
#SSDLC@imolinfo](https://image.slidesharecdn.com/devoxxma18-ssdlc-181129135214/85/Secure-Software-Development-Lifecycle-Devoxx-MA-2018-24-320.jpg)
![SAST - Static Application Security Testing
String key = “A Fixed Password"; // 128 bit key
// Create key and cipher
Key aesKey = new SecretKeySpec(key.getBytes(), "AES");
Cipher cipher = Cipher.getInstance("AES");
// encrypt the text
cipher.init(Cipher.ENCRYPT_MODE, aesKey);
byte[] encrypted = cipher.doFinal(password.getBytes());
What’s wrong with you bro’???
#SSDLC@imolinfo](https://image.slidesharecdn.com/devoxxma18-ssdlc-181129135214/85/Secure-Software-Development-Lifecycle-Devoxx-MA-2018-25-320.jpg)